Steganography is that the Art and Science of concealment the knowledge and noteworthy cover media. So, as to not arouse on Eaviesdropper’s suspicion. In this paper, secret image is hide into two totally different domains like as SVD (Singular value Decomposition) and DWT (Discrete wavelet Transform). the cover image and secret image DWT co-efficient values are embedded by 512*512 victimization fusion method techniques. The each domain offers safer with secret key and sure robustness of our algorithmic rule. This model provides high capacity and security. This proposed algorithm is tested with image quality parameters and compared to different algorithms. Experimental results analysed and showed that our proposed algorithm, by this method achieved high imperceptibility, were PSNR worth ranged between 45-55dB and sure robustness even many image process manipulations were performed.
Keywords |
| Steganography; Fusion method; DWT;
SVD; Arnold Transform; Color models |
INTRODUCTION |
| Steganography, the science of secret communication,
has received a lot of attention from the scientific
community recently. The most goal of Steganography is
especially involved with the protection of contents of the
hidden data. |
RELATED WORK |
| Umashankar Dewangan et al.,[1] proposed a
Development and Analysis of Stego Image Using
Discrete Wavelet Transform. The Experimental results
showed the high invisibility of the proposed model even
with large message size. Juned Ahmed Mazumder et
al.,[2] proposed a A High Capacity and Secured Color
Image Steganographic Technique Using Discrete Wavelet
Transformation. MSE and PSNR was calculated for each
of the cover and stego image and also the RGB histogram
of each of the file format was analysed. The MSE and Capacity are improved with acceptable PSNR compared
to the existing algorithm [3]. |
| Yambem Jina Chanu et al.,[4] proposed a
Steganography Technique based on SVD. Results of
different images with values are normalized correlation
(NC) and peak-signal-to-noise-ratio (PSNR. Ali Al-
Ataby et al.,[5] proposed a modified high capacity image
steganography technique that depends on wavelet
transform with acceptable levels of imperceptibility and
distortion in the cover image with high levels of overall
security. |
| Rowayda A. Sadek et al.,[6] proposed a SVD Based
Image Processing Applications: State of The Art,
Contributions and Research Challenges. Experimentally
examined and gave promising results compared to
developed ones. Image denoising and compression were
thoroughly examined and provided good results although
they are image dependent. Nilanjan Dey et al., [7]
proposed a Novel Approach of Color Image Hiding using
RGB Color planes and DWT. In this approach the stego
image generated is of acceptable level of imperceptibility
and distortion compared to the cover image and the
overall security is high. |
| This paper is organized in the following sections.
Methodology is described in section III. Section IV
introduced the proposed model. Testing and Performance
analysis is discussed in section V. Experimental results
are illustrated in section VI. Conclusion is discussed in
section VII. Finally References are given in the last
section. |
METHODOLOGY |
| A. Preprocessing |
| Pre-processing strategies use a tiny low
neighbourhood of an element in associate degree input
image to induce a brand new brightness price within the
output image. All the pixels of an image are spatial
domain square measure multiplexed by embedding.
B. Arnold Transform |
| Image Scrambling will be dispensed through several steps
to boost security levels. Arnold transform has special property of Arnold transform is that image involves its
original state once sure range of iterations. These numbers
of iterations is named ‘Arnold Period’ or ‘Periodicity of
Arnold Transform’. |
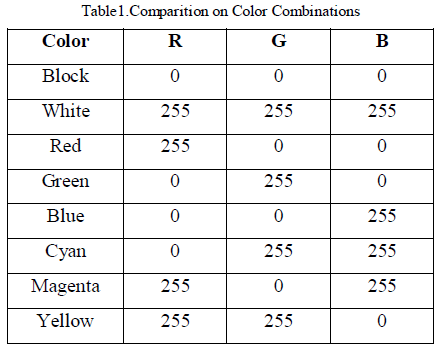
| C. Color models: |
| A Color space could be a mathematical illustration of
a collection of colours True color shown in Table 1. The
three most popular color models are RGB (used in
computer graphics), YIQ, YUV or YCbCr (used in video
system) and CMYK (used in color printing). However,
none of those color areas are directly associated with the
intuitive notions of hue, saturation and brightness. This
result within temporary pursuit of different models, likes
HIS and HSV, to modify programming, process and user
manipulation. |
 |
| D. Singular value decomposition: |
| Singular value Decomposition (SVD) is one amongst
variety of effective numerical analysis tools accustomed
analyse matrices. In SVD transformation, a matrix may be
rotten into 3 matrices that square measure constant size
because the original matrix. though SVD works for any
n*n matrix A, and while not loss of generality, our
discussion are restricted for the n*n matrix. |
| E. Discrete Wavelet Transform |
| Wavelet transforms square measure linear and that
they will be outlined by matrices of dimension n X n if
they\'re applied to inputs of size n. Wavelets convert the
image into a series of wavelets which will be hold on a lot
of expeditiously than component blocks. DWT square
measure applied to separate information sets and turn out
separate outputs. DWT eliminates the `blocking’ artifacts that deprive the reconstructed image of the required
smoothness and continuity. Wavelets convert the image
into a series of wavelets which will be hold on a lot of
expeditiously than component blocks. In numerical
analysis and useful analysis, a DWT any moving ridge
rework that the wavelets square measure discretely
sampled. like alternative moving ridge transforms, a key
advantage it\'s over Fourier transforms is temporal
resolution: it captures each frequency and placement info.
