ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Subanivedhi N K1, Rekha M2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
For wireless sensor networks, large amount of transmission is decreased by a data aggregation scheme. To conceal communication during data aggregation homomorphic encryptions have been applied. Adversaries are not able to compromise the aggregators because they work on the encrypted data. But this does not satisfy multi-application environment because decrypting ciphertexts from different application will be incorrect. This scheme is insecure if sensor nodes are compromised. The base station does not have knowledge of aggregated result. An extended new concealed data aggregation scheme from the existing homomorphic public encryption scheme is proposed. This is built for multi-application environment. By CDAMA (Concealed Data Aggregation Scheme for Multiple Application), the ciphertexts from different application can be encapsulated into only one ciphertexts. The base station obtains application related data from single aggregated ciphertexts. It also reduces the settlement of single application environment attacks. It reduces the damage caused by unauthorized aggregations. It is also planned for secure counting capability. In this proposed system, ECDAMA (Enhanced Concealed Data Aggregation Scheme for Multiple Application) is designed to mitigate the impact of compromising a single aggregator by storing the replica of main aggregator in sub aggregator and to discover an alternate route to the base station is performed.
Keywords |
| homomorphic public encryption, data aggregation, ciphertexts, secure counting capability. |
INTRODUCTION |
| A wireless sensor network composed of number of sensor networks that are deployed to gather data from the environment. The various factors such as fault tolerance, network topology, hardware constraints, power constraints have to be considered during the design of the protocol. In order to minimize the power consumption, cluster based wireless sensor network have been considered. In cluster based architecture, sensor nodes in nearby region group together to form cluster and one of the node is elected as a cluster head. The cluster head aggregate the data collected from the sensor node into one data. So that number of data packet routed to the base station is reduced. |
| Even though data aggregation consumes less transmission power, it is prone to number of attacks. If the cluster head is compromised at some point of time then it is possible to forge the entire aggregated result. In order to overcome this problem, number of studies such as the delay aggregation [14], SIA (Secure Information Aggregation) [15], ESPDA (Energy-Efficient Secure Pattern Based Data Aggregation) [7], and SRDA (Secure Reference-based Data Aggregation) [12], have been proposed. |
| The one another approach to solve the problem of compromising an cluster head is to encrypt the data at sensor node itself. The cluster head are not have capable of encrypting the data thus forgering the cluster head does not again any advantage. Girao et al. [11] proposed concealed data aggregation (CDA) utilizes the privacy homomorphism encryption (PH) to assist aggregation in encrypted data. By leveraging the additive and multiplicative homomorphism properties, cluster head are able to execute algebraic operations on encrypted numeric data. In addition, he extended the ElGamal PH encryption to construct theirs. |
| CDAMA (Concealed Data Aggregation scheme for Multiple Applications) is an extension of Boneh et al.'s [13] PH scheme. It is designed for an multiple application wireless sensor environment. Sensor nodes with different application can be deployed in same environment. In convention data aggregation scheme [9], [10], [11], [12], [14], the decryption of aggregated ciphertext of different application is erroneous. The key to this problem is to aggregate the ciphertext of different application independently. This has significant impact in communication cost. With CDAMA, ciphertext of several application are encapsulated into an single ciphertext. Thus base station can extract application related plaintext using corresponding secret key. CDAMA reduce the impact of compromising sensor node through the construction of multiple groups. An opponent can forge data only in the compromised groups, not the entire system. It is also having the knowledge of secure counting. That is base station has the information about number of data aggregated. In this proposed work, A ECDAMA Scheme is extended to address the problem of main aggregator failure by incorporating the encrypted replica of main aggregator. |
II.RELATED WORKS |
| This section overviews pervious work on concealing the data and performing aggregation on the data. Lingxuan Hu and David Evans [14] proposed delayed aggregation and delayed authentication. Delayed aggregation delays aggregation of data for an single hop instead of immediate aggregation at sensor node. Delayed authentication delays the authentication for some period of time. Therefore it is resilient to intruders device and single device key compromise. |
