ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Balasubramanian.C1, Prasanthi.T2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Cloud computing is an emerging technology of computing environment in the upcoming themes. The cloud provides an outstanding amenity to the business people, individuals, organizations, etc., with flexible infrastructure and storage as a service. Cloud computing is a type of computing that relies on sharing resources among the cloud users from a shared pool of computing resources (network, services, applications, server, databases, etc.). This computing move the application software‟s, databases and user files to the large data centers, where the management of these data may not be fully trustworthy. Cloud is the fullest innate with numerous security challenges, which cannot be well understood by the cloud users. Allowing users to store a large amount of data, including the sensitive information in the cloud stimulates the highly skilled attackers, thus creating a need for security to be considered as one of the top issues that exists within cloud computing. This paper depicts the survey on security issues raises in cloud computing and how the cryptographic functions are involved to preserve the integrity, confidentiality and availability of the user data.
Keywords |
| cloud computing, Data Confidentiality, Data Integrity, Data Security |
INTRODUCTION |
| Cloud computing is a model for enabling everywhere, well-located, on-demand network access to a shared pool of configurable computing resources (e.g., networks, servers, applications, and services) that can be rapidly provisioned and released with minimal management effort. Cloud is used to describe a new class of network based computing that takes place over the Internet. Cloud computing environment provides conventional services to be met are infrastructure and service providers. The Cloud platforms are managed and charter out the resources to users on-demand, by the infrastructure providers. The resources from infrastructure providers are sent as loan to the end users. The giant companies like Google, Microsoft, and Amazon has attracted towards cloud computing and considered as a great influence in today’s Information Technology industry. Business owners are paying more attention to cloud computing concepts because of several features. |
| The features are as follows: |
| • Lower initial investment |
| • Scalability |
| • Deploy faster |
| • Location independent |
| • Device independent |
| • Reliability |
| • Security |
| Although cloud computing has shown considerable amount of opportunities to the IT industry, but still there is a number of challenges to be addressed carefully. The main aim is to provide a better understanding of cloud computing and the ongoing research in this tremendously thriving arena of computer science. |
CLOUD COM PUTING OVERVIEW |
| A. Cloud Computing Definitions |
| Cloud computing is a technology where the users dig up resource (Application software’s, databases, platform etc.,) as a service from the Cloud by paying perservice basis, over the internet. |
| Buyya’s definition states that “A cloud is a type of parallel and distributed system consisting of a collection of interconnected and virtualized computers that are dynamically provisioned and presented as one or more unified computing resources based on service-level agreements established through negotiation between the service provider and consumers”. The Cloud model is composed with the following essential characteristics, three service models and four deployment models. |
| B. Essential Characteristics of Cloud |
| Cloud computing exhibits five essential characteristics defined by NIST (National Institute of Standards and Technology). |
| 1. on-demand Self-Service. A consumer can acquire unilateral computing resources by pay per-service basis. |
| 2. Broad Network Access. The resources are available over the network and accessed through standard mechanisms that endorse the usage by various thin or thick client platforms. |
| 3. Resource Pooling. The service provider’s pooled the computing resources to serve diverse users, with different the physical and virtual resources dynamically. The resources should be assigned and reassigned according to the consumers demand. |
| 4. Selection of Provider. A good service provider is the key to good service. So, it is crucial to select the right service provider. One must make sure that the provider is consistent, well-reputed for their customer service and should have a verified path record in IT- related ventures. |
| 4. Rapid Elasticity. Capabilities can be rapidly and elastically provisioned to the cloud users dynamically and automatically. |
