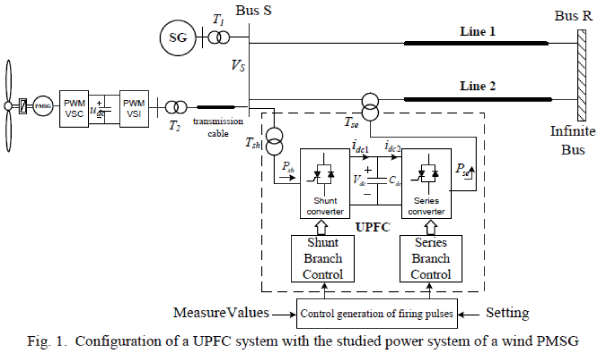
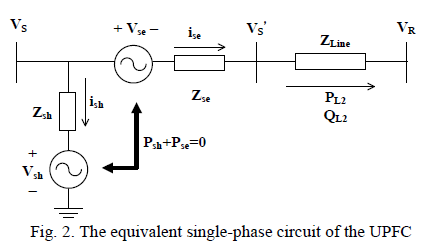
ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
| B. Steffi Diana, S. Vijayakumar |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Data aggregation is a process in which data is collected from the sensor nodes and sent to the base station via cluster heads. Data aggregation schemes are vulnerable to various security attacks. Such Attacks take place compromising at the sensor node and cluster head levels. An adversary node eavesdrops the sensed data, modifies and injects forged data. Security plays a key role in the data aggregation process and the base station needs to confirm data integrity and authenticity. Data aggregation schemes based on privacy homomorphism (PH) provide better security compared with traditional aggregation. In PH based encryption the cluster heads can directly aggregate the cipher texts without decryption. The proposed System is based on privacy homomorphism encryption and uses elliptic curve Cryptography (algorithm) to encrypt the sensed data. And this system deals with transmitting difference data rather than the raw sensed data from sensor node. Compared to the existing aggregation schemes, the differential data transfer achieves more energy efficiency and increase in the packet delivery ratio.
Keywords |
| Data Aggregation, Privacy homomorphism, Data integrity and authenticity. |
INTRODUCTION |
| Wireless sensor networks consist of small nodes that monitor physical and environmental conditions such as temperature, sound, vibration, process the data, and communicate through wireless links [7]. A wireless sensor network consists of a base station or gateway that communicates with a number of wireless sensor nodes by use of a radio link. Once the data is collected by some intermediate node, it is then transmitted to the gateway. Once the data reaches the base-station then it is presented to the system by the gateway connection and processed. |
| As nodes forward the data, they remove node’s redundant sensor information, and combine data at intermediate nodes reduces the overall number of messages, thus reducing communication and increasing the lifetime of the network. |
| Data aggregation mechanisms are proposed to reduce the power consumption of wireless sensor networks. Data aggregation schemes summarize data packets of several sensor nodes so that amount of data transmission is reduced [13]. In data aggregation scheme, a group of sensor nodes collect information from the target region. When the base station request for the data, instead of each node sensing the sensor data the data aggregator, collects the information from the sensor nodes, computes the sum or average, and sends the aggregated data to the base station over a multihop path. Thus data aggregation reduces the number of data transmissions, provides better bandwidth and energy utilization in the network. |
| As the majority of wireless sensor network applications require a certain level of security, security protocols require sensor nodes to encrypt and authenticate any sensed data prior to its transmission and the data has to be decrypted by the base station. Moreover, data aggregation alters the sensor data and therefore it is a challenging task to provide data encryption and authentication along with the data aggregation. |
| The objective of the paper is to provide solution for the security attacks taking place compromising sensor node and aggregator level. Data aggregation schemes are vulnerable to various security attacks. Secure communication requires sensor nodes to encrypt any sensed data prior to the transmission and to have end to end security with the data decrypted only at the base station. So the data aggregation and security protocol must be designed together so that data aggregation can be performed without compromising security. |
II. RELATED WORKS |
| Numerous secure data aggregation schemes have been proposed and designed for different security requirements. A number of data aggregation schemes have been proposed based on the privacy homomorphism. In privacy homomorphism based encryption scheme [8] allows direct computation on encrypted data and affords end to end concealment of data. |
