ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
| Somnath S.Berad ME Electronics Engineering, Amrutvahini College of Engineering Sangamner (MS), India |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
This research aims to generate key for network security to long term evolution network/radio network. In this project a hardware implementation of ZUC Stream cipher is designed. ZUC is a stream cipher that forms the heart to the 3GPP confidentiality algorithm 128-EEA3 and the 3GPP integrity algorithm 128-EIA3, offer in reliable security services in Long Term Evolution networks (LTE). A detailed hardware implementation is shown in order to reach satisfactory performance results in LTE systems. The design was coded using VHDL language and for the hardware implementation, a XILINX Spartan-3FPGA was used. Experimental results in terms of performance and hardware resources are shown.
Keywords |
| Long Term Evolution networks security, Zuc stream cipher, Hardware implementation, FPGA. |
INTRODUCTION |
| Protection and hiding of valuable information has a very old history [1] where cryptology has developed over the centuries from an art, in which only few were ingenious into a science with well established foundations. There are several goals which security professionals desire to achieve through the use of cryptography. These goals include condentiality, data integrity, entity authentication, non-repudiation and data origin authentication [2]. Cryptology encompasses two related fields: cryptography and cryptanalysis. Cryptography can be denied as the study of mathematical techniques to ensure various aspects of information security as those mentioned. On the other hand, cryptanalysis can be defined as the study of techniques to analyze, and break, information security services by targeting, specially, the underlying cryptographic algorithms. Now days there are many stream cipher algorithms proposed in academia and industry. Stream cipher is an important class of symmetric encryption algorithms [3], whats more stream ciphers do not suffer from the error propagation, because each bit is independently encrypted/decrypted from any other. Compared with block cipher, they are generally much faster than block cipher and they have greater software effciency, due to these features stream ciphers have been the choice for several communication protocols, especially wireless