ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Ram kumar.R1, Vijayalakshmi.B2,Revathi.S3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
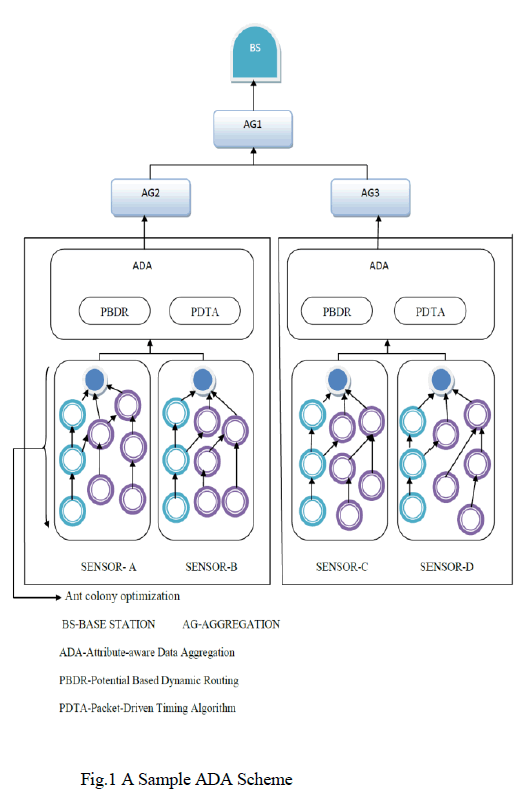
The fundamental challenge in design of wireless sensor network is to enhance the network lifetime. Many factors are taken into account for the maximization of life time of wireless sensor networks, such as minimizing the power consumption, low cost operation, optimal routing algorithms. Sensor nodes have much redundancy and data aggregation that becomes a productive procedure to eradicate the redundancy. It minimizes the number of transmissions and hence it saves power. The Packets that are generated by heterogeneous sensors or different submissions have different attributes. Packets from different submissions could not be aggregated. The data aggregation scheme uses static routing protocols that do not forward the packets dynamically according to network state or packet types. The spatial isolation initiated by static routing protocol is unfavorable to data aggregation .The concept of packet attribute, defined as the identifier of the data tried by different types of sensors or submissions suggest an Attribute-aware Data Aggregation (ADA) scheme consisting of a packet-driven timing algorithm with special Dynamic routing protocol and Potential-Based Dynamic Routing that is elaborated to support an ADA scheme which improves the efficiency of Data Aggregation.
Keywords |
| Wireless Sensor Network, ADA, Data Aggregation, Spatial Isolation, Dynamic Routing |
INTRODUCTION |
| WSN is a network of huge number of distributed sensor nodes. That sensor node is equipped with radio antennas in sensors nodes to sensing and transfer the data. Each node in the wireless sensor networks are used for gathering information needed by environments and are particularly useful in unattended situations [1], [2]. Analysis on wireless sensor networks a bit reason for diminish the lifetime of sensor networks are power Consumption, frequent radial of data to nodes, load traffic, overhead of message passing energy hole between the nodes and sink nodes[3]. The power for many operations like radial of data to sink node form every nodes or vice versa, data acquisition, data processing, load traffic, overhead of message passing. These are a bit reason for depressing the lifetime of wireless sensor networks [4]. |
| Attribute-aware Data Aggregation (ADA) scheme, which can make the collection of data with the same ascribe convergent as much as possible to advance the efficiency of data aggregation. ADA is to collect the packets and aggregate them before they come to the sink. So the energy can used efficient manner and aggregate the data properly. Attribute-aware data aggregation comprising of PBDR protocol and packet-driven timing control algorithm.The collection of the data is treated as ants, and then the rudimentary mechanism for finding routes. Dynamic routing protocol is anticipated to acclimatize to the common variation of packet ascribe circulation at each node. Potential-based routing is scalable and very simple to be applied since only localized data are needed and can be effortlessly got. To further improve the presentation of data aggregation scheme, the packets should furthermore be temporally convergent so as to rendezvous with each other at the identical node as well as at the same time.An ADA scheme is suggested to intentionally drive the packets with the identical attribute convergent as much as likely in the WSNs with heterogeneous sensors or various submissions. |
RELATED WORKS |
| A.A DYNAMIC TRAFFIC-AWARE ROUTINGALGORITHM |
| Routing means in the Internet have normally been founded on shortest-path for best effort traffic. This often determinates traffic jamming, particularly if bottleneck attachments on the shortest route harshly constraint the creative bandwidth between the source and the place visited [5]. Traditionally, jamming command in the Internet has been supplied by end-to-end means. A demonstration is the TCP jamming command mechanism that works by adjusting the dispatching rate at the source when it Routing means in the Internet have normally been founded on shortest-path for best effort traffic. This often determinates traffic jamming, particularly if bottleneck attachments on the shortest route harshly constraint the creative bandwidth between the source and the place visited [6]. |
