ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
R.Kausalya1 and S.Pandiarajan2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
In forensics latent fingerprint identification is critical importance to identifying suspects: latent fingerprints are invisible fingerprint impressions left by fingers on surfaces of objects. The proposed algorithm uses a robust alignment algorithm (mixture contour and Orientation based Descriptor) to align fingerprints and to get the similarity score between fingerprints by considering minutiae points and ridge orientation field information.The texture-based descriptors (local binary patterns and local phase quantization), address important issues related to the dissimilarity representation, such as the impact of the number of references used for verification and identification. However, the overlapped region shape similarity retrieved from minutiae spatial distribution information provides additional important criteria. After finding the overlapping region of a possible affine transform, we can measure to find the shape dissimilarity via the application of the shape context to all interior points.TheHybrid matching algorithm, is to prune outlier minutiae pairs, and secondly to provide more information to use in similarity evaluation.
Keywords |
| Orientation and texture descriptors, latent‘s, affine transform, contour context, matching. |
INTRODUCTION |
| Recent research and development efforts on latent fingerprints can be classified into three streams according to the manual input required from fingerprint examiners: consistent with existing practice, increasing manual input, or reducing manual input. Because of large variations in latent fingerprint quality and specific requirements of practical applications (crime scenes, border crossing points, battle fields), each of the three streams has its value. Nowadays, automated fingerprint identification system (AFIS) has become an indispensable tool for law enforcement agencies. Truly latent (âÃâ¬Ãâ¢hiddenâÃâ¬Ãâ) prints are not visible to the naked eye, and substantially consist of only the natural secretions of human skin. Such prints require treatment to cause them to become visible. This treatment is called âÃâ¬Ãâ¢latent print development.âÃâ¬ÃâLifting oflatents may involve a complicated process, and it can range from simply photographing the print to more complex dusting or chemical processing [1]-[3].Rolled prints contain the largest amount of information about the ridge structure on a fingerprint since they capture the largest finger surface area; latents usually contain the least amount of information for matching or identification because of their size and inherent noise. Compared to rolled or plain fingerprints, latents are smudgy and blurred, capture only a small finger area, and have large nonlinear distortion due to pressure variations. Due to their poor quality and small area, latents have a significantly smaller number of minutiae compared to rolled or plain prints (the average number of minutiae in NIST Special Database 27 (NIST SD27) [3], [4] images is 21 for latents versus 106 for their mated rolled prints). These characteristics make the latent fingerprint matching problem very challenging. |
RELATED WORK |
| A. Security Issues of Partial Fingerprint Matching |
| In general, fingerprint recognition systems are considered as being of high security strength. Since a fingerprint data is in the order of several kilobytes, it provides the security of having a long password without the overhead of remembering that information. However, unlike a password system, in which an exact match is expected for authentication of an individual, a fingerprint recognition system can only provide the individual‘s identity information with a certain confidence level. Thus, some kind of distortion tolerant mechanism is required which can reduce the security strength of the system. Moreover, with the small number of features on a partial fingerprint, the security strength of partial fingerprint recognition is further diminished. Before we replace the password and PIN authentication systems with fingerprint recognition, we must answer the question âÃâ¬Ãâ¢how secure is the fingerprint based system compared to the password or PIN based systems?âÃâ¬Ãâ Besides, the relation between the acquired fingerprint size and its security strength plays a key role in the designing of a fingerprint recognition system. This relation between the two must be further studied before we can expect wider acceptance of fingerprint authentication systems. |
| B. Fingerprint Image Enhancement |
