ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Pritam Kumar Tripathy1, Ratnesh Kumar1 and Dr. C. Nalini2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Now-A-Days the extremely interlinked urban population is precisely dependent on smart phones and mobile devices. The applications people use often rely on current locations of individual smartphone holders or a group of persons to provide location related mobile applications , which handers their privacy. Users are not supposed to reveal their exact (or preferred) locations to the service provider or to any other, possibly un trusted ,entity holders . In this paper, we propose privacy -preserving algorithms for accomplishing an optimal meeting location application for a group of users. We render a detailed privacy evaluation by formally quantifying privacy-hazard of the proposed approaches. In order to examine the enactment of our algorithms in a real disposition, we contrivance and test their execution efficiency on smart phones. By means of a targeted user-study, we endeavor to get an insight into the privacy-consciousness of users in location based amenities and the usability for the proposed. We propose a method for searching the location according to the user location. The location can be determined by GPS (Global positioning system). Position of current user can be realized as latitude and longitude entities. In our project if user download and update the location info from the server and use it in the corresponding application.
Keywords |
| Smart-phone-application, precise reckoning, Confidentiality, Private cloud, Hybrid cloud, MySQL database. |
INTRODUCTION |
| In today’s world, many people work in corporate office and they tend to travel more for business reasons. Scheduling meeting in the office is a manual work still, in which the scheduler does not consider any other terms except the time to schedule the meeting. In such case, the employees has to attend the meeting in correct time irrespective of the place. This may increase pressure and workload of the employees. In order to make the work easy a meeting scheduler can be built which tracks the location of the employees and using that location and considering the vehicle in which they travel, a common place can be decided to schedule the meeting reducing the cost, time, distance and workload of the employees. By introducing such an application employees feel free to attend the meeting without any pressure and it does not bring any loss to the office also. It becomes easy to schedule the meeting and satisfy employees which cannot be done when it is done manually. |
RELATED WORKS |
| 1.Igor Bilogrevic,“Privacy-Preserving Optimal Meeting LocationDetermination on Mobile Devices. THE rapid proliferation of smartphone technology in urbancommunities has enabled mobile users to utilize context awareservices on their devices. Service providers take advantageof this dynamic and ever-growing technology landscapeby proposing innovative context-dependent services for mobilesubscribers. Location-based Services (LBS), for example, areused by millions of mobile subscribers every day to obtainlocation-specific information. |
| Two popular features of location-based services are locationcheck-ins and location sharing. By checking into a location,users can share their current location with family andfriends or obtain location-specific services from thirdpartyproviders. The obtained service does not depend on the locations of other users. |
| 2.Hui Liu,”Survey of Wireless Indoor Positioning Techniques and Systems”.These systems have been successfully used in many applications such as asset tracking and inventory management. This paper provides an overview of the existing wireless indoor positioning solutions and attempts to classify different techniques and systems. Three typical location estimation schemes of triangulation, scene analysis, and proximity are analyzed. We also discuss location fingerprinting in detail since it is used in most current system or solutions. We then examine a set of properties by which location systems are evaluated, and apply this evaluation method to survey a number of existing systems. Comprehensive performance comparisons including accuracy, precision, complexity, scalability, robustness, and cost are presented. In general, measurement involves the transmission and reception of signals between hardware components of the system. An indoor wireless positioning system consists of at least two separate hardware components: a signal transmitter and a measuring unit. Algorithms: Location fingerprinting, Location positioning, closest-neighbor algorithm. |
