ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
K.J.Sathya, Mrs.S.Vidhya,
|
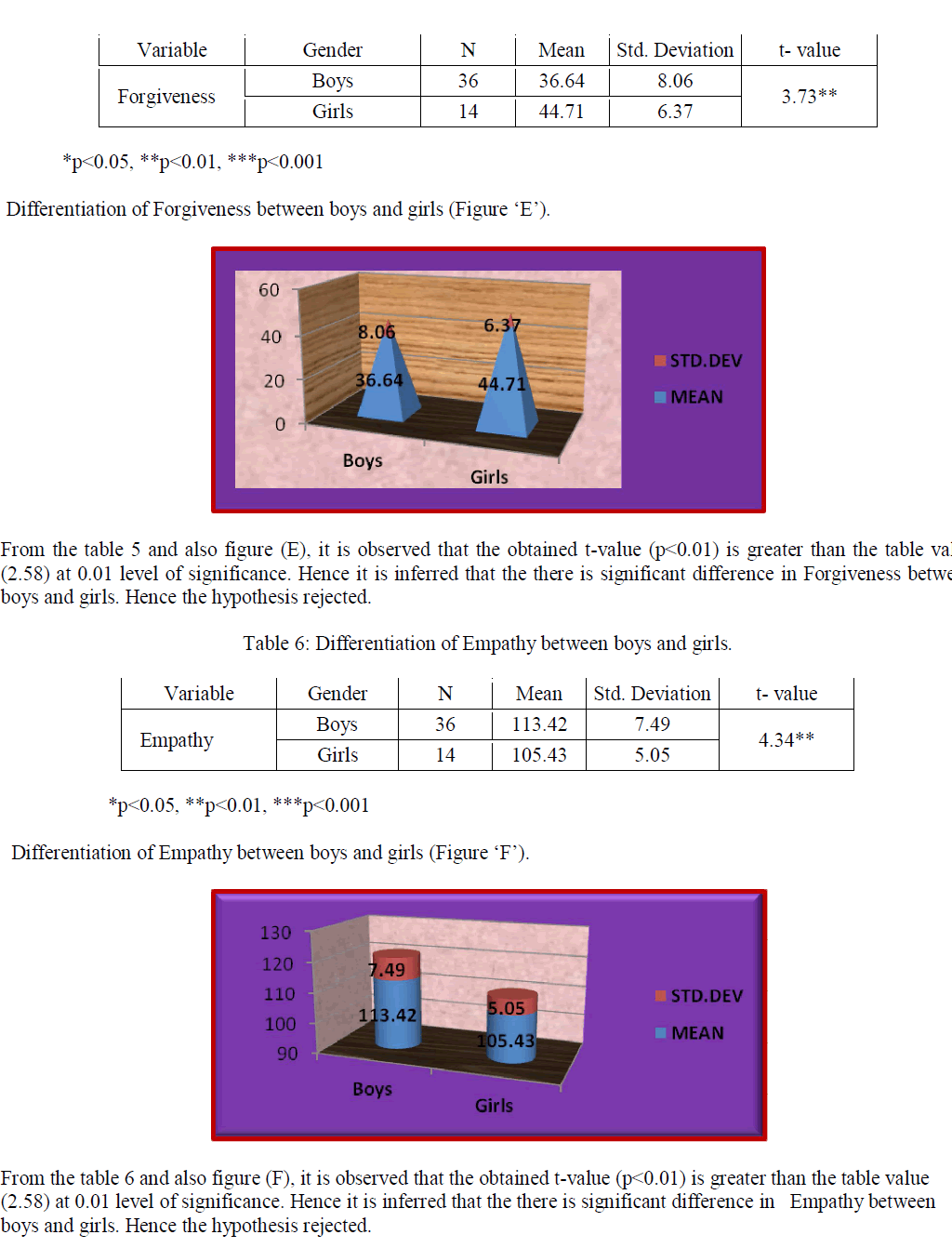
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
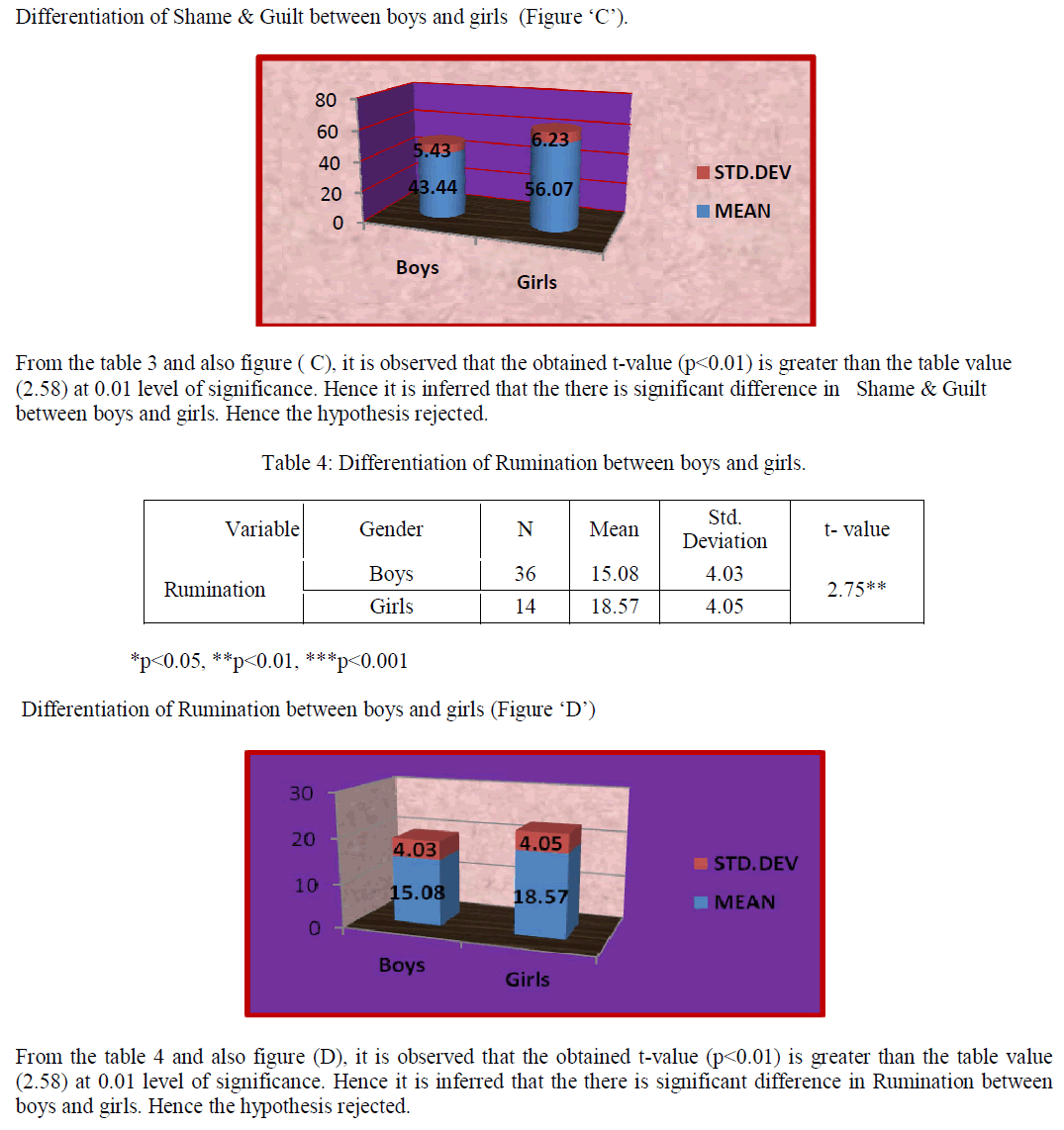
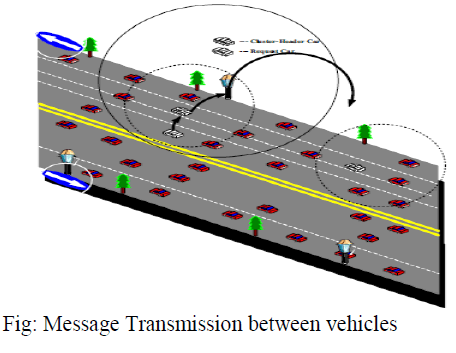
Vehicular AdHoc Networks or VANETs are emerging as a promising technology for providing safety and comfort applications for vehicular transportation. VANETs are receiving growing attention from the research community and from the transportation industry because of their great potential to improve traffic safety on roads. In existing system the IEEE 802.11 broadcasting mode, considers no request-to-send/clearto- send (RTS/CTS) handshaking process, because all of the nodes are within the range of a sending node and that node will be act as the recipients. Thus, the size of the potential hidden node activity‟s area is dramatically larger than the 802.11 unicast mode, which makes the communications more unreliable. In this work, the main objective is to show the hidden terminal problem, packet leakage and multi message broadcasting and the delay time has been reduced. To reduce the delay and overcome the single message broadcasting problem in the existing system, the probabilistic data structure is proposed. To address the degree of compatibility of the protocol Dedicate Short Range Communication (DSRC) method is used. The network operation mode is introduced for Dedicate Short Range Communication standardization. Thus the result of this work is to reduce the low priority messages and also determine the good tradeoff between network parameters.
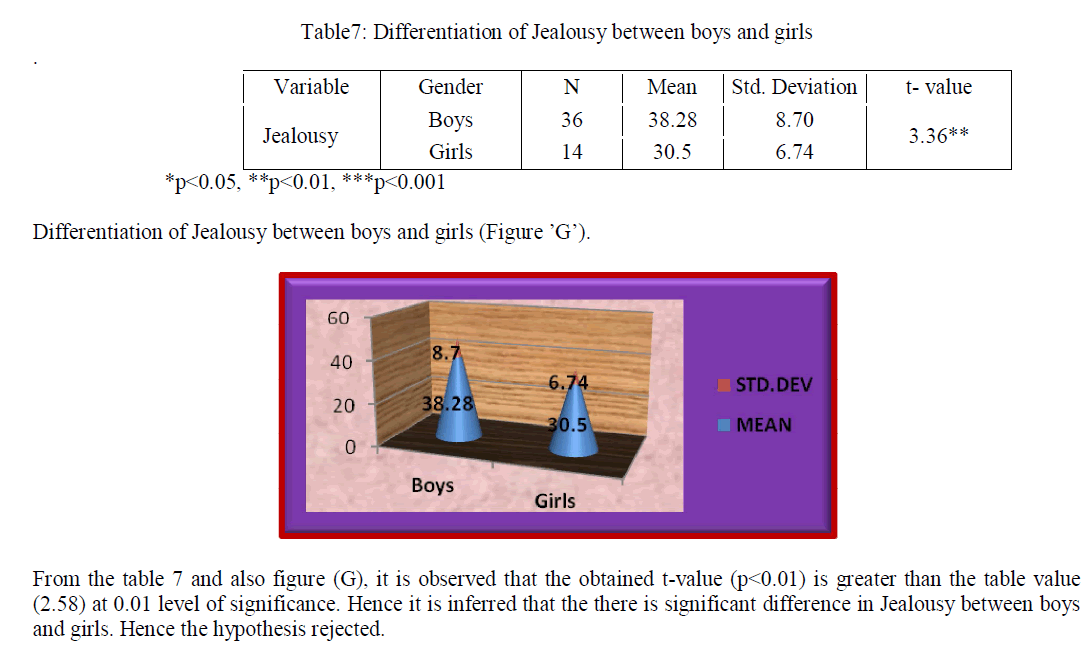
Keywords |
| DSRC,RTS/CTS. |
INTRODUCTION |
| WIRELESS SENSOR NETWORK |
| The Wireless Sensor Networks (WSN) is the emerging field that combines sensing, computation, and communication into a single tiny device. Wireless sensor network refers to a group of spatially dispersed and dedicated sensors for monitoring and recording the physical conditions of the environment and organizing the collected data at a central location. |
| The sensor node equipment includes a radio transceiver along with an antenna, a microcontroller, an interfacing electronic circuit, and an energy source, usually a battery. The size of the sensor nodes can also range from the size of a shoe box to as small as the size of a grain of dust. Each node of the sensor networks consist of three subsystems. They are sensor subsystem that used to senses the environment. Processing subsystem will performs local computations on the sensed data. Communication subsystem is responsible for message exchange with neighboring sensor nodes |
| VANET |
| A VANET turns every participating car into a wireless router or node, allowing cars approximately 100 to 300 meters of each other to connect and, in turn, create a network with a wide range. As cars fall out of the signal range and drop out of the network, other cars can join in, connecting vehicles to one another so that a mobile Internet is created. It is estimated that the first systems that will integrate this technology are police and fire vehicles to communicate with each other for safety purposes. The interactions with roadside equipment can likewise be characterized fairly accurately. And finally, most vehicles are restricted in their range of motion, for example by being constrained to follow a paved highway. |
