Keywords
|
| EEDC Algorithm, LEECH protocol, Digital Signature, Cluster node. |
INTRODUCTION
|
| In this modern world we thrive in using technology which is the most effective and easier in terms of viewing, scanning and to process the obtained data. Wireless sensor network has become a vital part in such activities. The wireless sensor network comprises of node which interfaces with nodes that scan the environment which are sensor nodes, and as the name depicts “wireless”, the obtained data is transmitted wirelessly to the base station which acts as a repository. |
| One of the major threats in wireless sensor network is security and huge consumption of energy which has to be addressed. Energy consumption can be constrained through clustering. Clustering is an effective way of avoiding complexities between sensor nodes of a network which will transmit data to the base station through the cluster head. Security for wireless sensor network can be provided using digital signature which is a critical security service offered in asymmetric key management like cryptography. As we have introduced clustering technique our network becomes a “cluster based wireless sensor network”. |
| Dynamic clustering of the sensor nodes will help in reducing the energy consumption to an extent by multi-hop technique. For this EEDC algorithm is used. The Energy Efficient Dynamic Clustering (EEDC) algorithm which supports two tier hierarchy networks for providing data to multiple base stations is known as two tier hierarchy network. |
LITERATURE SURVEY
|
A. Paper Title: Balanced energy sleep scheduling scheme for high density cluster-based sensor networks.
|
| This in paper the concept analyzed as, Conserving Battery power in sensor network is an important aspect , to achieve this nodes which are ideal can be put to sleep so that the energy can be used only those nodes which are active [2] . Three scheduling schemes can be used, which are Balanced-energy scheduling scheme (BS), Randomized scheduling scheme (RS), Distance Based scheme (DS). |
| Randomized Scheduling scheme (RS) selects the nodes randomly, which are ideal and puts them to sleep. Distance based scheduling scheme (DS) selects the ideal nodes with respect to the distance of those nodes from the cluster head. Balance-energy scheduling scheme maintains the average energy consumption of all the nodes in the cluster to be same. The BS is as same as DS. The mechanism used to put the ideal nodes to sleep has to be aware of putting only the ideal nodes and not the nodes which are active. |
| Timer will be provided to those nodes which are put to sleep which will consume very low energy in order to keep track of the time duration of the sleeping nodes. |
B. Paper Title: Routing Techniques in Wireless Sensor Networks: A Survey
|
| This paper enhances the major issue in Wireless Sensor Network is Energy consumption which would reduces the lifetime of the network [7]. Since the entire sensor nodes are battery powered, certain steps should be taken to conserve the battery power. Clustering could reduce the energy consumption to some extent. |
| Another method to reduce the energy-consumption is using Routing techniques. The data sensed by the sensor nodes are routed to the base station by some strategy which will reduce the energy consumption to a great extent. Routing in Wireless Sensor Network has three classification and they are |
| • Flat-based routing - all the nodes have equal functionality in the network |
| • Hierarchical-based routing - nodes have different functionality in the network |
| • Location-based routing - position of the nodes in the network decides the functionality. |
| In all the above routing techniques the best path that consumes less energy for the data transmission than any other path in the network is found and data is sent through it. If any node in the founded path is damaged or failed then the routing algorithm itself should accommodate a new path to the base station. The main objective is reducing the energy consumption of the nodes in the network. But the data delivery is not compromised. |
