ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
T.S.Raja1, R.Sujatha2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
The IEEE 802.15.4 standard for lower-power low-cost low-data-rate in wireless personal area networks. A tree topology is used to construct a wireless sensor network for data delivery applications. Data delivery failures occurs the form of mobile node movements and topology changes. The mobile node patterns to reduce the frequency router reconstruction and transmission of data to mobile nodes efficient.To increase the data delivery ratio and mitigate the effects of packet loss caused by the mobile nodes. we propose construction form of cluster based tree, And rumor protocol used to find the optimal path form of each indival nodes, and also used to mesh topology to detect the data failure and the gossip protocol used to communication between the nodes to transfer the information highly effective. we proposed algorithm for Adoptive Parent based algorithm, K-nearest neighbor search algorithm. The effective tree construction form of topology constructed using mobile nodes metric is demonstrated by NS2 simulations against a real-world scenario.
Keywords |
| cluster tree, Rumor protocol, Failure detection, gossip protocol. |
INTRODUCTION |
| The Wireless sensor Networks (WSNs)[1],[2] are collections of low-cost sensing devices.The wireless communication networks to perform sensing various sensor based application, Measuring Individual Behavior and physiology in natural situations (mobility, robustness) using multiple sensors.e.g healthcare monitoring,home automation,building monitoring system,economic and social benefits. In some of the cases, sensor may be connected by wire to IP network (camera at home for security), but in our personal space data applications, wireless connectivity,Wireless sensor networks also perform the form of zigbee application to operate low data rate ,low power,low cost ,and short |
| communication range,e.g.,[6,9] the excellent research results cannot be applied to handling of mobility issues for mobile sensor networks. Two types of sensor their Active,Passive sensor.The cluster-tree networks can serve as vehicle-to-infratructure communication form of ad hoc networks(VANETs).The traffic control, systemaided navigation, location-based information such as the VANETs[3]-[4].The frequent signal strength detection and rapid energy exhaustion of mobile nodes [5].For cellular networks to be perform the handover(or handoff) is typical mechanism [6].mobile IP provides an efficient mechanism for mobile object roam across subnets [7].self-awareness movements of mobile objects to rejoin a network and associated with a new base station.Therefore ,Mobile IP suitable for objects moving frequency. The adoptive-parent based framework for cluster tree network to increase bandwidth utilization without generating any extra message exchange. The IEEE 802.15.4 to operates the physical layer and MAC to control sublayer low rate in Wireless personal area networks(WPAN).The routers are connected to the normally backbone of network and reliable power supplies, where as mobile and end devices . |
| The major function of mobile and end devices is to receive data from the network coordinator rather send data through the network. Chen et al.[8] ,The central server cannot locate a certain mobile end device. we more efficient and automatic approach for locating mobile and end devices. The approach deploys routers and constructs topology with the property that mobile nodes will move along the constructed. The data will reach the mobile nodes to forward the router in particular optimal path. In other words ,we choose location on particular node positions of the routers to be design the tree topology that movements are directed toward the root of the tree. To achieve objective ,we gather information about mobile node movements and construct tree