ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
K.Supriya1, S RajeshKumar2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Vehicle to vehicle communication plays a vital role in exchanging of contents between two or more vehicles. Those contents are providing Varity of applications to vehicle users such as rollover warning, emergency vehicle warning, lane changing warning and so on. Precise communication between vehicles is very important to enable perfect content management such as maximize the throughput and size of content to transfer between vehicles which is obtained by improving the performance of vehicle to vehicle relaying .In this paper an Idealized approach has proposed to engrave the vehicle to vehicle relaying using Max-Flow Algorithm.
Keywords |
| Vehicular Network, Content Management, Vehicle to Vehicle relay, Max-Flow Algorithm |
INTRODUCTION |
| As today is an Emerging world not only the human population but also the vehicle population increasing dramatically. To provide sophistication more vehicles in market enabled with communication devices which helps the user in multiple point of view such as navigating maps, emergency warnings, and providing entertainment services. All such services need the contents which are downloaded from the internet based servers. Due to increased number of vehicles and its high network utilization leads network resource shortage on future. Shortly it is essential to take necessary steps to improve the network performance can support multiple users with lower utilization of bandwidth. The survey performed on traffic of us based network operator which result sixty percent of network resources drained by only one percent of smart phone users [12]. The designed network should be support huge amount of users the possibility for this is to share the part of traffic to Dedicated Short Range Communication (DSRC), but this approach suitable only download of large amount of delay tolerant contents[3]. Deployment of road side infrastructure in optimum way and its advancements are provided in [11].infrastructure to vehicle communications and performance of direct communications given in [6] Data transfer methods in vehicle to vehicle communication with performance measures are analysed and shown in [10]. So in idealized approach the content management process consider as Max- Flow problem which yields optimum Access point deployment and optimum data transfer. In [9] An AP deployment strategy designed to favour content download through relaying in vehicular networks is introduced. In [5], both I2V and V2V communications are considered and the performance evaluation is carried out through simulation and a test bed on a circular campus bus route. Furthermore, a comparison against the solution to a max-flow problem is presented, but (i) it is limited to a simplified, highway-like scenario featuring one AP and one downloader and (ii) it assumes atomic contacts between nodes, hence neglecting interference and channel contention. In [10]focus on the feasibility of using IEEE 802.11 APs to inject data into vehicular networks, as well as on the connectivity challenges posed by such an environment. |
| In [8], the authors show that a random distribution of APs over the street layout can help routing data within urban vehicular ad hoc networks. In [7], the impact of several AP deployments on delay tolerant routing among vehicles is studied. More precisely, each AP is employed as a static cache for content items that have to be transferred between vehicles visiting the AP at different times. Other than in the scope, the works in differ from ours also because they do not provide theoretical justification of the AP placements they propose. In [1] AP deployment is formulated as an optimization problem, where, however, the objective is not content downloading but the dissemination of information to vehicles in the shortest possible time. In [2], instead, estimates the minimum number of infrastructure nodes to be deployed along a straight road segment so as to provide delay guarantees to the data traffic that vehicles have to deliver to the infrastructure, possibly with the help of relays. A similar problem is addressed, with the aim to support information Dissemination. The different objectives of the above studies lead to completely different formulations, thus to results not comparable with the ones we present. This paper includes two basic works, one is study about the traffic pattern of