ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
1 Kalaiyarasi.R, 2Rajeswari.S
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Beacon and data transmission is based on the location information of each and every node which is connected in the geographic routing network. The beacon packets are transmitted to requested node by the neighbor node, using APU (Adaptive Position Update) scheme.APU scheme incorporates two rules are On- Demand Learning (ODL) and Mobility Prediction (MP) rule.APU dynamically adjust the beacon update interval based on the movement of the node. ODL rule is used to reduce the updating cost and also to improve the performance of the network.ODL creates the topology for the active nodes. But MP rule is not able to handle the link failure while transferring the data. Extended Adaptive Position Update (EAPU) scheme has been proposed to overcome that drawback. It has two ways to overcome the link failure, inaccuracy of the topology and performance degradation. The two ways are 1) Request for new neighbor node’s neighbor list.2) Verification of acknowledgement, Transmission and path.
INTRODUCTION |
| Mobile Ad hoc network is an infrastructure-less network in which nodes are mobile i.e., movable devices. In other words, MANET is a list of mobile devices such as laptop, smart phones, tablet etc...The word ad hoc gives the meaning, “for this purpose only” and thus gives “temporary” in Latin. The term has been applied to future office or home networks in which new devices can be quickly added, using, for example, the proposed Bluetooth technology in which devices communicate with the computer and perhaps other devices using wireless transmission. One vendor offers an ad-hoc network technology that allows people to come to a conference room and, using infrared transmission or radio frequency (RF) wireless signals, join their notebook computers with other conferences to a local network with shared data and printing resources. Each user has a unique network address that is immediately recognized as part of the network. The technology would also include remote users and hybrid wireless/wired connections. A mobile ad-hoc network is a kind of wireless ad-hoc network, and is a self-configuring network of mobile routers connected by wireless links – theunion of which forms an arbitrary topology. The routers are free to move randomly and organize themselves arbitrarily. Thus the network's wireless topology may change rapidly and unpredictably. Such a network may operate in a standalone fashion, or may be connected to the larger Internet. Mobile ad-hoc networks became a popular subject for research as laptops and 802.11/Wi-Fi wireless networking became widespread in the mid- to late 1990s. Many of the academic researches evaluate protocols and abilities assuming varying degrees of mobility within a bounded space, usually with all nodes within a few hops of each other, and usually with nodes sending data at a constant rate. Different protocols are then evaluated based on the packet drop rate, the overhead introduced by the routing protocol and other measures.The Children's Machine One Laptop per Child program hopes to develop a cheap laptop for mass distribution to developing countries for education. The laptops will use ad-hoc wireless mesh networking to develop their own communications network out of the box. |
| Thegeographic routing protocols requires position of the final destination of the packet and the position of a node’s neighbors. The final destination can be obtained by querying a location service such as the Grid Location System (GLS) [9]. To obtain the neighbor node’s position, each node exchanges its own location information by using GPS or the localization schemes discussed in [1]. This allowseach node to build a local map of the nodes within its vicinity, often referred to as the local topology. So that each node broadcasts its updated location information to all of its neighbors. These location update packets are usually referred to as beacons. In most geographic routing protocols, beacons are broadcast periodically for maintaining an accurate neighbor list at each