| Vehicular ad hoc networks are also known under a number of different terms such as Inter Vehicle Communication (IVC), Dedicated Short Range Communication (DSRC) or WAVE. The goal of most of these projects is to create new network algorithms or modifies the existing for use in a vehicular environment. In the future vehicular ad hoc networks will assist the drivers of vehicles and help to create safer roads by reducing the number of automobile accidents. |
IEEE 802.11MAC PROTOCOL |
| The MAC protocol is used to collect the sensor node. They are small, inexpensive, with constrained power. They are organized in a cooperative network. They communicate wireless in multi hop routing. The MAC protocol provides two medium access methods: Distributed Coordination Function (DCF) and Point Coordination Function (PCF). The DCF is a contention protocol based on the Carrier Sense Multiple Access Protocol (CSMA), known as CSMA/CA, with CA standing for Collision Avoidance. It also uses small RTS/CTS (Request To Send / Clear To Send) packets to reserve the medium in order to avoid collisions due to problems involving a hidden terminal. The exchange of such control messages allows all the terminals within the receiving range of both the source and the destination terminals to defer transmission in order to allow successful delivery of a data frame. |
| The Network Allocation Vector, NAV, represents the duration stations sensing RTS/CTS signals which have to leave the medium idle to allow successful delivery of both a data frame and the corresponding acknowledgement. When the traffic of a station is backlogged, Request-To-Send messages are sent to notify the other stations that it wants to transmit a packet to a specific receiver. The receiver then notices the sender that it can transmit by sending a Clear-To-Send message. No other stations transmit any packet in a period corresponding to the transmission time of the packet to be sent. The small size of RTS/CTS control frames makes the probability of collision during their transmission lower than that of the collision of data frames, since these frames are usually larger than those involving RTS/CTS frames. |
RELATED WORK |
| Many approaches like DSRC, IEEE 802.11 MAC, hidden Terminal problem etc... Have been proposed to broadcast the safety message .This chapter covers such approach in brief .In [1] they proposed about an investigate the feasibility of showing safety applications based on beacon message dissemination method. This system introduced the performance of a single-hop dissemination protocol which helps to improve the Quality of Service (QoS) metrics like delivery rate and delay. Here a new metric of effective range is shown which gives the more accurate facility for evaluating QoS in safety