city to found the impacts and difficulties for content management, the second one construct a network topology dynamically for the generation of effective content management schemes. Engraved performance of network topology shown by simulation results. The paper organised as follows. Section II shows the model of system and description about the delay tolerant networks and transfer paradigms with simulation architecture. The flow diagrams show the transfer paradigms of direct and relay transmission. Algorithm defines how the max flow has been achieved. Section III contains the simulation results and the performance. Conclusion and future work has show in Section IV and V viceversa. |
II. SYSTEM MODEL |
| A) (DTNS) The vehicular cooperation paradigm that we consider relates our work to DTNs. In particular, assesses the benefit to content dissemination of adding varying numbers of base stations, mesh nodes and relay nodes to a DTN, through both a real test bed and an asymptotic analysis. A DTN time-invariant graph, which is similar to the time-expanded graph used in our study, was presented With respect to we do not assume the contacts between mobile nodes to be atomic but to have arbitrary duration, and we build the network graph so as to account for the presence of roadside infrastructure and channel contention. The representation of a time-varying network topology as a time-expanded graph can be found over a road topology. B) Transfer paradigms I) Direct transfer A direct communication between an AP and a downloader. This represents the typical way mobile users interact with the infrastructure in today’s wireless networks. II) Connected forwarding Traffic relaying through one or more vehicles that create a multi-hop path between an AP and a downloader, where all the links of the connected path exist at the time of the transfer. This is the traditional approach to traffic delivery in ad hoc networks. C) Simulation Architecture The aim of the DNTG is to model all possible opportunities through which data can flow from the APs to the downloader’s, possibly through relays. Given the mobility trace, we therefore identify the contact events between any pair of nodes . To demonstrate simulation form a dynamic network topology graph (DNTG) from a vehicular mobility trace, which considering that on the corresponding road layout there are: (i) a set of A candidate locations (ai, i = 1, . . . ,A) where APs could be located, (ii) a set of V vehicles (vi, i = 1, . . . , V ) transiting over the road layout and participating in the network, and (iii) a subset of D vehicles that wish to download data from the infrastructure. Simulation model shown in following fig., |
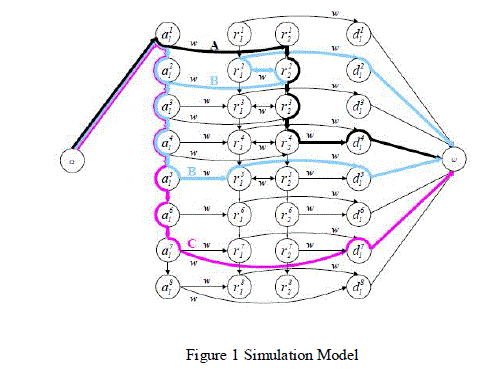 |
| To demonstrate simulation form a dynamic network topology graph (DNTG) from a vehicular mobility trace, which considering that on the corresponding road layout there are: (i) a set of A candidate locations (ai, i = 1, . . . ,A) where APs could be located, (ii) a set of V vehicles (vi, i = 1, . . . , V ) transiting over the road layout and participating in the network, and (iii) a subset of D vehicles that wish to download data from the infrastructure. |
| D) Characterstics Of Contact Events Quality of links between nodes starting time, of contact end time of contact |
| The time interval between any two successive contact events in the network is called frame. The frame represented as F and vechicles represented as vi and access points represented as ai. Downloaders represented as Dk and non downloaders represented as Rk. In frame k, a directed edge (vi k vj k) exists from vertex vi k € Rk and vj k € Vk if a contact between the non-downloader vehicle vi and another vehicle vj is active during that frame. Each edge of this type is associated with a weight w(vi k vj k) equal to the rate of that contact event. The set including such edges is defined as Lv k. Similarly a directed edge (ai k vj k) exists from vertex ai k € Ak and vj k € Vk if a contact between the accesspoint ai and vehicle vj is active during that frame. Each edge of this type is associated with a weight w(ai k vj k) equal to the rate of that contact event. The set including such edges is defined as La k. The DTNG used to identify paths in the graph that correspond to (i)direct download from the candidate AP to the downloader, as path C, (ii) connected forwarding through 3-hops (frame 2) and 2-hops (frame 5), as path B, and (iii) carry-and-forward through the movement in time of the relay r2, as path A |
