ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
| Dimple Elizabeth Baby 1, Sebastian George 2, Jessy Paul 3 P.G Student, Dept. of Computer Science & Engineering, VJCET, Kerala, India 1 Assistant Professor, Dept. of Computer Science & Engineering, VJCET, Kerala, India2 Professor, Dept. of Civil Engineering, MACE, Kothamangalam, Kerala, India3 |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
With the introduction of smart phones with wide range of applications, the modern business world gains the advantage of all in-one gadgets with roaming work place. The collaborative computing applications found in smart phones helps in performing group work with colleagues even out of the office as all the normal computer functions are possible with the smart phones. Such applications support the interaction between people and information sharing among the participants by storing the data in common storage area. But there is high potential risk for user’s security and privacy in this environment. In order to sustain privacy and security in digital collaborative environments, strong authorization and authentication framework is required and so a novel Trusted Third Party called Shielding Server is introduced which will provide strong authentication and access control mechanisms to make data sharing in collaborative computing environment more secure. Combining the finger print authentication along with conventional password authentication method will provide strong authentication. For providing good access control mechanism, the Shielding Server will classify the data into multiple levels like public, sharable and sensitive data, according to their sensitivity and impose strong access constraints for each level of data. Public data is stored as plain text and any registered user can be access it. Sharable and sensitive data are stored in an encrypted format so that only legitimate users who have the access right can decrypt the data. A novel access control mechanism based on biometric checksum block is introduced for providing privacy to the sharable data and the encryption key generated from the secret information supplied by the user will protect the sensitive data from unauthorized access.
Keywords |
| CRA Algorithm, Access Control, Secure Data Sharing, Privacy |
INTRODUCTION |
| Mobile devices are changing the way we experience the physical world, from personal usage to work applications. The latest applications found in the smart phones helps to collaborate on projects with friends and colleagues while you are roaming around the world. Collaboration requires individuals working together in a coordinated fashion, towards a common goal. Accomplishing the goal is the primary purpose for bringing the team together. Collaborative software helps facilitate action-oriented teams working together over geographic distances by providing tools that aid communication, collaboration and the process of problem solving. Additionally, collaborative software may support project management functions, such as task assignments, time-managing deadlines, and shared calendars. The collaborative technologies enable people to realize their ideas by sharing or taking advantage of their various resources through connected networks. Users of collaborative computing applications can store all their daily events which can be collected by their own mobile phone, for example, SMS, photos, call, movie, e-commerce information, Web service log and usage information, location information, documents, media, battery charge, personal schedule, and so on. The stored data are transferred to each user’s personal database by Internet, and then they are stored and managed as a personal history with the passage of times and can be retrieved when ever required. This service allows users to share their data with other people or a certain service provider and collaborate on projects with friends, colleagues. User can install these applications on their own laptops, palmtops, mobile phone etc and store their personal data in a remote database and share the data with others as shown in figure 1. |
 |
| The storing of data in a commonly accessible structure has both a great potential for the knowledge society as well as a high risk for the user’s privacy. Here in lies one of the greatest challenges for collaborative environments. That is, a continual balance must be sought between the interests of open easily accessible information with the protection of personal data and entity privacy. Strong privacy control is a major contributor to increased trust between member entities which in turn can facilitate increased participation and contribution to a collaborative environment. In this paper a novel Trusted Third Party called Shielding Server is introduced which will provide strong authentication and resource level access control mechanisms by making use of checksum blocks. |
