ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Adnan Affandi1 ,Mohammed Awedh2 ,Mubashshir Husain3&Ahmed Alghamdi4
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
In the past, most of the companies were using a magnetic stripe card which is a type of card capable of storing data by modifying the magnetism of tiny iron-based magnetic particles on a band of magnetic material on the card. Card has a Personal Identification Number (PIN) allow to access account electronically. These days, RFID card has been used widely. In this paper the researcher used RFID card instead of a magnetic stripe card because it does not need a physical contact. The researcher combine a face recognition system with RFID system to support the security system. If the PIN in the RFID card matches the recognized face then a response is send to a remote station by a modem. This paper is important because it enhance security. In this paper the researcher mix two type of security (FR and RFID) which make the security stronger and reliable. In turn, this give the user more control. The matlab program is developed and it met the design criteria and solve the paper problem
Keywords |
| RFID, PIN,etc. |
INTRODUCTION |
| Radio Frequency identification (RFID) system (as shown in fig.1) is an automatic identification sensor-based technology. It is a wireless information system, with real-time visual display of activities, resulting in the improvement in efficiency with less human efforts in data entry. It track and trace items automatically and consisting of three key elements: RFID tags, RFID readers, and a back-end database server to identify information. RFID technology promises many benefits to several sectors( manufacturing, logistics, military, health care,…etc) . Its main attempt is tracking and monitoring of goods moving through the supply chains, and manage the delivery and assembly process. It reduce the delivery and assembly processes time. The information transmitted in the air between the tag and the reader has a radio transmission nature, so it could face several threats: |
| Impersonation attack: by masquerade the reader or the tag. |
| Reply attack: by intercept the transmitted information and resend it to the reader. |
| Denial of service: by shielding the RFID device to stop operation or tocause the tag and the database unable to update their information. |
| Privacy concern: by accessing the tag data. |
 |
| A.COMMUNICATION SYSTEM |
| There are many ways of communication between stations. Communication can be applied by internet, but to increase security we wrote a special code by MATLAB for communication using phone line. The system response can be transferred to a remote control station by a modem. For example, the response can be matched or not matched result. Either the remote station or the main station which has the FR or RFID system can control the p's output process. The code is a GUI interface instead of a text interface to make it easy for the user to interact with it. Figure 2 shows the communication GUI. |
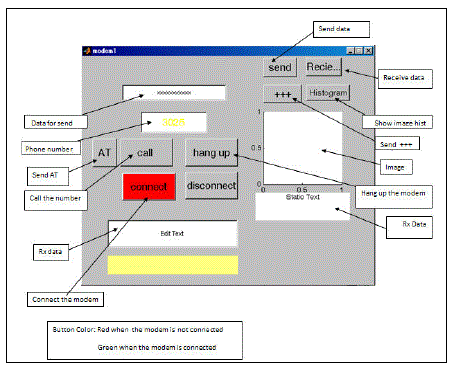 |
| C.THE MODEM |
| The researcher used Global voice modem from silicon lab. figure 3 shows the modem. The Voice modem consists of a motherboard with a complete removable daughter card. The Voice modem is a complete controller based modem chipset with an integrated and programmable direct access arrangement (DAA) that meets the global telephone line requirements. It is available in a 24-pin or 38-pin system side device and a 16-pin line side device. |
 |
| A basic RFID system consists of three components: |
| An antenna or coil |
| A transceiver (with decoder). |
| A transponder (RF tag) electronically programmed with unique information. |
| The researcher chose RFID because it is a non-contact system like face recognition system. Combining face recognition system with RFID system will add more strength to any security system, which are systems that enable an authority to control access to protected areas and resources. As an application, imagine a world where you don’t have to worry about authentication. Imagine instead that all requests to your area or resources already include the information you need to make access control decisions. Access control is, in reality, an everyday phenomenon. A lock on a car door is essentially a form of access control. APIN on an ATMsystem at a bank is another means of access control. The possession of access control is of prime importance when persons seek to secure important, confidential, or sensitive information and equipment. The system in any organization can trust another system component to securely provide user information, such as the user’s identity or numbers, The user’s information always arrives in the same simple format, regardless of the authentication mechanism, whether it’s from a keypad, camera or passive or active card. |