and transfer data particular optimal path and avoid the failure. The overhearing mechanism for mobile nodes and improve the data delivery. The existing approach to perform zigbee router and mobility robust tree to transfer data in highly efficient. The proposed approach used rumor protocol to perform find location form mobile nodes and find which path suitable for transfer the data, and also gossip protocol used to communication between the nodes, The K-nearest neighbor search algorithm, Adoptive parent based algorithm to be used avoid data failure. The simulation tool be used to deployment of node tree topology [6],[8].The simulation result show the proposed approach achieves significant improvements of data delivery path identifier and fault data and also node fault to detected. |
| The remainder of this paper is organized as follows. In the Section II, we review the related work, and in Section III, we describe the overview of the existing system, In the Section IV, we discuss the proposed algorithms for construct cluster tree. The simulation result for model analysis are presented in Section V, The Section VI contains concluding remarks. |
II RELATED WORK |
| In this section, we discuss mobility node transfer the data mechanism that we proposed the literature and explain the difficulties that arise in the direct application of existing mobility patterns to a cluster network. We also consider studies of mobility support WSN. |
A .Enabling Connectivity with Mobile node |
| The mobile networks issue of mobility, e.g., mobile ad hoc networks (MANETs), mobile wireless sensor networks(MWSNs),delay-tolerant(DTNs),it has generated much research interest in recent years[1],[2].The schemes of routing that utilize âÃâ¬Ãâ¢mobility predictionâÃâ¬Ãâ Reference[12] presents mobile nodes moving direction, and also the sender use the predicted information to choose the proper path and forwarding node moving toward the message recipient. Reference[13] builds a virtual coordinate for space based on the mobility patterns of mobile nodes. The proposed approach system represents the frequency to be allocated each mobile node location, So the system compute the routing path. |
| Reference [13] proposes the aware routing based on the property that mobile nodes moves among the direction based form of signal points. The challenges remain in the mobility issue in mobile sensor networks because of unique features, The data delivery among the routing schemes that utilize mobility prediction for MANETs and DTNs cannot directly applied for a cluster network, because they require movement of data collection, the route computation will introduce additional computation and message overheads in cluster. |
B. Mobile node and Localization in WSNs |
| The localization focus on MWSN, The localization algorithms determine the locations of nodes transforming signals emitted by neighboring sensor based position. The fixed sensor node information about the location, the mobile sensors can be coordinates absolute value. A sensor node precise location of pin point based MWSN location algorithms. The data delivery depends upon the node positions, only the information about routers to which the destination node can be connected is needed. |
| The node resolve form of âÃâ¬Ãâ¢network repairâÃâ¬Ãâ problems of mobility in WSN by reconstructing the topology to maintain the connectivity .In [9] and [11], the authors consider network issues. the approach proposed in[9],if node form of parent link failure or broken ,it broadcast a message to find a neighboring node with in the shortest path to the coordinator and also adopts that new parent. The drawback of this scheme is that it may cause loops in the repaired network topology. In the approach introduce d in [9] that allows parent node of a failed link to participate in the recovery. In this [10] scheme also increase the communication overhead and convergence delay. |