| Fingerprint image quality is an important factor in the performance of minutiae extraction and matching algorithms. A good quality fingerprint image has high contrast between ridges and valleys. A poor quality fingerprint image is low in contrast, noisy, broken, or smudgy, causing spurious and missing minutiae. Poor quality can be due to cuts, creases, or bruises on the surface of finger tip, excessively wet or dry skin condition, uncooperative attitude of subjects, damaged and unclean scanner devices, low quality fingers (elderly people, manual worker), and other factors. The goal of an enhancement algorithm is to improve the clarity (contrast) of the ridge structures in a fingerprint. General-purpose image enhancement techniques are not very useful due to the non-stationary nature of a fingerprint image. However, techniques such as gray-level smoothing, contrast stretching, histogram equalization, and Wiener filtering can be used as pre-processing steps before a sophisticated fingerprint enhancement algorithm is applied. |
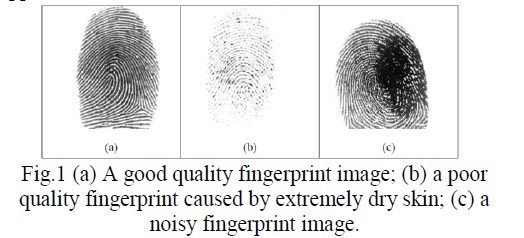 |
| Techniques that use single filter convolutions on the entire image are not suitable. Usually, a fingerprint image is divided into sub regions and then a filter whose parameters are pre-tuned according to the region‘s characteristics is applied. |
RESEARCH CONTRIBUTION |
| LATENT FINGERPRINTMATCHING APPROACH |
| A. Feature Extraction |
| The most common features in latent fingerprint are minutiae points essentially terminations and bifurcations of the ridge lines that constitute a fingerprint pattern. The overall feature extraction algorithm is divided into, (i)Preprocessing and segmentation, (ii)Thinning and feature extraction and (iii)Minutiae Extraction. The preprocessing is used to obtain the ridge segmented binary fingerprint image from the original gray scale fingerprint image. The following steps are involved in preprocessing, (a)Foreground and background segmentation, (b)Ridge segmentation and (c) Directional Smoothing of ridges. The Thinning and Feature Extraction technique, the binary image is thinned to have one pixel fingerprint image using skeletonization, which results in to spurious minutiae. The skeleton needs to be smoothed before minutiae point to be located.The two main methods of minutiae feature extraction either require the gray-scale image to be converted to a binary image, or work directly on a raw or enhanced gray-scale image. The binary image based method; the binarization of the gray-scale image is the initial step. This requires each gray-scale pixel intensity value to be transformed to a binary intensity of black (0) or white (1). The simplest approach is to apply a global threshold where each pixel is mapped according to |
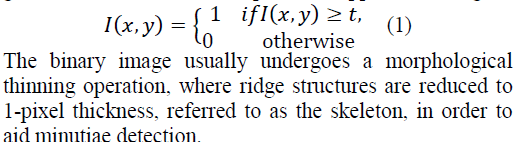 |
| B.Affine Transform |
| An affine transformation or affine map or an affinity is a function between affine spaces which preserves points, straight lines and planes. Also, sets of parallel lines remain parallel after an affine transformation. An affine transformation does not necessarily preserve angles between lines or distances between points, though it does preserve ratios of distances between points lying on a straight line.The normal image minutiae set cannot proceed to find minutiae pairs from triplets without some pre-processing for the following critical reasons: |
| • Fingerprint impressions can differ in orientation, considering the direction field in the triplet useless, |
| • Fingerprint impressions can differ in offset, considering the x-y fields in the triplet useless, and |
| • Skin elasticity creates non-linear distortion or âÃâ¬Ãâwarping‘ to occur when different directional pressure is applied causing triplet x-y variations to occur. |
| To address the issues concerning the lack of invariance of the triplet structure, registration is required. The registration concerns the alignment and overlay of the template and test fingerprints so that corresponding regions of the fingerprints have minimal geometric distance to each other. Registration can be achieved geometrically by applying (to either the test or template fingerprint minutiae set) a heuristically guided affine transform, where minutiae triplet field values are updated with, |
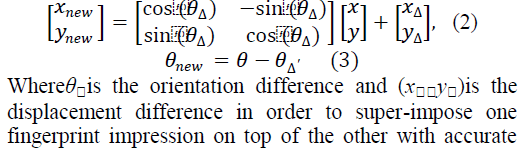 |
| overlap and uniform direction.The global registration process notably reduces the search space. This reduces algorithm complexity for finding minutiae pairs, since matching pairs are formed in smaller local neighbourhoods (i.e. constraints added for minutiae mappings). |
| C. Mixture Contour and Orientation Based Descriptor |