| 5. Measured Service. Cloud systems automatically control and optimize resource use by leveraging a metering capability at some level of abstraction appropriate to the type of service. |
| C. Cloud Deployment Models |
| Private cloud is a cloud infrastructure operated solely for a single organization, whether managed internally or by a third-party and hosted internally or externally. Undertaking a private cloud project requires a significant level and degree of engagement to virtualized business environment, and requires the organization to reevaluate decisions about existing resources. |
| Public cloud is a cloud where the services are rendered over a network that is open for public use. The users can obtain services from this cloud from the owned organizations. |
| Hybrid cloud is a combination of one or more clouds. Such composition expands deployment options for cloud services, allowing IT organizations to use public cloud computing resources to meet temporary needs. |
| Community cloud involves sharing of computing infrastructure in between organizations of the same community. For example all Government organizations within the state of California may share computing infrastructure on the cloud to manage data related to citizens residing in California. |
| D. Offered Cloud Services |
| Cloud provides the various service models to the users such as, |
 |
| Infrastructure as a Service (IaaS) is providing general on-demand computing resources such as virtualized servers or various forms of storage (block, key/value, database, etc.) as metered resources. This can often be seen as a direct evolution of shared hosting with added on-demand scaling via resource virtualization and use-based billing. |
| Platform as a Service (PaaS) is providing an existent managed higher-level software infrastructure for building particular classes of applications and services. The platform includes the use of underlying computing resources, typically billed similar to IaaS products, although the infrastructure is abstracted away below the platform. |
| Software as a Service (SaaS) is providing specific, already-created applications as fully or partially remote services. Sometimes it is in the form of web-based applications and other times it consists of standard nonremote applications with Internet-based storage or other network interactions. |
STUDY OF SECURITY ISSUES AND THE PROSPECTIVE SOLUTIONS |
| A. Issues in Cloud Storage Security |
| Security in the cloud is one of the major areas of research. The survey shows that, the researchers are focused on efficient algorithms and the traditional encryption techniques to enhance the data storage security in the cloud. |
| Recent days many of the Organizations or individuals stored their data in cloud in order to acquire an instant access to the stored data over the internet. But with the stored data, there is a loss of integrity and confidentiality over the network. For Examples., the Red Hat servers in cloud were corrupted in 2008, still they remain highly confident that their systems and processes prevents the intrusion from compromising RHN and accordingly made customers to believe that their systems updated using Red Hat Network are not at risk. |
| Qian Wang et al., proposed a novel model for dependable and secure data storage with dynamic integrity assurance [7]. Based on the proposed principle of secret sharing and erasure coding, a hybrid share generation and distribution scheme is proposed to achieve a reliable and fault tolerant initial data storage by providing redundancy for original data components. To further dynamically ensure the integrity of the distributed data shares, we then propose an efficient data integrity verification scheme exploiting the techniques of algebraic signature and spot-checking. The proposed scheme enables individual sensors to verify in one protocol execution the correctness of all the pertaining data shares simultaneously in the absence of the original data. |
| Ateniese et al., stated the model for Provable Data Possession (PDP) to ensure the possession of a file at untrusted storages [3]. The public key based homomorphic tags are utilized for auditing the user’s data file. However, the precomputation of the tags imposes heavy computation overhead that can be pricey for an entire file. In their subsequent work in 2008, PDP scheme used symmetric key based cryptography. This method shows a lower-overhead than their previous proposed scheme and also allows for block updates, deletions and appends to the stored file. This scheme focuses only on the single server scenario and does not provide the assurance of data availability against server failures and thus left both the distributed scenario and data error recovery issues uncharted. |