| In secure hierarchical data aggregation algorithm [6] achieves end to end security using an efficient public key cryptosystem. It employs homomorphism encryption and aggregate digital signatures for the end to end confidentiality and data integrity. It does not require a separate integrity verification phase and uses aggregate digital signature to relieve the extra communication cost for the network. In Security-enhanced Energy-efficient Data Aggregation [9] supports hop to hop data authentication. It uses homomorphism public key encryption into Message authentication code to offer an end to end concealment of the data and provides hop to hop verification. This method exploits homomorphism encryption to gain higher security and less computational complexity. On other hand a secured data aggregation protocol [1] attempt to detect false data injection during the data aggregation and thus to find the adversary node. Each sensor node reports the deviation to the base station and authenticates an attestation message with the attached MAC. The base station detects the attack if it receives sufficient number of attestation messages pointing at the attacking node (decision by majority). In concealed data aggregation scheme for multiple applications [7] designed for application specific environment. The base station extracts application-specific data from aggregated cipher text. It reduces the impact of compromising attacks in single application environments and degrades the damage from unauthorized aggregations. The cipher texts from different applications can be encapsulated into one cipher text and the base station can extract application specific plaintexts through the corresponding secret keys. Then PEPPDA [5] technique guarantees the privacy, authenticity and freshness of sensed data. It also promises the accuracy and confidentiality of the aggregated data without introducing a significant overhead on the battery limited sensors. |
III. PRELIMINARIES |
A. Network Model |
| A wireless sensor network (WSN) is controlled by a base station (BS). The base station has bandwidth efficiency, good computing capability, adequate memory, and stable power to support the cryptographic and routing requirements of the whole wireless sensor network. Besides the base station, sensors (SNs) which are small and low cost limited on computation, storage, and communication capability. They are deployed to sense and gather responsible results for the base station. |
| Generally, all sensors in a wireless sensor network may be divided into several clusters. Each cluster consists of number of cluster members. Among them one is selected as cluster head. A cluster-based wireless sensor network has several advantages such as efficient energy management, better scalability of medium access control and routing. The cluster head (CH) is responsible for collecting and aggregating sensing data from sensors within the same cluster. A cluster head then sends the aggregation results to the base station. In a homogeneous wireless sensor network, cluster heads act as normal sensors. |
B. Attack Model |
| 1) Without compromising any Sensor node or Cluster head: An adversary can only eavesdrop on packets in the air, so the attacker can inject the forged messages with this public information [2]. |
| 2) Compromising Sensor node: After compromising a sensor node, an adversary can acquire secrets such as encryption/ decryption keys. Then, an adversary can acquire sensing data and packets passed through the captured sensor node or impersonate this compromised sensor to forge malicious data. |
| 3) Compromising Cluster head: After compromising a cluster head, an adversary can obtain the secrets and the adversary can decrypt the cipher text of sensing data sent by its cluster members and generate forged aggregation results. |
IV. FRAMEWORK |
| The proposed protocol executes for two sessions, reference data transfer session and subsequent data transfer session. The reference data transfer session transfers the reference data from sensor nodes to Base station and performs verification of it in the Base station [4]. |
| In the subsequent data transfer session, the differential data is calculated between the reference data and sensing data. It is transferred from sensor nodes to Base station so that base station can recover the individual sensed data and can check the integrity all sensing data. |
| The proposed approach provides more energy efficiency by transmitting and aggregating the differential data instead of raw data. The original data is recovered from the differential data is by converting the differential data to raw data using reference data. The reduced amount of data transfer from the nodes conserves energy of the sensor nodes as well as cluster head because the cluster head wants to process small amounts of data. The framework of protocol is shown in fig. 1. It consists of five phases such as Setup phase, Initial phase, Aggregate phase, Recovery phase, and Verify phase. |