separate moving ridge transforms map information from
the time domain to the moving ridge domain. The result\'s
a vector of constant size. |
| F. Fusion Method |
| Fusion will be performed on pixel, feature or call level.
The complexions of pixel primarily based algorithms are
lesser than alternative strategies. Image fusion provides an
efficient manner of reducing this increasing volume of
information whereas at identical time extracting all the
helpful information from the supply pictures. In
application where ever each pixel spacing and spectral
properties of supply images are same or similar. |
PROPOSED WORK |
| In this section, we have a tendency to given our
increased physical property and lustiness for image
steganography theme with nice stego image quality and
increase payload by victimization dual embedding theme.
During this theme, that explores the characteristics of
each the rework. The represented illustration of planned
steganography encryption and decryption model was
shown in fig1 and fig2. |
| A. Encoding process |
| During the statistical encoding process as shown in
fig1, both cover image and secret image converting given
color image to SVD. Perform DWT on cover image and
DWT on secret image by using alpha blend technique.
Then take inverse IDWT to get stego image. |
| 1). Algorithm for steganography encoding process |
| Step 1: Select the Image from Image Database. |
| Step 2: The Selected Image is a Cover Image, and
checks with size, contrast, brightness and etc., |
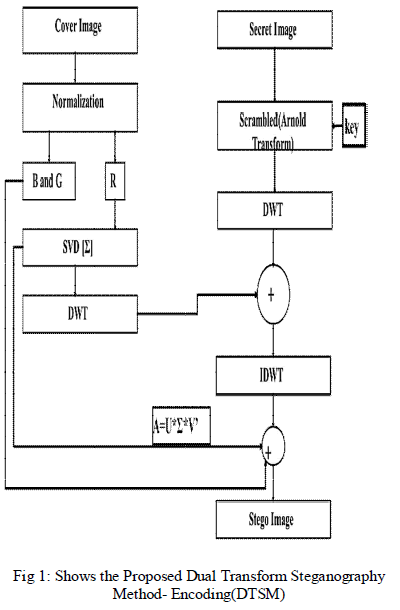 |
| Step 3: Apply preprocessing on cover image can be
Separated into R, G, B Planes. |
| Step 4: Calculate SVD for R-component Image. |
| Step 5: Decomposition on Ʃ-Singular Value block
image using for DWT. |
| Step 6: Simultaneously Select the Secret Image. |
| Step 7: Secret Image is scramble by Arnold
Transform with key(key2). |
| Step 8: Decomposition on image using for DWT. |
| Step 9: Both are added with Fusion Process.