| 3.Heikki Helin” Mobile Agent Communication in Wireless Networks” University of Helsinki, Department of Computer Science. Kluwer, 2004. While agents may solve many problems typical to these environments, agents require special support from underlying architecture. Mobile agents, perhaps the most known class of agents, needs special treatment in these environments. Although moving agent’s code from mobile device to stationary host, and running agent there solves the problem of unexpected disconnections, the migration process is sometimes too time consuming compared to traditional message passing. In this paper we discuss about agent communication issues concentrating on the problems the wireless environment causes, and give some guidelines how these problems may be solved. In interaction protocol layer, an agent may optimize its communication pattern by reducing the number of messages to send by coupling several messages to one. Moreover, an external observer agent may learn about communication patterns used by other agents, and optimize these patterns without interfering the communicating agents. Algorithms: naive compression, round-trips. |
| 4.Guanling Chen and David Kotz” Policy-Driven Data Dissemination for Context-Aware Applications” (PerCom 2005).Traditional flow-control and congestion control policies either drop data or force the sender to pause. When the data sender is sensing the physical environment, however, a pause is equivalent to dropping data. Instead of arbitrarily dropping data that may contain important events, we present a policy driven data dissemination service named PACK, based on an overlay-based infrastructure for efficient multicast delivery. PACK enforces application-specified policies that define how to discard or summarize data flows wherever queues overflow on the data path, notably at the mobile hosts where applications often reside. A key contribution of our approach is to uniformly apply the data-stream “packing” abstraction to queue overflow caused by network congestion, slow receivers, and temporary disconnection. We present experimental results and a detailed application study of the PACK service. Which means that they can adapt to occasional data loss and often do not require exact data delivery. Many multimedia applications are less tolerant in nature, but we focus on non-multimedia applications in this paper. Algorithms: Ladder, faster. |
| 5. Shuai Zhang, XiuzhenHuo” Cloud Computing Research and Development Trend” 2010 Second International Conference. The concept of computing comes from grid, public computing and SaaS. It is a new method that shares basic framework. The basic principles of cloud computing is to make the computing be assigned in a great number of distributed computers, rather than local computer or remoter server. The running of the enterprise’s data center is just like Internet. This makes the enterprise use the resource in the application that is needed, and access computer and storage system according to the requirement. This article introduces the background and principle of cloud computing, the character, style and actuality. This article also introduces the application field the merit of cloud computing, such as, it do not need user’s high level equipment, so it reduces the user’s cost. It provides secure and dependable data storage center, souse needn’t do the awful things such storing data and killing virus, this kind of task can be done by professionals. It can realize data share through different equipment’s. It analyses some questions and hidden troubles, and puts forward some solutions, and discusses the future of cloud computing. Cloud computing is a computing style that provide power referenced with IT as a service. Users can enjoy the service even he knows nothing about the technology of cloud computing and the professional knowledge in this field and the power to control it. Algorithm: Radius algorithm, fixed Interval algorithm. |
| 6. Chunye Gong, Jie Liu, Qiang Zhang, Haitao Chen and Zhenghu Gong-“The Characteristics of Cloud Computing” 2010 39th International Conference on Parallel Processing. Cloud computing is based on several other computing research areas such as HPC, virtualization, utility computing and grid computing. In order to make clear the essential of cloud computing, we propose the characteristics of this area which make cloud computing being cloud computing and distinguish it from other research areas. The cloud computing has its own conception, technical, economic and user experience characteristics. There have also been several research results in the literature that focus on the problem of privacy-preserving location-based queries and location sharing or anonymous location check-ins. Mobile agents, perhaps the most known class of agents, needs special treatment in these environments. Although moving agent’s code from mobile device to stationary host, and running agent there solves the problem of unexpected disconnections, however, these research efforts attempt to solve issues that are orthogonal, and uniquely different, from the ones addressed in this paper. Jaiswal and Nandi propose a privacy-preserving platform, called Trust No One, for privately locating nearby points-of-interest. Their architecture relies on three non-colluding parties. The service oriented, loose coupling, strong fault tolerant, business model and ease use are main characteristics of cloud computing. Clear insights into cloud computing will help the development and adoption of this evolving technology both for academe and industry. Algorithm: Byzantine fault tolerant algorithms. |