LITERATURE REVIEW |
| a) In 1991, M. Turk and A. Pentland have used Principal Component Analysis (PCA) algorithm in their research. They defined Principal component analysis (PCA) as a mathematical procedure that uses an orthogonal transformation to convert a set of observations of possibly correlated variables into a set of values of uncorrelated variables called principal components. The number of principal components is less than or equal to the number of original variables. This transformation is defined in such a way that the first principal component has as high a variance as possible (that is, accounts for as much of the variability in the data as possible), and each succeeding component in turn has the highest variance possible under the constraint that it be orthogonal to (uncorrelated with) the preceding components. Principal components are guaranteed to be independent only if the data set is jointly normally distributed. PCA is sensitive to the relative scaling of the original variables. Depending on the field of application, it is also named the discrete Karhunen–Loève transform (KLT), the Hotelling transform or proper orthogonal decomposition (POD)"( http://en.wikipedia.org/wiki/Principal_Component_Analysis). M. Turk, and A. Pentland have developed a computer system which can recognize the person by comparing characteristics of the face to those of known individuals by using Eignfaces. (M. Turk and A. Pentland, 1991) |
| b) H. Moon, P.J. Phillips have also used PCA algorithm in their research in 2001. They used PCA because it is a statistical dimensionality-reduction method. (H. Moon, P.J. Phillips, 2001) |
| c) In 1999, Chengjun Liu and Harry Wechsler have used Independent Component Analysis (ICA) for Face Recognition in the Second International Conference on Audio- and Video-based Biometric Person Authentication. "Independent Component Analysis (ICA) defines a generative model for the observed multivariate data, which is typically given as a large database of samples. In the model, the data variables are assumed to be linear mixtures of some unknown latent variables, and the mixing system is also unknown. (Chengjun Liu and Harry Wechsler, 1999)d) The latent variables are assumed nongaussian and mutually independent and they are called the independent components of the observed data. These independent components, also called sources or factors, can be found by ICA. ICA is superficially related to principal component analysis and factor analysis. ICA is a much more powerful technique, however, capable of finding the underlying factors or sources when these classic methods fail completely. The data analyzed by ICA could originate from many different kinds of application fields, including digital images, document databases, economic indicators and psychometric measurements. In many cases, the measurements are given as a set of parallel signals or time series; the term blind source separation is used to characterize this problem. Typical examples are mixtures of simultaneous speech signals that have been picked up by several microphones, brain waves recorded by multiple sensors, interfering radio signals arriving at a mobile phone, or parallel time series obtained from some industrial process" (http://en.wikipedia.org/wiki/Independent_component_analysis). |
| e) “Independent component analysis (ICA) is a method for finding underlying factors or components from multivariate (multidimensional) statistical data. What distinguishes ICA from other methods is that it looks for components that are both statistically independent and nongaussian". (A. Hyvarinen, I. karhunen, E. Oja , 2001) |
| f) RaufKh. Sadykhov , Vladimir A. Samokhval, Leonid P. Podenok have used Face Recognition Algorithm on the Basis of truncated Walsh-Hadamard Transform and Synthetic Discriminant Functions. They presented face recognition algorithm by constructing synthetic discriminant functions in feature space of 2D truncated Walsh-Hadamard transform. The method relies on slicing facial image onto the number of binary ones which are used after some preprocessing operations as input vectors to construct SDF. (RaufKh. Sadykhov , Vladimir A. Samokhval, Leonid P. Podenok, 2004) |