| There have been deliver the data to mobile nodes in WSN based on the property where nodes are move the form of mobile. Reference [11] introduces routing scheme called as âÃâ¬Ãâ¢data stashingâÃâ¬Ãâ it have been perform to energy consumption and exploiting knowledge about the mobile sink. As sink traverse relay nodes then send directly to the sinks. Because data stashed in the relay nodes are waiting for mobile sinks. |
| The route interruptions caused by node mobility and cluster form of applications, If any node loses the link to its parent, the node must rejoin the network, That time to increase the communication. The network coordinator periodically applies the regular repair scheme to maintain the network topology. |
C. Mobile node deployment of WSNs |
| The network form of WSN used to deploy the topology and efficiency. The deployment can be reduce the cost and also improve the energy efficiency of the nodes. The deployment requires form of prior information about environment and users. The propose scheme of node-scheduling that tries to reduce a system âÃâ¬Ãâs energy consumption and increase system lifetime. In[14],to support distributed applications for efficient deployment, And optimize the number of sensors to be determine their locations. The must research approach focus on data collection applications. |
| The approaches in [14],as discussed in the previous paragraph, to determine the locations of network routers and mobile node movements on different sensing interest. The main goal to motivate us mobile node have been consider as cluster tree to be designing unique features of WSNs. The operating overhead such as route searching packets to be reduced. |
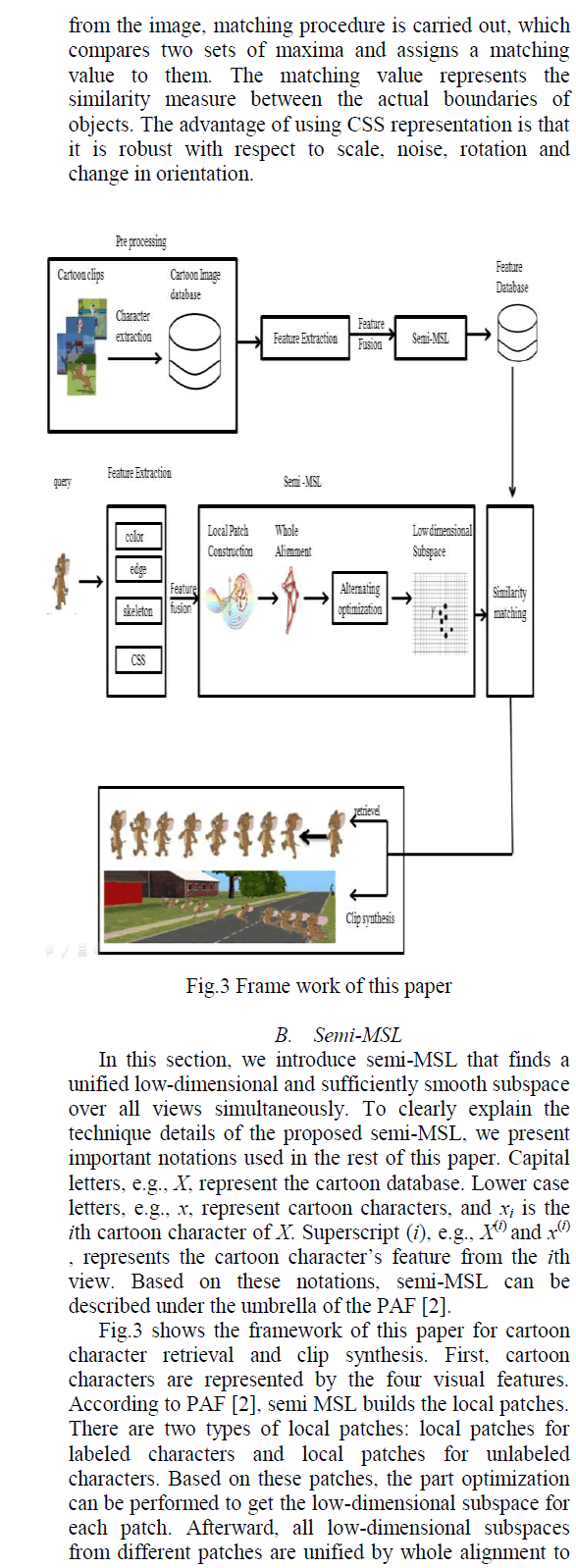
III Overview of Existing System |
| In this section to development of the of zigbee based form of measured coverage area, it is perform low cost, low power, and low data rate .To form a zigbee tree based operation to perform ,and it consists of following three basic form |
| 1. zigbee coordinator 2.zigbee Router 3.mobile and end device. To transfer the highly data be exchange |
 |
A. System model |
| A zigbee tree comprises form of 1.zigbee coordinator 2.zigbee router 3.device,the zigbee coordinator performs initialization, maintance, and control functions of the network topology, The router responsible for data between routing and end devices. the zigbee to support following topologies:1)star topology 2)mesh networks. the star network act as directly connect to multiple device. The zigbee tree to be act as the form of star topology, it have been perform only data transfer data between the nodes; it will cover certain range of the environment. |
 |
 |
| Path Failure Detection In Wireless Sensor Networks between the nodes. |
| The zigbee router can be act as the data transmission and doesn‘t find the optimal path. The zigbee canperform the certain coverage area only use. It‘s doesn‘t find the packet loss form of network topology. The routing overhead to occur the form of routing mechanism. |
IV The Overview of Proposed System |
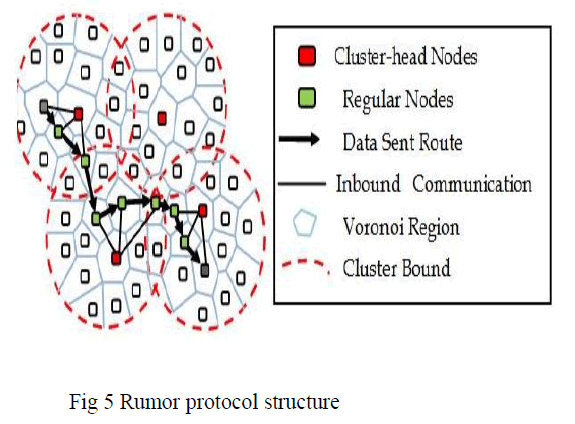
| In this section we describe nodes to be perform cluster tree based routing operation, it can perform the following algorithm to be used 1. Adoptive Parent based algorithm 2. K-nearest neighbor search algorithm The above two algorithm have been perform the form of routing operation. The following form of two protocols to be implemented and find the optimal path and also detect the packet loss 3.Rumor routing protocol 4.Gossip protocol. |
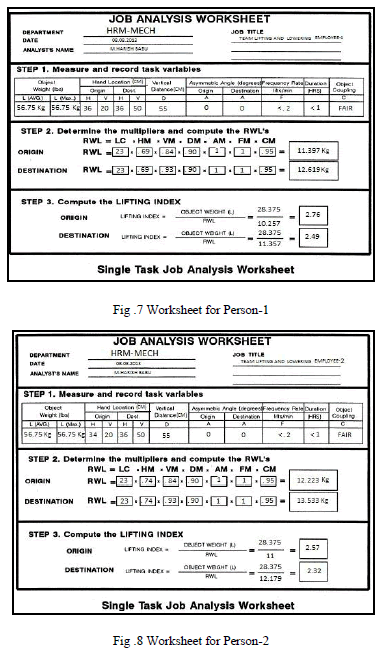
1. Adoptive Parent based algorithm |
| The Adoptive parents in cluster tree networks, the concept of this technique a parent node adopts a child of other parent node as own child node so this algorithm to improve the throughput, In form of following basic operation to be perform 1.PULL 2.PUSH 3.RELABEL,The PULL condition to perform the form of insert the node in the tree, and PUSH can be perform the form of node flow back of parent node, the RELABEL increase the vertex of node capacity. |
