ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
R.Udhayakumar1, M. Jawahar2 , I.Ramasamy3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Clouds are being used to store sensitive information about patients to enable access to medical professionals, hospital staff, researchers, and policy makers. It is important to control the access of data so that only authorized users can access the data. This scheme proposed validity of the message without revealing the identity of the user who has stored information in the cloud and also added feature of access control in which only valid users are able to decrypt the stored information. In Attribute Based Signature scheme to achieve versatile primitive users can allows a party to sign a message with finegrained control over identifying information. In ABS, a signer, who possesses a set of attributes from the authority, can sign a message with a predicate that is satisfied by his attributes. The signature reveals no more than the fact that a single user with some set of attributes satisfying the predicate has attested to the message
Keywords |
| Access control, Authentication, Attribute-based signatures, Attribute-based encryption, Cloud security. |
INTRODUCTION |
| In today’s competitive environment, the service dynamism, elasticity, and choices offered by this highly scalable technology i.e. Cloud Computing are too attractive for enterprises to ignore. These opportunities, however, don’t come without challenges, in the world of Information Technology cloud computing is the most exciting topic. Many organizations in the market are now adopting this technology. However, security and privacy are perceived as primary obstacles to its wide adoption. There are several critical security challenges and which motivate further investigation of security solutions for a trustworthy public cloud environment.Cloud computing is the newest term for the long-dreamed vision of computing as a utility. The cloud provides convenient, on-demand network access to a centralized pool of configurable computing resources. |
| A. Contributions |
| The main contributions of this paper are the following: 1) Distributed access control of data stored in cloud so that only authorized users with valid attributes can access them. 2) Authentication of users who store and modify their data on the cloud. 3) The identity of the user is protected from the cloud during authentication. 4) The architecture is decentralized, meaning that there can be several KDCs for key management. 5) The access control and authentication are both collusion resistant, meaning that no two users can collude and access data or authenticate themselves, if they are individually not authorized. 6) Revoked users cannot access data after they have been revoked. 7) The proposed scheme is resilient to replay attacks. A writer whose attributes and keys have been revoked cannot write back stale information. 8) The protocol supports multiple read and write on the data stored in the cloud. 9) The costs are comparable to the existing centralized approaches, and the expensive operations are mostly done by the cloud. |
II. RELATED WORK |
| Clouds are being used to store sensitive information about patients to enable access to medical professionals, hospital staff, researchers, and policy makers. It is important to control the access of data so that only authorized users can access the data. Using ABE, the records are encrypted under some access policy and stored in the cloud. Users are given sets of attributes and corresponding keys. Only when the users have matching set of attributes, can they decrypt the information stored in the cloud. |
III. EXISTING SYSTEM |
| Large number of data can be stored in clouds is highly sensitive, for example, medical records and social networks. Security and privacy are thus very important issues in cloud computing. In one hand, the user should authenticate itself before initiating any transaction, and on the other hand, it must be ensured that the cloud does not tamper with the data that is outsourced. User privacy is also required so that the cloud or other users do not know the identity of the user. The cloud can hold the user accountable for the data it outsources, and likewise, the cloud is itself accountable for the services it provides. The validity of he user who stores the data is also verified. Apart from the technical solutions to ensure security and privacy, there is also a need for law enforcement. |
| a) Lack in security. |
| b) More energy consumption. |
| c) More computational time. |
| d) Not efficient. |
IV. PROPOSED SYSTEM |
| An access control model to enforce controlled information sharing in emergency situations is proposed. Model is able to enforce flexible information sharing within a single organization through the specification and enforcement of emergency policies. Emergency policies allow the instantiation of temporary access control policies that override regular policies during emergency situations., each emergency is associated with one or more tacp templates, describing the new access rights to be enforced during specific emergency situations. |
| In emergency management scenarios the response plans are defined by experts on the field based on regulations and laws and based on reports resulting by the emergency preparedness phase, during which emergency managers conduct a risk assessment. That all these documents represent a solid base from which emergencies, emergency policies, and emergency obligations can be specified as shown in Fig 1.1. |
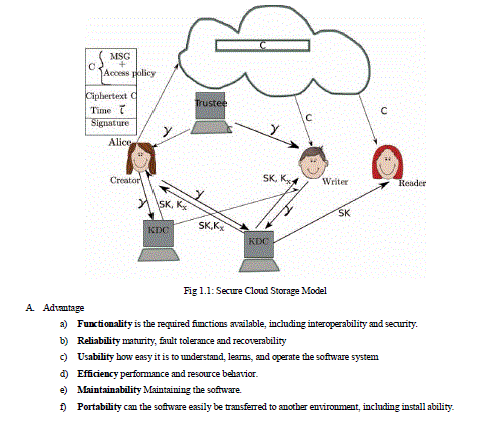 |
| A. Advantage a) Functionality is the required functions available, including interoperability and security. b) Reliability maturity, fault tolerance and recoverability c) Usability how easy it is to understand, learns, and operate the software system d) Efficiency performance and resource behavior. e) Maintainability Maintaining the software. f) Portability can the software easily be transferred to another environment, including install ability. |
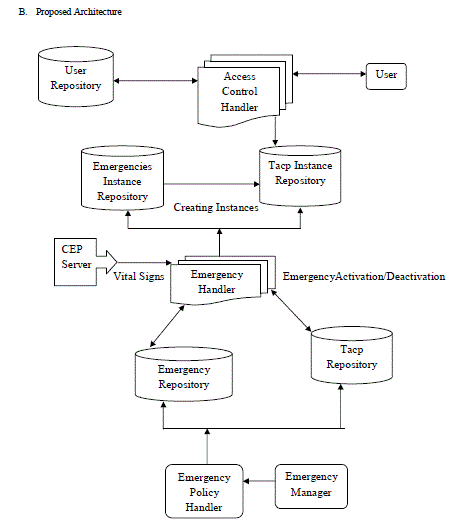
B. Proposed Architecture |
 |
V. COMPARATIVE STUDY |
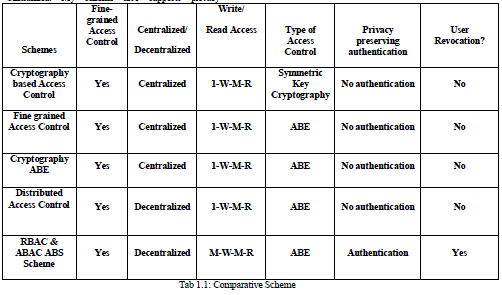
| In compare my scheme with other access control schemes and show that my scheme supports many features that the other schemes did not support. 1-W-M-R means that only one user can write while many users can read. M-W-M-R means that many users can write and read. In see that most schemes do not support many writes which is supported by our scheme. In my scheme is robust and decentralized, most of the others are centralized. My scheme also supports privacy preserving authentication, which is not supported by others. Most of the schemes do not support user revocation as shown in Tab 1.1. |
 |
VI.CONCLUSION |
| Extension of the emergency access control model presented in with the possibility of defining administration policies, which subjects are enabled to define emergency policies and over which scope. They have implemented an extended version of the prototype presented in and carried out an extensive set of test to check what is the impact of emergency policies into an access control system. A set of correctness checks have also been to useless activation/deactivation of emergencies. To avoid possible proliferation of policies due to template instantiation, there are currently investigating to instantiate tacps during the access request evaluation. This would allow us to instantiate only those policies indeed needed to take the deny/grant decision. However, this requires storing contextual information as soon as an emergency occurs, so as to be able to instantiate and evaluate conditions on tacp only if the protected resource is requested. |
References |
|