ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
U.Sathya Rekha, Mrs P.Hemalatha
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Data aggregation is implemented in wireless sensor networks to reduce data redundancy and to summarize relevant and necessary information without requiring all pieces of the data and to reduce large amount of data transmission.Homomorphic public encryption is the proposed scheme designed for multiapplication environment. The base station extracts application-specific data from aggregated cipher texts, and compromised attacks in single application environments, and to degrade damage from unauthorized aggregations. To enhancing a new approach as symmetric key algorithm used where the keys for encryption and decryption are done in same shared secret. These keys are used to provide security in data aggregation and separate the cipher text when it stored and retrieve from database. In Database As a Service (DAS) model, the client has to secure their database. The attacker cannot change the data because it is dynamically created.
Keywords |
| Aggregation, Homomorphic public Encryption, Symmetric Key, Database Asa Service, Attacker, Cipher text |
INTRODUCTION |
| Wireless Sensor Networks (WSNs),consist of thousands of sensor nodes (SN) that gather data from deployed environments and it is used in plenty of rich applications, such as environment monitoring, accident reporting, and military investigation. Depending on the purpose of each application, SN is customized to read different kinds of data. The aggregators collect data from a subset of the network and aggregate the data and aggregate function. Aggregation reduces the amount of network traffic which helps to reduce energy consumption on sensor nodes in WSN, the aggregators in a secure data aggregation scenario need to decrypt the encrypted data to perform aggregation.Girao et al [4] proposes an additive and multiplicative homomorphic encryption that allows aggregation of encrypted data and it is secure and efficient. Concealed data aggregation(CDA) schemesthatarebasedonthehomomorphiccharacteristicsof aprivacy homomorphism(PH)enableend-toendencryptioninwirelesssensornetworks.. CDA requires that a key be distributed to a subgroup of nodes that form a reverse-multicast routable region in the WSN. This key enables the nodes to perform end-to-end encryption where the corruption of one node, or a subset of nodes. The CDA approach significantly reduces the energy consumption at aggregator nodes since no encryption and decryption is performed. |
| Concealed Data Aggregation in Multiple Applications (CDAMA) is the scheme that provides Concealed Data Aggregation (CDA) between multiple groups. CDAMA having two limitations when it aggregate multiple applications that shared in WSN can reduce the system cost and improvesystem flexibilitysuch as |
| ïÃâ÷ CDA requirements provide solutions to maintain data privacy and reduce the communication overheads; corresponding cipher text must be aggregated. |
| ïÃâ÷ Aggregation of multi-application is still hard even if aggregation of cipher texts is possible, becausethe decryption cannot extract application-specificaggregated result from a mixed cipher text. |
| A. Characteristics of CDAMA are as follows: |
| ïÃâ÷ Designed for multiple applications in WSN. In this characteristic, cipher text of different applications can’t aggregate together. |
| ïÃâ÷ In CDAMA, cipher text of different applications aggregate into a single cipher text. |
| ïÃâ÷ Designed for single application WSNs and it mitigates the impact of compromising SN through the construction of multiple groups. |
| ïÃâ÷ Designed for secure counting. The base station doesnotknow how many messages are aggregated from the decrypted aggregated result. |
| CDAMA having several issues including efficient implementation, cipher text length and curve selection. First operations in CDAMA are based on scalar multiplication on elliptic curvepoints, skills which accelerate scalar multiplications that can enhance the performance of CDAMA. Secondly the length of cipher texts isalso defined because of deciding the lowest bound of cipher text length for sufficient security. |
B. CDAMA Requirements: |
| CDAMA requires bandwidth, security, Data integrity, authentication [4][8]. |
| a) Bandwidth: The bandwidth overhead attributed to sending ciphertexts should not require the transmission of large amounts of additional data. |
| b) Provable Security: Thesecurityleveloftheencryption scheme should be measurable and it should be based upon the commonly agreed hardness of a mathematical problem to be provably computationally secure. |
| c) Data Integrity:Data integrity ensures the receiver that the received data is not altered in transit by an adversary. Integrity can be implemented to ensure that information is not altered in any unexpected way. |
| d) Authentication:It is necessary that the interface defined between the user, the system and the admin has to provide authentication. In a sensor network, an adversary can inject the messages and the authentication techniques can verify the identity of data using symmetric key. The privacy homomorphic encryption functions only one-way authentication of sensor data at the base station only. |
