ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
R.Gopi1, Ramsna Ramesh2, V.Shafla Shinu2, Sonam.S2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Each application have different Qos (quality of service) in same platform on wireless sensor network. We are proposing coldspots technique and multi path relay algorithm using coldspots technique. It improve the data fidelity and end to end delay of the sensitive to overcome problems like delay minimization and high data integrity and data fidelity. By applying a virtual hybrid potential field IDDR separates packets based on their weight.And the packets are forwarded to the destination through different path applications.Data fidelity can be improve by collecting idle buffer space or under loaded paths to cache excessive packets.For prioritizing packets transmission we are using lyapunov drift technique. IDDR also provide good energy efficiency and scalability.
Keywords |
| Wireless sensor network, data integrity, data fidelity, IDDR, Virtual hybrid potential field |
INTRODUCTION |
| Wireless Sensor Networks (WSNs) are envisioned to be the next generation of networks which will form an integral part of man’s lives andwhich Provide a bridge between the real physical and virtual worlds. WSNs should be able to support various applications over the same platform. Different applications might have different QoS requirements. For instance, in a fire monitoring application, the event of a fire alarm should be reported to the sink as soon as possible. On the other hand, some applicationsrequire most of their packets to successfully arrive at the ssink irrespective of when they arrive. For example, in habitat monitoring applications, the arrival of packets is allowed to have a delay, but the sink should receive most of the packets. |
| WSNs have basic QoS requirements: low delay and high data integrity, leading to what are called delay sensitive applications and high-integrity applications, respectively. Generally, in a network with light load, both requirements can be readily satisfied. However, a heavily loaded network will suffer congestion, which increases end to end delay.We try to improve the fidelity for high-integrity applications and decrease the end-to-end delay for delaysensitive , when the network is bottlenecked. We use the concept of potential field from the discipline of physics and design an integrity and delay differentiated routing (IDDR). |
| 1. Improve fidelity for high-integrity applications: We try to find free and unused path to cache excessive packet for efficientTransmission on shortest path. |
| 2. Decrease end-to-end delay for delay-sensitive applications: Assign weight to each application or data.Based on their weight transmission paths are choosen. i.e larger weight packet choosen shortest path and priority queue is used to reduce delay in queuing. |
RELATED WORKS |
| For example, the standard shortest path tree (SPT) routing will forward all of them to node 1 as shown in Fig. (a) This will cause congestion and thus lead to many high integrity packets loss and large end-to-end delay for delay sensitive packets. A multipath routing algorithm can fig (b) utilize more paths to avoid hotspots. However, the lowdelay and high throughput are hardly metsimultaneously |
| 1. Delay-sensitive packets occupy the limited bandwidth and buffers, worsening drops of high-integrity ones . |
| 2. High-integrity packets block the shortest paths, compelling the delay-sensitive packets to travel more hops before reaching the sink, which increases the delay. |
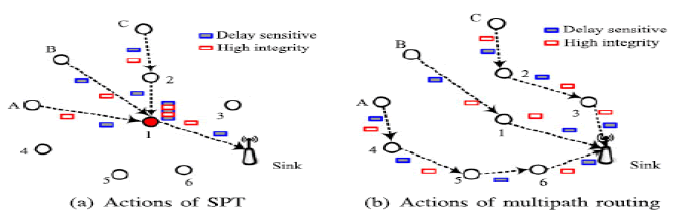 |