node. Position updates are costly in many ways. Each update consumes node energy, wireless bandwidth, and increases the risk of packet collision at the medium access control layer. Packet collisions cause packet loss which in turn affects the routing performance due to decreased accuracy in determining the correct local topology (a lost beacon broadcast is not retransmitted). A lost data packet does get retransmitted, but at the expense of increased end-to-end delay. Adaptive Position Update (APU) gives only less or similar amount of beacon overhead when compared with periodic broadcasting. So APU is comparatively wasteful in point of link failure. |
| In this paper, Extended Adaptive Position Update (EAPU) is introduced in order to handle the impact of link failure. This is done by referring the neighbor nodes neighbor list. EAPU incorporates two rules: Mobility Prediction (MP) and On-Demand Learning (ODL) rule.Mobility Prediction (MP) uses a simple mobility prediction scheme to estimate when the location information broadcast in the previous beacon becomes inaccurate. The next beacon is broadcast only if the predicted error in the location estimate is greater than a certain threshold, thus tuning the update frequency to the dynamism inherent in the node’s motion. The second rule, referred as On-Demand Learning (ODL), aims at improving the accuracy of the topology along the routing paths between the communicating nodes. ODL uses an on-demand learning strategy, whereby a node broadcasts beacons when it overhears the transmission of a data packet from a new neighbor in its vicinity. This ensures that nodes involved in forwarding data packets maintain a more up-to-date view of the local topology. On the contrary, nodes that are not in the vicinity of the forwarding path are unaffected by this rule and do not broadcast beacons very frequently. After receiving the beacon packets, need to find the optimal route by using GPSR (Greedy Perimeter Stateless Routing Protocol).Trustworthy logical connection must be established by using TCP along with GPSR protocol after choosing the optimal path from source to destination. This approach is simulated using JiST (Java in Simulation Times) tool which is mainly focused to simulate using java for integrated TCP with GPSR protocol. Thus the geographic routing protocol has been enhanced. |
RELATED WORK |
| The packet forwarding is based on the locations of the node’sone-hop neighbors and location of the packet destination as well. A forwarding nodes therefore needs to maintain these two types of locations. 1) Location of destination and 2) one-hop neighbors’ location. In the periodic beaconing scheme, each node broadcasts a beacon with a fixed beacon interval. If a node does not hear any beacon from a neighbor for a certain time interval, called neighbor time-out interval, the node considers thisneighbor has moved out of the radio range and removes the outdated neighbor from its neighbor list. The neighbor time-out interval often is multiple times of the beacon interval. |
| In the distance-based beaconing, a node transmits a beacon when it has moved a given distance d. The node removes an outdated neighbor if the node does not hear any beacons from the neighbor while the node has moved more than k-times the distance d, or after a maximum time out of 5 s. This approach therefore is adaptive to the node mobility. First, a slow node may have many outdated neighbors in its neighbor list since the neighbor time-out interval at the slow node is longer. Second, when a fast moved node passes by a slow node, the fast node may not detect the slow node due the infrequent beaconing of the slow node, which reduces the perceived network connectivity. In reactive beaconing, the beacon generation is triggered by data packet transmissions. When a node has a packet to transmit, the node first broadcasts a beacon request packet. The neighbors overhearing the request packet respond with beacons. Thus, the node can build an accurate local topology before the data transmission. However, this process is initiated prior to each data transmission, which can lead to excessive beacon broadcasts, particularly