ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
K. Somu1, Mr. U.Gowri Sankar2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
In this project, I concentrate on critical event monitoring occur in wireless sensor networks (WSNs), most of the time small number of packets get transmit on network. When critical event occurs, an alarm message should be broadcast to the entire network as soon as possible. To elongate the network lifetime, in WSNs some sleep scheduling methods are always employed. Resulting in significant delay broadcasting, especially in large scale WSNs. In this project, I propose a novel sleep scheduling method to reduce the delay of alarm broadcasting from any sensor node in WSNs. I design two determined traffic paths for the transmission of alarm message, and level-by-level based wake-up pattern according to the paths, respectively. An alarm is quickly transmitted along one of the traffic paths to a center node, when a critical event occurs and then it is immediately broadcast by the center node along another path without any collision.
I. INTRODUCTION |
| WIRELESS SENSOR NETWORKS |
| Wireless Sensor Network (WSN) is a collection of spatially deployed wireless sensors by which to monitor various changes of environmental conditions (e.g., forest fire, air pollutant concentration, and object moving) in a collaborative manner without relying on any underlying infrastructure support. Recently, a number of research efforts have been made to develop sensor hardware and network architectures in order to effectively deploy WSNs for a variety of applications. |
| Due to a wide diversity of WSN application requirements, however, a general-purpose WSN design cannot fulfill the needs of all applications. Many network parameters such as sensing range, transmission range, and node density have to be carefully considered at the network design stage, according to specific applications. To achieve this, it is critical to capture the impacts of network parameters on network performance with respect to application specifications. Wireless sensor networks are deployed to monitor the sensing field and gather information from it. |
| Traditionally, two approaches can be adopted to accomplish the data collection task: through direct communication, and through multi-hop forwarding. |
| i) Sensor nodes upload data directly to the sink through one-hop wireless communication, which may result in long communication distances and degrade the energy efficiency of sensor nodes. |
| ii) On the other hand, with multi-hop forwarding, data are reported to the sink through multiple relays, and the communication distance is reduced. |
| NATURES OF ROUTING |
| Since a distributed network has multiple nodes and services many messages, and each node is a shared resource, many decisions must be made. There may be multiple paths from the source to the destination. Therefore, message routing is an important topic. |
| The main performance measures affected by the routing scheme are throughput and average packet delay (quality of service). Routing schemes should also avoid both deadlock and live lock. |
| Routing methods can be fixed (i.e. pre-planned), adaptive, centralized, distributed, broadcast, etc. Perhaps the simplest routing scheme is the token ring. Here, a simple topology and a straightforward fixed protocol result in very good reliability and precomputable QoS. A token passes continuously around a ring topology. When a node desires to transmit, it captures the token and attaches the message. |
| As the token passes, the destination reads the header, and captures the message. Which is then received by the original source node? Then, the token is released and can accept further messages. Though this scheme is very reliable. The token must pass once around the ring for each message. |
| Routing Protocol: |
| Routing has two main functions: route discovery and packet forwarding. The former is concerned with discovering routes between nodes, whereas the latter is about sending data packets through the previously discovered routes. One can distinguish proactive and reactive protocols. Another type of classification distinguishes routing table based protocols (e.g., DSDV) and source routing protocols (e.g., DSR). |
| Proactive Routing Protocols (Table-driven) |
| i) Nodes exchange routing information periodically in order to maintain consistent and accurate information. |
| ii) To transmit data to a destination, path can be computed rapidly based on the updated information available in the routing table. |
| iii) The disadvantage of using a proactive protocol is high overhead needed to dynamic topology that might require a large number of routing updates. |
| iv) Each node maintains a routing table, with an entry for each possible destination address, next hop on the shortest path to that destination, shortest known distance to this destination sequence number that is created by the destination itself. |
| Reactive Routing Protocols (On-demand) |
| i) Route discovery mechanism is initiated only when a node does not know the path to a destination it wants to communicate with. |
| ii) In case of mobile ad hoc network, reactive routing protocols have been demonstrated to perform better with significantly lower changes that may occur in node connectivity, and yet are able to reduce/eliminate routing overhead in periods or areas of the network in which changes are less frequent. |
| iii) A reactive routing has two main operations. Route discovery (usually broadcasting using a form of controlled flooding) and route maintenance. Various reactive protocols have been proposed in literature such as Ad Hoc On-demand vector (AODV), Dynamic source routing (DSR), |