 |
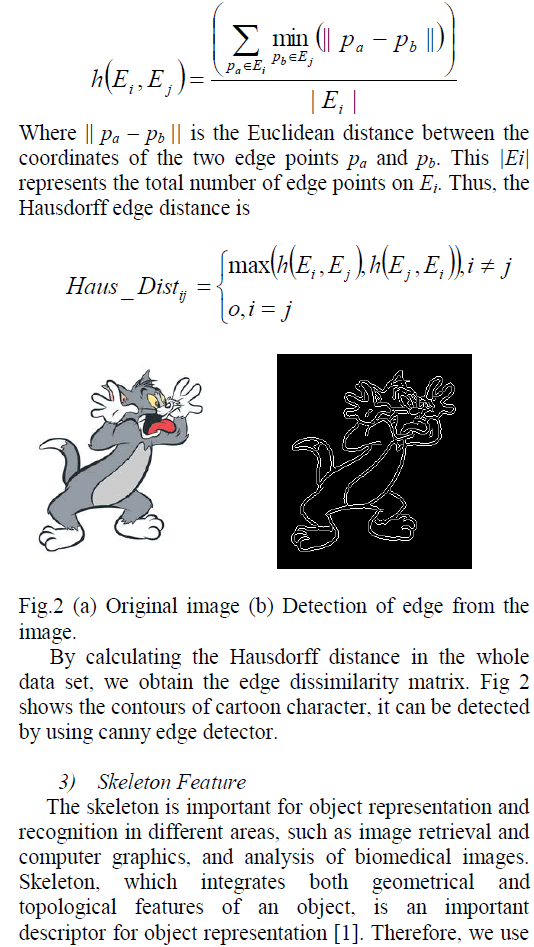
| 2. K nearest Neighbor Search Algorithm |
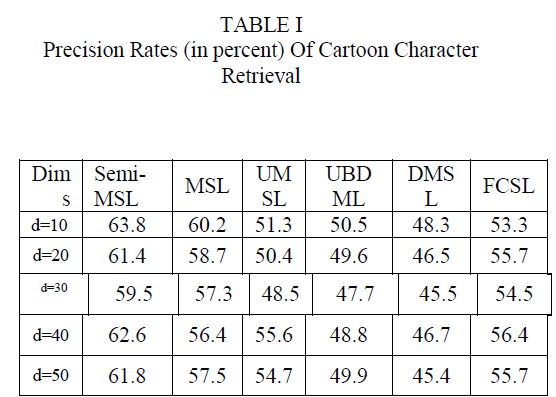
| 2.1 K-Means |
| The algorithm can group your data into k number of categories. The principle is to minimize the sum of squares of distances between data and the corresponding cluster centroids. |
 |
| The classification is using majority vote. The classifiers do not use any model to fit the data and only based on memory. The KNN uses neighborhood classification as the predication value of the new query instance, its work as the general principle is to find the k training samples to determine the k nearest neighbors based on a distance measure. Next, the majority of those k nearest neighbors decide the category of the next instance. The nearest neighbor methods is to find a predefined number of training samples closest in distance to the new point, and predict the label from these. The number of samples can be a user-defined constant (knearest neighbor learning), or vary based on the local density of points (radius-based neighbor learning). The distance can, in general, be any metric measure: standard Euclidean distance is the most common choice. Neighbors-based methods are known as non-generalizing machine learning methods, since they simply âÃâ¬Ãâ¢rememberâÃâ¬Ãâ all of its training data (possibly transformed into a fast indexing structure such as a Ball Tree or KD Tree.). |
| Nearest neighbors has been successful in a large number of classification and regression problems, including handwritten digits or satellite image scenes. Being a non-parametric method, it is often successful in classification situations where the decision boundary is very irregular. Neighbors-based classification is a type of instance-based learning or non-generalizing learning: it does not attempt to construct a general internal model, |
| but simply stores instances of the training data. Classification is computed from a simple majority vote of the nearest neighbors of each point: a query point is assigned the data class which has the most representatives within the nearest neighbors the point. The basic nearest neighbor classification uses uniform weights: that is, the value assigned to a query point is computed from a simple majority vote of the nearest neighbors. Under some circumstances, it is better to weight the neighbors such that nearer neighbors contribute more to the fit. This can be accomplished through the weights keyword. The default value, weights = 'uniform', assigns uniform weights to each neighbor. weights = 'distance' assigns weights proportional to the inverse of the distance from the query point. Alternatively, a user-defined function of the distance can be supplied which is used to compute the weights. |
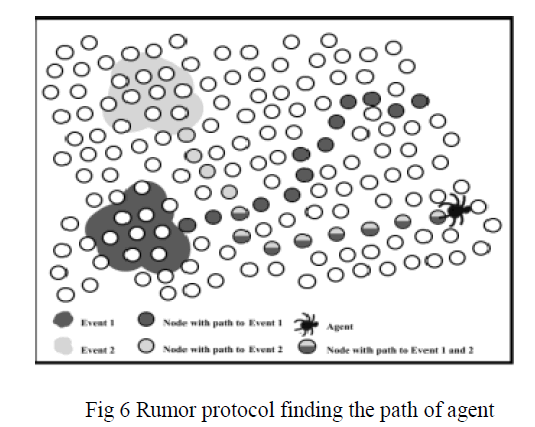
3. Finding the optimal path by using rumor protocol |
| This protocol used to node transfer data means, it first search for a valid route to the Base Station and it transmits the data, it have been perform agent based path creation operation. The routing is trade-off between flooding overhead and delivery consistency and also be adjusted to the parameters. The routing use agents to find the path to an event area on finding the path agents store the path at nodes as a state, The event node creates agents by the allocation of a path of length 0 to themselves, If many many nodes watching the same event and trying to creating path to event node which as a result create huge overhead. The agent travelling to limited number of hops, on returning agents their own routing table of visited nodes. To find the multiple agents has been perform path the form of priority based operation. |
 |
 |
  |
4. Classification of Gossip Protocol |