II. BACKGROUND KNOWLEDGE |
| In order to sustain privacy and security in digital collaborative environments, strong authorization and authentication framework is required. Privacy is the right of individuals to determine for themselves when, how and to what extent information about them is communicated to others. Privacy in general is very subjective and means different things to different people [1] [2]. Common privacy dimensions include privacy of the person, privacy of personal behaviour, privacy of personal communications, and privacy of personal data. |
| The Technical, Legal, and Community Privacy Protecting framework provides a broad information privacy solution for collaborative environments. The three key components being Technical, Legal and Community models of protection each provide three unique privacy protecting and personal data management utilities for member entity use. The integration and application of the TLC-PP framework is a significant contribution towards the delivery of a Privacy Augmented Collaborative Environment (PACE) [2] [3]. Shield Privacy provides the necessary privacy tools organizations need to build privacy protecting information systems. Shield Privacy is aimed at making information system designers and developers to consider information privacy in its own right as a design objective [3]. It forces information system owners to be aware of privacy requirements in their systems, from both a legal standpoint and as a way of building customer trust and satisfaction The guidelines like personal data minimization, separation of duty and data (SDD), information security for privacy Protection are useful in the design and implementation of collaborative environments to ensure information privacy and personal data management requirements. |
| Different access control mechanisms are used to provide privacy and security. Role based access control model element (RBAC) model as a whole is fundamentally defined in terms of individual users being assigned to roles and permissions being assigned to roles [6]. As such, a role is a means for naming many-to-many relationships among individual users and permissions. A role is a job function within the context of an organization with some associated semantics regarding the authority and responsibility conferred on the user assigned to the role. Permission is an approval to perform an operation on one or more RBAC protected objects In purpose based access control mechanism, the users are required to state their access purposes along with the data access requests, and the system validates the stated access purposes by ensuring that the users are indeed allowed to access data for the particular purposes [7][8]. To facilitate the validation process, each user is granted authorizations for a set of access purposes, and an authorization for an access purpose permits users to access data with the particular purpose. |
| In Hippocratic database design, the purpose is the central concept around which privacy protection is build [9]. The privacy metadata tables define for each purpose and for each piece of information (attribute) collected for that purpose: the external-recipients: whom the information can be given out to, the retention-period: how long the information is stored, and the authorized-users: the set of users (applications) who can access this information. |
| A mediator based access control is implemented using a community authorization service (CAS) server that is responsible for managing the policies that govern access to a community’s resources [10]. It also contains policy statements that specify who (which user or group) has the permission, which resource or resource group the permission is granted on, and what permission is granted. A member of a community may send the CAS server a request for a capability that will allow the user to perform a set of actions; if that request is consistent with the community’s policy, the CAS server will delegate an appropriate capability back to the user. The user can then use that delegated credential to authenticate to a resource server and exercise the rights described by the capability. |
III. SHIELDING SERVER WITH STRONG AUTHENTICATION AND CHECKSUM BLOCK BASED ACCESS CONTROL |
| Collaborative computing applications found in smart phones are designed for note taking and archiving and helps to remember things you like in your everyday life. Since memory of smart phone is very small, these kinds of applications help the user to store a large amount of data in a remote personal storage server with the help of internet and retrieve the data whenever needs. Users will feel that their personal storage memories are on every computer, phone and device they use. The user can collaborate on projects with friends and colleagues. But data stored in the storage server is not secure as no encryption is used and no special access control mechanisms used for providing privacy. |