when the traffic load in the network is high. In Adaptive Position Update (APU) beaconing,dynamically adjusts the beacon update intervals based on the mobility dynamics of the nodes and the forwarding patterns in the network. But it is failed to overcome the impact of the link failure due to some snags inthe network. The Extended Adaptive Position Update (EAPU) strategy proposed dynamically adjust the beacon update without the impact of link failure.. The beacons transmitted by the nodes contain their current position and speed. Nodes estimate their positions periodically by employing linear kinematic equation. If the predicted location is different from the actual location, a new beacon is broadcast to inform the neighbors about changes in the node’s mobility characteristics.The neighbor that has the smallest timer will expire first and relay the packet. By overhearing the relayed packet, other neighbors can cancel their own timers and ensure that no Duplicate packet is transmitted,hence, the beaconless routing protocols can avoid excessive position update. |
EXTENDED ADAPTIVE POSITION UPDATE (EAPU) |
| Each node broadcasts a beacon informing its neighbors about its presence and its current location and velocity upon initialization. Following this, in most geographic routing protocols such as GPSR, each node periodically broadcasts its current location information. The position information received from neighboring beacons is stored at each node. Based on the position updates rece2/21/2014ived from its neighbors, each node continuously updates its local topology, which is represented as a neighbor list. Only thosenodes from the neighbor list are considered as possible candidates for data forwarding. Instead of APU, EAPU adapts the beacon update intervals to the mobility dynamics of the nodes and the amount of data being forwarded in the neighborhood of the nodes with less beacon overhead.The assumptions made in our work: |
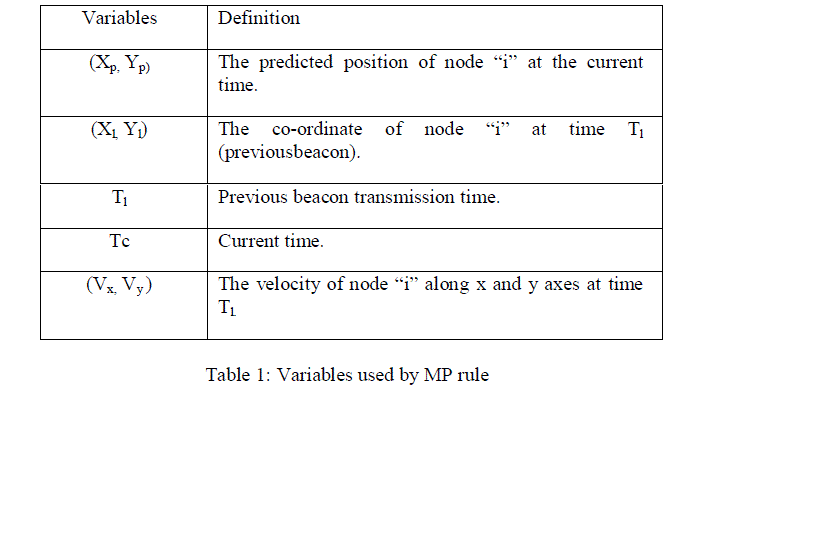
| (1)Network should be able to handle the impact of link failure |
| (2) All nodes are aware of their own position andvelocity, |
| (3) All links are bi-directional, |
| A. Mobility Prediction (MP) Rule |
| Nodes that frequently change their motion need to frequently update their neighbors, since their locations are changing dynamically. The goal of the MP rule is to send the next beacon update from node i when the error between the predicted location in the neighbors of i and node i’s actual location is greater than an acceptable threshold. The predicted location of node “i” can be calculated by using the following formula. |
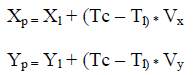 |
| Here (Xl,Yl) and (Vx,Vy) refers to the location and velocity information that was broadcast inthe previous beacon from node i. |
| Node i uses the same prediction scheme to keep track of its predicted location among its neighbors. Let (Xa, Ya), denote the actual location of node i, obtained via GPS or other localization techniques. |
 |
 |
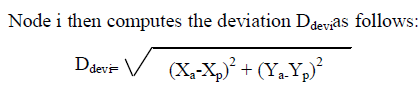 |
| If the deviation is greater than a certain threshold, known as the Acceptable Error Range (AER), it acts asa trigger for node i to broadcast its current location and velocity as a new beacon. |
| B. On-Demand Learning (ODL) rule |
| Since MP rule is failed to handle the link failure, we introduced a new proactive rule called On-Demand Learning. As the name suggests, a nodebroadcasts beacons on-demand, i.e., in response to dataforwarding activities that occur in the vicinity of that node. According to this rule, whenever a node overhears a data transmission from a new neighbor, it broadcasts a beacon as a response. By a new neighbor, we imply a neighbor who is not contained in the neighbor list of this node. In reality, a node waits for a small random time interval before responding with the beacon to prevent collisions with other beacons. |
ROUTE DISCOVERY |