applications .This method helps them to improve the performance of the three parameters vehicleâÃâ¬ÃŸs transmission range, message transmissionâÃâ¬ÃŸs interval time and message payload size. But they make a theoretical approach about improving the quality, safety application and they show in this IEEE 802.11. S. Eichler (2007) They proposed about a method of performance evaluation. It provides the collision probability, throughput and delay, using simulations and analytical method. This system sends the message in WAVE method. It will prioritise the message to reduce the throughput. The EDCA method was used in WAVE to prioritizing the message. Here control channel and service channel will use the different packet queues so the collision will occur in high rate.so the message will show the collision warning. This system mainly focused about the reduction on collision of message transmission through WAVE. |
| X. Ma, X. Chen, and H. H. Refai(2008), In this paper, they explained about the performance of broadcast service in IEEE802.11 based on 1-D method. This paper shows the MANET (mobile ad hoc network) method under the multihop environment. But they mainly focuses about the IEEE 802.11 back off counter process and hidden terminal problem. Here an analytical model proposed the packet reception rates in IEEE802.11 based on broadcast MANET. The packet reception rate (PRR) used to reduce the hidden terminal problem and increasing the carrier sensing range.[4]Mohammad Ali azimi, They discussed about a new metric solution it focused on the significance of coverage in safety scenarios is called effective range which is based on the satisfaction of restrict quality of service. The beacon based application may tolerate some message loss. The beacon safety message in Vehicular Ad-hoc Networks (VANETs) suffers from poor reliability especially in congested road traffics. The main aim of this problem is CSMA nature of Dedicated Short Range Communications (DSRC) in MAC layer. So in this paper they used a scheduling algorithm for making the geographical sections. In each section, they form a cluster between moving vehicles. Then it performs a scheduling in two levels. In the first level, they describes about the nonadjacent clusters can transmit messages at the same time. While the second level of scheduling deals with inside of each cluster in which we implement a TDMA-like approach.The results show that the algorithm improves the reliability in beacon message dissemination. So the accuracy of the information which each vehicle can obtain from its neighbouring vehicles is significantly increased. Thus this scheduling scheme leads to considerable enhancement of the safety level provided by Beacon Safety Messages (BSMs). |
| But in this paper their output was shown in graphical but they didnâÃâ¬ÃŸt implemented VANET method. They show their collision reduction in algorithmic way they didnâÃâ¬ÃŸt simulate with node. |