| g) Yasufumi Suzuki and Tadashi Shibata used an algorithm which used in VLSI hardware accelerator. They used multiple-clue face detection algorithm using edge-based feature vectors and was applied to the problem of face detection. In this algorithm, feature vectors are generated utilizing distribution of edges in an input image, thus achieving dimensionality reduction for efficient processing. Multiple clues in the edge distribution are utilized to enhance the accuracy of face detection. Several feature vector generation schemes have been developed, which are all compatible to the direct hardware implementation. (Yasufumi Suzuki and Tadashi Shibata, 2004) |
| h) SittinonKongsontana and YuttapongRangsanseri have used face recognition using 2dlda algorithm. Their research proposes Two–Dimensional Linear Discriminant Analysis (2DLDA) for feature extraction which used for face recognition application. This method is developed from Fisher Linear Discrimnant (FLD) and Two–Dimensional Principle Component Analysis (2DPCA). In this method, 2DLDA directly uses the image matrix to calculate the between-class scatter matrix and within-class scatter matrix. Moreover, 2DLDA will be handling the problem that the within-class scatter matrix maybe singular. The experimental results indicated that the 2DLDA method is more computationally efficient than conventional methods. |
| Face detection in color images using AdaBoost algorithm based on skin color Information. (SittinonKongsontana and YuttapongRangsanseri, 2005) |
| i) Yan-Wen Wu 1, Xue-Yi Ai propose a novel technique for detecting faces in color images using AdaBoost algorithm combined with skin color segmentation. First skin color model in the YCbCr chrominance space is built to segment the non-skin-color pixels from the image. Then, mathematical morphological operators are used to remove noisy regions and fill holes in the skin-color region, so we can extract candidate human face regions. These face candidates are scanned by cascade classifier based on AdaBoost for more accurate face detection. This system detects human face in different scales, various poses, different expressions, lighting conditions, and orientation. Experimental results show the proposed system obtains competitive results and improves detection performance substantially. (Yan-Wen Wu 1, Xue-Yi Ai, 2008) |
| j) Nakano and his colleagues propose a new statistical learning algorithm. This study quantitatively verifies the effectiveness of its feature extraction performance for face information processing. Simple-FLDA is an algorithm based on a geometrical analysis of the Fisher linear discriminant analysis. As a high speed feature extraction method, the present algorithm in this paper is the improved version of Simple-FLDA. First of all, the approximated principal component analysis (learning by Simple- PCA) that uses the mean vector of each class is calculated. Next, in order to adjust within-class variance in each class to 0, the vectors in the class are removed. By this processing, it becomes high-speed feature extraction method than Simple-FLDA. The effectiveness is verified by computer simulations using face images. (M. Nakano, S. Karungaru, S. Tsuge, T. Akashi, Y. Mitsukura. andM. Fukumi, 2008) |
| k) KanghunJeong, Dongil Han, Yongguk Kim, and Hyeonjoon Moon used face recognition algorithm based on Linear Discrete Analysis (LDA) algorithm as a substitute for the PCA. It requires more processing time, but the recognition performance was better. Based on LDA algorithm, they collect feature vector and analyze data statistically. LDA is relatively strong for frontal image but weak on profile image on general face recognition system. (KanghunJeong, Dongil Han, Yongguk Kim, and Hyeonjoon Moon, 2008) l) Raghavendra.R, Ashok Rao, HemanthaKumar.G address new face verification scheme based on Log- Gabor filter (texture based) and Gaussian Mixture Model. They proposed method consists of three parts. The first part is a Log-Gabor filtering on facial image. The second part is to model the Log-Gabor filter response using Gaussian Mixture Model to obtain more than one set of features. The third part is transforming the set of features using subspace methods such as Principal Component Analysis (PCA) and Independent Component Analysis (ICA). Thus, in this paper two methods namely Log-Gabor Mixture Model (LGMM) based on PCA and Log-Gabor Mixture Model (LGMM) based on ICA is proposed.Proposed methods are evaluated for its performance by conducting series of experiments on three image databases: ORL, AR, YALE face database. The nature of type & size of databases chosen on the performance of these algorithms are also studied. The experimental results indicate the efficacy of the proposed methods and varied nature of results based on these algorithms. (Raghavendra.R, Ashok Rao, HemanthaKumar.G, 2008) |