| Bartosz et al.,[15] proposed Aggregate-Commit- Prove method that allow aggregator to aggregate the data collected from node, commit and prove that it uses the data collected from the sensor nodes. Hasan Cam, Suat Ozdemir, Prashant Nair and Ozgur San ali[7] proposed sleep-active mode coordination that allows to identity overlapping sensing range of some node to switch off. Thus it avoids duplicate transmission and saves energy. |
| Girao et al.,[9] proposed Privacy Homomorphism technique that allows to perform algebraic or statistical operation on encrypted data. Wu et al.,[13] proposed that classifier has set of keywords and they match these keyword against the received encrypted message. Based on the resultant, it forwards the data. |
| Perrig et al.,d[18] designed and developed SNEP (Secure Network Encryption Protocol) protocol to provide data confidentiality, data freshness, data authentication with minimal overhead. |
III.PROPOSED SYSTEM |
| Sensor nodes having different purposes are deployed an environment. Sensor nodes senses the value and encrypt these values using group key generated by the base station. Sensor nodes are responsible for forwarding the data to the sub aggregator. Sub aggregator aggregate the ciphertext of similar application and forwards to the main-aggregator. Main aggregator encapsulate the ciphertext of the different application into single ciphertext and routes to the base station. Base station can extract the application specific plaintext using the corresponding secret key. In this proposed system the problem of failure of the whole wireless sensor network with respect to main aggregator is eliminated by enhancing the ECDAMA scheme. The replica of main aggregator software is stored in the sub aggregator. If someone tries to compromise the main aggregator it sends error message to the sub aggregator and disconnects itself from base station. The sub aggregator now performs task of both sub aggregator and main aggregator as well as finds an alternate route to the base station. |
 |
IV.METHODOLOGY |
A.PRIVACY HOMOMORPHISM |
| Privacy homomorphism is an encryption scheme that has a homomorphic property. Privacy homomorphisms allows to map set of operations on cleartext to the set of operations on the ciphertext. Dk(Ek(m1)*Ek(m2))=m1+m2, where Ek() is the encryption with the key k, Dk() is the decryption with the key k, * and + denote the operations on the plaintext and ciphertexts. The Privacy homomorphic scheme can be classified as symmetric crytosystem where similar key is used for encryption and decryption. This scheme is considered to be more secure when an ciphertext space is larger then an cleartext space. |
B.CONCEALED DATA AGGREGATION |
| Conventional aggregation scheme allows any intermediate node to be forged thus they are considered to be insecure. PH scheme allows to perform aggregation operation on the ciphertext without decryption and they are more secure. The compromising any intermediate node gains no advantage. Girao et al [11] extended privacy homomorphic scheme to construct an aggregation in which all share a same key thus compromising any intermediate node will be able to forge. To solve this problem, each node share unique key in beginning of the transmission. By this forging a single node have no effect on it. |
C.ECDAMA |
| ECDAMA comprises of key generation, aggregation, and decryption processes. For ease we consider two user groups ie (k=2). Consider three points P, Q, H and theirs orders are q1, q2 and q3. The scalar of the two points carry aggregated message in a GA and GB and last point is used to carry random number for security. The aggregated ciphertext is multiplied by their order to get the aggregated message. The ciphertext from different applications are aggregated however they are not mixed. The message of each group can be obtained by simply decrypting the ciphertext with their private keys. |
| Pseudo code for key generation: |
| Step 1: Based on the security parameter τ, compute the values of (q1,q2,q3,E). E denote set of the elliptic curve points that forms a cyclic group. ord(E) = n and n=q1q2q3, such that q1, q2, q3 are large prime numbers and length of q1, q2, q3 are of same. |
| Step 2: Select three generators G1, G2, G3 in such a way that ord(G1) = ord(G2) = ord(G3) = n. |
M.R.ThansekharandN.Balaji(Eds.):ICIET’14 2526 |
 |
| The function of main aggregator is to encapsulate the ciphertext of different application into an single ciphertext. The replica of main aggregator is stored in sub aggregator. When an main aggregator is overwritten by an opponent, it sends error message to sub aggregator and disconnect itself from base station. Now the elected sub aggregator performs the task of both main aggregator and sub aggregator. The sub aggregator also finds an alternate path to route the packet. |