| The mixture based matching algorithms that use contour based descriptors based on point samples (or point pattern matching algorithms) are analogous to minutiae-based fingerprint matching algorithms, as they usually combine the use of descriptors with dynamic programming, greedy, simulated annealing, and energy minimization based algorithms, in order to register shapes and compute a similarity measure. The texture based descriptor is a robust contour based shape descriptor used for calculating shape similarity and the recovering of point correspondences.The mixture contour representationthat flexibly encodes junction information and curvature. The representation discretizes contour orientation at an interest point and records contour intensity at each angle as feature elements.Contour shape techniques only exploit shape boundary information. There are generally two types of very different approaches for contour shape modelling: continuous approach (global) and discrete approach (structural). Continuous approaches do not divide shape into subparts; usually a feature vector derived from the integral boundary is usedto describe the shape.The orientation based descriptor context are distributed as histograms, we can use a modification of the X2 statistic: |
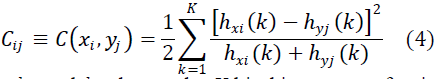 |
| wherehxi and hyj denote the K-bin histograms of points xi and yj, respectively. This cost canbe modified to include application specific weighting and additional costs, in order to addextra relevant information, and hence, improve accuracy. |
| D.Hybrid Matching Process |
| The proposed hybrid matching algorithm based on a modified version of the enhanced shape context method along with the integration of the orientation-based descriptor illustrating asignificant performance improvement over the enhanced shape context method. The main objective of the integration is two-fold, firstly to prune outlier minutiae pairs, and secondly to provide more information to use in similarity assessment.The minutiae pairs have been established, pruning is performed to remove unnatural pairings. However, if we closely analyze the orientation-based descriptor used for pruning, we can see that a fundamental flaw arises with partial fingerprint coverage, specifically for minutiae pairs near fingerprint image edges.A proposed modification to the contour context and orientation-based descriptor is applied so that the amount of common region coverage that each descriptor has is reflected in the similarity score. This is achieved by a simple Gaussian weighting of equation, |
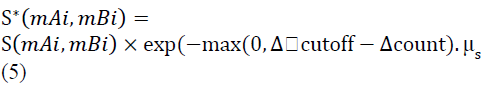 |
| The cut-off point where all good sample totals below this value are weighed count is the total number of good samples (i.e. where a good sample is defined to be in a coherent partial fingerprint region), and is a tunable parameter. However, for a more exhaustive approach, one could empirically review the estimated distribution of orientation-based similarity scores for true and false cases, with specific attention towards the effect of coverage completeness on the accuracy of the similarity measure. |
EXPERIMENTAL RESULTS |
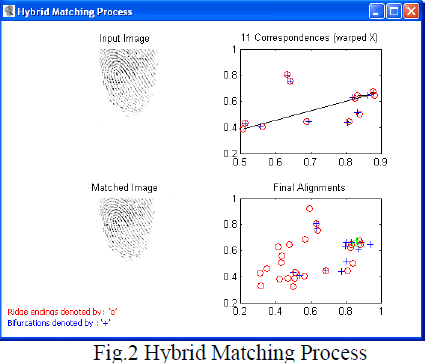
| The latent fingerprint images from the FVC2002 DB1 to DB4 (388 x 374 pixel) database, were used for our simulation.The experimental results presented in this paper suggested that our proposed framework consistently performs well for different security environments, while ensuring the security of biometric system. Fig.2 shows implementation result of Hybrid matching process which gives better matching performance. |
 |
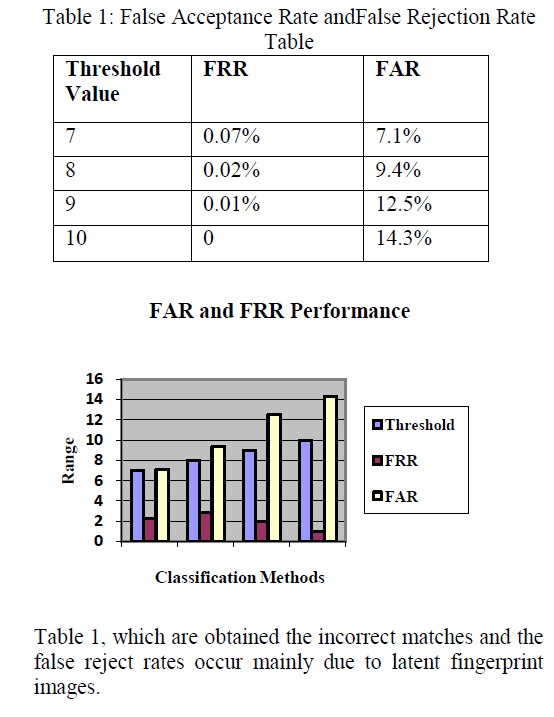
| The number of imposter points is very low; the False Acceptance rate (FAR) ishigh with the high degree of polynomial. According to this, higher the FAR, Genuine Acceptance rate (GAR) is also high but False Rejection rate is low. If this is not happened, FRR is high, and then system will not be valid one. |
 |
 |
CONCLUSION |
| In this paper, the idea of latent fingerprint matching method using a texture based shape and orientation descriptor outperforms many well-known methods on the FVC2002 database competition, considering that the feature set was not in pristine condition due to the chosen extraction and filtering methods, highlighting theoverall robustness of the proposed algorithm. A fingerprint Hybrid matching algorithm designed for matching latents to rolled/plain fingerprints which is based on a descriptorbased Affine Transform alignment. A comparison between the alignment performance of the proposed algorithm and the well-known Generalized Affine Transform shows the superior performance of the proposed method. |
References |
|