| If multiple traffic creeks share the equal bottleneck attachment, each gets only a part of the bottleneck attachment bandwidth even though there may be bandwidth accessible along alternate paths in the network. Furthermore, lining up hold ups at the bottleneck attachment can add significantly to end-to end hold ups. Finally, varying traffic situation can make this lining up delay variable, thereby adding to jitter. |
| B. POWER EFFICIENT DATA GATHERING |
| In Wireless sensor networks various processor, memory and radio technology have enabled wireless sensor networks which are deployed to collect useful information from an area of interest [6]. The sensed data must be gathered and transmitted to a base station where it is further processed for end-user queries. Since the network consists of low-cost nodes with limited battery power, power efficient methods must be employed for data gathering and aggregation in order to achieve long network lifetimes [7]. In an environment where in a round of communication each of the sensor nodes has data to send to a base station, it is important to minimize the total energy consumed by the system in a round so that the system lifetime is maximized. With the use of data fusion and aggregation techniques, while minimizing the total energy per round, if power consumption per node can be balanced as well, a near optimal data gathering and routing scheme can be achieved in terms of network lifetime [8]. |
| So far, besides the conventional protocol of direct transmission, two elegant protocols called LEACH and PEGASIS have been proposed to maximize the lifetime of a sensor network[9]. There are two new algorithms under name PEDAP(Power Efficient Data gathering and Aggregation Protocol), which are near optimal minimum spanning tree based routing schemes, where one of them is the power-aware version of the other. Our simulation results show that our algorithms perform well both in systems where base station is far away from and where it is in the centre of the field [10]. PEDAP achieves between 4x to 20x improvement in network lifetime compared with LEACH, and about three times improvement compared with PEGASIS. |
| C. DISTRIBUTED MONITORING AND AGGREGATION |
| Self-monitoring the sensor statuses such as liveness,node density and residue energy is critical for maintainingthe normal operation of the sensor network [11], [12]. When buildingthe monitoring architecture, most existing work focuses onminimizing the number of monitoring nodes. However, withless monitoring points, the false alarm rate may increase as aconsequence.The fundamental tradeoffsbetween the number of monitoring nodes and the false alarm ratein the wireless sensor networks [13]. The distributed monitoring algorithms, to build up a poller-polleebased architecture with the objective to minimize the numberof overall power while bounding the false alarm rate. Basedon the established monitoring architecture, further explorethe hop-by-hop aggregation opportunity along the multihop pathfrom the polee to the power, with the objective to minimizethe monitoring overhead [14]. The optimal aggregationpath problem is NP-hard and suggest an opportunistic greedyalgorithm, which achieves an approximation ratio of 5/4.This is the first proved constant approximationratio applied to the aggregation path selection schemes over thewireless sensor networks[15]. |
| D. AGGREGATION TREE CONSTRUCTION IN SENSOR NETWORKS |
| Large-scale wireless sensor networks are expectedto play increasingly important role in future civilian and military settings [16]. Collaborative micro sensorscould be very effective in monitoring their operations [17]. However,low powerand in-network data processingmake data-centricrouting in wireless sensor networks a challenging problem [18].The heuristics to construct and maintainan aggregation tree in sensor networks. This aggregationtree can be used to facilitate data-centric routing. Themain idea is to turn off the radio of all leaf nodes to savepower, and thereby extending the network lifetime [19]. Therefore,in order to save the number of broadcasting messages,only the non-leaf nodes in the tree are in charge of dataaggregation and traffic relaying[20].An efficient energy-aware distributedheuristic to generate the aggregation tree and EADAT[21],[22],[23].EADAT algorithm makes no assumptionon local network topology, and is based on residualpower. It makes use of neighbouring broadcast schedulinganddistributed competition among neighbours [24]. These novel conceptsmake EADAT very efficient and effective. |
DESIGNING ADA |
