ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
C. Suhashini1, S. Sivakumar2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Establishing correct and efficient routes is an important design issue in mobile ad hoc networks (MANETs), a more challenging goal is to provide secured routing, because ad hoc environment is accessible to both legitimate network users and malicious attackers. Moreover, as the wireless links are highly error prone and providing security is still a critical task. Generally, security in this type of network is provided by interference of signals, which is not energy efficient. Physical layer security has been considered to provide confidentiality against eavesdropping. Shift difference algorithm has been proposed to transfer the data securely over the network. It converts the data into noise for transmission. Network traffic has been reduced, as only intended participants transmit the data. By default network layer security has been provided by encryption.
Keywords |
| physical layer security, eavesdropping,network layer security. |
INTRODUCTION |
| Wireless networks are usually vulnerable to attacks by intruders of various nature, and there is no doubt that including security issues in the system design would be very desirable. One approach to security issues focuses on the physical layer [1]. Focusing on transmission-only problems, instead of detection ones. This problem can be traced back to the seminal 1975 work by Wyner [2] on the wiretap channel, where the tradeoff between the communication rate achievable by the legitimate user and the amount of information intercepted by the wiretapper, as measured in terms of equivocation, is addressed. Obviously, Wyner’s viewpoint was not focused on modern wireless networks and results form a solid basis for the modern approach to physical-layer security [3]– [8] and later generalized by Csiz´ar and K¨orner [9]. The wiretap channel assumes that the legitimate receiver has a better channel than the eavesdropper. For this reason, researchers have long considered that, in many wireless communication scenarios, the wiretap channel is impractical. various physical-layer techniques were proposed to achieve secure communication, even if the receiver’s channel is worse than the eavesdropper’s channel. |
| One of the main techniques is the use of interference or artificial noise to confuse the eavesdropper. With two base stations connected by a high-capacity backbone, one base station can simultaneously transmit an interfering signal to secure the uplink communication for the other base station [10], [11]. In the scenario where the transmitter has a helping interferer or a relay node, the secrecy level can also be increased by having the interferer [12] or relay [13] to send code words independent of the source message at an appropriate rate. |
 |
A. Unique Features of MANET |
| The following are the features of MANET by which it varies from other types of network. |
| Human interface: with device Screens and keyboards tend to be small, which may make them hard to use. Alternate input methods such as speech or handwriting recognition require training. |
| Security standards: When working mobile, one is dependent on public networks, requiring careful use of VPN (Virtual private Network). Security is a major concern while concerning the mobile computing standards on the fleet. One can easily attack the VPN through a huge number of networks interconnected through the line. |
| Power consumption: When a power outlet or portable generator is not available, mobile computers must rely entirely on battery power. Combined with the compact size of many mobile devices, this often means unusually expensive. |
| Transmission interferences: Weather, terrain, and the range from the nearest signal point can all interfere with signal reception. Reception in tunnels, some buildings, and rural areas is often poor. |
| Distributed operation: There is no background network for the central control of the network operations; the control of the network is distributed among the nodes. The nodes involved in a MANET should cooperate with each other and communicate among themselves and each node acts as a relay as needed, to implement specific functions such as routing and security. Multi hop routing: When a node tries to send information to other nodes which is out of its communication range, the packet should be forwarded via one or more intermediate nodes. |
| Autonomous terminal: In MANET, each mobile node is an independent node, which could function as both a host and a router. |
| Dynamic topology: Nodes are free to move arbitrarily with different speeds; thus, the network topology may change randomly and at unpredictable time. The nodes in the MANET dynamically establish routing among themselves as they travel around, establishing their own network. |
| Light-weight terminals: In maximum cases, the nodes at MANET are mobile with less CPU capability, low power storage and small memory size. |
| Shared Physical Medium: The wireless communication medium is accessible to any entity with the appropriate equipment and adequate resources. Accordingly, access to the channel cannot be restricted. |
II.BACKGROUND AND RELATED WORK |
| This section introduces some background knowledge including the network Architecture and some related works. |
A. ENERGY EFFCIENCY |
| MANETs, therefore, impose a very fundamental constraint on the security solution being designed for this environment, i.e. “the security solution needs to be highly efficient in energy consumption”, and it translates to the following requirements: |
| Minimum Control Overhead: Control overhead (bytes or packets) of the routing protocol needs to be minimized. Lower the control overhead, higher is the channel bandwidth utilization due to minimizing the transmission of redundant control bytes. Moreover, lower energy would be required to actually transmit and/or receive bits at the network interface card. |