| After getting the beacon information from the neighbor node, the source node should find the forwarding path by sending the packet through forwarding node with low less loaded node. This can be achieved by using GPSR (Greedy Perimeter Stateless Routing) Protocol along with TCP protocol. The next section will give the brief description of the roles of GPSR protocol and TCP protocol. Unlike the existing, it establish the trustworthy logical connection and also periodic verification of destination location. |
| A. Greedy Perimeter Stateless Routing Protocol |
| Greedy Perimeter Stateless Routing, GPSR, is a responsive and efficient routing protocol for mobile, wireless networks. Unlike established routing algorithms before it, which use graph-theoretic notions of shortest paths and transitive reachable to find routes, GPSR exploits the correspondence between geographic position and connectivity in a wireless network, by using the positions of nodes to make packet forwarding decisions. GPSR uses greedy forwarding to forward packets to nodes that are always progressively closer to the destination. In regions of the network where such a greedy path does not exist (i.e., the only path requires that one move temporarily farther away from the destination), GPSR recovers by forwarding in perimeter mode, in which a packet traverses successively closer faces of a planar sub graph of the full radio network connectivity graph, until reaching a node closer to the destination, where greedy forwarding resumes. |
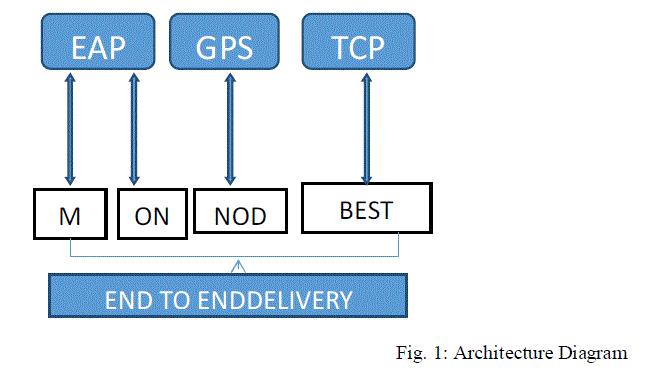 |
| EAPUfirst focus on the transmission of the beacon packets effectively by using two rules MP and ODL rule. Then the GPSR protocol starts to find the route based on the location sent by the beacon packets. Instead of UDP protocol, TCP is used to transport the data packets as wells as beacon packets for the trust worthy logical connection. Load at the time of transmission of data packets in the forwarding node get reduced since TCP protocol is an End-to- End Packet delivery. Thus the system is enhanced with the benefits of EAPU along with TCP for routing purpose. In this paper, GPSR is also called as load balanced protocol because it not only consider the movement of the nodes, but also analyze the packet queue of neighbor node while selecting the best route to forward data.A community of adhocnetwork researchers has proposed, implemented, and measureda variety of routing algorithms for such networks. |
DYNAMIC LOCATION UPDATE AND LOAD BALANCING MECHANISM |
| Geographic routing and data transmission operations are managed with dynamic position update mechanism. TCP and UDP data transmission operations are supported in the system. Data traffic is managed with link failure and node mobility factors. The system is divided into five major modules. They are location management, route discovery process, position update process, node status management and load balancing process. Nodes initial location and neighbor details are managed in the location management process. Path identification is carried out under the route discovery process. Position update process is designed to maintain the current location of the nodes. Node mobility and link failures are handled under the node status management process. Load balancing process is performed in the data transmission process. |
| A. Location Management |
| Beacon messages are constructed with location details for the node. Geographic location for each node is identified and update in the beacon. Neighbor nodes and their location details are updated in the neighbor discovery process. Neighbor details are distributed to all the nodes. |
| B. Route Discovery Process |
| Source and destination node details are used in the route discovery process. Greedy Perimeter Stateless Routing Protocol (GPSR) is used for the route discovery process. Forwarding path is identified in the route discovery process. Route details are updated with current position of the path nodes. |
| C. Position Update Process |
| The position process is used to update the current location of the nodes. Adaptive Position Update (APU) based model is used for the position update process. Node mobility prediction mechanism uses the previous and current location of the neighbors. Forwarding path analysis is also used for the position update process. |
| D. Node Status Management |