| Aggregation techniques are used to decline the amount of data broadcast interior a WSN and therefore conserves electric battery power. As measurements are noted by all individual sensors, they need to be assembled and processed to make data of the entire WSN, such as mean and/or variance of the temperature or humidity inside a locality. One natural approach is for sensors to send their standards to certain exceptional nodes, i.e., aggregators. Each aggregator then condenses the data prior to dispatching it on. In periods of bandwidth and, aggregation, energy utilization is beneficial as long as the aggregation process is not too CPU-intensive. The aggregators can either be outstanding (more powerful) nodes or usual sensors nodes. To assume that all nodes are potential aggregators and that data gets aggregated as they propagate to the go under. In this setting, sensors have very restricted capabilities and aggregation should be easy and not engage any expensive or convoluted computations. It would need only a couple of easy arithmetic procedures, such as supplements or multiplications. |
| System design is the process of defining the architecture, components, modules, and data for a system to satisfy specified requirements. One could see it as the application of systems theory to product development. There is some overlap with the disciplines of systems analysis, systems architecture and systems engineering. If the broader topic of product development blends the perspective of marketing, design, and manufacturing into a single approach to product development, then design is the act of taking the marketing information and creating the design of the product to be manufactured. System design is therefore the process of defining and developing systems to satisfy specified requirements of the user. Wireless sensor network is implemented by using two points of different orders so that the effect of one point can be removed by multiplying the aggregated cipher text with the order of the point, and then the scalar of the other point can be obtained. Based on the same logic of new knowledge is designed by using multiple points, each of which has different order that can obtain one scalar of the specific point through removing the effects of remaining points (i.e., multiplying the aggregated cipher text with the product of the orders of the remaining points). The security of ADA and Time Driven Knowledge are based on the hardness assumption of subgroup decision problem, whereas ADA requires more precise secure analysis for parameter selections. |
 |
| Depth:The depth of a node is the number of hops that it isaway from the sink (2). Neighbor: The neighbor of node i is all nodes in the radio Coverage disk of node i except for i itself. Attribute: The attribute of data packet is its identification. The heterogeneous sensors and nodes involved in differentapplications may generate data packets with differentattributes. The identical sensors on the nodes involved inthe same applications will generate the packets with identicalattribute.Use different natural numbers to identifydifferent attributes, and extend the packet header to carrythis value. |
| A.PBDR |
| Before beginning to recount the solid routing algorithm,first show how it works. Intuitively, the deepness potentialfield in the PBDR can be examined as a basin. The go under residesat the bottom, and all packets in most of existing tree-baseddata aggregation designs flow down along the exteriordirectly just like water does without combining with eachother. However, the packets with correlated datashould be accumulated simultaneously for more efficient dataaggregation. To realize this aim, the pheromone promisearea is assembled. Packets with different attribute departdifferent odor at every node that it passed, and the odor willvolatilize with the time. |
| Each package is transmitted to theclose by in response to the allowance of the identical odor as thatof itself, so that the packets with the same describe canappeal each other and gather simultaneously in space. Intuitively,the pheromone promise field types the valleys in the exterior of the basin. The stronger is the odor, the deeperis the valley. Each package is conveyed to the deepestvalley with the same odor as that of itself, rather than bedispatched along a fixed route such as the shortest tree. In this way,the packets with the identical ascribe can intentionally pursuethe identical path and converge as much as possible. |