| The proposed scheme introduces a novel Trusted Third Party called Shielding Server, for providing security using strong encryption methods and privacy through multilevel data classification and access control. Shielding server situated between user and storage server, will shield the data storage server from direct access of users. Only the legitimate user who has access right can contact the storage server. In order to provide security, strong authentication method like finger print verification is included, along with traditional method like password authentication. For providing privacy data is classified into different levels like public, sharable and sensitive according to its sensitivity (Table I) and separate encryption keys are used for each level of data. User has to prove that he has the permission to access a particular data at the time of retrieval. If the user is valid one, then decryption key for the requested data will be obtained. |
| A. Notations Used |
| This section introduces some notations used throughout this paper and their meaning |
 |
| B. Entities Involved in Proposed Scheme |
| The proposed scheme has three main parties: a user/a mobile device, a Shielding server, and a data server (S).The Shielding Server is located in front of storage server as shown in figure 2. It authenticates a legitimate user and verifies the accessible authorization to data which the user wants to retrieve. In order to achieve this, Shielding server manages all of the things related to authentication such as enrolment of biometric information, personal information, and generation of instances for authentication processes, with powerful computational and storage abilities. All the data of each user are stored in the user’s personal DB, which is managed by a server manager S. The Shielding Server knows secret keys of sharable data so that it can decrypt the data stored in personal DBs. The secret keys should not be given to any administrator and it means that the server cannot decrypt any data. A data server S only has to store all data and implement queries of Shielding Server. |
 |
| C. Classification of Information according to sensitivity |
| All of the data to be stored in storage server are classified into three categories according to their sensitivity. This classifying standard is determined by a user with his or her subjective standard. Users can determine the level of data when they store with pop-up message. It is associated with self regulation of privacy. In this way, users can control their own information by themselves. |
| Public data is the information that anyone can access and share the information. Sharable data is not public but sharable information so that this level of information requires to be encrypted with distinctive encryption keys for each file. For providing security while transferring data, encryptions are implemented in each user’s mobile phone and then the encrypted data are transferred to Shielding Server. In order to share this level of information, the original keys need to be managed by Shielding Server because valid users’ access authorization can be changed dynamically. Sensitive level information is highly sensitive information and the owner does not share this information with anyone. |
 |
| D. Finger Print Authentication |
| Fingerprint authentication is one of many biometric forms of human identification. A fingerprint sensor captures a digital image of a fingerprint pattern of the user at the time of registration. The captured image will be encrypted using key generated from the password of the user and stored at the Shielding Server. |
| f1 = Ek_pwd (fin) |
| At the time of login of the user, this encrypted image will be shipped back to the user and decrypted correctly if user could submit correct password. This image will be compared with the newly submitted image for checking whether the user is valid or not. |
| fin = Dk_pwd (f1) |
| E. Sensitive level data key generation |
| The sensitive data should be encrypted and stored in a secure manner. Sensitive level data can be decrypted only by the owner and so key used for encryption and decryption should be strong enough. A strong key can be generated from a secret information provided by the user at the time of file saving. The secret information is just like a password and it has to be remembered by the user for decrypting the file. The decryption of the file is possible only if the user supplies same secret information used at the time of file saving. The advantage of this method is that sensitive data key is not stored anywhere and only the owner can decrypt the file. |
| F. Encryption and Decryption of the file |
| The sharable level and sensitive level file is encrypted using separate key. [Encryption] |
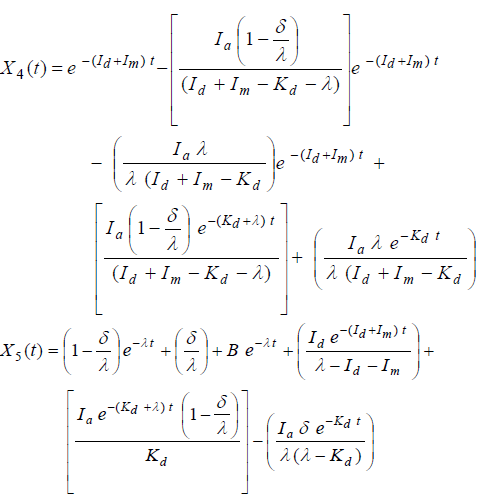 |
