ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Lavanya 1, Dhanalakshmi 1, Dhivyanjali 1, Priyanga 1 , Esther 2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
Wireless sensor networks consist of sensor nodes with sensing and communication capabilities. We focus on data aggregation problems in energy constrained sensor networks. The main goal of data aggregation algorithms is to gather and aggregate data in an energy efficient manner so that network lifetime is enhanced. In this paper, we present a survey of data aggregation algorithms in wireless sensor networks. We compare and contrast different algorithms on the basis of performance measures such as lifetime, latency and data accuracy. We conclude with possible future research directions. Since sensors have limited lifetime, the need for developing algorithms for aggregating sensors' data forms an important concern in the area of WSNs. We present W-LEACH, a data-stream aggregation algorithm for WSNs that extends LEACH algorithm. W-LEACH is able to handle non-uniform networks as well as uniform networks, while not affecting the network lifetime. It, instead, increases the average lifetime for sensors. We simulate our algorithm to evaluate its performance. Results show that WLEACH increases the network lifetime and the average lifetime for sensors for uniform and non-uniform WSNs.
Keywords |
| Wireless Sensor Network, Data Aggregation, Data Density, Clustering method, W-leach. |
INTRODUCTION |
| A Wireless Sensor Network (WSN) consists of spatially distributed autonomous sensor to monitor physical or environment conditions, such as temperature, sound, pressure etc. and to cooperatively pass their data through the network to a main location. The more modern networks are bi-directional; also enabling control is sensor activity. The development of wireless sensor network was motivated by military applications such as battlefield surveillance; today such networks are used in many industrial and consumer applications, such as industrial process monitoring and control, machine health monitoring, and so on. |
| The WSN is built of “nodes”- from a few to several hundreds or even thousands, where each node is connected to one(or sometimes several) sensors. Each such sensor network node has typically several parts: a radio transceiver with an internal antenna or connection to an external antenna, a microcontroller, an electronic circuit for interfacing with the sensor and an energy source, usually a battery or an embedded form of energy harvesting. A sensor node mighty vary in size from that of shoebox down to the size of grain or dust, although functioning “motes” of genuine microscopic dimensions have yet to be created. The cost of sensor node is similarly variable, ranging from few hundred of dollars, depending on the complexity of the individual sensor nodes. Size and cost constraints on sensor nodes result in corresponding constraints on resources such as energy, memory, computational speed and communications bandwidth. The topology of WSN can vary from a simple star network to an advanced multi-hop wireless mesh network. The propagation technique between the hops of the network can be routing of flooding. |
| A WSN composed of self-organized wireless sensor nodes scattered in a monitored area collects, processes and transmits data acquired from the physical atmosphere [1],[2]. The main goal of a WSN is consistently detecting a accurately evaluating the events in the monitored area with the collected data. For this purpose, sensor nodes should be deployed closely. However, this will cause overlapping of sensor nodes’ sensing areas and the spatial redundancy of adjacent sensor nodes’ data [3],[4]. If every sensor node transmits collected data to the sink node, the sensor nodes will consume a large amount of energy. To reduce the amount of transmitted data in a WSN, a great number of correlationbased data aggregation methods have been studied in the literature [5]-[11]. |
| According to the level of sampled data in data aggregation strategy, data aggregation methods are grouped into three classes: data level aggregation, feature level of aggregation and decision level aggregation [12]. Also, based on the aggregation strategy, we can divide the data aggregation methods into three types: in-network query type [5],[13], data compression type[6],[14] and representative type [7],[9],[15],[16]. It will acquire a long time to obtain a reply from WSN in the first type. The second type is of limited effectiveness as it is too difficult. The third type is perceptive to the correlation measurement for sensor nodes. |
| The major objective of the representative type is selecting a representative sensor node in the neighbourhood and sending its observation to the sink node. Therefore, the relative error between a representative data and its correlated data is a considerable index for evaluating the represented performance. |
| The energy efficiency of the DDCD clustering method is not always the uppermost in data transmitting process. While in the clustering process, the DDCD clustering method is an energy efficient one. The main goal of data aggregation algorithms is to gather and aggregate data in an energy efficient manner so that network lifetime is enhanced. Wireless sensor networks (WSN) offer an increasingly attractive method of data gathering in distributed system architectures and dynamic access via WSN. |