ones [4]. Block ciphers are memoryless algorithms that permute N-bit blocks of plain text data under the influence of the secret key and generate N-bit blocks of encrypted data, compared with the block cipher, stream ciphers contain internal states and typically operate serially by generating a stream of pseudo random key bits, the key stream (stream ciphers are also called key stream generators). The key stream is then bit-1wise XORed with the data to encrypt/decrypt .Cipher systems are usually subdivided into block ciphers and stream ciphers. Block ciphers tend to simultaneously encrypt groups of characters, whereas stream ciphers operate on individual characters of a plain text message one at a time [11]. The new stream cipher ZUC is a word-oriented stream cipher [7]. It takes a 128-bit initial key and a 128-bit initial vector as input, and outputs a key stream of 32-bit words. |
| This key stream can be used to encrypt the plaintext. The execution of ZUC has two stages: key initialization stage and working stage. In the frst stage, a key initialization is performed, i.e. the cipher is clocked without producing output. The second stage is working stage. In this study, the new architecture is proposed to generate 32-bit key per clock cycle. ZUC has three logical layers. The top layer is a linear feedback shift register (LFSR) of 16 stages, the middle layer is bit-reorganization, and the bottom layer is a nonlinear function F. Long Term Evolution (LTE) is the nextgeneration network beyond 3G that enable fixed to mobile migrations of Internet applications such as Voice over IP (VoIP), video streaming, music downloading, mobile TV and many others. LTE networks will also provide the capacity to support an explosion in demand for connectivity from a new generation of consumer devices tailored to those new mobile applications. The current radio interface protection algorithms for LTE,128-EEA1 for confidentiality and 128-EIA1 for integrity have been designed by SAGE/ETSI Security Algorithms Group of Experts[4] . 128-EEA1 and 128-EIA1 are based on SNOW3G stream cipher. Also, the 3rd Generation Partnership Project (3GPP), together with the GSM Association specifies a second set of algorithms, 128-EEA2 and 128-EIA2 [3], which are based on AES block cipher [4]. |