| Dedicated Short-Range Communication (DSRC) This book discussed about the DSRC model in theoretical way. The (DSRC) technology, for use in vehicle-tovehicle and vehicle-to-roadside communication. The effectiveness of this technology is highly dependent on cooperative standards for interoperability. This shows the content and status of the DSRC standards and the IEEE 802.11p for wireless access in vehicular environments (WAVE), methods. The main motivation for developing DSRC is to enable collision prevention applications. These applications depend on frequent data exchanges among vehicles, and between vehicles and roadside infrastructure. It will calculate the distance between the two vehicles and helps to avoid the accident. |
IEEE 802.11MAC PROTOCOL |
| The MAC protocol provides two medium access methods: Distributed Coordination Function (DCF) and Point Coordination Function (PCF). The DCF is a contention protocol based on the Carrier Sense Multiple Access Protocol (CSMA), known as CSMA/CA, with CA standing for Collision Avoidance. It also uses small RTS/CTS (Request To Send / Clear To Send) packets to reserve the medium in order to avoid collisions due to problems involving a hidden terminal. The Network Allocation Vector, NAV, represents the duration stations sensing RTS/CTS signals which have to leave the medium idle to allow successful delivery of both a data frame and the corresponding acknowledgement. When the traffic of a station is backlogged, Request-To-Send messages are sent to notify the other stations that it wants to transmit a packet to a specific receiver. The receiver then notices the sender that it can transmit by sending a Clear-To-Send message. No other stations transmit any packet in a period corresponding to the transmission time of the packet to be sent. The small size of RTS/CTS control frames makes the probability of collision during their transmission lower than that of the collision of data frames, since these frames are usually larger than those involving RTS/CTS frames. |
OVERVIEW OF THE PROJECT |
| In this project, the main objective is to show the hidden terminal problem, packet leakage and multi message broadcasting and the delay time has been reduced .To reduce the delay and overcome the single message broadcasting problem in the existing system, the probabilistic data structure. To address the degree of compatibility of the protocol DSRC method is used. The network operation mode is introduced for Dedicate short range communication standardization. Thus the result of this work is to reduce the low priority messages and also determine the good tradeoff between network parameters. The safety message will be broadcasted according to their distance between the vehicles. |
SYSTEM ANALYSIS |
EXISTING SYSTEM |
| In existing system the IEEE 802.11 broadcasting mode considers no Request-To-Send/Clear- To-Send (RTS/CTS) handshaking process, because all of the nodes within the range of a sending node are assumed as recipients. Thus, the size of the potential hidden node activityâÃâ¬ÃŸs area is dramatically larger than the 802.11 unicast mode, which makes the communications more unreliable. Lower reliability in broadcast communication due to higher collision rates and hidden-terminal activities is another challenge that needs to properly be handled in VANETs |