D.CONCRETE EXAMPLE |
| Consider a wireless sensor network consising of six sensor nodes, three aggregators and forming two clusters. The public key for sensors belonging to application A is denoted using subset of n, E, P, H, TA. Similarly, The public key for sensors belonging to application B is denoted using subset of n, E, P, H, TB. E indicates set of elliptic curve points that form a cyclic group. Points P, Q and H are orders of q1, q2, q3. In order to reduce the complexity, the values of P, Q, H are conveyed to small values. n is the product of q1, q2, q3. Messages from these sensor nodes are encrypted to ciphertexts. After aggregator aggregates the ciphertext, base station receives the final result. Now base station decrypt the aggregated message using corresponding group private key. |
E. KEY DISTRIBUTION |
| The base station is responsible for generating the group public keys and distributing it to the sensor nodes. The key distribution is done based on two methodology. The first method is key predistribution in which sensor node locations are known in prior. Therefore we insert keys and functions into sensor nodes and aggregators. |
| The second method is Key postdistribution. Here sensor nodes have their keys distributed in their prior location. The key can be of secret key or master key. After sensor nodes are deployed, cluster based protocol is used to elect the aggregator and construct the cluster environment. Now sensor node uses the shared key to encrypt the plaintext. |
V. APPLICATION |
A.WIRELESS SENSOR NETWORK WITH MULTIPLE APPLICATION |
| The deployment of sensor nodes with multiple application has significant reduction in organisation cost. It is more flexible. Consider a scenario of monitoring the physical environment of an IT industry where different rooms require different temperature eg : mainframe physical environment require temperature of about 18 to 24 degrees centigrade. Each room has some sensor nodes and aggregator. The main challenge is data privacy and to minimize the communication overhead because, sensor nodes encrypt the sensed values and ciphertexts are aggregated. Aggregating the ciphertext from different application is difficult because, decryption cannot extract exact sensed value. This overhead is reduced by this scheme. |
B. SECURE COUNTING |
| The main drawback in conventional concealed data aggregation scheme is that aggregator can manipulate aggregated result. There is a chance for aggregator to increase or decrease the aggregated value by continuously adding or subtracting value by a fixed number. Base station does not have the knowledge of number of data aggregated. Hence it cannot detect error. This is overcome by providing secure counting. Base station knows number of sensed values aggregated. |
VI. RESULTS AND DISCUSSION |
| The total cost of ECDAMA is very large. Although data aggregation scheme reduce number of data transmitted to base station, sensor nodes takes high cost for encryption and aggregation. |
| In this wireless sensor network, nodes are classified are leaf nodes, aggregator and base station. |
| Leaf nodes are deployed to gather information from the environment. Aggregators are similar to cluster head they aggregate the data sent from leaf nodes and sent to the base station. Base station decrypt the ciphertext using the corresponding key. Under ECDAMA scheme, leaf nodes consumes thousand times the energy greater than the conventional aggregation scheme. The aggregator at the level next to sensor node consumes energy ten times larger. The aggregator at next level consumes the energy equal to that of the traditional scheme. As the transmission moves closer to the base station, the energy consumption is reduced. |
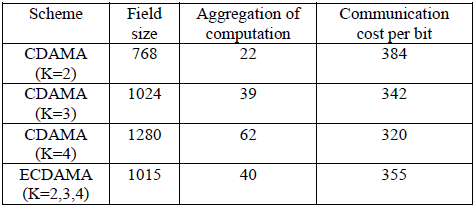 |
| Table 6.1 Aggregation Cost of Data Concealment Scheme |
| The result of field size, aggregation cost, communication cost of CDAMA AND ECDAMA Scheme with varying number of application is shown in the fig 6.1. |
 |
| The ECDAMA scheme shows better accuracy against four types of attacks namely ciphertext only attack, known-ciphertext attack, chosen-plaintext attack, chosen-ciphertext attack. The CDA scheme resist only against ciphertext only attack and CDAMA scheme survive against three attacks namely ciphertext only attack, known-ciphertext attack, chosen-plaintext attack. This is shown in the Fig 6.2. |
VII. CONCLUSION |
| ECDAMA is the concealed data aggregation scheme proposed for an multi-application environment. The ECDAMA under single application environment is found to be more secure then traditional scheme. For multi-application environment, data from different appliction can be aggregated but they are not mixed. The system also reduce the impact of compromising an aggregator. The result also shows that ECDAMA is more applicable to wireless sensor network while number of groups are not large. In future, we hope to apply this scheme to aggregate query in Database-As-a-Service (DAS) model[19]. |