| Finally, 3GPP with GSM association specifies a third set of algorithms for confidentiality and integrity the 128- EEA3 and 128-EIA3 respectively. Both ciphers are based on ZUC stream cipher. The most serious reason for these new ciphers is that LTE will be used in many countries worldwide. But Chinese regulation will not allow those algorithms to be used in China, because they were not designed in China. However, ZUC has been designed in China, and thus that it can be used in China. In this paper an efficient FPGA implementation of ZUC stream cipher is presented. Minimize the registers and Look-Up Tables in the design. Our FPGA hardware implementation covers 385 slices and achieves 2.08 Gbps throughput in maximum frequency operation. Comparisons with other stream ciphers implementations are provided. The comparisons prove that the proposed system is efficient in terms of throughput. The aim of the work is to ascertain that the ZUC stream cipher can operate on a recent hardware device for efficient use on LTE networks. Compared with block ciphers, stream ciphers are more efficient when implemented in hardware environment, like Field Programmable Gate Array (FPGA). In this paper, we propose three optimized schemes in the FPGA implementation of a novel and recently proposed stream cipher, ZUC, which is a new cryptographic algorithm proposed for inclusion in the 4G mobile standard called LTE (Long Term Evolution). |
| Aim |
| Aim and contribution of this project are summarized as following. |
| 1. The aim of Project is to gives the network security to long term evolution network/radio network. |
| 2. The aim of the work is to ascertain that the ZUC stream cipher can operate on a recent hardware device for efficient use on LTE network. |
SYSTEM DESIGN |
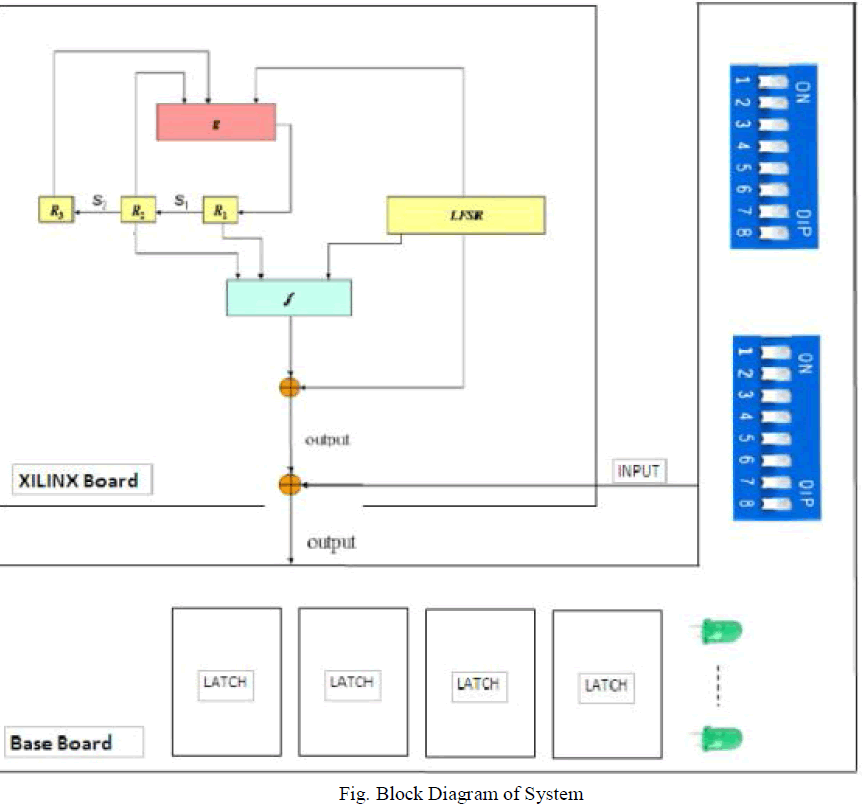 |
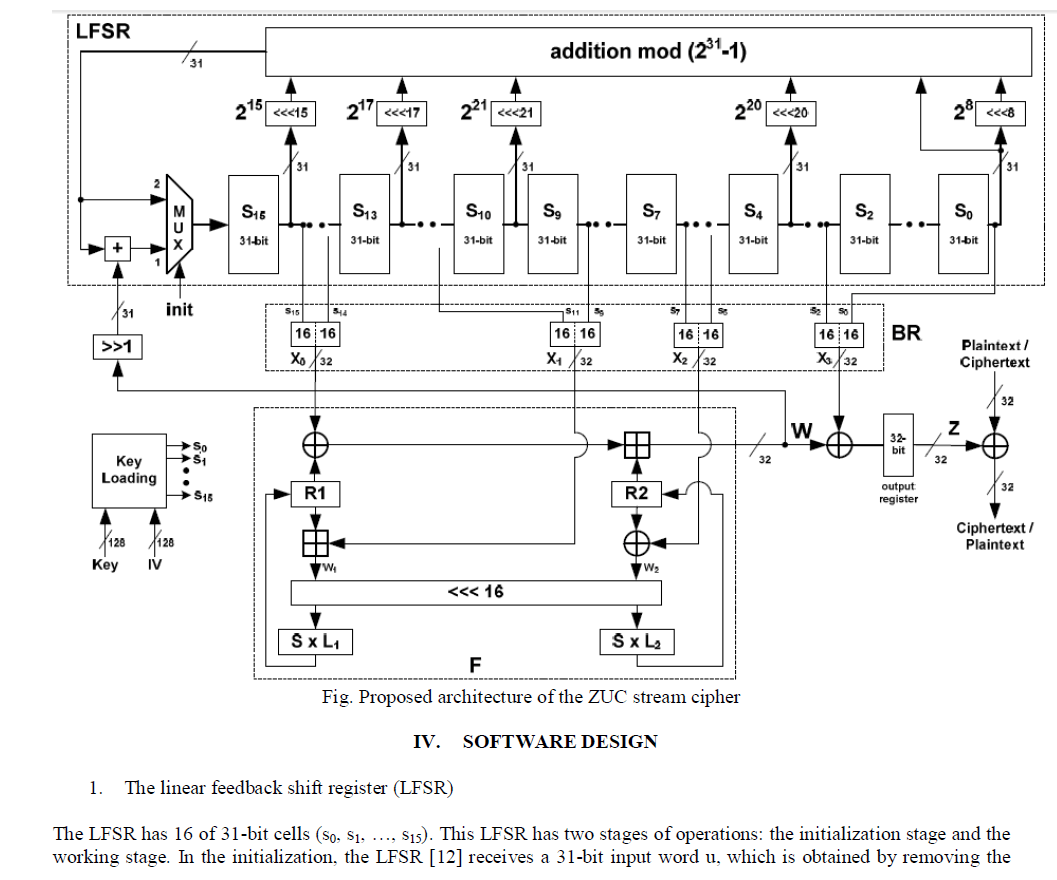
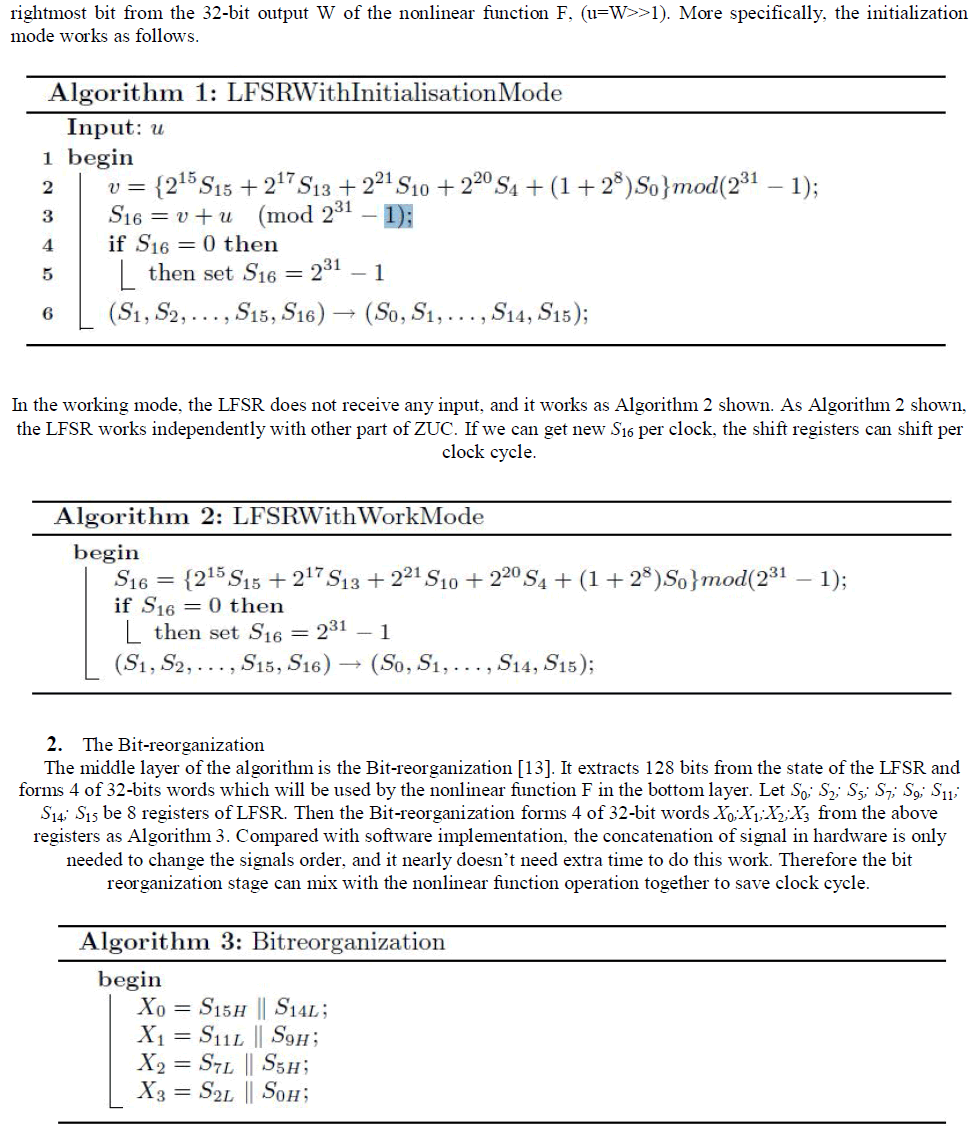
| ZUC is a word-oriented stream cipher [8] that takes a 128-bit Key and a 128-bit Initial Vector (IV) as input, and outputs a key stream of 32-bit words. ZUC has three logical layers. The top layer is a Linear Feedback Shift Register (LFSR) of 16 stages, the middle layer is for bit reorganization (BR), and the bottom layer is a nonlinear function F. The LFSR has 16 of 31-bit cells (s0 , s1 , , s15 ). This LFSR has two stages operations: the initialization stage and the working stage. In the initialization, the LFSR receives a 31-bit input word u, which is obtained by removing the rightmost bit from the 