ISSSUES |
| The main problem is only one message will be broadcast at a time. There was a hidden terminal problem and Lower reliability in communication. They used IEEE 802.11, so it has RTS\CTS problem and low reliability in broadcasting the message because of high collision. |
PROPOSED SYSTEM |
| In the proposed system a novel analytical model is used to determine the main performance measures of VANETs with two traffic priority classes. This modeling took a multihop perspective rather than the generalization of single-hop results, which captures the dynamics of the system such as the hidden-terminal activity better. Later that the arrival time of a message to the channel corresponds to the moment that its back off counter reaches zero, after which the message is transmitted. Therefore, the medium access control (MAC) back off time was considered part of the message interarrival time, and the effect of the messages in a back off process was neglected due to mathematical complexities. The safety message will show the distance between the node and calculate the distance of the vehicle. The probalistic data structure will limit the acknowledgement size. The RTS/CTS will limit the acknowledgement problem. |
TECHNOLOGY USED |
INTRODUCTION TO UBUNTU |
| Ubuntu is composed of many software packages, the majority of which are free software. Free software gives users the freedom to study, adapt/modify, and distribute it. Ubuntu can also run software. Ubuntu comes installed with a wide range of software that contains LibreOffice, Firefox, Empathy, Transmission, and several lightweight games (such as Sudoku and chess). Additional software that is not installed by default (including software that used to be in the default installation such as Evolution, GIMP, Pidgin, and Synaptic) can be downloaded and installed using the Ubuntu Software Center or other apt-based package management tools. Programs in the Software Center are mostly free, but there are also priced products, including applications and magazines. Ubuntu can also run many programs designed for Microsoft Windows (such as Microsoft Office), through Wine or using a Virtual Machine (such as Virtual Box or VMware Workstation). |
| Ubuntu Desktop includes Unity, a graphical desktop environment. The Ubiquity installer allows Ubuntu to be installed to the hard disk from within the Live CD environment. GNOME (the former default desktop) supports more than 46 languages. For increased security, the sudo tool is used to assign temporary privileges for performing administrative tasks, allowing the root account to remain locked, and preventing inexperienced users from inadvertently making catastrophic system changes or opening security holes. Policy Kit is also being widely implemented into the desktop to further harden the system through the principle. Ubuntu can close its own network ports using its own firewalls software. End-users can install Gufw (GUI for Uncomplicated Firewall) and keep it enabled. |