| Juels and Kaliski present proofs of retrievability (PORs), focusing on static archival storage of large files [6]. Their scheme’s effectiveness rests largely on preprocessing steps the client conducts before sending a file F, to the server: “sentinel” blocks are randomly inserted to detect corruption, F is encrypted to hide these sentinels, and error-correcting codes are used to recover from corruption. As expected, the error-correcting codes improve the error-resiliency of their system. Unfortunately, these operations prevent any efficient extension to support updates, beyond simply replacing F with a new file F′. Furthermore, the number of queries a client can perform is limited, and fixed a priori. Let N be an RSA modulus. The verifier stores k = F mod φ (N) for file F (suitably represented as an integer).To challenge the prover to demonstrate retrievability of F, the verifier transmits a random element H ∈ . The prover returns s = , and the verifier checks that mod N = s. This protocol has the drawback of requiring the prover to exp onentiate over the entire file F . |
| Cong wang et al., projected the ideas for generating the proofs of data storage in the cloud by homomorphic identication protocols [7].It allows the client to verify whether the cloud server loyally stores the copy of a file. In prior, the proof of storage was developed from the homomorphic linear authenticator (HLA) but later it was generated from the signatures and message authentication codes (MAC). |
 |
| This scheme commonly translates any HLA to verifiable proof of storage where the complexity of communication and the client’s state are autonomous of the file size. |
| Sadiaet al., implements an extensive authentication protocols with RSA to enhance the security of cloud computing [8]. This scheme is to ensure the storage correctness of the users file previously stored in the cloud. It proposes the two sections, one of which analyzing the attackers involved in accessing the client data and the other uses Challenge-Handshake Authentication Protocol (CHAP) for authentication , RSA for encryption of users data. In this research, the asymmetric key encryption (RSA) encryption algorithm is used for cryptography. In RSA, anyone can encrypt messages using the public key, but only the holder of the paired private key can decrypt. Security depends on the secrecy of that private key and two parts of the key pair are mathematically linked. |
| Lanxiang and Gongde, have discussed the RemoteData Checking (RDC) scheme, that incorporates the mechanisms to mitigate arbitrary amounts of data corruption in cloud server [23]. In particular, protection against small corruptions (i.e., bytes or even bits) ensures that attacks modify a few bits do not destroy an encrypted file or invalidate authentication information. The initial solution to the integrity problem is RSA based hash functions to hash the entire file at every challenge. This technique solves the initial problem of storing data to the external server that verify the sever continually and faithfully stores entire file. But the problem with this technique is providing exponential over the entire file F and accessing the entire file’s blocks. This is clearly prohibitive for the server whenever the file is large. Early RDC schemes have focused on static data, whereas later schemes such as DPDP support the full range of dynamic operations on the outsourced data, including insertions, modifications, and deletions. |
| Wayne stated the benefits of cloud computing and the basic security issues associated with the cloud services [9]. The security issues faced by end users or clients are mandatory. The researchers and professionals generate the strong security policies to make sure that the data is safe and prohibited from an unauthorized access, in both corporate data centers and in the cloud servers. The key security issues recognized and addressed in this paper are end user trust, Insider Access, Visibility, Risk Management, Client-Side Protection, Server-Side Protection, Access Control and Identity management. The main work is to identify and discuss the cloud security issues and in this they didn’t proposed any tool or framework to address these issues. |
| B. Prospective Solutions |
| To boost the security in cloud server data by using the cryptographic techniques: |
| 1. Cryptographic Encryptions |
| Encrypting data is one of the solutions to secure cloud data , but it limits the efficiency of the cloud. This is because encrypted documents must first be decrypted before they can be searched or manipulated. Furthermore, cloud data must be encrypted before storing. Performing encryption and decryption on large data sets can be prohibitively expensive and time consuming. The data loss in server will violate the data integrity and affects the storage correctness in cloud. |
