Keywords
|
| User Recommendation, Spammers, ALAC algorithm, Videos, User, Provider, Uploading, Filtering, Ranking. |
INTRODUCTION
|
| According to Cisco’s latest forecast, simple fraction of the world’s mobile information traffic and sixty two of the patron net traffic are video by the top of 2015. The add of all kinds of video (TV, video on demand, Internet, and P2P) can still be or so ninetieth of worldwide client traffic by 2015. Net users post an outsized variety of video clips on video-sharing websites and social network applications every day. The video content is also duplicate, similar, related, or quite totally different. Facing billions of transmission websites , on-line users ar sometimes having a tough time finding their favorites. this example is even worse for mobile users as a result of screen limit and low information measure. the way to facilitate mobile user acquire their desired content lists from billions of websites in a brief time is incredibly difficult.[1] |
| . Some video-sharing websites advocate video lists for finish users in step with video classification, video description tags, or observance history. However, these recommendations don't seem to be correct and are perpetually not in step with the top users’ interests. To enhance this, some websites additionally give users with computer programme the search their desired videos quickly. However, looking is predicated on the keywords.[7] Multimedia recommendation system are based on the user request, they are most widely used in Social networks, IPTV, other social medias and they are the efficient one that deal with the overloading of information and are most widely used to analyze, find the methods for recommendation context. Generally, the recommendation techniques are classified as two categories: Collaborative technique, content based techniques based on the preferences of user unknown item and their previous technique .[10] The large multimedia content will cause the information overload problem, to avoid this it is important to create a personalization technique that recommend appropriate contents to the users. The problem of information overload points out that it requires a extraction of information and the data mining system which helps to identify the unused information and it identifies whether a user like the given data. |
| Recommended system may guide the people to make their own decision like what to buy, what to watch, especially useful in the large amount of data. Recommended system helps to find out the choices or to decide the solution without any previous experiences, although they are famous in various concepts and familiar with many related works, some of their problems are still continuing in the market, the problem may be estimated as the rating of items, and one of the important and main issue is the low-performance that too in generic applications, other related issues may be the limited content analysis, data sparsity etc.[2] In this paper section I the description about introduction on multimedia systems, In section II the related work describes the existing system work, section III explained the User Video Recommendation ,section IV explained the experiment setup and result and finally section V and VI the paper was concluded with References. |
II.RELATED WORK
|
| In this Yonggang Wen, Xiaoqing Zhu, Joel J.P.C rodrigues, Chang Wen Chen [1] proposes on cloud media with two views namely (i) end-end view and (ii)cloud-view, using the Cloud Centric media platform (CCMP) developed at Nan yang Technological university, the outlooks covers the following like the improved performance, lower cost, better, Qos ,human-centric and it concludes with the realization of cloud mobile media vision. This Jinsul Kim,Ilmin kim,Beyung-ok Jang [2] surveys research on the users ,using the SNS and IPTV and in order to provide a suitable platform for the simplified social TV based on the Hadoop Map Reduce ,the proposed social TV methods improves or extends the simple functions like chatting, shopping service and their comments, At present the Social TV uses the Java Development Kit Set Up Box. |
| The V.Venugopal ,R.Revathi [3] proposes a new method called Mobile Video Streaming Method based on the cloud by using User- Adaptive Mobile Video Streaming(AMoS),the User behavior Oriented Video pre-Fetching(UBoP)and the video quality is depended on the feedback of the link quality, this could conclude that the cloud works effective on the video streaming and sharing. This Hong-YiChang,Chih-ChunLail,yuan-weiLin [4] is based on the user’s historical information and can be achieved through the internet of things, they worked with the DCXP(Distributed Context Protocol) where it reduces the number of subscription that reduces the overall cost and it shows the infrastructure that are connected. In Hong-YiChang,Chih-ChunLail,yuan-weiLin [5] surveys on fast scalable video coding(svc) based channels recommendation by applying IPTV in the cloud using peer to peer hybrid ,here the feedback looser tree algorithm is used to find out the user’s previous history and it identifies the users interest very fast. |
| This Jaqueline Ferreira de brito,Luciano Antonio Digiampietri, [6] proposes a recommendation system that deals efficiently with the overloading of the information that is the internet reality which analyze, identifies the methods for the recommendation context by Naïve Bayes ,k-NN and the CBF algorithms also it provides the higher results for the all the models. In Nana Yaw Asabere [7] is based on the hybrid recommendation system from the perspective of the types, architectures, and applications, algorithm to overcome the recommendation system problems by applying the hybrid CBF and CF methods, In Pedro M.P.Rosa,Joel J.P,C Rodrigues,Fillippo Basso[8] proposes a mobile based recommendation on the basis of location, habit by using the weight awareness data fusion algorithm that combine various data fusion algorithms like comb SUM for small amount of documents and and combMNZ for large number of documents. |