| The PBDR protocol will be presented, followed with some analysis of key parameters, then a Packet-driven timing scheme which cooperates with the dynamic routing will be developed. For a legible description, first introduce some definitions the heterogeneous sensors and nodes involved in different applications may generate data packets with different attributes. The identical sensors on the nodes involved in the same applications will generate the packets with identical attribute. Use different natural numbers to identify different attributes, and extend the packet header to carry this value. The pheromone potential field is constructed. Packets with different attribute leave different odor at every node that it passed, and the odor will volatilize with the time. Each packet is transmitted to the neighbor in response to the amount of the same odor as that of itself in equation (1), so that the packets with the same attribute can attract each other and gather together in space. Intuitively, the pheromone potential field forms the valleys in the surface of the bowl. |
| This protocol identifies the dynamic routing path using ant colony optimization path selection algorithm. Neighbor Node Different Calculation: |
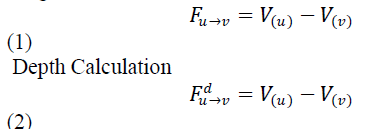 |
| In PBDR Ant Colony Optimization algorithm is used. Ant Colony Optimization |
| Description: |
| The objective of the strategy is to exploit historic and heuristic information to construct candidate solutions and fold the information learned from constructing solutions into the history. Solutions are constructed one discrete piece at a time in a probabilistic step-wise manner. The probability of selecting a component is determined by the heuristic contribution of the component to the overall cost of the solution and the quality of solutions from which the component has historically known to have been included. |
| B.Packet Driven Timing Algorithm: |
| This is introducing the avoidable delay and degrades the performance.An adaptive packet-driven timing control algorithm is proposed to provide more chances for data aggregation on nodes. |
| Waiting Time Calculation: |
| Time Driven Scheme Calculation: |
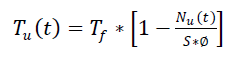 |
DATA AGGREGATION AND SELECTION OF PATH |
| A. NETWORK EVALUATION |
| To construct the all node for wireless setup and also SN collect information from deployed environments and forward the information back to base station (BS) via multihop transmission based on a tree or a cluster topology. The accumulated transmission carries large energy cost for intermediate nodes. Wireless sensor network is implemented by using two points of different orders so that the effect of one point can be removed by multiplying the aggregated cipher text with the order of the point, and then the scalar of the other point can be obtained. Based on the same logic of new knowledge is designed by using multiple points, each of which has different order. Obtain one scalar of the specific point through removing the effects of remaining points (i.e., multiplying the aggregated cipher text with the product of the orders of the remaining points). The security of ADA and Time Driven Knowledge are based on the hardness assumption of subgroup decision problem, whereas ADA requires more precise secure analysis for parameter selections. |
| B. DATA AGGREGATION |
| The PBDR protocol will be presented, followed with some analysis of key parameters, then a Packet-driven timing scheme which cooperates with the dynamic routing will be developed. For a legible description, first introduce some definitions the heterogeneous sensors and nodes involved in different applications may generate data packets with different attributes. The identical sensors on the nodes involved in the same applications will generate the packets with identical attribute. Use different natural numbers to identify different attributes, and extend the packet header to carry this value. The pheromone potential field is constructed. Packets with different attribute leave different odor at every node that it passed, and the odor will volatilize with the time. Each packet is transmitted to the neighbor in response to the amount of the same odor as that of itself, so that the packets with the same attribute can attract each other and gather together in space. Intuitively, the pheromone potential field forms the valleys in the surface of the bowl. |