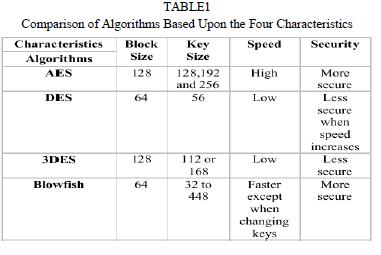
| DES: (Data Encryption Standard), was the first encryption standard to be recommended by NIST (National Institute of Standards and Technology). Since many attack that exploit the weaknesses of DES, which made it an insecure block cipher. |
| 3DES (Triple DES), the enhancement of DES is, the 3DES. In this standard, the encryption method is similar to the original DES but the encryption level is increased by 3 times and slower than other block cipher methods. |
| AES: (Advanced Encryption Standard), is the new encryption standard recommended by NIST to replace DES. Rijndael (pronounced Rain Doll) algorithm was selected in 1997 after a competition to select the best encryption standard. Brute force attack is the only efficient attack known against AES, since the attacker tries all the possible combinations of characters or values to unlock the encryption. |
| BLOWFISH: It is one of the most common public domain encryption algorithms provided by Bruce Schneier. Blowfish is a variable key length of 64 bit block cipher. This algorithm can be optimized in both hardware applications and software applications. Although it suffers from weak key problems, no attack is known to be successful against this standard. |
 |
 |
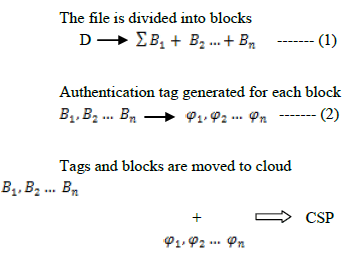
| 2. Homomorphic Metadata Generation |
| The homomorphic metadata are generated based on the message authentication codes, where these codes are constructed based on the hash functions. In hashing algorithm, mathematical function is applied to the data, an alphanumerical value is produced. There are many different hash functions, SHAâÃâ¬ÃÂ1, 256, 512, MD5, CRC etc., that each returns a unique value. A set of data will produce the same hash value in most cases, as long as the same mathematical function is used and nothing in the data has been changed. The value that is produced can be thought of as a “digital fingerprint”. |
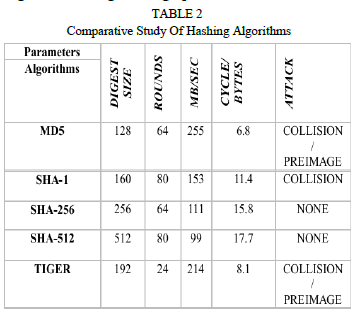 |
| It is possible for two different sets of data to come up with an identical hash value. When two sets of data produce the same hash value, it is called a “Collision”. For a collision resistant hash function H, it is computationally infeasible to find out any two data’s D and D’ such that H (D) = H (D’) where D = D’. Then the authentication tag is generated based on hashing algorithms. |
 |
| SHA1, for example, a collision rate of 2^69, (5.9 x 10^20).Hash algorithms have different Collision rates. Using multiple hashing algorithms also reduces the chance of having a collision. |
| 3. Auditing |
| In cryptography, a Trusted Third Party (TTP) is an entity which facilitates secure interactions between two parties who both trust this third party. The scope of a TTP within an Information System is to provide end-to-end security services, which are scalable, based on standards and useful across different domains, geographical areas and specialization sectors. In cloud environment includes the Trusted Third Party Auditor (TTPA) for verifying the data storage correctness of cloud server in a timely manner. As described by Castell, „„A Trusted Third Party is an impartial organization delivering business confidence, through commercial and technical security features, to an electronic transaction. It supplies technically and legally reliable means of carrying out, facilitating, producing independent evidence about and/or arbitrating on an electronic transaction. Its services are provided and underwritten by technical, legal, financial and/or structural means’’. Mainly auditing scheme involves the following algorithms: |
 |
CONCLUSIONS |
| Cloud Computing is an extension of distributed computing systems. For example, “VPN tunneling can be used for secure communication; existing encryption methods can be used to ensure protection of data on the cloud; and existing user-centric authentication methods, such as Open ID, can be used to authenticate with cloud services”. There are number of inbuilt features in cloud computing, such as “resource pooling, multitenancy, rapid elasticity, broad network access, and on-demand self-service”, where the existing security techniques are not adequate to deal with cloud security risks. This paper, presents a survey on cloud computing and the cryptographic techniques are involved to address the cloud computing security issues. The security techniques are used by the clients and end users on data based on PKI and hashing functions, in order to achieve the integrity, confidentiality, privacy for the stored data etc. |
References |
|