C. Paper Title: Secure Routing In Wireless Sensor Networks: Attacks And Countermeasures
|
| Many routing protocols have been proposed to reduce the energy consumption in the network. But none of them had concerned with the security issues in the wireless sensor network [9]. If a Wireless sensor network is attacked, then it would cause a serious loss than any other network. |
| The two classes of attacks against the sensor networks are sinkholes and Hello floods. |
| • Sinkhole Attack – It compromises a node in the network, attracts the neighboring nodes and makes every data to go through it with respect to the routing algorithm. |
| • Countermeasure – Geographic protocol is used to avoid sinkhole attack. This protocol uses the localized interaction and information to construct a topology and also avoid the initiation from the base station. |
| • Hello Flood attack – An attacker outside the network who has large transmission power may send a HELLO packet to every node in the network and them to believe that it is within the network. So, attacker can easily steal the data. |
| Countermeasure - Each node is provided with an ID. And during data transmission each node should authenticate its neighboring node using Identity verification protocol to avoid Hello Flood attack. Multipath protocol can be used to avoid compromised nodes. In this protocol the data is routed over ‘n’ paths and the nodes in it are disjoint. |
D. Paper Title: A Survey of Security Issues in Wireless Sensor Networks
|
| This paper analyzes the efficiency of the Wireless sensor networks which are mainly used for military purpose for send and receive the code or message [3] . It rectifies the open research issues for direction on security in WSNs. Secure routing protocols are be considered in key distribution the node sends the message from one node to base station. Aggregation of sensor data is to be secured. It produce less important for low level data to save energy level and produce high level security for more sensitive data. |
| The main purpose of security requirements is to identify the information and resource from attacks and misbehavior. Symmetric key cryptography is power consumption in sensor nodes. Open research issues are high speed and low energy cost. In this efficient and flexible key distribution are to be design. There are many routing techniques are been designed for WSNs. Some networks are been design security as a goal. Wireless sensor network are VULNERABLE to many kind of attack in secure routing protocols. |
| Secure routing is a ad hoc network similar to sensor network. It depends on appropriate key management scheme in WSNs. Data aggregation is mainly for WSNs. The nodes are been provide by pair wise key and other node are in multiple hops. The cluster head collect all the information and send it to the base station as they required. Sensor nodes are constrained by less energy. |
EXISTING SYSTEM
|
| In the current system the functionality is that they have used a single cluster for overall system. So that the formations of nodes are in hierarchical and for this they used LEECH protocol. The main drawback of this system is that reduces the energy level and it rotates randomly, dynamically and periodically because of this there may cause of misusing of data`s and it rearrange the cluster and link. Node to node trust is not adequate and also the pair wise key is one of the problems in the transformation. |
PROPOSED SYSTEM
|
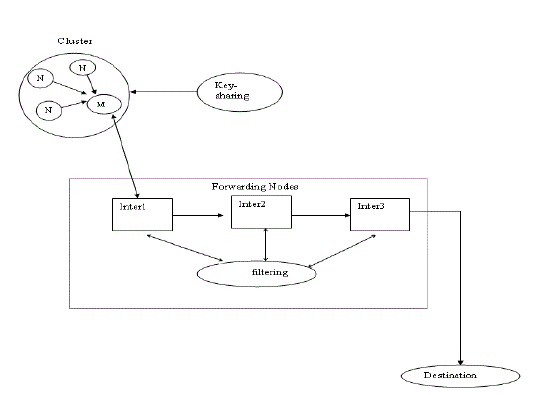
| In the proposed system, the main alter is the protocol, we use the EEDC protocol in which it is mainly used in the wireless Sensor Network for the transmission in the multipath environment. |
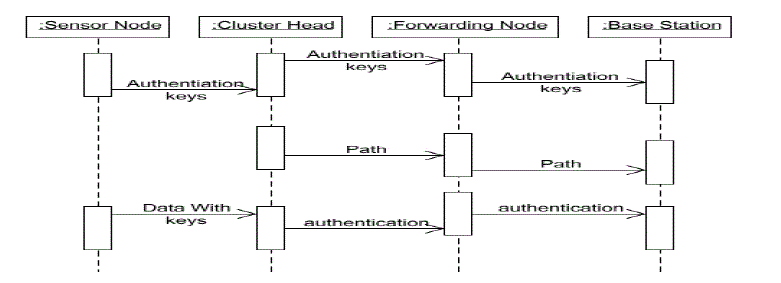
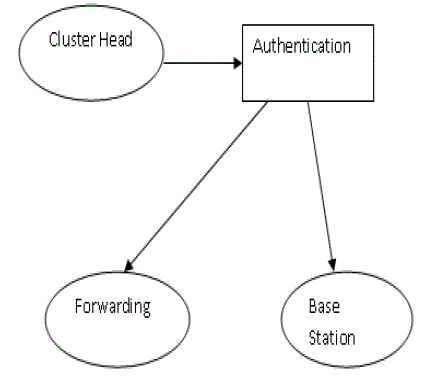
| And the security used is the Digital Signature in two ways as explain in the abstract those methods follows the instruction as the name as identity so that the level of security is high and also the communication and computational problem is resolved. |