| This Miao LV,Chun JIN, Jim c.HAN, Yoshiyuki HIGUCHI [9] surveys on the ontology based preference of the user Bayesian Model that avoid the traditional problem, it also forms the Bayesian network that represents the user’s characteristics, preferences and their contexts and it produce the accurate results, |
| In Zibin Zheng, Hao Ma, Irwin King ,Michael R.Lyu [10] proposes a WSRec method that avoid the selection of the web and designing and Qos is achieved by applying this using the Java language also applied to the real world environment. In Abdelkar Outtagarts [11]surveys a method that could use infrastructure of the network which may share the other remotes sites until it get the target result also co-operate with the other related site and also return to their own home page once completing their task, this may be based on the content sharing, filtering and ,monitoring and so on. In UmaraniG.R, Dr.C.Nalini [12] is a survey based paper to detect spammers using ALAC algorithm. |
III. USERS VIDEO RECOMMENDATION (UVR)
|
| User’s video recommendation system is based on the report of user’s previous history, so it is useful to detect the Spammer, so this can avoid the posting of unrelated videos, Normally the videos are filtered using collaborative based filtering and content filtering etc .But here we are using a ALAC algorithm to classify the videos based on the user’s history. User Recommender systems have changed the way of users to the find products, information, and even other people. They study the patterns of behavior to know that what someone will prefer from among a collection of things he has never experienced. The technology behind recommender systems has evolved over the past 20 years into a rich collection of tools that enable the practitioner or researcher to develop effective recommenders. We will study the most important of those tools, including how they work, how to use them, how to evaluate them, and their strengths and weaknesses in practice. |
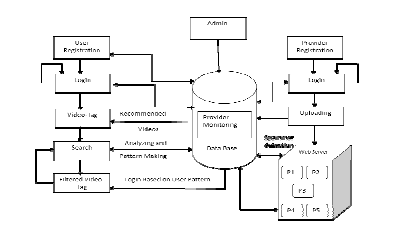 |
| III.Fig 1:OVERALL ARCHITECTURE DIAGRAM |
| The Database present here will have every information about the system which is maintained by the admin. The database will be linked to the web Server .The each and every user will register and login and then user will tag for the video. At the time of tagging the video he will get the recommended videos from provider monitoring which is in the database and has all the video information from the web server. After user tags the video then by Pattern making and analyzing the video tag will be filtered and provided to the user. Users can recommend the videos to the user itself, at the time of user profile creation. The Recommended videos post to the client profile as cloud-tag video system. The cloud-tag is generated based on the user Recommended. In same way the video providers will register and login and then upload the video file to the web server and then it will be directed to the provider monitoring in the database. Videos upload from provider is stored to the own Storage space. Video files are uploading to cloud server based on the keywords. This is the private cloud storage space, they can assess and view there video files only. Spammers may post an unrelated video as response to a popular one. We detect the spammers using customer suggestion private storage formation process. Supervised classification algorithms to automatically detect spammers. The admin will have the whole control over the system. |
 |
| We make a Private Storage Space for every Providers in our media storage Server. At the time of creating a Provider account the video storage space will be allocated to the provider. That memory of the storage space is not a fixed, it can large-scale storage .From this format we can uphold videos confidentially. |
 |
| Users can recommend the videos to the user itself, at the time of user profile creation. The Recommended videos post to the client profile as video tag system. The video tag is generated based on the user Recommended. Recommender Systems or recommendation systems (sometimes replacing "system" with a synonym such as platform or engine) are a subclass of information filtering system that seek to predict the 'rating' or 'preference' that a user would give to an item (such asmusic, books, or movies) or social element (e.g. people or groups) they had not yet considered, using a model built from the characteristics of an item (content-based approaches) or the user's social environment (collaborative filtering approaches). Recommender systems have become extremely common in recent years. |
 |
| A content-based recommendations system recommends the most likely matched item. To compares the recommendation list to a user’s previous input data or compared to preference items. A content-based recommendations system is based on information searching and generally uses a rating method which is used in the information searching. The Profile Filtering Agent (PFA) creates a personalized channel profile based on the accumulated viewed content list by using a content based filtering. |
 |
| Fig 5:SPAMMER DETECTION |
| Spammers may post an unrelated video as response to a popular one. We detect the spammers using customer suggestion private storage formation process. lazy associative classification algorithms to automatically detect spammers. Classifying them as spammers, promoters, and legitimate users. Using our test collection, we provide a characterization of content, individual, and social attributes that help distinguish each user class. We investigated the feasibility of applying supervised learning methods for identifying the two envisioned types of polluters. We consider two state-of-the-art supervised classification algorithms, namely, support vector machines (SVMs) and Active lazy associative classification (ALAC) |
