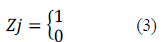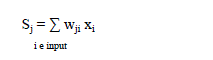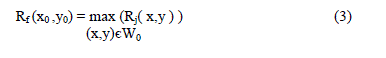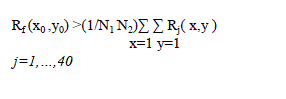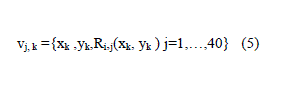Keywords
|
| Routing protocol, in-network aggregation, wireless sensor networks, InFRA\ |
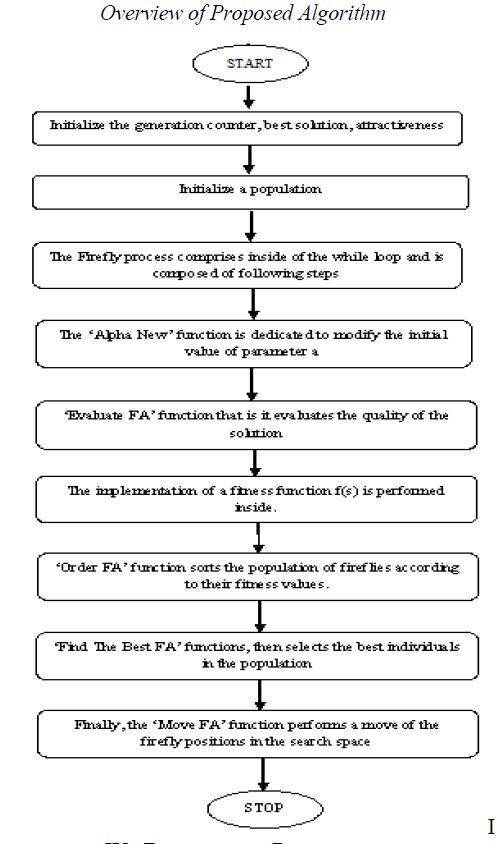
INTRODUCTION
|
| A Wireless Sensor Network (WSN) is built of nodes from a few to several hundreds or even thousands of nodes where each node is connected to one sensor. Each such sensor node has several parts radio transceiver, microcontroller and battery. Depending on the complexity of the individual sensor nodes, the cost of the sensor nodes ranging from few to hundreds of dollars. Forest-fire detection, water quality monitoring and natural disaster prevention are some of the applications of wireless sensor networks. Routing plays an important role in data aggregation. It is the process of selecting paths in network traffic. Routing schemes has different delivery semantics: unicast, multicast, broadcast, any cast and geocast. One of the main challenges in routing algorithms is even in the presence of nodes failures and interruptions in communications, how guarantee the sensed data is delivered. Because of the higher redundancy in raw data collected by sensor nodes, in-network aggregation make used to decrease the communication cost by forwarding a little aggregated information and eliminating redundancy. To overcome these challenges, we propose Data Routing algorithm for In-Network Aggregation for WSNs, which we refer to as DRINA algorithm. This algorithm will maximize the information fusion in reliable way by fault tolerant mechanism. This paper is organized as follows: in Section 2, discussion about Centered-At-Nearest-Source algorithm. Section 3 some theoretical description about SPT and InFRA. In Section 4 introduces our proposed DRINA algorithm and Finally, Section 5 presents our conclusions and Future work. |
II.CENTERED–AT- NEAREST – ALGORITHM
|
| In this technique,the node which is closest to the sink node could act as an aggregation point. This node gathered the data from all other source node and then forwards this aggregated data towards the sink. when the number of sources are high,then it results in a poor performance because many sources may directly route towards the sink faster rather than the node that route towards one particular node that is nearest to the sink. |