| This protocol used to perform the communication between the nodes, it have been perform to distributed system, it also perform two-phase commit protocol operation. It have been works on a slightly different basis from its flooding counterpart. It‘s mechanism of flooding. The receiving the data packet a sensor node form of randomly, selects one of its neighbours and the data packet is forwarded to that neighbour only and next the node which received data packet selects and forwards that packet to another node and process continues. |
| If the two neighbour nodes send the same information to send sensor node means, the protocol used to allocate the random number to the neighbour. |
5. Optimized Link State Routing Protocol(OLSR) |
| The information in this section concerning the Optimized Link State Protocol is taken from its RFC . The OLSR is a proactive routing protocol, the routes are always immediately available when needed. In this optimization version of a pure link state protocol. So the topological changes cause of flooding to the topological information to all available host form of network. To reduce the possible overhead in the network protocol uses Multipoint Relays (MPR). The idea of MPR is to reduce flooding of broadcasts by reducing the same broadcast in some regions in the network, more details about MPR can be found later to reduced. It can provide the shortest path. The reducing the time interval for the control messages transmission can bring more reactivity. The OLSR used two kind of control messages 1.Hello messages 2.Topology Control (TC). The Hello messages used to finding the information about the link status, it also construct Multipoint Relay(MPR) it can chose the negihbours host act as this form. The Hello message to be sent only hop away, The TC messages are broadcasted throughout the entire network. TC messages are used to broadcasting information about own advertised neighbours which includes at least the MPR Selector list. |
| Multiple Interface Declaration (MID) messages are used for informing other host that the announcing host can perform multiple OLSR interface addresses. The MID message is broadcasted throughout the entire network only by MPRs. There is also a âÃâ¬Ãâ¢Host and Network AssociationâÃâ¬Ãâ (HNA) message which provides the external routing information by giving the possibility for routing to the external addresses. The HNA message provides information of network and the net mask addresses, of the OLSR host can consider that the announcing host can act as a gateway to the announcing set of addresses. The HNA is considered to generalized version of the TC message with only difference that the TC message can inform about route cancelling while HNA message information is removed only after expiration time. |
5.1 Routing |
5.1.1 Neighbour Sensing |
| The link in the ad hoc network can be either unidirectional or bidirectional so the host must know this information about the neighbours. The Hello messages can be broadcasted periodically for the neighbour sensing. The Hello messages are only broadcasted one hop away so that they not forwarded. When the first host receives the Hello message from the second host, it sets the second host status to asymmetric in the routing table. When the first host sends a Hello message and includes that, it has the link to the second host as asymmetric, the second host set first host status to symmetric in own routing table. Finally, when second host send again Hello message, where the status of the link for the first host is indicated as symmetric, then first host changes the status from asymmetric to symmetric. |
| The Hello messages are used for getting the information about local links and neighbours. The Hello messages periodic broadcasting is used for link sensing, neighbour‘s. When the host gets a new broadcast message, which is need to be spread throughout the network and the message‘s sender interface address to the MPR Selector set, then the host must forward the message. Due to the possible changes of ad hoc network, the MPR Selectors sets can be updated continuously using Hello messages. |