| III.(b)ALGORITHM |
| A computing platform distributed in large-scale data center. Uses Virtualization technology to dynamically and transparently supply virtual, Computing and storage resources. A search system ranked lists of top videos. Detection of Spammers, Reusability and extensibility of this framework component. ALAC (Active lazy associative classifier), which relies on an effective selective sampling strategy to deal with the high cost of labeling large amounts of examples. ALAC was extended to allow itself to select the subset of examples to be labeled, thus performing active classification. It does this sequentially, using the requested labeled examples to inform its decision of which example to select next. The hope is that by only requesting the labels of most informative examples, ALAC can learn to detect spammers and promoters using significantly fewer labeled examples than would be required if the examples were randomly sampled. Next, we describe the sampling function used by ALAC as well its stop condition. |
| The classification results discussed in the previous section are obtained assuming that the correct identification of a user is equally important for users from all three classes. However, there might be scenarios in which a system administrator could prefer to correctly identify more users from one class at the possible expense of misclassifying more users from the other classes. For instance, a system administrator, who is interested in sending automatic warning messages to all users classified as spammers, might prefer to act conservatively, avoiding sending messages to legitimate users by mistake, even if this comes at the cost of reducing the number of correctly identified spammers and/or promoters. In contrast, another system administrator, who adopts the policy of manually inspecting each user flagged as polluter before sending a warning, might prefer to favor the correct detection of spammers. In that case, misclassifying a few more legitimate users has no great consequences, and may be acceptable, since these users will be cleared out during manual inspection. Let D be the set of all n training instances, Let T be the set of all m training instances |
| 1. for each ti € T do 2. let Dtt be the projection of D on features only from ti |
| 3 .let ct tt be the set of all rules{x→c} m ined from Dtt 4. sort Ct tt according to information gain 5. pick the first rule {X→c}€Ct tt,and predict class c |
IV.EXPERIMENTAL SETUP
|
| The software used here as follows: Windows Operating System 2000 and Above ,JDK 1.6,JSP & Servlets ,Tomcat 6.0,the hardware used here is Hard Disk of 40GB and Above, RAM 512MB and Above Processor, Pentium IV and Above. Sports, Cinema, Cartoon, Entertainment, News ,Songs and Research videos. The exact that we is the user provides the record as dislike then the video is deleted from the user page alone and in the video recommendation table the rank is recorded and if it reaches 10 then the video will be deleted from the entire page, if the rank reaches 30 then the provider login is not allowed. |
 |
| The uploading entries window shows the various videos that has been uploaded for various users request criteria. This window may appear once the user or provider login into the form after registration. |
 |
 |
| The above table gives the video information which was uploaded by the provider. At first the home page is created then the registration form for both User and Provider was created ,the user is allowed to upload the videos after he signed in with the user name and password, the user can login with their User name and Password based on the category ,the videos uploaded by the provider can be viewed by the user and they can record their result as Like or Dislike based on the results the video is deleted and it is useful to detect Spammer. |
V.CONCLUSION
|
| Promoters and spammers can pollute the retrieval of video in online, the satisfaction of the user is important but also with the usage of the resources and effective delivery to the user, hence the proposed method will provide a effective solution that may help the system administrator to detect the promoters and spammers easily. |
References
|
- Yonggang Wen, Xiaoqing Zhu, Joel J.P.C rodrigues, Chang Wen Chen,” Cloud Mobile Media :Reflection and Outlook” ,2014,ISSN:1520-9210.
- JinsulKim,Ilminkim,Beyung-ok Jang “Research on user customized social mobile platform base on Personalized TV through IP networks”,2014,ISSN:1975-0080.
- V.Venugopal ,R.Revathi ,”user adaptive Mobile Video streaming and user Behavior oriented video Pre-fetching in cloud”, 2014, ISSN:2319-8753.
- Jamie walters,TheoKanter and Rahim Rahmani,”Adaptive Information Provisioning in Distributed Context Centric Architectures”,2014 ,ISSN:1694-0784.
- Hong-YiChang,Chih-ChunLail,yuan-weiLin ,”A Fast SVC based Channel Recommendation System for an IPTV on a cloud and P2P Hybrid Platform”,2013,ISSN:1460-2067.
- Jaqueline Ferreira de brito,Luciano Antonio Digiampietri,”A study about Personalized content Recommendation”,2013,ISSN:0976-6413.
- Nana Yaw Asabere,”Towards perspective of hybrid Approaches and Methodologies in recommender system” ,2012,ISSN:2047-3338.
- Pedro M.P.Rosa,Joel J.P,C Rodrigues,FillippoBasso,”A Weight aware recommendation algorithm for mobile multimedia systems”,2013,ISSN:1875-905X.
- Miao LV,Chun JIN, Jim c.HAN, Yoshiyuki HIGUCHI, “Ontology based user preferences Bayesian model for Personalized Recommendation”,2013,ISSN:1553-9105.
- ZibinZheng, Hao Ma, Irwin King ,MichaelR.Lyu, “WSRec:A Collaborative Filtering Based Web Services Recommendation system”,2009,ISSN:9780-7695.
- AbdelkarOuttagarts,”Mobile Agent based Application”:a survey,2009.
- G. R. Umarani , Dr. T. Nalini ,”A Review on Multimedia Recommendation System to Detect Spammer and Detector”,2015,ISSN: 2349-6495.
|