INTRODUCTION TO NS2 |
| NS-2 is an open-source simulation tool running on Unix-like operating systems. It is an object oriented and discrete event simulator targeted at networking research and provides substantial support for simulation of routing, multicast protocols and IP protocols, such as UDP, TCP, RTP and SRM over wired, wireless and satellite networks. It has many advantages that make it a useful tool, such as support for multiple protocols and the capability of graphically detailing network traffic. Additionally, NS-2 supports several algorithms in routing and queuing. |
| There are presently five schedulers available in the simulator, each of which is implemented by using a different data structure: a simple linked-list, heap, calendar queue (default) and a special type called ''realtime''. The scheduler runs by selecting the next earliest event, executing it to completion, and returning to execute the next event. An event is handled by calling the appropriate Handler class. The most important Handler is NsObject with TclObject as its twin in the OTcl world. They provide all the basic functions allowing objects to interact one with another. For this purpose the receive function group is mainly used. For handling OTcl statements in C++ Ns Objects provide the so-called command function |
SYSTEM DESIGN |
BLOCK DIAGRAM FOR THE PROPOSED SYSTEM: |
| SYSTEM ARCHITECTURE |
 |
MODULE DESCRIPTION |
| NETWORK TRACKING MODULE: |
| The IEEE 802.11 broadcasting mode considers no request-to-send/clear-to-send (RTS/CTS) handshaking process, because all of the nodes within the range of a sending node are assumed as recipients. Thus, the size of the potential hidden node activityâÃâ¬ÃŸs area is dramatically larger than the 802.11 unicast mode, which makes the communications more unreliable. Each node sends messages to allow other nodes to detect it. Once a node detects messages from another node (neighbor), it maintains a contact record to store information about the neighbor. Using multicast socket all nodes are used to detect the neighbor nodes. This Model fits many application that gather data from environment as user specified rates. |
HIDDEN TERMINAL PROBLEM |
| In this module we mainly focus about the hidden terminal problem. Here each node movement will be shown by their energy level. Each node activities will be monitored by the Road Side Unit (RSU). The message sending and dropping will be monitored by RSU. If the two nodes are sending the message at a time to another node then the hidden terminal problem will occur. So in this module we show that problem where it occurs and how the message send and received. While the hidden terminal problem occurs the message will be dropped so we have shown that dropped node activities in terminal. |
 |
 |
| DSRC |