| Minimum Computational Complexity: An algorithm with lower computational load allows the mobile node to achieve longer battery life by consuming less amount of energy for its internal processing. |
| Energy efficient routing requires optimizing the packet routing process for lower energy consumption. However, none of the classical MANET routing algorithms have been designed keeping in view energy efficiency. The authors in [9] studied DSR and AODV for energy efficiency and report that protocol design parameters, such as lower delay and higher packet delivery ratio, do not achieve low energy consumption. |
B. Related Work |
| The popularity of MANETs has lead to an increasing interest in addressing their security issues. There are a number of proposals for secure MANETs that are based on standard cryptography and Artificial Immune Systems (AISs). The cryptographic systems include both the symmetric as well as asymmetric approaches. The AODV protocol has been secured by a public key system (using asymmetric keys) through Secure Ad-Hoc Ondemand Distance Vector protocol (SAODV) [15]. While the DSR protocol has a secure version ARIADNE [16], which employs symmetric key cryptography to provide security to the source routing process. However, cryptography includes compute intensive mathematical operations [17], especially the asymmetric systems, and thus imposes heavy computational load on mobile nodes causing rapid battery depletion. Moreover, most of these security systems involve computing digital signatures and/or message hashes and transmitting them along with the data, resulting in transmission of additional control information, which reduces the effective protocol throughput. |
C.SECURITY GOALS |
| In MANET, all networking functions such as routing and packet forwarding, are performed by nodes themselves in a self-organizing manner. For these reasons, securing a mobile ad -hoc network is very challenging. The goals to evaluate if mobile ad-hoc network is secure or not are as follows: Availability: Availability means the assets are accessible to authorized parties at appropriate times. Availability applies both to data and to services. It ensures the survivability of network service despite denial of service attack. Confidentiality: Confidentiality ensures that computerrelated assets are accessed only by authorized parties. Protection of information which is exchanging through a MANET. It should be protected against any disclosure attack like eavesdropping- unauthorized reading of message. |
| Integrity: Integrity means that assets can be modified only by authorized parties or only in authorized way.. Integrity assures that a message being transferred is never corrupted. Authentication: Authentication is essentially assurance that participants in communication are authenticated and not impersonators. The recourses of network should be accessed by the authenticated nodes. |
| Authorization: This property assigns different access rights to different types of users. For example a network management can be performed by network administrator only. |
| Resilience to attacks: It is required to sustain the network functionalities when a portion of nodes is compromised or destroyed. |
| Freshness: It ensures that malicious node does not resend previously captured packets. |
 |
III. ALGORITHM |
A. TRIPLE DATA ENCRYPTION STANDARD |
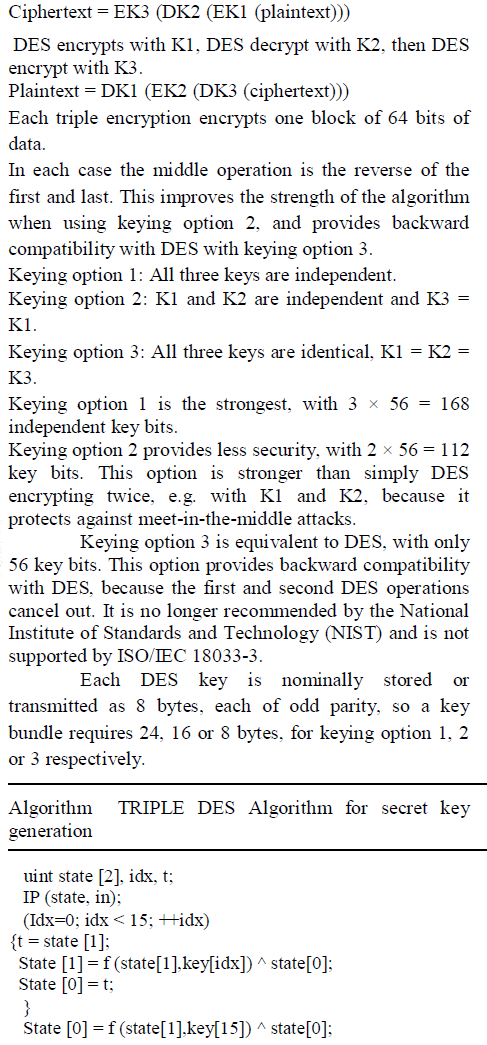
| In cryptography, Triple DES is the common name for the Triple Data Encryption Algorithm (TDEA or Triple DEA) block cipher, which applies the Data Encryption Standard (DES) cipher algorithm three times to each data block. |
| The original DES cipher's key size of 56 bits was generally sufficient when that algorithm was designed, but the availability of increasing computational power made brute-force attacks feasible. Triple DES provides a relatively simple method of increasing the key size of DES to protect against such attacks, without the need to design a completely new block cipher algorithm. |
| Triple DES uses a "key bundle" which comprises three DES keys, K1, K2 and K3, each of 56 bits (excluding parity bits). |
 |
 |
B. SHIFT DIFFERENCE ALGORITHM |
| Due to the increase in business transactions in the internet. There is a need for safety data transmission. There exists a threat to the message that we transmit using old known encryption algorithms, because it is known public to all. Hence we introduce a new algorithm for safety data transmission. |
| Read the first character of the file and use this as key for subsequent characters. Find the difference (D) for the successive characters and write the difference in the cipher text file. |
| If D=+ve, write the D value as such. |
| If D=-ve, we use a filler character and the D value. |
| The filler character is a prime number. The key is shifted either as left shift or right shift on the cipher text, based on number of bits. Hence the key on the cipher text is even changed which provides the strong security. For decryption Reverse shift to the shift that done on the Encryption side to Obtain the Key. The key Obtained will be used for the generation of the plain text. The algorithm is simple and secure, because the key is not intelligible to the hacker. The encrypted text is independent of language. Shifting numbers is an Prime Number, hence it is difficult to identify. |
 |
IV. CONCLUSION |
| A simple application is created for secure data transaction in mobile ad hoc network. Physical layer security is considered to provide confidentiality against eavesdropping. Physical layer encryption has been provided, by encrypting the data before being transmitted in the network. Network layer security is provided as default. Physical layer security has been provided by transmitting data as noise over the network. An enhancement to this application can be considered to provide physical layer encryption, while transmitting data from multiple source to single destination and from multiple source to multiple destination. |
References |
|