| iv) Temporary Ordered Routing Algorithm (TORA), etc |
II. PROPOSED SYSTEM |
| I propose a novel sleep scheduling method, which is still based on the level-by-level offset schedule, to achieve low broadcasting delay in a large scale WSN. As the alarm message may be originated by any possible node, I set two phases for the alarm broadcasting It is known that the alarm could be originated by any node which detects a critical event in the WSN. To essentially reduce the broadcasting delay, the proposed scheduling method includes Three phases: |
| i) Any node which detects a critical event sends an alarm packet to the center node along a predetermined path according to level-by-level offset schedule; |
| ii) The center node broadcasts the alarm packet to the entire network also according to level-by-level offset schedule. |
| iii) Local monitoring will be maintained to reduce the critical event. |
| I define the traffic paths from nodes to the center node as uplink and define the traffic path from the center node to other nodes as downlink, respectively. Each node needs to wake up properly for both of the two traffics. Therefore, the proposed scheduling scheme should contain two parts: |
| i) Establish the two traffic paths in the WSN; |
| ii) Calculate the wake-up parameters (e.g., time slot and channel) for all nodes to handle all possible traffics. |
| SENSOR NETWORK SETUP |
| I contribute to a more systematic understanding and treatment of sensor deployment issues. A wireless network that is temporarily installed alongside the actual sensor network during the deployment process. |
| Parameters considered during sensor network formation |
| i) Transmission range: nodes communication depends under transmission range which is placed nearly close to each other thus gets better link. |
| ii) Local information system: Nodes must be grouped under specific feature like battery power, processing capability, bandwidth, memory etc. so according to those, nodes are partitioned using driver methods. |
| iii) Mobility: Mobility refers the node movement prqocedure so need to consider the mobility options with limitation in maximum and minimum speed. |
| According to the critical event monitoring process, sensor network formed under local information system with sleep wake scheduling mechanisms. |
| ROUTING PROTOCOL DESIGN |
| A routing protocol is a protocol that specifies how routers communicate with each other, disseminating information that enables them to select routes between any two nodes on a computer network, the choice of the route being done by routing algorithms. Each router has a prior knowledge only of networks attached to it directly. A routing protocol shares this information first among immediate neighbors, and then throughout the network. This way, routers gain knowledge of the topology of the network. |
| Design a Routing protocol named as ELMP (Energy aware local monitoring protocol), which is going to implement in OSI layer that need to get and deliver the messages from other layers for that make some more changes in supported layers. The routing protocol is implemented in the layered architecture of the GloMoSim simulator. |
| To essentially reduce the broadcasting delay, the proposed scheduling method includes two phases: |
| i) Any node which detects a critical event sends an alarm packet to the center node along a predetermined path according to level-by-level offset schedule; |
| ii) The center node broadcasts the alarm packet to the entire network also according to level-by-level offset. |
| SYSTEM ARCHITECTURE DESIGN |
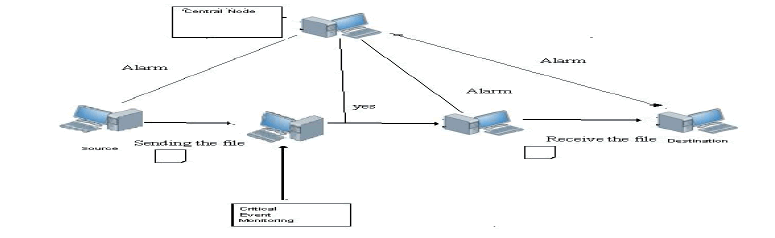 |
| MECHANISMS IMPLEMENTED |
| i) Sleep wake Scheduling |
| ii) Local monitoring |
| Local monitoring: For the critical event monitoring in a WSN, sensor nodes are usually equipped with passive event detection capabilities that allow a node to detect an event even when its wireless communication module is in sleep mode. Upon the detection of an event by the sensor, the radio module of the sensor node is immediately woken up and is ready to send an alarm message.The nodes are maintain in three states to establish Sleep wake scheduling which are |
| i) Active state-Node in routing process |
| ii) Ideal state-Node which are in ready state |
| iii) Sleeping state-Node which is in slow sleeping state by reducing its transmission range wake up once get the wake signal from authorized node |
| ELMP Process |
| The Local Monitoring in Sensor Networks (ELMP) methodology, which consists of a set of mechanisms that significantly reduce the node wake time required for monitoring. ELMP does not need to do anything since a node and its monitoring neighbors will be automatically awakened by the baseline (local boundary) itself. ELMP requires each node to have a passive or a low-power wake-up antenna in addition to the usual antenna. |
| A node that is not involved in network activities such as data forwarding is ordinarily asleep according to the baseline. However, for monitoring purposes, it is awakened on demand by a neighboring node using the wake-up antenna. On-demand sleep-wake protocols use either special purpose low-power wake-up antennas. |
III. PERFORMANCE EVALUATION |
| First, I need to specify the necessary input parameters in the Config.in file as said above. For our simulation procedure, we have been specific about certain parameters as mentioned below to enable hassle free simulation |
| Terrain range – (500,500) |