32-bit output W of the nonlinear function F The bit-reorganization [9] layer extracts 128-bit 16 from the cells of the LFSR and forms 4 of 32-bit words, where the first three will be used by the nonlinear function F in the bottom layer, and the last word will be involved in producing the key stream [15]. For the cipher operation firstly the key loading procedure expands the initial key and the initial vector into 16 of 31-bit integers as the initial state of the LFSR and then two stages are executed; initialization stage and working stage. In the first stage, a Key/IV initialization is performed and the cipher is clocked without producing output. The second stage is a working stage in which every clock cycle produces a 32- bit word of output. |
ARCHITECTURE OF ZUC STREM CIPHER |
| The aim of the work is to ascertain that the ZUC stream [10] cipher can operate on a recent hardware device for efficient use on LTE networks. The proposed hardware implementation of the ZUC stream cipher is illustrated in Fig. The proposed system has as main I/O interfaces a 32-bit plaintext/ciphertext input and a 32-bit ciphertext/plaintext output. In addition it has two inputs, a 128-bit secret key, Key, and 128-bit initialization value, IV. Our system supports, the initialization stage, the working stage and the key stream producing stage. The configuration of the proposed hardware system supports all stages of operation. The main parts of the proposed architecture of ZUC are the Key Loading, the Linear Feedback Shift Register (LFSR)[11].the BR (bit-reorganization) and the configuration according the cipher operation scenario (initialization or working stage). Also, one more adder mod (231 -1) is needed with its result used as first input of the multiplexer. In the Feedback Logic six additions mod (231 -1) are used. |
 |
 |
 |
CONCLUSIONS |
| 1. A ZUC high-speed hardware architecture is described, which has been implemented by means of an FPGA device. Experimental results prove that the ZUC implementation is a flexible solution for LTE applications. |
| 2. The implementation on FPGA achieves a throughput of 2.08 Gbps at a 65 MHz clock frequency. |
ACKNOWLEDGEMENTS |
| I thank god almighty for guiding me through the project. I would like to thank all those who have contributed to the completion of the project report and helped me with valuable suggestion for improvement. |
References |
|