 |
| It construct the routing tree in a distributed fashion. Whenever an event is detected by every node, by using the shortest path it reports the gathered information to the sink node. whenever this shortest path overlap for different sources, information fusion occurs. In the Fig. 1, consist of non overlapping routes because simple shortest path is used. Fusion does not takes place between cluster data.Distance vector routing and link state vector routing are the protocols to calculate the shortest path. In the distance vector routing, each router sends a vector of distances to its neighbor node. The vector contains distances to all nodes. In the link state routing, each router sends a vector of distances to all nodes. The vector contains distances to the neighbor node. |
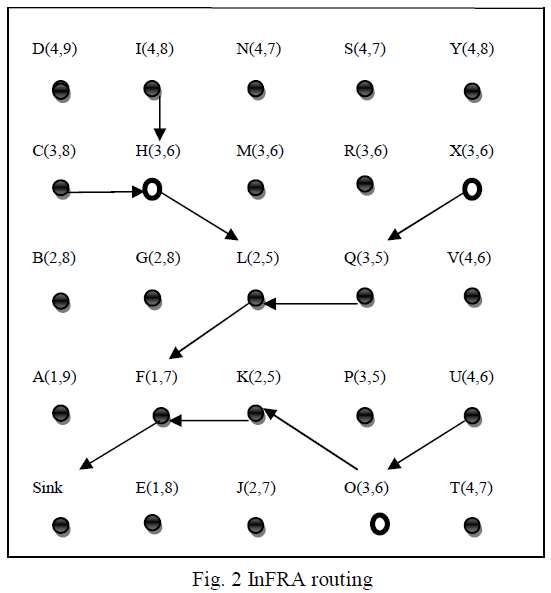
| Information-Fusion-based Role Assignment,in this algorithm two or more nodes detect the same event then the nodes are grouped into clusters. Cluster head collects the data from its members and forward the event data to the sink.In the Fig. 2, minimum shortest path is found. The nodes H,O and x has performed Inter-cluster fusion. |
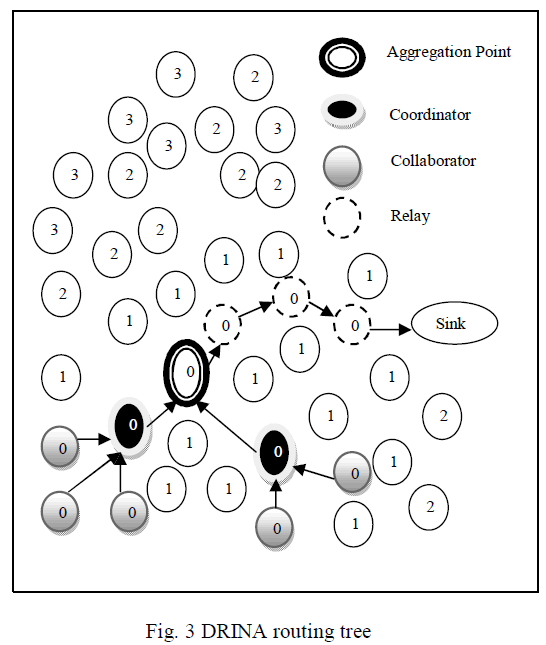
| The following roles are involved to create the routing infrastructure: |
 |
| ïÃâ÷ Collaborator (Cluster Member): An event is detected and forward its collected data to a coordinator node. |
| ïÃâ÷ Coordinator (Cluster Head): An event is detected and also responsible for gathering data from the collaborator and performs aggregation and sends the result to a sink node. |
| ïÃâ÷ Sink :A node that receiving data from a set of collaborator and coordinator nodes. |
| ïÃâ÷ Relay :A node receives data from another node and forwards towards the sink. |
| When there is no event is detected then except the sink, all the sensor node performs relay role. |
 |
A .Cluster Formation
|
| Each event involves in sensor networkhas detected by only one cluster called Head, and nodes are detected by cluster members.We have several strategies to select the cluster head(Coordinator).We can select the node which has the smallest id,node which is very closest to the sink node, highest degree,less energy consumption. |
B. Route Formation
|