Stego=α*C coff+(1- α)S coff. |
| Step 10: Obtained Scrambled Image is fusion with
SVD and G,B components. |
| Step 11: To get the Stego Image. |
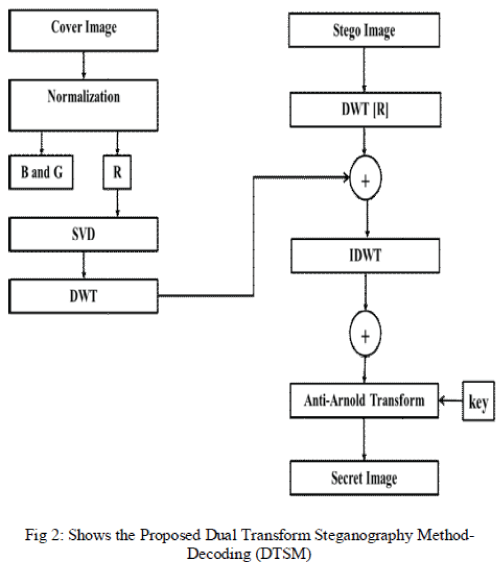
| B. Decoding process |
| During the statistical decoding process as shown in
fig2, the recover stego image and known cover image was
reconstructed with DWT transform domain and followed
by alpha blending process. Next, IDWT was performed to
rebuild the secret image. Finally the secret image is
obtained, which is similar to original secret image. |
| 2). Algorithm for steganography decoding process |
| Step 1: The Select Image is a Cover Image, and
checks with size, contrast, brightness and etc., . |
| Step 2: Apply preprocessing on cover image using
Normalization. |
| Step 12: Normalized Image is can be Separated into
R, G, B Planes. |
| Step 3: Calculate SVD for R component Image. |
| Step 4: Decomposition on each Ʃ-Singular Value
blocks image using for DWT. |
| Step 5: Get the Stego Image and take R-component. |
| Step 6: Stego image R-component is Decomposition
on image using for DWT. |
| Step 7: Apply Reverse Fusion Process on
Coefficient Values |
| Step 8: Obtained Scrambled Image is reconstructed
by Arnold Transform with Key(key2). Modify
Anti-Arnold Transform x’=x+y, and
N+y’=x+2y. |
| Step 9: To recover the Secret Image. |
TESTING AND PERFORMANCE ANALYSIS |
| We designated commonplace check image of
enormous size grey scale (512*512)cover image and
enormous size of grey scale secret image (image to be
embedded into cover image) for analysis of performance.
Here we have a tendency to are about to engraft a
512*512 secret image into a 512*512 cover image. |
| A. Testing |
| MATLAB could be a high performance language for
technical computer, integrates computation, mental image
and programming in a simple to use atmosphere. one in
all the explanations of choosing is to judge the
performance of the method, we tend to implement the
planned technique by exploitation Matlab R2010a and
7.10 version. |
 |
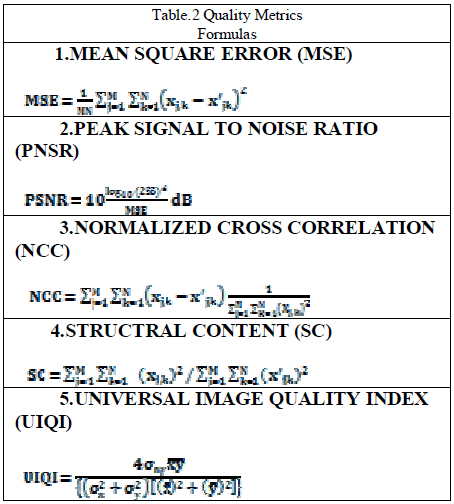
| B. Image Quality Metrics Measurements |
| The equations of the image quality metrics with
corresponding formulas used in our study has been
illustrated in Table(2). |
| C. Performance analysis |
| Performance analysis of these wavelet transforms is
done based on parameters. PSNR is used to measure the
quality of the reconstructed image. We used PSNR to
measure the distortion between an original cover image
and stego image. MSE is the mean square error
representing the difference between the cover image X
sized M x N and the stego image X’ sized M x N, and the
Xj,k and X’j,k pixels are located at the jth row the kth
column of images X and X’, respectively. Normalized
Correlation coefficient (NCC) between recovered and
original secret image, is used as a metric for performance
evaluation. |
| To evaluate the Dual Transform Steganography