5.1.2 Multipoint Relays Selection |
| The algorithm constructs the MPR set which includes minimum number of the one hop symmetric neighbours from which it is possible to reach all the symmetrical strict two hop neighbours. The host must have the information about one and two hop symmetric neighbours in order to start the needed calculation for the MPR set. All the exchange of information are broadcasted using Hello messages. The neighbours which have status of willingness different than WILL_NEVER in the Hello message can be chosen to act as MPR. The neighbour must be symmetric in order to become an MPR. |
| The algorithm for selecting Multipoint Relay set |
| 1. Take all the symmetric one hop neighbours can willing to act as an MPR. |
| 2. Calculate for every neighbour host degree, which is a number of the symmetric neighbours, that are two hops away from the calculating source and does not include the source or its one hop neighbours. |
| 3. Add the neighbour symmetric host to the MPR set. If it can only neighbour from which is possible to get to the specific two hop neighbour, to be remove the chosen host neighbours from the two hop neighbour set. |
| 4. If there are still some hosts in the form of two hop neighbour set, then calculate the reachability of the each one hop meaning of two neighbour set. |
| 5. Repeat previous step until the two hop neighbours set Empty. |
| 6. If one host is taken away and all the two hop neighbours, covered by at least one host and the willingness of the host is smaller than WILL_ALWAYS, then the host may be removed. |
| The possible improvements of this algorithm to be needed |
5.1.3 Routing Table Calculations |
| The routing table entries have following information: destination address, next address, and also number of hops to the destination and local interface address. Next address can be indicates to next hop host. The information to perform topological set (from the TC messages) and from the local link information base (from the Hello messages). So if any changes occur in these sets, then the routing table is recalculated. Because this is proactive protocol then the routing table must have routes for all available hosts in the network. The information broken links or partially known links is not stored in the routing table. |
| The routing table is changed if the changes occur in the following cases: neighbour link appear or disappear, two hops neighbour is created or removed, topological link is appeared or lost or when the multiple interface association information changes. But the update of this information does not lead to the sending of the messages into the network. Finding the routes for the routing table entry the shortest path algorithm is used. |
5.1.4 Advantages |
| OLSR is also a flat routing protocol, it need not central administrative system to handle its routing form of process. The proactive characteristic of protocol can provides that the protocol has all the routing information to all participated hosts in the network. However, the drawback OLSR protocol needs that each host periodic sends the updated topology information throughout the entire network, to be increase the protocols bandwidth usage. The flooding is minimized by the MPRs, which can be only allowed to forward the topological messages. |
 |
VI Conclusions |
| In this, paper we describes to find the optimal path by using rumor protocol and using the gossip protocol and also OLSR protocol to communicate between the mobile nodes form of agent and finding the path ,to transfer data from the path of the section. The data loss doesn‘t perform this section. Future work to implement the each protocol work indival. |
References |
|