| Thus, it considers the IEEE 802.11 MAC protocol in broadcast mode, as suggested for VANETsâÃâ¬ÃŸ safety applications. Briefly, in broadcast, unlike unicast communication, a back off process is performed only once for a new generated message and no binary back off process is employed. Broadcasting is highly appropriate to disseminate safety messages in VANETs, be-cause all nearby vehicles are considered destination nodes, and less time will be spent for medium access process. However, the lack of RTS/CTS handshaking and packet acknowledgment makes the communication more vulnerable to interferences and hence results in lower communication reliability. Its main function is it will calculate the distance between the two nodes. |
 |
| DESCRIPTION |
| In this module we mainly focused about the showing the distance between the node. This method will calculate the distance between the node and it will take the distance as the minimum and maximum criteria. The minimum criteria will show the critical situation of the node. Here we estimate a particular distance for calculation if the node enters into that node the RSU will monitor their situation. The RSU will monitor about the path leaving and path joining of the node. If the node leaved from the road it will show the safety message about their activities. The DSRC will calculate the new entry arrival node distance also. The minimum distance between the nodes will show in safety message. |
| VIRTUAL TRANSIMISION: |
| In this module is used to show the transmission between the nodes and calculate the performance of the safety message broadcasting. The results are obtained from based on the above topology. Here the novel analytical model is used to determine the main performance measures of VANETs with the traffic priority classes. Therefore, the medium access control (MAC) back off time was considered part of the message inter arrival time, and the effect of the messages in a back off process was neglected due to mathematical complexities Evaluate the impact of the Virtual transmissions approach presented. We measured the performance when the number of parents is varied from one to three. The results are obtained from based on the above topology. This module is used to show the performance of the DSRC model and the network tracking model |
| Architecture: |
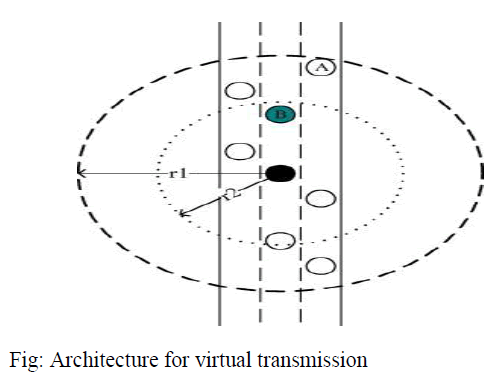 |
CONCLUSION AND FUTURE ENHANCEMENT |
| Thus the result of this project shows the safety message about node activities and determines the hidden terminal problem also. Thus the packet leakage and multi message broadcasting and the delay time has been reduced .To reduce the delay and to overcome the single message broadcasting problem the probabilistic data structure method is used and it will be list in beacon message process . The network operation mode is introduced for Dedicate short range communication standardization. Thus the result of this work is to reduce the low priority messages and also determine the good tradeoff between network parameters. The safety message will be broadcasted in table. The result of this system will be performed in the simulation method. The virtual transmission method will calculate the performance of the safety message broadcasting. Each method will be derived in mathematical model. In future we have planned to continue working on ABSM in the vehicular context. |
References |
|