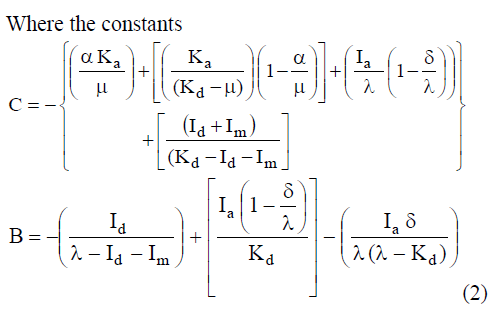 |
| G. Checksum Row Based Access Control Mechanism |
| Corresponding to each sharable file stored at Data Server, a checksum row will be formed (Fig.4). This checksum block will corresponds to the list of users who have the permission to access the file. User list will include the set of users who are selected by the owner of the file to whom he is willing to share the file. Corresponding to each sharable file, Shielding server will create a checksum row of n blocks if n users are selected by the owner of the file. |
| XCKS_BLOCK fi = xcks_u1 + xcks_u2 + xcks_u3 … xcks_un , where xcks_un is formed by XOR-ing checksum of file fi and checksum of finger print image of user n. |
 |
| The authorization to a particular file is stored as the checksum blocks. No one can understand who all have the permission to a particular file by examining the checksum block. When a user request for a particular file, the Shielding server will XOR the checksum of finger print image and file content and search in whole n-blocks to find a match. If the requested user has the permission to access the file, then a matching block will be obtained. |
| H. Checksum Row Authorization (CRA) Algorithm |
| Algorithm 1 is a pseudo code for CRA algorithm. FILE_SET is the set of all files and IMG_SET is the set of all finger print images of users to whom a particular file is to be shared. If the user is willing to share f number of files with others, the algorithm will produce f rows of checksum block (CKS_ROWf). The variable FLCKS holds the checksum of file and BLOCKui is the XORed checksum of finger print image and the file. |
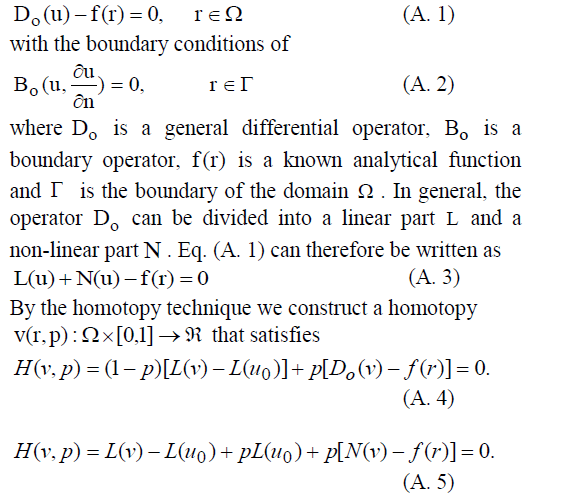 |
| I. Whole Protocol Used |
| For establishing a secure communication path between user and Shielding Server, public-private key pair is used. The public key of Shielding Server is distributed to the users. A public–private key pair will be created for each login session of the user and request and public key of the user will be sent to Shielding Server after encrypting them with public key of Shielding Server. The following steps explain the whole protocol. [User] |
| 1. User i inputs his password pwd’ and fingerprint B’ on each sensor of the mobile device. |
| 2. Encrypted finger print stored (B) at Shielding Server will be shipped to MDi and decrypt it with key generated from the password. Compare B and B’ |
| 3. If B= = B’, the user is valid one and user has the right to upload or download file. A public-private key pair is used for establishing a secured communication path and public key must be sent to Shielding Server after encrypting with its public key. |
| 4. If upload mode is chosen by user, select the file to be stored and its level of access send it to Shielding server. If public data, it is stored as plain text. If sharable data list of users who have the access permission to the file must be sent. If sensitive level data, it is encrypted using sensitive level key obtained from the secret information supplied by the user and sent to Shielding Server. All communications to Shielding Server will be encrypted using its public key. |
| 5. If download mode is selected, user has to prove that the user has the permission to the requested file. [Shielding Server] |
| 6. If the mode of operation is uploading and access level is either public or sensitive, Shielding Server will send the file to Data Server by encrypting it using a symmetric key shared between Shielding Server and Data Server. If sharable level is chosen, checksum block for authorization will be formed from user list and stored at Shielding Server. Then encrypt data by sharable level key randomly generated and reencrypt it using symmetric key shared between Shielding Server and Data Server for secure data transfer. The original sharable data key is stored at Shielding Server |
| 7. If mode of operation is downloading, Shielding Server will first check whether the user has the access right to the requested file. If the user is authorized one the request is forwarded to Data Server [Data Server] |
| 8. Data Server will decrypt the request from Shielding Server by the symmetric key shared between Shielding Server and Data Server. |
| 9. If the request is to upload the file, Data Server will store the file. If the request is to download the file, Data Server will retrieve the content sent to Shielding Server by encrypting it using same symmetric key. [Shielding Server] |
| 10. If level public or sensitive file is requested by the user Shielding Server simply decrypt the result obtained from Data server and sent to user after encrypting it with a newly generated random key. This key will be sent to user after encrypting it using user’s public key. |