Method using in Color Image Steganography. The
performance results of our transform steganography
technique based on SVD and DWT techniques. We
compare their image quality measurement values with the
other existing method, our algorithm calculated the
quality metrics which gets better acceptable ratio that was
shown in above equation on Table.2. |
 |
EXPERIMENTAL RESULTS AND DISCUSSIONS |
 |
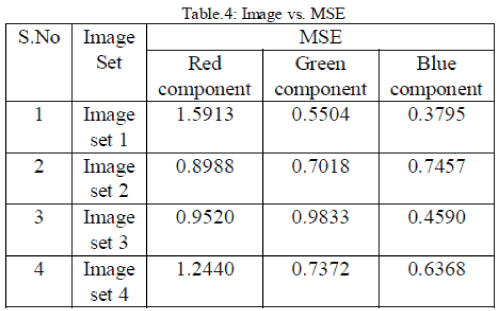 |
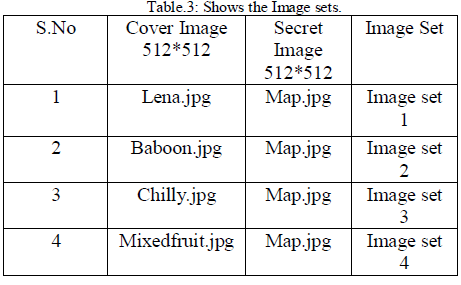
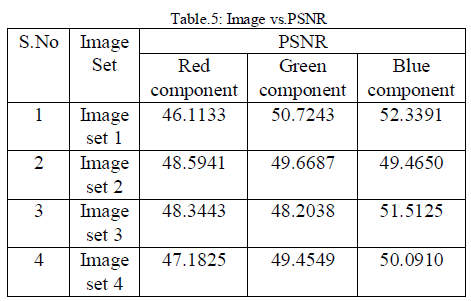
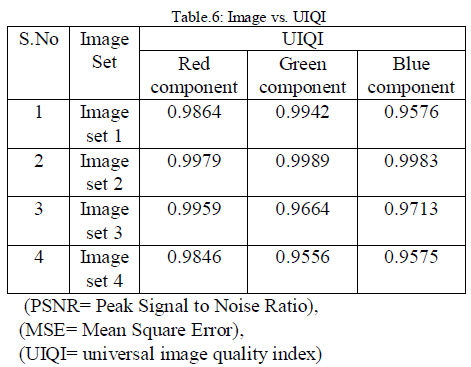
| The performance of a steganography system can be
measured using several properties shown in Table 3, Table 4, Table 5 and Table 6. The most important
property is the statistical undetectablility
(imperceptibility) of the data, which shows how difficult
it is to determine the existence of a hidden message. Other
associated measure is robustness, which refers to how
well the steganography system resists the extraction of
hidden data. |
 |
 |
| The comparison was done in favour of DWT as
expected due to the ability of wavelet transform technique
not only provides a better way for embedding large
amounts of data into cover images with imperceptions,
but also offers more robustness, which can avoid various
image attacks like as noise addition, compression and so
on. |
| There are mainly three aspects that should be taken
into account when discussing the results of Double-Key
Dual Transform method using in image steganography.
They are security, imperceptibility and robustness. |
| The perceptual difference between the stego image
and original cover image should be unnoticeable to the
human observer. As we seen the stego image given nice
invisibility and quality. PSNR is often expressed on a
logarithmic scale in decibels (dB). PSNR values below
30dB indicate low quality (distortion caused by
embedding is clear). A high quality stego image should
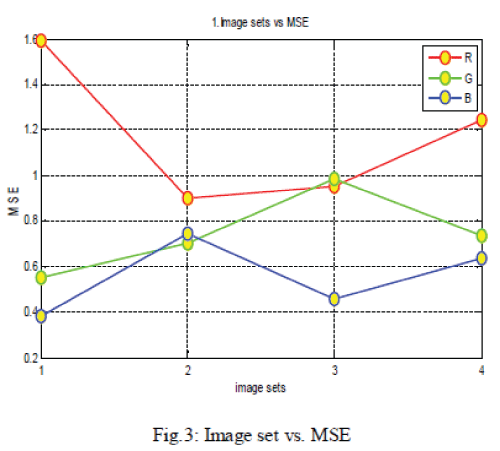
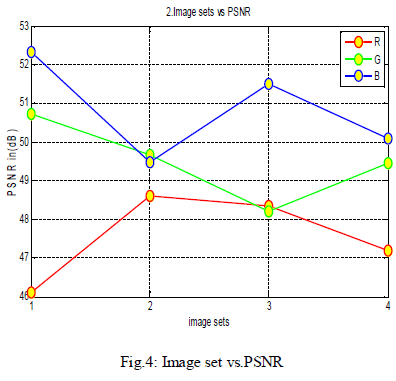
strive for a PSNR of 40 dB, or higher shown in fig.3, fig.4
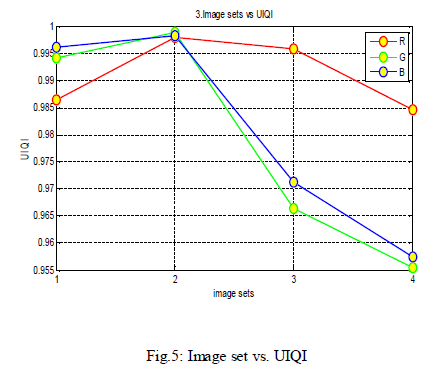
and Quality for UIQI as shown in fig5. |
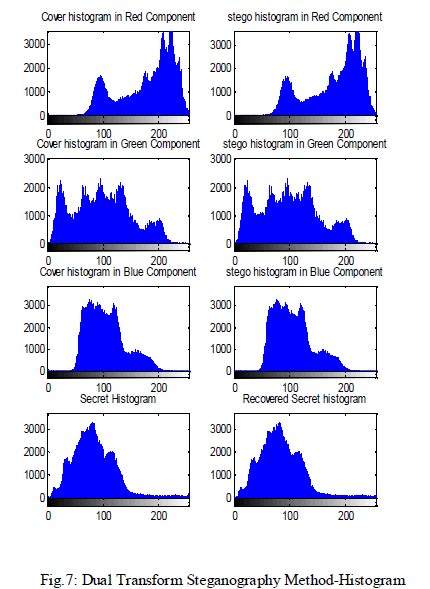
| This proposed technique is employed to increase the
robustness and the imperceptibility of the image after
embedding as shown in fig6 and fig7. |
 |
 |
 |
 |
 |
CONCLUSION |
| Eventhough all types of steganography techniques
provide high imperceptibility, security and robustness, it
is not easy to develop a method that satisfies all these
three needs, because of being application dependent may
vary from one application to another application. In this
paper we have presented a new image steganography
scheme under Dual Transform Steganography Method in
Color Image. Simulations are carried out on images of
different formats viz. JPEG, TIFF and BMP using
MATLAB. This technique achieved Embedded Image is
512*512, more robustness against image manipulation.