| The more intense is the odor, the deeper is the valley. Each packet is transmitted to the deepest valley with the same odor as that of itself, rather than be sent along a fixed path such as the shortest tree. In this way, the packets with the same attribute can intentionally follow the same path and converge as much as possible. |
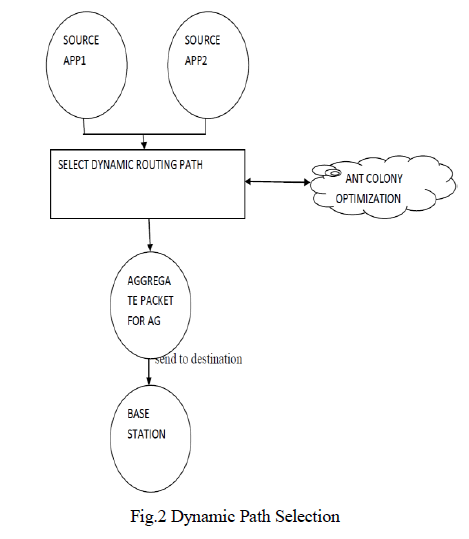
| C.DYNAMIC PATH SELECTION |
| The dynamic routing would be constructed according to the network state and the data features as shown in Fig. 2, for example, node 1 sends packets to node 3 instead of node 2, the packets from App1 could gathered together as much as possible, and thus the aggregation efficiency would be improved drastically. Comparing with the static routing, the dynamic routing intentionally drive the packets from the same application converge spatially during their transmission procedure, the dynamic routing protocol is the cornerstone of ADA suitable for heterogeneous data or various application in the same WSN. |
| In nature, ants leave pheromone, which can emanate an odor and evaporate with time, along the paths that they have passed. The afterward ants will select their paths according to the amount of pheromone on different paths. If the packets in WSNs are treated as the ants in nature by analogy, and then the attribute-dependant pheromone is left on the nodes through which packets with different attribute pass. Subsequently, the node with different pheromone will emanate different odor. |
| The packets just follow the odor to meet with other packets with the same attribute. In this way, the packets can be gathered together by intentional forwarding, which will assist in achieving the goal of our ADA scheme. Applying the principle that ants select the paths to find food based on pheromone, the routing protocols the ant routing protocol needs to inject extra packets (i.e., forward “ants” and backward “ants”) into networks to update routing tables and distribute state information of network; moreover, the convergence of routing depends on the number of “ants.” The excessive overhead is unaffordable for WSNs with limited energy. Therefore, in this work, only use the concept of pheromone in ant colony to identify data attribute from different applications or heterogenous sensors, and borrow another concept in physics (i.e., potential field) to construct the dynamic routing for the ADA scheme. |
 |
| D.DATA ACCESSING |
| There are two different applications. The packets are randomly generated with average interval with minutes. All applications start at 100 s and end at 130 s. The distribution of packets in space is centralized in ADA so that the normalized queue length is smaller than those in other schemes. This phenomena occurring in the queue indicate that ADA does more efficient aggregation than CT, DDS, and WCDS since ADA always attracts the packets with the same attribute together, the limited buffer on nodes only caches the packets from one applications, which can be inferred from the following fact, namely, in ADA, the packets with the same attribute are transmitted to the sink along relatively constant paths, while in CT, DDS, and WCDS, the distribution of packets in space are decentralized. Both sharing buffer and decentralized paths are not beneficial for data aggregation. |
PERFORMANCE EVALUATION |
| In this section, perform sequence of replication experimentsto evaluate the presentation of the ADA design andcontrast it with some usual data aggregation schemes |
| A. PERFORMANCE METRICS |
| To make a performance evaluation, twospecial metrics are introduced except for common performance metrics,such as delay and dropping ratio. |
| Average number of transmission per received packet (ANTRP) is defined as the ratio of the total number of transmissions to the total number of packets received by the sink. Without data aggregation, every packet generated at the node whose depth is d can reach the sink after at least d transmissions. An efficient data aggregation mechanism will reduce transmissions by aggregating packets at intermediate nodes. Thus, ANTRP is a proper metric to evaluate the efficiency of data aggregation schemes. |
| Aggregation ratio (AR) is characterize as the ratio of the total number of packets obtained by the sink to the distinction between the total number of packets developed by applications and the number of fallen packets. If there are only packets with the same attributes and most packets are aggregated beside events and then forwarded to the go under, the sink will receive a few packets. Conversely, the detail that more packets are obtained at the go under indicates that fewer aggregation procedures are presented in networks. |