| E) The Max-Flow Problem This max flow problem used to maximize the flow from α to ω the total amount of downloaded data. Denoting by x(·, ·) the traffic flow over an edge connecting two generic |
| vertices, the objective mathematically can be expressed as: |
 |
| F) Constraints Non-negative flow. Flow conservation. Channel access. Overlapping AP coverage’s. Maximum number of APs. Maximum number of active AP |
| G) Algorithms / Techniques Used |
| Step 0: (Preprocessing) Set up directed graph and sparsify. |
| Step 1: (Upper bound) Obtain an upper bound on the MILP objective function by running a heuristic to And a feasible solution.s |
| Step 2: (Lower bound). Solve the LP relaxation of the VRPSF. |
| Step 3: (Optimality check) If the optimality conditions are satisfied go to Step 8; otherwise go to Step4. |
| Step 4: (Improvement) If a new integer solution has been obtained, use heuristic post-processor to improve the incumbent upper bound. If an improvement results,update the incumbent and go to Step 3; otherwise go to Step 5. |
| Step 5: (Variable Fixing) Determine if any binary variables can be fixed at zero or one. |
| Step 6 :(Cut generation) Solve the separation problem to generate valid inequalities. If no such inequalities can be identified go to Step 7; otherwise go to Step 2. |
| Step 7: (Branching) Create a new node in the search tree following the logic of branch and bound. If branching is not possible, go to Step 8; otherwise go to Step 2. Step 8: (Desparsification) If no sparsfied variables remain fixed at zero, stop and declare the incumbent the optimal solution to the MILP. Otherwise, introduce a subset of the sparsified variables whose reduced costs are negative back into the model and go to Step 2. |
III.SIMULATION ANALISIS |
| The performance metrics are consistent in revealing the critical importance of the penetration rate p and The lower impact of the roadside infrastructure extension. Accordingly, we can separate two regimes. The first , when P <20%, i.e., at early stages of the technology adoption, characterized by lower throughput and higher delay, a stronger dependency on direct I2V communication and lower downloading fairness. The second, for P>30%, i.e., in presence of a quite mature technology, featuring instead higher throughput and lower delay, massive use of V2V communication and high fairness. As the impact of the system settings is different within these two regimes, in the following we will study them separately. According to the results above, we will employ the max- flow problem solution on the complete and on the sampled graph in the low- and high-penetration regime, respectively. |
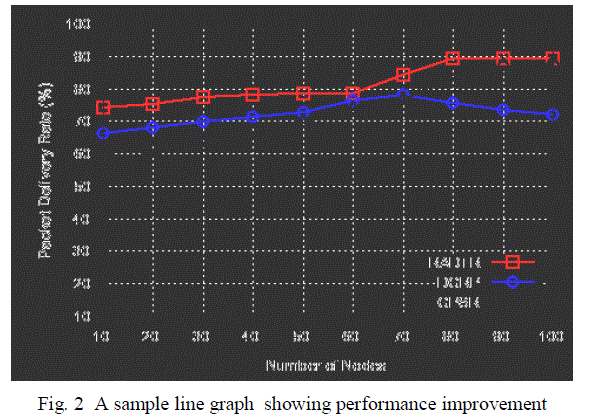 |
| Fig. 2 shows an performance variations of idealized approach and cooperative approach. The red colour graph indicates improved throughput against number of nodes which is higher than the existing cooperative approach. |
III. CONCLUSION |
| This idealized approach allows to capture the space and time network dynamics, and to formulate a max-flow problem whose solution provides an upper bound to the system performance. Through a graph-sampling technique, we solved the problem for realistic, large-scale traces. Simulation results showed that the physical and MAC-layer assumptions on which the framework relies have a minor impact, leading to a tight upper bound. The major findings are strategy and the extension of the AP deployment with well planned deployments leading to a throughput twice or three times higher than that observed In the high-penetration regime a random AP deployment works well Knowledge of user mobility is paramount to the system performance, since most of the V2V traffic relaying takes place through the carry-and-forward paradigm. However, the complexity of multi-hop protocols can be limited to one relay, as the contribution of transfers over a higher number of hops is negligible. |
V. FUTURE WORK |
| This Idealized approach provide optimal way to find best reley node for content transfer and provide appropriate candidate Access point using Max-Flow algorithm. Due to best relay node selection it provides improved throughput and maximize the size of the content to download. Additionally security mechanisms will be added to improve the network performance by assuring the secure content download. Security mechanism can be added via using secure protocol like ARAN will be considered for our future work. |