| m) Jun-Ying Gan, Si-Bin He on Proceedings of the Eighth International Conference on Machine Learning and Cybernetics, proposed an improved 2DPCA algorithm for face recognition. on the basis of two-dimensional principal component analysis, an improved two-dimensional principal component analysis (I2DPCA) is presented for face recognition. Firstly, the criterion functions of global and between-class scatters of projection features are defined. Secondly, the two defined criterion functions are fused by way of ultiplication or addition. Therefore, the criterion function of I2DPCA is produced, and the optimal projection axis vector of I2DPCA algorithm is the vector which maximizes its criterion function. Experimental results show that, the correct recognition rate of I2DPCA is higher than that of 2DPCA. In I2DPCA algorithm, the correct recognition rate fused by way of addition is higher than that by way of multiplication. (Jun-Ying Gan, Si-Bin He, 2009) |
| n) AnikaSharin, MahmudurRahman Khan, Hafiz Imtiaz, MirzaSaquib Us Sarwar, and ShaikhAnowarul Fattah proposed An Efficient Face Recognition Algorithm Based on Frequency Domain Cross-correlation Function. Their paper presents an algorithm for face recognition based on the principle of spectral domain cross-correlation. Instead of considering the spatial data of a face image as a whole, spectral feature is extracted from the each row of the spatial data individually. As each of these rows bears distinct characteristic of the face image, Considering row-wise Fourier domain representation of all of them ensures the extraction of detail variation in face geometry. It is shown that the cross-correlations obtained considering pairs of spectral representations of consecutive rows provide a signature of the particular face image reflecting the variation in the face geometry along the vertical direction. In a similar fashion, a horizontal signature can be obtained considering spectral crosscorrelations along consecutive columns. In the proposed method, both of these horizontal and vertical signatures are utilized in order to obtain a distinguishable feature space for a particular person. It is found that the proposed feature extraction algorithm offers advantages of simple practical implementation with a high degree of face recognition accuracy. (AnikaSharin, MahmudurRahman Khan, Hafiz Imtiaz, MirzaSaquib Us Sarwar, and ShaikhAnowarul, 2010) |
PRINCIPAL COMPONENTS ANALYSIS (PCA) ALGORITHM |
| Principal Components Analysis (PCA) is a statistical technique in modern data analysis that has found application in different areas such as face recognition. It can be used for data analysis and data compression. It reduces a complex data set to a lower dimension to disclose the hidden, simplified structures that often underlie it. It is a method to identify patterns in data, and express the data in a way to highlight their similarities and dissimilarities. PCA is appropriate when you have obtained measures on a number of observed variables and wish to develop a smaller number of artificial variables (called principal components) that will account for most of the variance in the observed variables. PCA is a variable reduction procedure. It is useful when there is some redundancy in variables. Which means that some of the variables are correlated with one another. We could possible reduce the observed variables into a smaller number of principal components (artificial variables) that will account for most of the variance in the observed variables. PCA is a linear transformation that transforms the data to a new coordinate system such that the new set of variables, the principal components, are linear functions of the original variables, are uncorrelated, and the greatest variance by any projection of the data comes to lie on the first coordinate, the second greatest variance on the second coordinate, and so on. In PCA we compute the covariance matrix for the full data set. Next, the eigenvectors and eigenvalues of the covariance matrix are computed, and sorted according to decreasing eigenvalue. |
EXPERIMENTAL DETAILS |
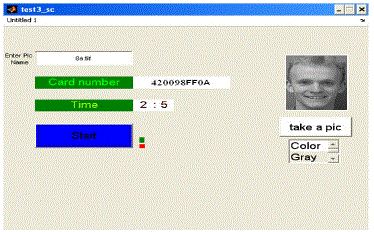