| 11. If the requested file is sharable, first the result from data server is decrypted using symmetric key. Then decrypt the content by the original key stored at the Shielding Server and sent to user after encrypting it with a newly generated random key. This key will be sent to user after encrypting it using user’s public key. [User] |
| 12. If public level or sharable level file is requested, the result is simply decrypted for obtaining the actual content. |
| 13. If sensitive level file is requested, the result is decrypted using sensitive level key obtained from the secret information. |
IV. IMPLEMENTATION |
| The following section describes different module and the implementation details. |
| A. Registration and Login |
| User must register with Shielding Server by submitting user id, password and biometric information (finger print).Here fingerprint authentication is added along with the traditional method of user id and password for getting strong authentication. After registration, Shielding Server has to finger print (B) after encrypting it using key generated from password. Key of 128-bit length can obtained after applying MD5 to the user’s password and by using AES encryption byte array of finger print image can be stored RSA algorithm is used for secure communication channel establishment between user and Shielding Server. Shielding server’s public key is distributed to all users and a public-private key pair will be generated for each login session of the user. |
| B. Data Storage |
| By using collaborative computing applications in smart phones, user can store SMS, Contacts, and files in a remote personal database. The user will classify the data at time of storage. Different levels of data include public, sharable and sensitive and different encryption keys are used accordingly. Data encryption is performed by AES algorithm. Each time when a sharable file is stored at Data Server, the user must select multiple persons from the group that the user is willing to share file. In other words, along with the file stored, user must selects name of persons from list who can access the user’s file and it has to send to Shielding Server. The key for sharable data is generated by the Shielding Server and it will hold a file details table with the following structure. |
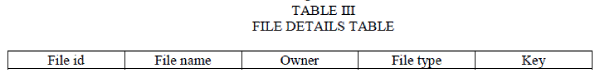 |
| The field file id corresponds to the unique file id, file name corresponds the name of the file storing. File type shows the level of storage and key is the encryption key for the file. Rows created for the file details table during the execution is shown below in table III. The filed file type can have values zero, one and two. The value zero corresponds to the public level, one corresponds to the sharable level and two corresponds to the sensitive level data. |
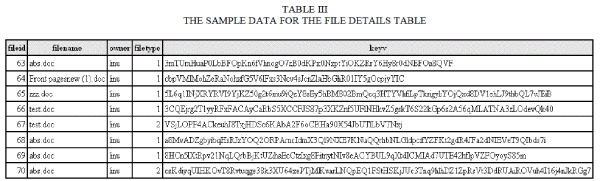 |
| C. Checksum Row Authorization |
| Checksum of the file is obtained after applying MD5 algorithm to the file content. Similarly, each user’s finger print byte stream is taken and applying MD5 algorithm. After that, XOR the two checksum results. For the implementation of checksum row authorization, we can use the permission table with the following structure. The field file id corresponds to the unique file id and userid indicates to the share corresponds to the authorized users to whom the file is shared. The authorized user list is sent to the Shielding Server by the user. The checksum row created in the permission table during the execution is shown below in table V |
 |
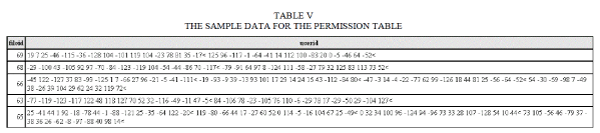 |
IV. CONCLUSION |
| Collaborative computing has emerged as a new way for interaction between people and it will support information sharing among the participants. The collaborative computing applications in smart phones promote teamwork by allowing users to share their data with the members of the team. In order to provide information privacy and security in this environment, a Trusted Third Party called Shielding Server is introduced. Shielding server will shield the data storage server from direct access of users. Only the legitimate user who has access right can contact the storage server. Strong authentication mechanism like finger print identification is included so that only valid user can access the storage server. For providing information security, the data is stored in an encrypted format and for privacy, data is classified into multiple levels according to their sensitivity and strong authorization methods are introduced for each level of data. A secure communication path is established using public-private key pairs for request-replay transfer. The proposed system will covers functions like private key management of PKI, biometric management, data sharing over an encrypted database, etc. This scheme is secure against all the attacks from various routes and provides privacy preserving access control and therefore, can be applied to other applications which require strong authentication and access control mechanisms. |
References |
|