Performance analysis of these two transforms is done
based on parameters PSNR, MSE and UIQI than the
earlier techniques. In this technique more Secure, Robust
and High Capacity steganography based on Dual
Transform technique, we achieved high PSNR ratio
values approximately near 53 and less MSE values. |
References |
- UmashankarDewangan, Monisha Sharma, and SwagotaBera,,âÃâ¬ÃÅDevelopment and Analysis of Stego Image Using DiscreteWavelet TransformâÃâ¬Ã , International Journal of Science andResearch (IJSR), Vol 2, pp. 142-148, 2013.
- Juned Ahmed Mazumder and KattamanchiHemachandran, âÃâ¬ÃÅAHigh Capacity and Secured Color Image SteganographicTechnique Using Discrete Wavelet TransformationâÃâ¬ÃÂ, InternationalCopyright to IJIRSET www.ijirset.com 135Journal of Computer Science and Information Technologies, Vol. 4(4), pp. 583 - 589, 2013.
- KB. Shiva Kumar and Khasim T, and K B Raja , âÃâ¬ÃÅDualTransform Technique for Robust steganographyâÃâ¬ÃÂ, Internationalconference on Computational Intelligence and CommunicationSystems, pp. 173-178, 2011.
- YambemJinaChanu, Kh. Manglem Singh and ThemrichonTuithung, âÃâ¬ÃÅSteganography Technique based on SVDâÃâ¬ÃÂ,International Journal of Research in Engineering and Technology(IJRET), vol 6 , pp . 293-297 , 2012 .
- Ali Al-Ataby and Fawzi Al-Naima , âÃâ¬ÃÅA Modified High CapacityImage Steganography Technique Based on Wavelet Transform âÃâ¬ÃÅ ,International Arab Journal of Information Technology , vol 7 (4) ,pp . 1-7 , 2010.
- Rowayda A. Sadek, âÃâ¬ÃÅSVD Based Image Processing Applications:State of The Art, Contributions and Research ChallengesâÃâ¬ÃÂ,(IJACSA) International Journal of Advanced Computer Scienceand Applications, vol.3, ,2012.
- NilanjanDey, AnamitraBardhan Roy, and SayantanDey, âÃâ¬ÃÅANovel Approach of Color Image Hiding using RGB Color planesand DWTâÃâ¬ÃÂ, International Journal of Computer Applications,vol.36, ,2011.
- K. B Raja and H S ManjunathaReaddy , âÃâ¬ÃÂWavelet Based NonLSB Steganography âÃâ¬ÃÅ, International Journal of AdvancedNetworking and Applications, vol 03(3) , pp . 1203-1209 , 2011.
- ShikhaSharda and SumitBudhiraja, âÃâ¬ÃÅ proposedPerformanceAnalysis of Image Steganography based on DWT and ArnoldTransformâÃâ¬ÃÂ, International Journal of Computer Applications ,vol69, pp 46-50, 2013.
- AshishChawla and PranjalShukla, âÃâ¬ÃÅA Modified Secure DigitalImage Steganography Based on DWT Using Matrix RotationMethodâÃâ¬ÃÂ, International Journal of Computer Science andCommunication Engineering, vol 2, pp 20-25, 2013.
- AnahitaShojaei-Hashemi, Hamid Soltanian-Zadeh, ShahrokhGhaemmagham and Mahmoud Kamarei, âÃâ¬ÃÅUniversal ImageSteganalysis against Spatial-domain Steganography based onEnergy Distribution of Singular ValuesâÃâ¬ÃÂ, The 7th InternationalConference on Information Technology and Applications (ICITA2011), pp 179-183, 2011.
|