| The researcher started this paper by collecting and analyzing information about an RFID and Face recognition. The researcher have studied some of the face recognition (FR) algorithms and figured out that PCA is the popular algorithm have been used recently. In this paper the researcher has used discrete wavelet transform (DWT) for face recognition. DWT method have been used in data compression (JPEG2000). The researcher introduced RFID technology and its components.In this paper we have designed three systems, one is a MATLAB program for face recognition which capture an image by a camera and then recognize it from images in the database, the other system is RFID system using a MATLAB to scan and read user RFID card, and the third system is a communication system to send and receive a response by a modem to another station which take any response regarding to the result from station 1. We used graphical user interface (GUI) to let the user interact with the electronic devices (RFID reader, Camera, and Modem) with images rather than text command as it shown in the figure1. |
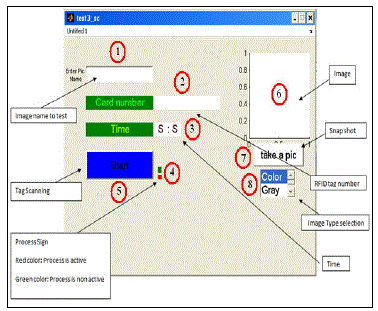 |
| Figure 3 shows an information and actions represented as graphical icons. Figure 1 contain several fields and buttons and they are as follow: |
| This field is for an image name to test face recognition function. |
| This field shows the RFID tag number. |
| This field shows the time. |
| This field shows the process status (active or not). |
| This button is for starting the program. |
| This field shows the image. |
| This button is for taking an image snapshot. |
| This field is to chose the type of an image (color or gray image). |
| The researcher used GUI to show processes graphically. figure 4 shows paper process steps. Each box represents a step, the red circle represents the step sequence, and the row represent the transportation from step to next. Steps as follow: |
| Capture an image by a camera. |
| Resize the image - optional step - to be identical to database field which is images data type. |
| Save the image in the database with a unique ID. |
| Recognize the image. |
| Scan the RFID tag. |
| Save the RFID tag number in the database. |
| Match the image with the RFID tag number |
| Result process |
| Send a response to a far away station 2 by using a phone line. |
| User retrieves the response from station 2. |
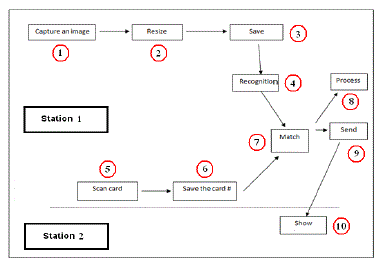 |
RESULT AND DISCUSSION |
| Inthis experiment ,we assume that there are 12 users( fig.) of the security system. Each of them hold an RFID card. The system is built to verify whether the card holder is the card owner. These 12 images are stored in database. |
 |
| The web-cam of the security system takes a snapshot when a person presents his RFID card to the system(fig.). The system scans RFID card. |
 |
| The security system match the recent image with the image in database. Once the imaged is matched , system sends the information to the other station through modem. Finally, it received response from other station like open the gate. Security is a request for all organizations or companies. Combining several security systems will gain significant improvements. The researcher has used DWT and an Euclidean distant measurement in face recognition system and he has got a good result. This method is not just used for face recognition but also we can use it for any type of recognition. We can enhance security by adding RFID system to face recognition system. By combine both system in one system we expect to increase security degree by 50%. To improve security more, we can share or send the result to a third part far away from the main station which has FR and RFID system. Finally, we developed Matlab program to to solve the paper problem. |
CONCLUSION |
| The researcher in this paper support face recognition with RFID and communication system. The researcher expect to increase strength of security by 50%. Face recognition under constrained condition and RFID are contactless processes. The approach presented in this paper for face recognition uses DWT and Euclidean distance method. Face recognition is a very important component in many applications like search engine and emotion detector. Furthermore, the researcher use a communication system to communicate with faraway station to be part of control process to boost the performance of the security process. The matlab code was developed and it met the design criteria and solve the paper problem. |
ACKNOWLEDGMENT |
| This article was funded by Deanship of Scientific Research (DSR), King Abdulaziz University, Jeddah. The authors, therefore, acknowledge with thanks DSR technical and financial support. |
References |
|