| 3.High-integrity packets occupy the buffers, whichalso increases the queuing delay of delay-sensitivepackets. |
PROVIDING REAL TIME AND RELIABILITY SERVICE: |
| Implicit Earliest Deadline First (EDF) mainly utilizes a medium access control protocol to provide real-time service. SPEED mechanism maintains a desired delivery speed across the network through a novel combination of feedback control. Two-hop neighbor information-based gradient routing mechanism is proposed to enhance real time performance. ReInforM uses the concept of dynamic packet states to control the number of paths required for the desired reliability.LIEMRO utilizes a dynamic path maintenance mechanism to monitor the quality of the active paths during network operation .SPEED mechanism use to satisfy the delay requirements for different types of traffic, and uses redundant paths to ensure reliability. MAC layer function continues transmit from source node to sink node even when network is congested without using some other mechanism. Energy-Efficient and QoS based Multipath Routing Protocol (EQSR) improves reliability through using a lightweight XOR-based Forward Error Correction (FEC) mechanism, which introduces data redundancy in the data transmission process, EQSR employs a queuing model to manage real-time and non-real-time traffic. |
IDDRAND POTENTIAL FIELD |
| IDDR differentiate the packet using weight values in header of packets and then perform different actions.Potential Field whose shape looks like a bowl. All data packets are transmitted to the bottom along the surface like water. In WSNs with light traffic, IDDR works similar to the shortest path routing algorithm. But in WSNs with heavy load, large backlogs will form some bulges on the bowl surface. The bulges will block the paths and prevent packets from moving down to the bottom directly. |
| To provide the basic routing function, i.e., to make eachpacket move towards the sink, the proposed IDDRalgorithm defines a depth potential field Vv d(t)=Dv(t)where Dv(t) is the depth of node v at time t. Thus the depthfields force Fd v w(t) from node v to its neighbor is |
| Fd v w (t) =Dv (t) -DW(t) |
| Two nodes with more than one hops distance cannot become neighbors. virtual hybrid potential on the basis of thedepth and queue length potential fields IDDR has two steps |
| • Finding enough buffer spaces from the idle or underloaded nodes, which is actually resource discovery. |
| • Caching the excessive packets in these idle buffers efficiently for subsequent transmissions, this implies an implicit hop by-hop rate control. |
| Virtual hybrid potential proposes two effectivemechanisms to decrease the end-to-end delay of delay-sensitive packets. |
DELAY-DIFFERENTIATED SERVICES |
| There are factors which affect end to end delay are Transmission delay, Competition of the radio channel. ,Queuing delay, Path length.The IDDR aims to decrease the queuing delay and shorten the path length for delay sensitive packets. |
PACKET WEIGHT |
| Packet header contains a 8-bit weight to represent the level of delay sensitivity. The larger is the weight, the more delay-sensitive is the packet. IDDR uses the weight values to build different potential fields with different slope |
| α' = α+ packet weight÷0xff |
| 0xff maximum of the 8-bit weight.α' higher weight depth potential field so packet with larger weight out of shortest path light ones with smaller weight. They will immediately occupy most of the buffer along the shortest paths. The backlog filled by the heavy packets will further reject the light ones. IDDR will find other nodes and paths to cache the light packets to improve their throughput, while the shortest paths are used to forward the heavy ones to decrease their end-to-end delay. |