| B.NODE DENSITY |
| Generally, the density of nodes in WSNs is initially muchdense, step-by-step decline as some nodes pass away due to energyexhaustion or other components. An efficient data aggregationdesign should present well as long as the WSN isattached and no issue the node density is high or reduced.To assess the performance of ADA with different nodedensity, nodes are established in a 100 m * 100 m rectanglewhere the sink finds at (90 m, 50 m). The number ofsensors changes from 100 to 450. In this way, the meannumber of friends of a node rises, i.e., the nodedensity rises. Three distinct submissions occurs in aaround and the packets are randomly developed with meaninterval 10 ms. All three submissions start at 110 s and endat 120 s. The ANTRP with different node density in differentschemes is shown in Fig.3.All thecurves decline as the number of nodes increases. It isreasonable since the average number of neighbors of a nodeincreases as nodes become denser, which is helpful toimprove spatial convergence degree and then reduceANTRP. |
| SPT performs the worst since it does nothing tomake packets spatially convergent and temporally convergent.ADA outperforms the otherschemes at any node density. |
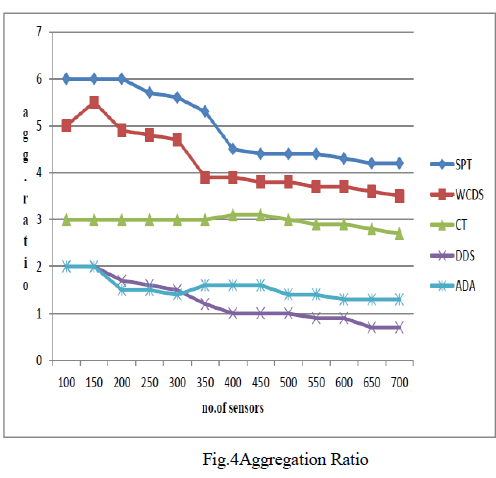
| Fig.4 illustrates the AR of different schemes in thesamescenario. As the node density increases, all schemesperform better, and both ADA and DDS are prominent. Itseems that ADA obtains more gains in Fig.4 than that in Fig.3. The reason is that ADA indeed improves spatial andtemporall convergence remarkably and thus the number ofthe packets received by the sink is rather small. |
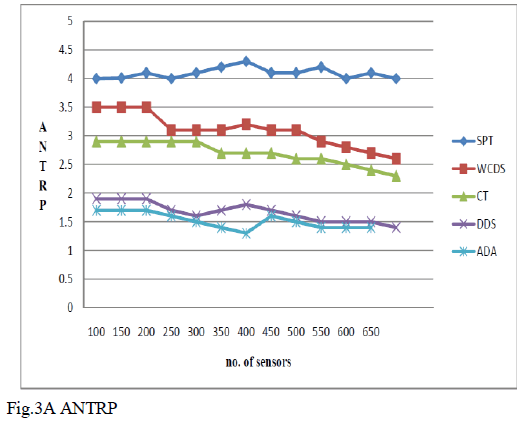 |
| However,with respect to the average number of transmissions perreceived packet as shown in Fig.3, the packets sometimeswill be forwarded to the next hop with the same depth oreven with a deeper depth to improve spatial convergencedegree. Although this detour transmission increases thenumber of transmissions, it is indeed beneficial for dataaggregation. Hence, the advantage of ADA in Fig.4 ismore obvious than that in Fig.3. |
 |
| C.SCALABILITY |
| The scale of WSNs could be very large. For example, a WSNcould be deployed on an island for biological investigationor in the forest to detect fire. The scalability of protocols inWSN is very important, at least, the performance shouldgracefully degrade as the network size increases. Toevaluate the scalability of our ADA, enlarge the WSN into a 1000 m * 1000 m rectangular area with 1,000 sensorsand the radio range becomes 50 m. The sink locates at(950 m, 500 m). Only one application happens in a circlewith radius of 40 m and the center of the circle is x; ywhere y = 500 m and x = (150 + 100 *i) m(i = 1, 2,. . . ; 7),namely the different distances between the event and thesink denote WSNs with different scale. The packets arerandomly generated with average interval of 100 ms. |
ACKNOWLEDGMENT |
| I would like to thank Ms.B.Vijayalakshmi and S.Revathifor helpful discussions about this work. |
CONCLUSION |
| The data aggregation is a productive means to save limited energy in WSNs. Heterogeneous sensors and diverse submissions expected run in the identical mesh. To handle this heterogeneity, in this task, insert the notion of packet attribute to identify different packets developed by heterogeneous sensors and different submissions, and then propose an attribute-ware data aggregation scheme consisting of PBDR protocol and packet-driven timing control algorithm. Packets are treated as ants, and then the basic mechanism for finding routes based on phenomenon in ant colony is borrowed to attract the packets with the identical attribute to gather together. Enlightened by the notion of promise in physics, a PBDR protocol is developed. Blending with the adaptive timing control algorithm, the attribute-ware data aggregation scheme can make the packets with the same attribute spatially convergent as much as likely, and thus improve the effectiveness of data aggregation. The replication trials validate the effectiveness of our ADA design and illustrate that it also has some properties needed by genuine submissions in WSNs, such as scalable with respect to mesh dimensions and suitable for following wireless events, and so on. In addition, the theoretical investigation provides some guidelines on parameter settings. |
References |
|