| 7. Guido Gehlen, Fahad Aijaz, Muhammad Sajjad, Bernhard Walke-“A Mobile Context Dissemination Middleware” 2010. This paper introduces a context dissemination middleware based on a mobile Web Services framework. In a P2P environment, each context source/provider offers services to other devices. A monitor service is proposed which reduces the communication amount between devices and decreases the reaction time according to context changes. Moreover, to provide monitoring service of arbitrary context information, a rule description (policy) language has been designed. The paper presents an exemplary application in the health care domain to demonstrate the use of the middleware. Additionally, the application development process is described to point out the strength of the middleware for application developers. |
| 8. echoSurangsrirat and Chusak Thanawattano- Android Application for Spiral Analysis in Parkinson’s Disease” 2012:- The paper presents an application for spiral analysis in Parkinson’s disease (PD). PD is one of the most common degenerative disorders of the central nervous system that affects elderly. Four cardinal symptoms of the disease are tremor, rigidity, slowness of movement, and postural instability. The current diagnosis is based on clinical observation which relies on skills and experiences of a trained specialist. Thus, an additional method is desirable to help in the diagnosis process and possibly improve the detection of early PD as well as the measurement of disease severity. Many studies have reported that the spiral analysis may be useful in the diagnosis of motor dysfunction in PD patient. We therefore implement a mobile, safe, easy to use, and inexpensive. Methods: Unified Parkinson’s disease Rating Scale (UPDRS). |
| 9. Wang∗, Zhiyang Wang†, Guobin Shen‡, Fan Li‡, Song Han§ and Feng Zhao”WheelLoc: Enabling Continuous Location Service on Mobile Phone for Outdoor Scenarios” 2013 Proceedings IEEE INFOCOM. The proliferation of location-based services and applications calls for provisioning of location service as a first class system component that can return accurate location fix in short response time and is energy efficient., we present the design, implementation and evaluation of Wheel Local continuous system location service for outdoor scenarios. Unlike previous localization efforts that try to directly obtain point location fix, Wheelock adopts an indirect approach: it seeks to capture a user mobility trace first and to obtain any point location by time- and speed-aware interpolation or extrapolation. WheelLoc avoids energy-expensive sensors completely and relies solely on commonly available cheap sensors such as accelerometer and magnetometer. With a set of novel techniques and the leverage of publicly available road maps and cell tower information, WheelLoc is able to meet those requirements of a first class component. Experimental results confirmed the effectiveness of WheelLoc. It can return a location estimate within 40ms with an accuracy about 40 meters, consumes only 240mW energy. Algorithm: Hidden Markov Model (HMM) and Viterbi algorithm. |
| 10. Arnab Nandi #, SteliosPaparizos, John C. Shafer, Rakesh Agrawal- ”With a Little Help from My Friends “The Ohio State University, 2015 Neil Avenue, Columbus, ICDE Conference 2013. A typical person has numerous online friends that, according to studies, the person often consults for opinions and advice. However, public broadcasting a question to all friends risks social capital when repeated too often, is not tolerant to topic sensitivity, and can result nonresponse, as the message is lost in a myriad of status updates. Direct messaging is more personal and avoids these pitfalls, but requires manual selection of friends to contact, which can be time consuming and challenging. We demonstrate a working system that addresses these issues by returning an ordered subset of friends predicting (a) near-term availability, (b) willingness to respond and (c) topical knowledge, given a query. The combination of these three aspects are unique to our solution, and all are critical to the problem of obtaining timely and relevant responses. Our system acts as a decision aid – we give insight into why each friend was recommended and let the user decide whom to contact. Algorithm: Data model and algorithmic sketches. |
MEETING SCHEDULER FOR ANDROID |
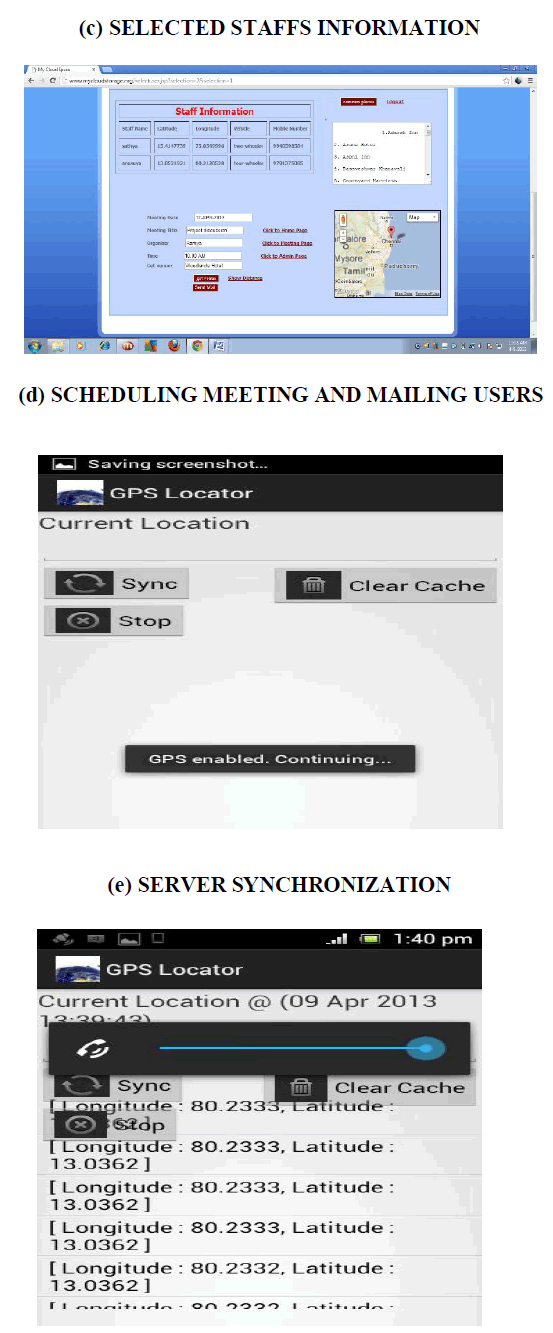
| The aim of this project is to identify the location of the employees and to schedule meeting according to that, which satisfies all the employees in the peer group. The location of the employees is tracked using the GPS in smart phones and it gets updated in the Cloud storage. Based on the location of the employees common place is identified using the Google maps and the distance is calculated using Google API to get a centralized place. Where the meeting canbe schedule using that centralized place automatically search the nearest hotels and resort at all. That particular meeting location and address will send to the corresponding employee mail-id. |
| Advantages: When the GPS values didn’t get the interior area that time it will automatically navigate the Service provider. Reducing the time, fuel wastage of travelling. Reduce the distance and work pressure of the employees. |
| Location-based services |
MODULE DESCRIPTIONS |
| • Tracking the location using Google Maps |