QUEUING TECHNIQUE |
| To decrease the queuing delay, IDDR employs the priority queue mechanism to allow the delay-sensitive packets to be transmitted prior to the other packets. Specifically,the most heavy packets are transmitted first and the othersare ranked according to their weights. The packets with thesame weight are ordered according to their arrival time. |
IDDRALGORITHM |
| WSN with different high-integrity or delay-sensitiveapplications. Let c be the identifier of different applications. In summary, the main procedure of the IDDR algorithm at node i works as follows: |
| 1. If the queue at node i is not empty, thenα' = α+ packet weight÷0xffis computed for packet p at the head of the queue. |
| 2. Let Wi,b (t)={(Qi (t) +α( c) Di (t)) –(Qb (t) +α( c ) Db (t))}Select the next hop b* =argmax b belongs Ω i(t) ,Q j (t) ≠ 1 W i,b (t). |
| 3. Node i send packet p to node b. Go to (1). |
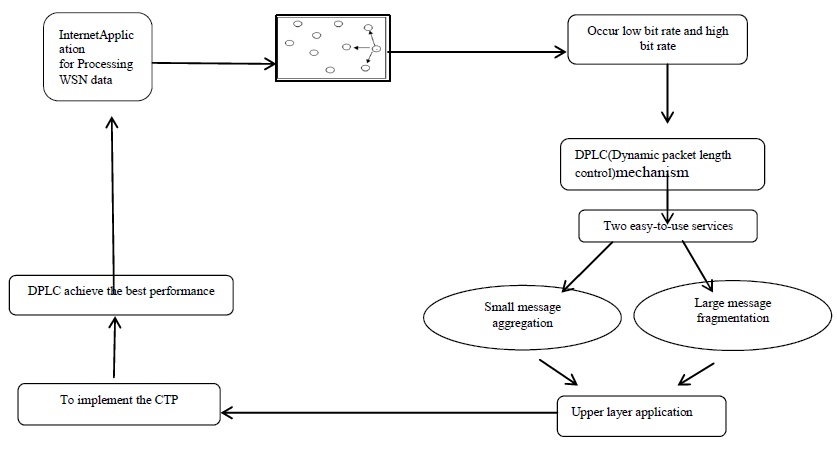
DPLC MECHANISM |
| DPLC more efficient in terms of channel utilization, we incorporate a lightweight and accurate link estimation method that captures both physical channel conditions and interferences. We further provide two easy-to-use services, i.e., small message aggregation and large message fragmentation, to facilitate upper-layer application .The work of requires the sender to measure the channel availability period for adaptation. The fragmentation service is useful for bulk data transmission. Aggregation Service is useful for small data collection.Aggregation Service send the data to sink node. |
SYSTEM ARCHITECTURE: |
 |
COLD SPOT AND POWER AWARE METRICS |
| Cold spot if the utilizations of all its resources are below a cold threshold. This indicates that the server is mostly idle and a potential candidate to turn off to save energy. Transmission power depends on distance between nodes and corresponding shortest power algorithm .power cost metrics based on combination of both nodes life time and distance based power metrics. |
PERFORMANCE ANALYSIS |
| The proposed IDDR algorithm needs to be stable and Lyapunov drift technique is used to prove IDDR is stable. Lyapunov functions are used extensively in control theory to ensure different forms of system stability. Lyapunov drift is central to the study of optimal control in queueing networks. A typical goal is to stabilize all network queues while optimizing some performance objective, such as minimizing average energy or maximizing average throughput. |
SIMULATION AND RESULTS |
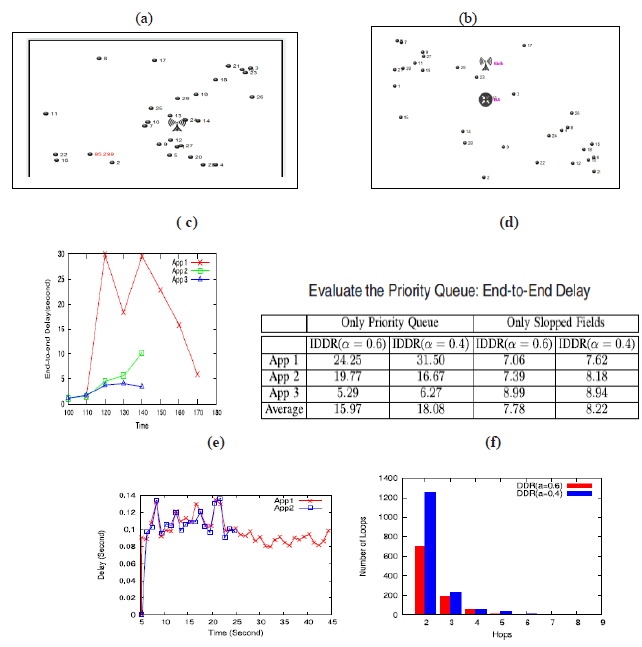
| Figures shows the results of transfer packets and application end to end delay ratio fig (a) show that IDDR differentiate the packet using weight values forward to sink node fig(b) Aggregation Service send the data to sink node. Fig (c) plots the average end-to-end delay of each application we can see that both of the delay-sensitive applications gain a steady low delay while App 1 suffers much larger delay. Table (d) we can conclude that the priority queue significantly influences the performance of IDDR. On one hand, without the different sloped fields, delay-sensitive packets will be driven out of the shortest path and compelled to travel more hops before reaching the sink. Fig (e) Average packet delay of each application under IDDR on the test. Fig(f) Distribution of hops and energy consumption of each packets. |
 |
CONCLUSION |
| Concept of potential in in physics to satisfy the two different QoS requirements, high data fidelity and low end-to-end delay, over the same WSN simultaneously.IDDRprovides good scalability. |
References |
|