| Route are constructed by choosing the best neighbor at each hop.Depending on the followingconstraints,the best neighbor node can be chosen.The node which is Shortest path to the sink. If two or more nodes closest to the sink ,then tie appears. In that cases we choose the node which has shortest distance to other coordinator(Cluster Head).Aggregated coordinatorsdistance could taken into this consideration. |
 |
| Where distance(vi, u) is the distance between nodes vi and u , in hops.Coordset is the set of all coordinator nodes. To understand this,as soon as the cluster get formed each coordinator floods a control message,during this floodingevery node computes its distance to that coordinator. Therefore chances of route overlapping and data aggregation are enhanced. |
C. Information fusion
|
| In this InFRA algorithm,we have two types of information fusion intra-cluster, inter-cluster fusion. In the former the tree is composed only of collaborators(i ,e) only data from the collaborator nodes are fused whereas in the later, it allows the aggregation of multiple clusters (i,e) only data from the coordinator nodes are fused. |
D.Dynamic Topologies
|
| In this algorithm dynamic topologies are illustrated.while notifying an event,if the chosenrelay node get fails, then a new relay node(second best option) is chosen. If the failure rate is high, then the InFRA algorithm can’t find the best path. Proactive solutions are the best choice based on the failure rate. |
IV. DRINA (DATA ROUTING FOR IN-NETWORK AGGREGATION)
|
| While maximizing data aggregationDRINA algorithm is to construct the routing tree from source to the sink node with the shortest path. This algorithm has three phases. |
A .Constructing the Hop Tree
|
| Hop tree is constructed from sensor node to the sink node. The distance is computed inhops from the sink node to each node in the network. The sink node sends HCM(Hop Configuration Message) to allnodes through flooding. Thisand HopToTree which is the distance through which theHCM message has passed.The initial value of HopToTreeis 1 at the sink.This HCM message is passed to its neighbors. when receiving this message, each node verifies if the stored HopToTree value is greater than the value of HopToTree in the received HCM message.If the condition is true then the node update the stored HopToTree value with the value in the HCM message else the node discards the received HCM message. |
B. Formation of cluster
|
| Similar to InFRA,Election algorithm should be done when one or more nodes detects the same event. Basedon the result of this algorithm, roles are assigned to the |
 |
