ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Chitra G.Desai1,Rupali Bhakkad2 and Sonal Sarnaik2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Cryptography is the study of “Mathematical Systems” involving two kinds of security protocols: Privacy and Authentication. The mathematical concepts from the branch of number theory known as Modular arithmetic, Quadratic residue are significantly useful in cryptography. Cryptography Deals with large number integers i.e. integers as big as hundred digits and more. In such situation identifying whether an integer “a” is quadratic residue modulo “p” where p is Prime can be achieved using Legendre and Jacobi Symbol. This paper introduces to the mathematical concepts of Quadratic Residue, Fermat's little theorem, Euler’s criterion and Legendre and Jacobi symbol. However it has been observed that Jacobi symbol in case of some example fails to give correct result and therefore the Limitation for predicting the quadratic residue.
Keywords |
| Cryptography, Quadratic residue, Legendre Jacobi symbol |
INTRODUCTION |
| Cryptography is the study of exchange of information between sender and receiver over an insecure channel is such a way that the opponent (any third user) cannot understand what is being said [2][13][18].The actual information sender wants to send is called as “Plaintext”, sender converts this plaintext in “Cipher text” (by using different techniques) by applying Key to it. This cipher text is very difficult to read, need mathematical knowledge to read it. At receiver this cipher text gets converted into plaintext by applying key (same or different) to it, so receiver can read it. The conversion from plaintext to cipher text is called encryption and from cipher text to plaintext is called as decryption[13][20]. |
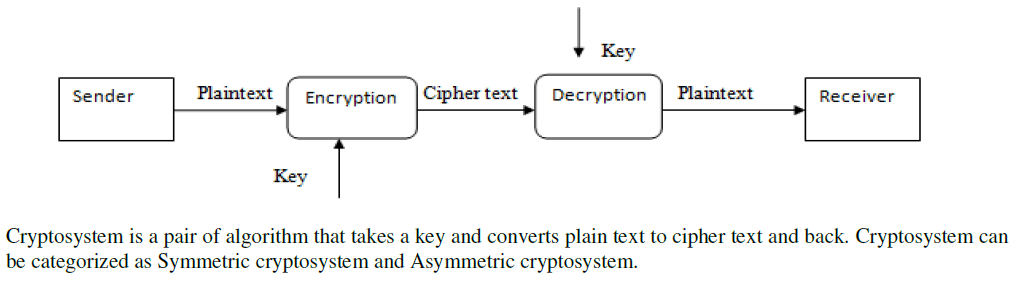 |
| Symmetric cryptosystem uses a shared secret key in the encryption process as well as in decryption process .for example DES (Data Encryption Standard)[12][13][18][20], AES(Advance Encryption Standard) [8][18][20],Blowfish[1]. It has few limitations such as key distribution, compromised KDC (Key Distribution Center), random number generation, placement of encryption function. |
| Asymmetric cryptosystem uses public key for encryption and a private key for decryption, there is no need for a shared secrete [3][20]. Examples of this are Diffie-Hellman [14], RSA [7][12] and Elgamal [5]. |