| e) Authorization:Data authorization specifies access rights to resources and is strongly related to access control. Access control should prevent unauthorized users from participating in network resources. |
| C. Types of Attacks: |
| CDAMA faces several types of attacks[8], they are as follows; |
| a) Ciphertext Analysis:Themostbasicattackis the analysisofencryptedpacket; the adversarywantstoobtaininformationonlyby interpreting cipher texts.InWSNswithascarcedomainofvalues,the attackcanveryefficientlyresultinadeductionoftheplaintexts |
| b)KnownPlaintextAttack: |
| Theadversarytriestodeterminesecret informationwiththeadditionalknowledgeofplaintexts.With knownplaintextandcorrespondingcipher text,itis theaimoftheadversaryeithertorevealthesecretkeyoratleastt ogatheradditionalinformationthatcanbeexploited todeductmaliciouscipher textsordecryptothermessages. |
| c) Malleability:Malleability is simply variation of the attack that would generate the cipher text that is correct. |
| d) ForgePackets:An adversary doesn’t need to modify existing data, if she is able to create correctly encoded cipher text with a specific content. The attacker could substitute the packets of sensed value that the forge done. APH scheme that is resistant to maliciously forged packets must not allow any third party to create properly encoded messages atleast not without be in able to detect the interference during decryption. |
II. RELATED WORK |
| In WSN,sensor data must be encrypted with a single key to perform concealed data aggregation sensor nodes in the network must share a common key and use it for encryption. Using a single symmetric key in the network is not secure as an adversary can fake the aggregated results through compromising only a sensor node. |
| Symmetric key based privacy homomorphism is shown to be insecure for chosen plaintext attacks for some specific parameter settingsas dropping or forging messages and transmitting false data. Witness nodes of data aggregators alsoaggregate data and compute MACs to help verify the correctness of the aggregators’ data at base station because the data validation is performed at base station, thetransmission of false data and MACs up to base station affect adversely the utilization of sensor network resources. |
| Due to their high computational overhead, asymmetric key homomorphic encryption algorithms are not feasible for sensor nodes. The privacy homomorphic encryption algorithm introduced by Domingo[3] Ferrer is symmetric key based. The concealed data aggregation algorithm that is proposed which employs Domingo[3] Ferrer’s privacy homomorphic encryption algorithm. |
 |
| However in order to aggregate the data of the all network, the proposed scheme must uses a secret key known by all sensor nodes which leads to provide effective security to data. If a sensor node is compromised, it can decrypt data of any sensor node which is encrypted by the secret key. |
| Dolev Yao threat model [6], theattacker can capture a sensor node and acquire al linformation stored withinit. Should the attacker capture a subset of sensornodes, the probability that captured nodes are from the same region is higher than if the captured nodes areequallydistributedovertheWSN. |
| OkamotaandUchiyama [9] proposedapublickeycryptosystemwithhomomorphicproperties, whichispro ventobeassecure. |
| Castellucciaetal. [2] presentedanefficient aggregationofencrypteddatainwirelesssensornetworks whichisalsobasedonadditivelyhomomorphicfeaturesof theencryptionscheme based on an extension of the onetime pad technique.Thisapproachusesdifferentkeys persensoratthecostofmandatorytransmittingthesensorIDlis toftheinvolved monitoring nodes. |
| Chan et al [7] present the first secure hierarchical data aggregation scheme based on aggregation commit verify, which forces the adversary to commit to its choice of aggregation results and then allow the sensors to verify whether their aggregation contribution is correct or not. |
| Goldwasser and Micali [7] is to provide data security, goal is to prevent an attacker from gaining information about sensor data. |
 |
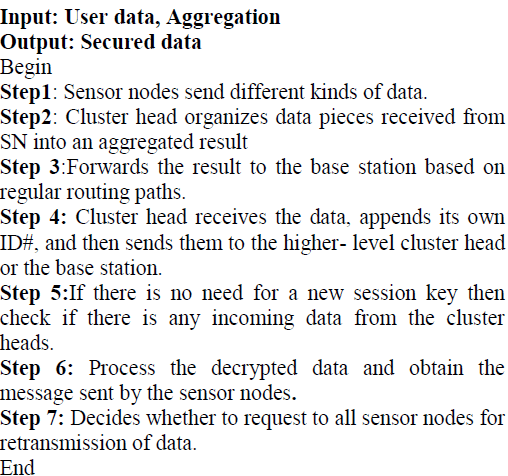
| In WSN’s, sensor nodes sends the encrypted data that is capable of performing some processing the data to cluster Head, CH organizes data pieces received from SN into an aggregated result, and then forwards the result to the base station based on regular routing path. Aggregators would forward the results to the next hop after the aggregation done. In order to perform aggregation, aggregators are used to increase the lifetime, tree-based or cluster networks force the intermediate nodes. Whenever the user needs information for the group or individual it will send to the BS. The base station received the request and split the cipher text. Performing the reverse aggregation the cipher text can decrypt to sends the data for users. The CH sends the result to aggregation, after aggregation done the results must be sends to base station. Base station now can extract the data (cipher text) with decryption and verifies the decrypted data is secured and finally the data must be stored in database repository.An important aspect of encryption scheme for aggregation in WSNs is that the sink node needs to be aware of the encryptors id’s such that it can regenerate the correct key stream for decryption purposes. Because WSNs are not always reliable, it cannot be expected that all nodes reply to all requests. There need a mechanism for communicating the id’s of the non-responding nodes to the base station. |