| The advantage of this algorithm is that the information collected by the nodes which are sensing the same event will be aggregated at a point (called aggregation point) is more efficient. |
C.HopTree Updates
|
| New route is established by the coordinator for the event dissemination. To establish the route(Fig. 3),Coordinator sends a route establishment message to its NextHop node.Whenthis node receives a route establishment message,it retransmits the message to its NextHop and starts updating node is reached or a node that is closer to the already established route. |
| After the route establishment,hoptree updating process is started.The main aim of this phase is to update the value of the HopToTree in all nodes so that newly established route can taken into consideration.Relay nodes are responsible for this process.Each node will send only one packet so that the whole cost of this process is same as flooding. |
D. Route Repair Mechanism
|
| DRINA algorithm has piggybacked and ACKbased route repair mechanism.when the relay node wants to forward data to its NextHop node then it sends the data packet. For every data packet transmission,it sets the timeout and waits for acknowledgement.If the node has not receive any acknowledgement then it recognize that particular node get failed and select the new node.A newly partial reconstructed path is created after the repairing mechanism is applied. |
V.CONCLUSION AND FUTURE WORK
|
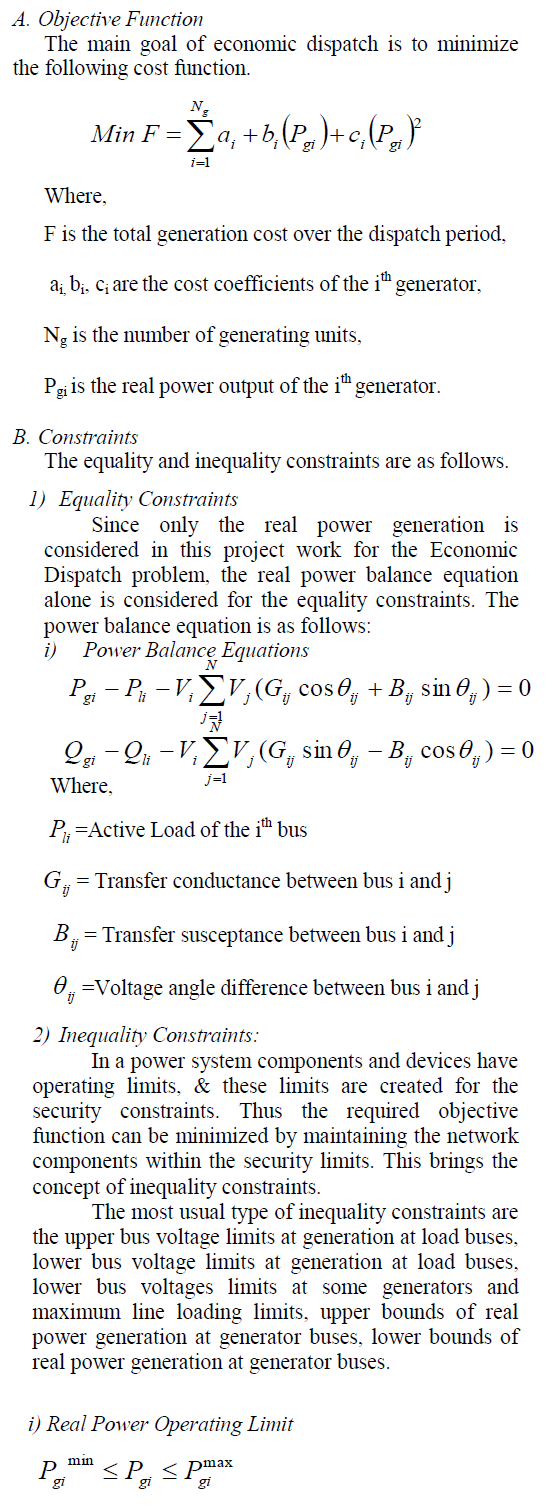
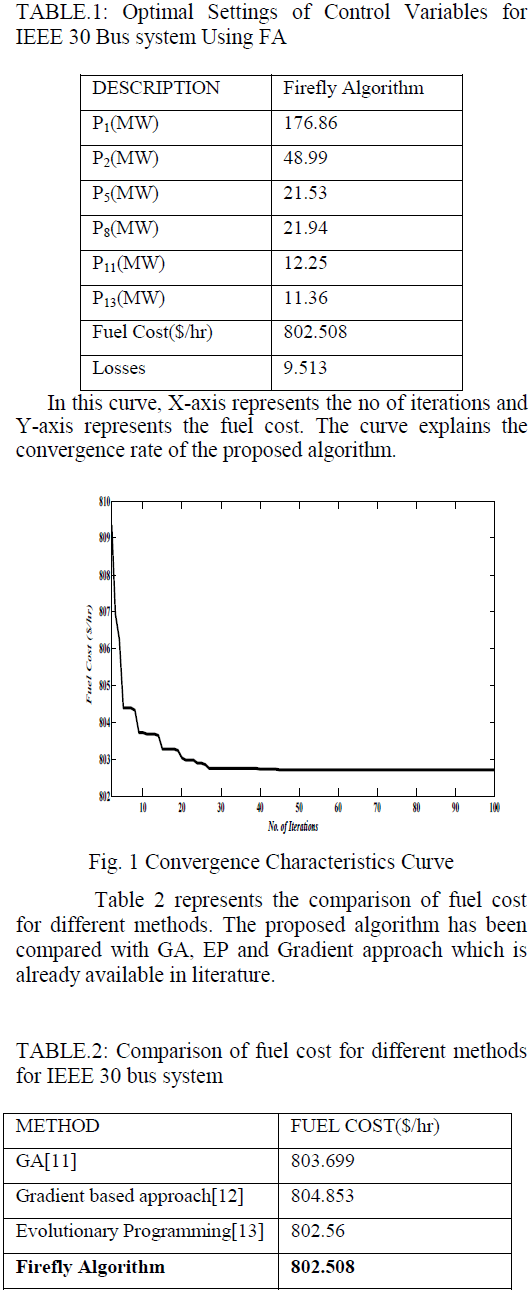
| In this paper, DRINA(Data Routing for In- Network Aggregation) algorithm are compared to SPT, CNS and InFRA with respect to stability, communication cost, aggregation rate, data delivery data. Table I shows the comparison ofthe above algorithm.DRINA improves the delivery rate thanInFRA ,SPT and CNS by performing the fault tolerant mechanism and maximizing the aggregation points. DRINA performs efficient only in the case of staticevents of fixed radius.Our future work may consider the Dynamic sizes of events. |
References
|
- I.F. Akyildiz, W. Su, Y. Sankarasubramaniam, and E. Cyirci, “Wireless Sensor Networks: A Survey,” Computer Networks, vol. 38, no. 4, pp. 393-422, Mar. 2002
- G. Anastasi, M. Conti, M. Francesco, and A. Passarella, “Energy Conservation in Wireless Sensor Networks: A Survey,” Ad Hoc Networks, vol. 7, no. 3, pp. 537-568, http://dx.doi.org/10.1016/j.adhoc.2008.06.003, May 2009.