| All of the techniques used here are based on mathematical concepts of number theory and discrete logarithms. Particularly in number theory most important is integer factorization, modular arithmetic’s. This paper introduces to the mathematical concepts of Quadratic residue, Fermat's little theorem, Euler’s criterion and Legendre and Jacobi symbol. However it has been observed that Jacobi Symbol in case of some example fails to give correct result and therefore the limitation for predicting the quadratic residue. |
FERMAT'S LITTLE THEOREM. |
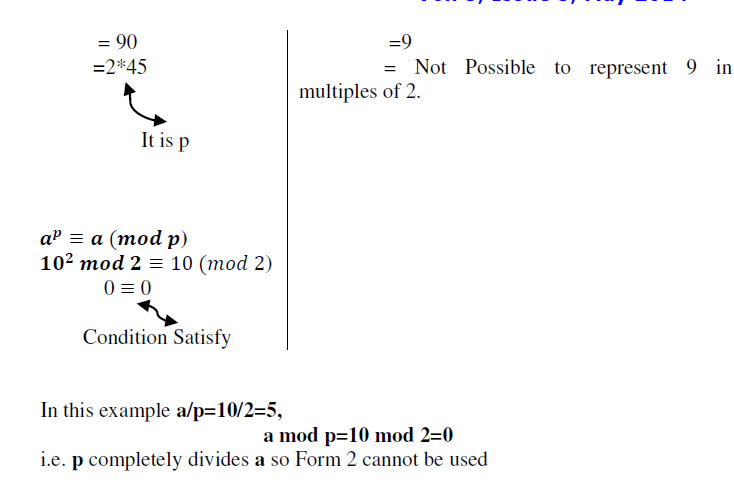
| Fermat’s little theorem works in two forms. First form is applicable to all but second form has limitation. |
Form 1:- |
 |
 |
QUADRATIC RESIDUE: |
| Let a ∈ N and p be an odd prime number such that gcd(p,a) = 1. Then a called a quadratic residue modulo p if a is a perfect square modulo p[4][6][9][13][15][16] i.e. there is a number y such that, |
 |
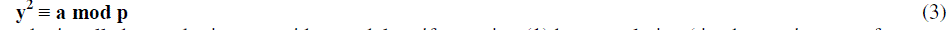 |
| So, we find square of all the numbers in z5 set and find each square modulo 5,here we find that there is no such perfect square exist. Here a=2 and p=5 and we conclude that a is quadratic non residue modulo p. |
| Finding whether a is quadratic residue modulo p becomes a tedious task for large integers. It is therefore necessary that we first identify whether there exists such y which satisfies y2 = a mod p |
| This can be achieved through Legendre and Jacobi symbol. However, we need to first understand Euler’s criterion as discussed in next section. |
EULER’S CRITERION |
 |
LEGENDRE SYMBOL. |
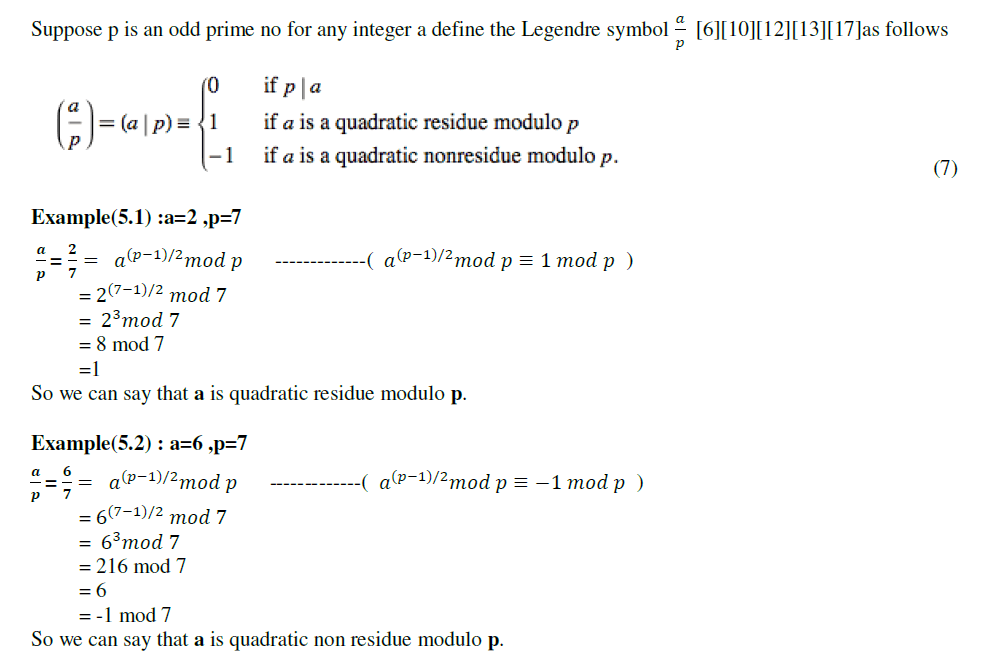 |
JACOBI SYMBOL. |
| It is generalization of Legendre symbol [6][10][11][13].suppose n is and odd positive integer , and the prime power factorization of n is , |
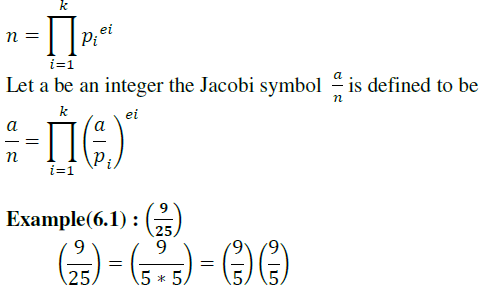 |
 |
 |
CONCLUSION |
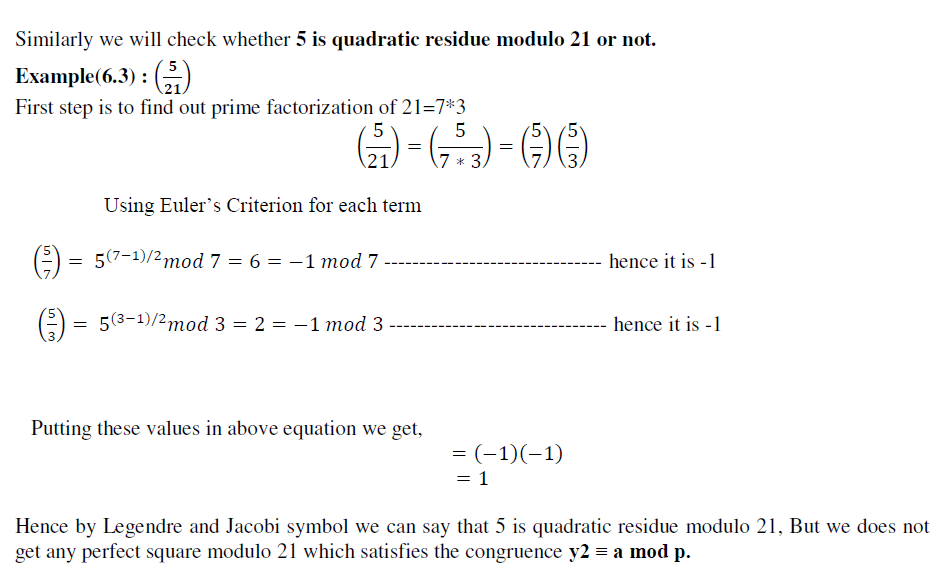
| Cryptography has been built over the mathematical concept to construct hard problems to increase the efficiency of cryptographic algorithms. Quadratic residue is one such important concept used in cryptography. In this paper we have demonstrated how we can identify where an integer a is quadratic residue modulo p (p is prime) using Legendre and Jacobi symbol. Also with the help of example we have shown our observation that the results of Legendre Jacobi Symbol in some cases do not agree with the actual expected results of quadratic residuity. |