| • Selecting the users and getting the common places. |
| • Getting the venue by prioritizing the vehicle parameters. |
| • Sending the meeting location via mail |
TRACKING THE LOCATION USING GOOGLE MAPS |
| a)Sending the data from Android device |
| All the data received in the application including the username, password, latitude, longitude co-ordinates need to be sent to the server. This is done by the Android application that will invoke the server by synchronizing, all the parameters are encoded and posted to the server. |
| b.)Receiving all the data from the Android device |
| The cloud server receives all the parameters from the Android device and then connects to a database and execute a series of queries to save all the parameters in their respective tables. |
| c.)UI design and layout |
| The interfaces if the Android device are programmed in XML, they are organized using Layouts and the graphical layout can be decorated with Buttons, Scrollbars, Text fields and form widgets. The interface for the user in the web is designed with HTML and is decorated with CSS for better appearance. |
SELECTING THE USERS AND GETTING THE COMMON PLACES |
| From the database, the admin will select the group of users for the meeting and their latitude and longitude will be tracked. The common places will be retrieved from the Google Maps and it will be displayed. |
GETTING THE VENUE BY PRIORITIZING THE VEHICLE PARAMETER |
| From the available common places the venue will be selected by using the vehicle parameter. The venue will be sorted in such a way that, the user using 2-wheeler will travel more distance than the user using 4-wheeler. |
| a.) Getting Geo position from GPS receiver |
| The location and map based capabilities are used in the application using the classes of the Android Location package and the Google maps external library. The application has access to the location services supported by the device through the classes in the Android Location package. The central component of the location framework is the location manager system service, which provides APIs to determine location and bearing of the underlying device. |
| b.) Google provides a maps external library that includes the com.google.android.maps package. The key class in the maps package is com.google.android.maps.MapView, a subclass of View Group. A Map View displays a map with data obtained from the Google Maps Service. |
SENDING THE MEETING LOCATION VIA MAIL |
| The scheduled meeting will contain the meeting name, organizer, time and venue. Finally, it will be sent via mail to the selected users. |
| a.) Plotting the location on Google Maps |
| The Google Maps is embedded in the webpage using Google Maps JavaScript API V3. |
| All maps API applications should load the Maps API using an API key. This API key is embedded in the JavaScript which loads the Google maps. The latitude and longitude coordinates are received from the database and are plotted using Overlays. Overlays are objects on the map that are tied to latitude and longitude coordinates. Markers identify locations on the map, thus placing a marker on the desired location of the map. |
PPFRVP PROBLEM FORMULATION |
| In this work, we consider the problem of finding a rendezvous point among a set of user-proposed locations, such that (I) the Rendez-Vous point is fair (as defined in Section IV-A) with respect to the given input locations, (ii) each user learns only the final Rendez-Vous location and (iii) no participating user or third-party server learns private location preference of any other user involved in the computation. We refer to an algorithm that solves this problem as Privacy- Preserving Fair Rendez-Vous Point (PPFRVP) algorithm. In general, any PPFRVP algorithm A should accept the inputs and produce the outputs. |
EXPERIMENTAL SETUP AND RESULTS |
| We used personal system consisting i5 processor with 2.4 GHz 3GB RAM. The storage of HD is 500GB. Hence are the hardware specifications and the operating system we used was Win7. The editor we used was IDE-Eclipse. Version of JAVA was JDK 1.6.0. The database for synchronization was MYSQL. Specifications mentioned are the minimum individuals; maximum are suggested for better issues avoidance. |
| The corresponding architecture shows the overall working environment for all of the following four modules. Hence the design above shows starting from the tracking user location, calculating and selecting the nearest common places, thus by scheduling the accordance meeting and notifying the selected users. |
 |
 |
CONCLUSION |
| In this paper, the privacy issue in the Fair Rendez-Vous Problem (FRVP). The privacy issue in the Fair Rendez-Vous Problem (FRVP). Our Researches are based on the homomorphic properties of well-known cryptosystems. We have analyzed and enlightened several prioritized locations preferences on the basis of our literature survey. Used many applications on smart phones an android devices privacy features are crucial for the adoption of any location sharing or location-based applications. Thus the phase 1 is accomplished under studying the algorithms precisely and examining them on server-client process successfully. |
References |
|