| The first phase happens only once and it is common to both the sessions. The further four phases execute first for the reference data transfer session until a successful reference data for all nodes reaches at base station and then it repeats for subsequent data transfer sessions until a false aggregated result reach at the base station. When base station found that the aggregation result reached at the base station is false, it concludes that the data is changed during transmission or reference data kept in the node changed by because of node compromise attack. |
 |
| To demonstrate the proposed protocol, we consider cluster 1 (in fig. 2), here SNw is chosen as CH of cluster 1 and the remaining sensor nodes (SN1…SNw-1) is considered as cluster members. Both cluster head and cluster members perform sensing and the CH’s performs data aggregation. |
| In the setup phase, the Base station uses this phase to generate and install all necessary secrets for each sensor node and for them also |
| Base Station generates public key, private key for every sensor nodes (SN1….SNw). |
 |
| Base Station loads public key of Base Station (PUBS), private key of sensor node (PRSNi), hash function to every sensor node. |
| Base Station keeps public key of every sensor node as corresponds to the node ID, public key of Base Station, hash function in them. |
| In the initial phase, the sensor node executes this phase for transferring cipher text. The encrypted text is appended to the node id with the digital signature as a pair to Cluster head. |
| In aggregate phase, the Cluster head (CHi) uses this phase to aggregate the cipher texts, signatures coming from its cluster members and to generate aggregated cipher text and aggregated signature without performing any decryptions at the cluster head (CHi).This is achieved because of additive Privacy Homomorphism property of the encryption algorithm. So this phase saves the energy spend for the decryptions and encryption at the aggregator node and mitigate the aggregator node compromise. Thus, the system provides an end to end concealment to the data. |
| In the recovery phase, the base station recovers each individual sensing data from the aggregated cipher text reached at the Base station. Thereby Base station overcomes the limitations of it on the aggregation functions and can perform any operations on the recovered data after verification. |
| In the recovery phase, the base station recovers each individual sensing data from the aggregated cipher text reached at the Base station. Thereby Base station overcomes the limitations of it on the aggregation functions and can perform any operations on the recovered data after verification. |
 |
A. Reference and Subsequent Data Transfer Session |
| The protocol executes the reference data transfer session and then the subsequent data transfer session. The reference session transfers the sensing data value to base station and this sensing data is verified in the Base station. The Base station keep the reference data as corresponds to the node ID for recovery of original sensed data in differential data transmission session. |
| Then the following in the subsequent data transfer session difference data is calculated between raw sensor measurements and reference data and sent to the base station. Working procedure is explained below. |
1) The Initial phase: |
| a. For reference session sensor nodes (SN1….SNw) take the raw measurement value as reference data and keep in them. |
| Rfi =di (3) |
| And in the subsequent session sensor nodes (SN1….SNw) compute the differential data by |
| Where di is the original sensed data of node i, |
| Rfi is the reference data of node i and |
| ddi is the differential sensed data of node i. |
| • If it is negative, ddi = di− Rfi and append a negative sign to its node ID. |
| • If it is zero, the corresponding sensor node (SNi) does not go for further steps. |
 |
 |
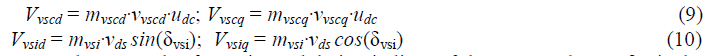 |
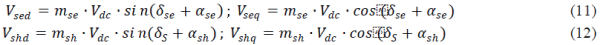 |
 |
 |
IV. CONCLUSIONS AND FUTURE WORK |
| Thus the proposed technique recovers sensing data from the aggregated result and verifies data integrity and authenticity. It improves the network lifetime by achieving energy and bandwidth efficiency while preserving security requirements such as confidentiality, data authentication, and integrity. It reduces the energy consumption by transferring differential data rather than raw data from nodes so that the cluster head also wants to process small amounts of bits. Thereby it gives energy relief to sensor nodes as well as the cluster head. |
| Our future works aims at integrating the proposed technique with the network layer security primitive ContikiSec that uses symmetric key encryption algorithms that are available in the Contiki operating system. |