IV. IMPLEMENTATION |
| The process is divided into several major tasks such as sensor node and group aggregation, attacker, key generation, data security. |
Sensor Node and Group Aggregation |
| Multi group data can collect which is used to create and separate the node and aggregate it. The aggregate node can analyse the cipher text, and can verify the message in group data from multi group data and produce the result that must be stored in base station.SN collect information from deployedenvironments and forward the information back to base station (BS) via multihop transmission based on a tree or a cluster topology. The tree-based or cluster networks force the intermediate nodes (a sub tree node or a cluster head) to perform aggregation, i.e., to be aggregators (AG). After aggregation done, AGs would forward the results to the next hop. The source information for data aggregators may originate from public data. Aggregator nodes summarize the datasets in order to provide a higher level view of available data. After aggregation the cipher text is encoded after it has been passed through an encryption. The cipher text is the product or combination of plain text and its encryption. |
Attacker |
| Base station sends data which is aggregate to form a cipher text, when encrypting a group keys and a cipher key to produce a cipher text. Attacker can collect the cipher text, then find whether the data has attacker, attacker is inside the text then analyse the text send back to user if the attacker is not present in cipher text then decrypt the data and send to user. Adversary wants to send the forged messages to cheat the BS even though she does not know the secret key. Attacker is a special type of player, usually one whose role involves aggressive data. A group key is a cryptographic key that is shared between groups of users. Group key are distance by sending them to individual users physically or encrypt individually for each user using either that user’s pre distributed private key. |
| Secure aggregation is required when an attacker may capture secret data as sensor networks are vulnerable. Symmetric key cryptography algorithms are possible to achieving the secured data. |
Key Generation |
| Cluster Head can aggregate the data sent by a sensor after aggregation the Cluster Head can generate a key added to the aggregated data, after aggregation finally the data are sent to base station. Key generation is the process of generating keys for cryptosystem. A key is used to encrypt or decrypt whatever data is being encrypted or decrypted. Key Generator objects are reusable, i.e., after a key has been generated, the same Key Generator object can be re-used to generate further keys. There are two ways to generate a key: in an algorithm-independent manner, and in an algorithmspecific manner. The only difference between the two is the initialization of the object. |
Data Security |
| Initially the base station can verifies the key from the aggregated data sent by the Cluster Head, after verifying the keys the base station can decrypt the aggregated data. Data security is used to protecting a database from destructive forces or unwanted actions of unauthorized users. |
 |
 |
V. EXPERIMENTAL RESULTS |
| The following graph shows the security level of data when Symmetric Key compared with other algorithms such as Homomorphic Encryption (HE) and Homomorphic Public Encryption (HPE). Symmetric Key can provide 90-96% secured data from an attacker. |
 |
VI. CONCLUSION AND FUTURE WORK |
| CDAMA is the first multi-application environment; the cipher texts from distinct applications can be aggregated, but not mixed, and in singleapplication environment, CDAMA is still moresecure than other CDA and finally mitigates the impacts and reduces damage from a compromising attacks occur in WSNs. Thus CDAMA provide secure counting, and the base station would know the exact number of messages aggregated. |
| In future, CDAMA can be applied to realize aggregation query in Database-As-a-Service(DAS) model. By using symmetric key aggregating multiple applications can provide more security to all the data aggregated. In DAS model, a client stores her database on an untrusted service provider and the client has to secure their database through PH schemes because PH schemes keep utilizable properties than standard ciphers. |
| Symmetric Key can be implemented in base station when an attacker trying to change the data. In Base station, symmetric keys are used to conceal the encrypted data whatever sends to server, DES cryptosystem act as a buffer when sending and receiving the data from users. Thus the DES cryptosystem in symmetric key are used to aggregate multiple audios, videos in future and it is used in critical area surveillance, web applications and military applications. |
References |
|