| Number of nodes – 20 (This is a scalable simulator. Hence number of nodes can be increased at will.) These parameters were adhered to for the whole process of experimentation with the new protocol. |
| The performance of the proposed algorithm is evaluated via glomosim simulator. Performance metrics are utilized in the simulations for performance comparison: |
| i) Packet arrival rate. The ratio of the number of received data packets to the number of total data packets sent by the source. |
| ii) Average end-to-end delay. The average time elapsed for delivering a data packet within a successful transmission. |
| iii) Communication overhead. The average number of transmitted control bytes per second, including both the data packet header and the control packets. |
| iv) Energy consumption. The energy consumption for the entire network, including transmission energy consumption for both the data and control packets. |
IV. IMPLEMENTATION AND RESULTS |
| PARSEC |
| PARSEC (for PARallel Simulation Environment for Complex systems) is a C-based simulation language developed by the Parallel Computing Laboratory at UCLA, for sequential and parallel execution of discrete-event simulation models . It can also be sued as a parallel programming language. |
| PARSEC runs on several platforms, including most recent UNIX variants as well as Windows. PARSEC adopts the process interaction approach to discrete-event simulation. An object (also referred to as a physical process) or set of objects in the physical system is represented by a logical process. Interactions among physical processes (events) are modeled by time-stamped message exchanges among the corresponding logical processes. |
| One of the important distinguishing features of PARSEC is its ability to execute a discrete-event simulation model using several different asynchronous parallel simulation protocols on a variety of parallel architectures. |
| PARSEC is designed to cleanly separate the description of a simulation model from the underlying simulation protocol, sequential or parallel, used to execute it. Thus, with few modifications, a PARSEC program may be executed using the traditional sequential (Global Event List) simulation protocol or one of many parallel optimistic or conservative protocols. In addition, PARSEC provides powerful message receiving constructs that result in shorter and more natural simulation programs. |
| SCALABILITY OF GLOMOSIM |
| The node aggregation technique gives significant benefits to the simulation performance. As each entity needs to examine packet receptions only for the nodes located in the region it is simulating, using many partitions reduce the total search space for packet delivery. The impact of multiple partitions for the models with 2500 and 5000 wireless nodes. Both simulation models consist of wireless nodes running CSMA at the MAC layer, each of which is randomly placed in 2000 x 2000m free space region. |
| The executions for both models become faster as the number of partitions increases. The effect of multiple partitions is larger for the model with 5000 nodes as the reduction in the execution time is related to the number of wireless nodes to be examined for each radio transmission. |
| GloMoSim achieved better parallel performance for models with higher number of wireless nodes because more activities occur concurrently in those models, which increase the parallelism of models. Users, especially those who need to simulate large-scale models can benefit from this parallel simulation capability of GloMoSim. shows increases of execution times against the number of mobile nodes in the model. |
| With the same number of processors, the execution time increases dramatically as the number of mobile nodes in the model increases. However, the execution time with 6 processors for the 10000 node model is shorter than the sequential execution for the 5000 node model. This implies that the user can run the simulation for a model consisting of twice the number of mobile node in the same amount of time with 6 processors. |
| Parallel simulation requires synchronization of simulation clock among multiple processors. PARSEC simulation environment provides four variations of conservative protocols and an optimistic protocol for the synchronization. The current GloMoSim kernel has parallel execution directives for conservative protocols and will be capable of executing models using optimistic protocols in future. |
V. CONCLUSION |
| In this project, we proposed a novel scheme for critical event monitoring in WSNs. The proposed scheme could essentially decrease the delay of alarm broadcasting from any node in WSN. Presented the mechanisms of monitoring a wireless sensor networks, for the following reasons: topology control (connectivity and the coverage), and the security in wireless sensor networks. Then we have to develop a new monitoring mechanism to guarantee strong connectivity in wireless sensors networks with sleep scheduling mechanisms we have also develop a way to monitor the robustness of the coverage between fixed targets and sensor nodes under local. We are also able to reduce the number of monitoring node and assume mechanisms for fault tolerance by auto organization of nodes to increase connectivity. Theoretical analysis and conducted simulations will show that the broadcasting delay and the energy consumption of the proposed scheme is much lower than that of existing methods. Finally, we have to demonstrate the effectiveness of our approach and algorithms with satisfactory results obtained through simulation. |
References |
|