- A. Boukerche, R.B. Araujo, and L. Villas, “Optimal Route Selection for Highly Dynamic Wireless Sensor and Actor NetworkEnvironment,” Proc. 10th ACM Symp. Modeling, Analysis, andSimulation of Wireless and Mobile Systems (MSWiM ’07), pp. 21-27,2007
- H.S. AbdelSalam and S. Olariu, “A Lightweight Skeleton Construction Algorithm for Self-Organizing Sensor Networks,” Proc. IEEE Int’l Conf. Comm. (ICC), pp. 1-5, http://dblp.unitrier. de/db/conf/icc/icc2009.html#AbdelSalamO09, 2009.
- L. Villas, A. Boukerche, R.B. de Araujo, and A.A.F. Loureiro, “Highly Dynamic Routing Protocol for Data Aggregation in Sensor Networks,” Proc. IEEE Symp. Computers and Comm (ISCC),pp.496502,http://dx.doi.org/10.1109/ISCC.2010.5546580, 2010.
- I. Chatzigiannakis, T. Dimitriou, S.E. Nikoletseas, and P.G. Spirakis, “A Probabilistic Algorithm for Efficient and Robust Data Propagation in Wireless Sensor Networks,” Ad Hoc Networks, vol. 4, no. 5, pp. 621-635, 2006.
- L.A. Villas, D.LGuidoni, R.B. Arau´ jo,A. Boukerche, and A.A. Loureiro, “A Scalable and Dynamic Data Aggregation ware Routing Protocol for Wireless Sensor Networks,” Proc. 13th AC Int’l Conf. Modeling, Analysis, and Simulation ofWireless and MobileSystems, pp. 110-117
- E.F. Nakamura, A.A.F. Loureiro, and A.C. Frery, “Information Fusion for Wireless Sensor Networks: Methods, Models, and Classifications,” ACM Computing Surveys, vol. 39, no. 3, pp. 9- 1/9-55, 2007.
- F. Hu, X. Cao, and C. May, “Optimized Scheduling for Data Aggregation in Wireless Sensor Networks,” Proc. Int’l Conf. Information Technology: Coding and Computing (ITCC ’05), pp. 557- 561, 2005.
- I. Solis and K. Obraczka, “The Impact of Timing in Data Aggregation for Sensor Networks,” IEEE Int’l Conf. Comm., vol. 6, pp. 3640-3645, June 2004.
- B. Krishnamachari, D. Estrin, and S.B. Wicker, “The Impact of Data Aggregation in Wireless Sensor Networks,” Proc. 22nd Int’l Conf. Distributed Computing Systems (ICDCSW ’02), pp. 575- 578,2002.
- J. Al-Karaki, R. Ul-Mustafa, and A. Kamal, “Data Aggregation inWireless Sensor Networks—Exact and Approximate Algorithms,”Proc. High Performance Switching and Routing Workshop (HPSR ’04),pp. 241-245, 2004.
- J. Al-Karaki and A. Kamal, “Routing Techniques in Wireless Sensor Networks: A Survey,” IEEE Wireless Comm., vol. 11, no. 6,pp. 6-28, Dec. 2004.
- E. Fasolo, M. Rossi, J. Widmer, and M. Zorzi, “In-network Aggregation Techniques for Wireless Sensor Networks: A Survey,” IEEE Wireless Comm., vol. 14, no. 2, pp. 70-87, Apr. 2007.
- C. Intanagonwiwat, R. Govindan, D. Estrin, J. Heidemann, and F. Silva, “Directed Diffusion for Wireless Sensor Networking,” IEEE/ACM Trans. Networking, vol. 11, no. 1, pp. 2-16, Feb. 2003.
- E.F. Nakamura, H.A.B.F. de Oliveira, L.F. Pontello, and A.A.F. Loureiro, “On Demand Role Assignment for Event- Detection in Sensor Networks,” Proc. IEEE 11th Symp.Computers and Comm.(ISCC ’06), pp. 941-947, 2006.
- A.P. Chandrakasan, A.C. Smith, and W.B. Heinzelman, “An Application-Specific Protocol Architecture for Wireless MicrosensorNetworks,” IEEE Trans. Wireless Comm., vol. 1, no. 4, pp. 660-670, Oct. 2002.
|