| Link failure and node mobility are handled in the node status management process. Link failure analysis is carried out under the forwarding paths. Node movement is analyzed in the node mobility process. Node status is used for the path update process. |
| E. Load Balancing Process |
| Load balancing is applied for the data transmission process. Data forwarding path and traffic levels are used in the load balancing process. TCP and UDP based transmissions are supported with load balancing process. Load balancing algorithm is used to distribute the transmission load. This transparency is a key benefit: simulation code that runs on JiST need not be written in a domain-specific language invented specifically for writing simulations, nor need it be littered with special-purpose system calls and callbacks to support runtime simulation functionality. Instead, JiST converts an existing virtual machine into a simulation platform, by embedding simulation time semantics at the byte-code level. Thus, JiST simulations are written in Java, compiled using a regular Java compiler, and run over a standard, unmodified virtual machine. |
SIMULATION RESULTS |
| In this section, we present a comprehensive simulation based evaluation of EAPU using the popular JiST simulator. We compare the performance of EAPU with other beaconing schemes. These include PB and two other recently proposed adaptive beaconing schemes in (i) Distance-based Beaconing and (ii) Speed-based Beaconing. In the second set of simulations, we evaluate the impact of varying the traffic load on the performance of EAPU and also compare EAPU with the three beaconing schemes under consideration. We use the same scenario as in the first set of experiments. We fix the average node speed to 15 m/s. We vary the number of flows from 5 (low load) to 25 (high load). As the number of traffic flows increase, more nodes in the network are involved in forwarding packets |
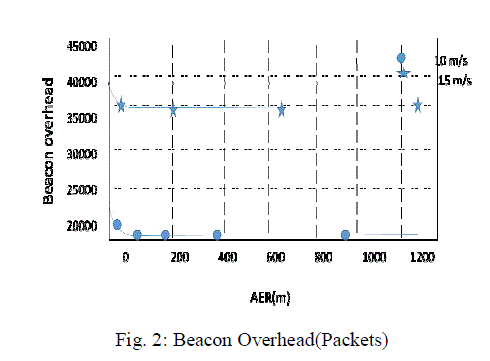 |
| Next, we focus on the second set of metrics, whichevaluate the impact of the beaconing strategies on thePerformance of the geographic routing protocols (GPRS in this case). These metrics include the packet delivery ratio, end-to-end packet delay, and energy consumption. Since,EAPU is successful in maintaining an up-to-date view of the local network topology, it also achieves a consistently high packet delivery ratio as illustrated in Fig.2, independent of the speed, since each node involved in forwarding a packet is almost always able to find an appropriate next hop neighbor. Even in the absence of MP component, the first few data packets transmitted will serve as the pilots to discover the topology in ODL rule (though they may fail to reach to the destination). However, we expect that packet lost due to the absence of the MP rule will have a greater impact on TCP connections, since TCP performance is more sensitive to the packet loss, e.g., thedata rate can be halved due to packet timeout. The selection of appropriate AER depends on the requirement of application. |
CONCLUSION |
| In this paper, we have identified the need to adapt thebeacon update policy employed in geographic routingprotocols to the node mobility dynamics and the trafficload and link failure. We proposed the Extended Adaptive Position Update strategy to address these problems. The EAPU scheme employs two mutually exclusive rules. The MP rule uses mobility prediction to estimate the accuracy of the location estimate and adapts the beacon update interval accordingly, instead of using periodic beaconing. The ODL rule allows nodes along the data forwarding path to maintain an accurate view of the local topology by exchanging beacons in response to data packets that are overheard from new neighbors. We mathematically analyzed the beacon overhead and local topology accuracy of EAPU and validated the analytical model with the simulation results. Future work includes the enhancement of security mechanism with the GPSR protocol, Since GPSR protocol failed to handle the compromise node in security attack. And also evaluate the performance of proposed scheme with security mechanism. |
References |
|