| Every node created by the cluster head is analyzed, to the base station for the authentication and the transfer of node can be done by means of the mobility of the sensor head. This can be analyzed by means of various levels of authentication and the level of transparency. Thus when compare to the existing system here we analyzed that the efficiency of various nodes in the cluster will be available in case of the authentication when processed in the transfer of the message in multi cluster environment. |
EXPRIEMENTAL RESULT
|
| The result shown the overall performance of the proposed system the analyses can be found that the cluster region formed is to be a node and the access point and the notification can be formed in the mobility space and for the node formation the distance is to be mentioned in a practical way. The levels of the experimental process are given below. It shows the complete analysis of the proposed method. |
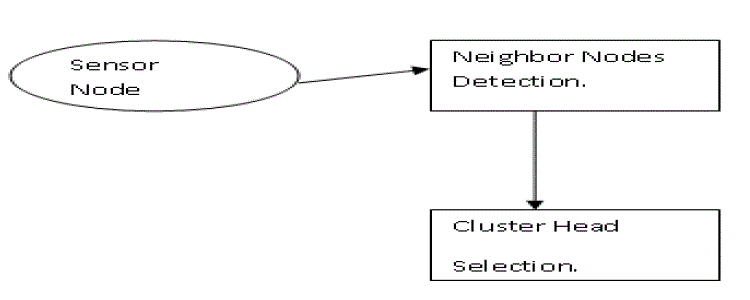
| The sensor node can be also identified for the detection it will be aware of the attacker side process. |
| By the Formation of the cluster region the data start transform from one node to another by means of analyzing the transfer rate and the mobility of the sensor. If any change in access level end then it is to be found that the attacker is sending and won’t accept the data inside the cluster. This is to analyses the level of security. |
CONCLUSION
|
| We first analyzed the data transmission issues and the security issues in CWSNs. Then the absence of the symmetric key management for secure data transmission has been discussed. Then, we accessed two secure and efficient data transmission protocols for CWSNs, they are SET-IBS and SET-IBOOS and the feasibility is also analyzed again the routing mechanism. Finally, the comparison in the calculation and results shows that the proposed protocols have better performance than the existing secure protocols for CWSNs. With respect to both computation and communication costs the system efficiency is moderately good. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
| |
References
|
- Huang Lu, Jie Li and Mohsen Guizani “Secure and Efficient Data Transmission for Cluster-Based Wireless Sensor Networks”Ieee Transactions On Parallel And Distributed Systems, Vol. 25, No. 3, March 2014.
- Deng, Jing; Han, Yunghsiang S.; Heinzelman, Wendi B.; and Varshney, Pramod K., "Balanced energy sleep scheduling scheme for high density cluster-based sensor networks" (2004). Electrical Engineering and Computer Science. Paper 102.
- Y. Wang, G. Attebury, and B. Ramamurthy, “A Survey of Security Issues in Wireless Sensor Networks,” IEEECommun. Surveys Tuts., vol. 8, no.2, pp. 2–23, 2006.
- A. Abbasi and M. Younis, “A survey on clustering algorithms for wireless sensor networks,” Comput. Commun., vol. 30, no. 14-15, pp. 2826–2841, 2007.
- W. Heinzelman, A. Chandrakasan, and H. Balakrishnan, “An Application-Specific Protocol Architecture for Wireless Microsensor Networks,” IEEE Trans. Wireless Commun., vol. 1, no. 4, pp. 660–670, 2002.
- Mohamed Younis, Moustafa Youssef, KhaledArisha, “Energy-Aware Routing in Cluster-Based Sensor Networks”.
- Jamal N. Al-Karaki, The Hashemite University Ahmed E. Kamal, Iowa State University “Routing Techniques In Wireless Sensor Networks: A Survey”, , 1536-1284/04/$20.00 © 2004 IEEE IEEE Wireless Communications, December 2004
- K. Pradeepa, W. R. Anne, and S. Duraisamy, “Design and Implementation Issues of Clustering in Wireless Sensor Networks,” Int. J. Comput. Applications, vol. 47, no. 11, pp. 23–28, 2012.
- Chris Karlof , David Wagner., “Secure routing in wireless sensor networks: attacks and countermeasures,” 1570-8705/$ - see front matter _ 2003 Elsevier.
- R.Shanmugapriya,” Secure Transmission Approach for Multi Cluster Wireless Sensor Network”, conference publication.
- P. Banerjee, D. Jacobson, and S. Lahiri, “Security and performance analysis of a secure clustering protocol for sensor networks,” in Proc. IEEE NCA, 2007, pp. 145–152.
- K. Zhang, C. Wang, and C. Wang, “A Secure Routing Protocol for Cluster-Based Wireless Sensor Networks Using Group Key Management,” in Proc. WiCOM, 2008, pp. 1–5.
|