II. LITERATURE SURVEY |
Wireless Sensor Networks: a Survey on Environmental Monitoring |
| Traditionally, environmental monitoring is achieved by a small number of expensive and high precision sensing unities. Collected data are retrieved directly from the equipment at the end of the experiment and after the unit is recovered. The implementation of a wireless sensor network provides an alternative solution by deploying a larger number of disposable sensor nodes. Nodes are equipped with sensors with less precision, however, the network as a whole provides better spatial resolution of the area and the users can have access to the data immediately. This paper surveys a comprehensive review of the available solutions to support wireless sensor network environmental monitoring applications |
Data Routing in In-network Aggregation in WSN: a Cluster Based approach |
| Large scale wireless sensor networks (WSNs) consists of many sensor nodes & these networks are deployed in different classes of applications for accurate monitoring, health, environment etc. The sensor nodes equipped with limited power sources. Therefore, efficiently utilizing sensor nodes energy can maintain a prolonged network lifetime. One of the major issues in sensor networks is developing an energy-efficient routing protocol to improve the lifetime of the networks. The proposed approach is a Cluster Based Data Routing for In-Network Aggregation that has some key aspects such as a reduced number of messages for setting up a routing tree, maximized number of overlapping routes, high aggregation rate, and reliable data aggregation and transmission & provides the best aggregation quality when compared to other existing algorithms |
Distributed Spatial Clustering in Sensor Networks |
| Sensor networks monitor physical phenomena over large geographic regions. Scientists can gain valuable insight into these phenomena, if they understand the underlying data distribution. Such data characteristics can be efficiently extracted through spatial clustering, which partitions the network into a set of spatial regions with similar observations. The goal of this paper is to perform such a spatial clustering, specifically δ-clustering, where the data dissimilarity between any two nodes inside a cluster is at most δ. We present an in-network clustering algorithm ELink that generates good δ-clusterings for both synchronous and asynchronous networks in O(√N logN) time and in O(N) message complexity, where N denotes the network size. Experimental results on both real world and synthetic data sets show that E Link’s clustering quality is comparable to that of a centralized algorithm, and is superior to other alternative distributed techniques. Furthermore, E-Link performs 10 times better than the centralized algorithm, and 3-4 times better than the distributed alternatives in communication costs. We also develop a distributed index structure using the generated clusters that can be used for answering range queries and path queries. The query algorithms direct the spatial search to relevant clusters, leading to performance gains of up to a factor of 5 over competing techniques. |
| Coverage in Wireless Sensor Networks: A Survey |
| Wireless sensor networks are a rapidly growing area for research and commercial development. Wireless sensor networks are used to monitor a given field of interest for changes in the environment. They are very useful for military, environmental, and scientific applications to name a few. One of the most active areas of research in wireless sensor networks is that of coverage. Coverage in wireless sensor networks is usually defined as a measure of how well and for how long the sensors are able to observe the physical space. In this paper, we take a representative survey of the current work that has been done in this area. We define several terms and concepts and then show how they are being utilized in various research works. |
III. CLUSTERING METHOD DESCRIPTION |
Data Density Correlation Degree |
| In a WSN, if a certain number of neighbouring sensor nodes’ data are close to a sensor node’s data; this sensor node can represent its neighbours in the data domain. This representative sensor node is called the core sensor node. |
| Definition 1: Core sensor node. Let us consider sensor node v has neighbouring sensor nodes. They are respectively v1, v2…vn. The data object of v is D. Its neighbouring sensor nodes’ data objects are respectively D1, D2... Dn. If there are N data object in D1, D2... Dn whose distances to D are a smaller amount than ÃÂõ and min Pts ≤ N ≤n then the sensor node v is called sensor node. Where min Pts is the amount threshold, ÃÂõ is the data threshold. Instinctively, the larger the N is, the better representative the sensor node v is to those sensor nodes whose data objects are in ÃÂõ-neighbourhood of D. Meanwhile, high attention of the data objects in the ÃÂõ -neighbourhood of D implies that sensor mode v has a high spatial correlation between it and these sensor nodes. Therefore, to determine the representation degree of v to those sensor nodes whose data objects are in ÃÂõ-neighbourhood of D in quantity, we proposed the data density correlation degree as shown in definition 2. |
| Definition 2: Data density correlation degree. Let sensor node v has n neighbouring sensor nodes which are inside the cycle of the communication radius of v. They are v1, v2...vn, respectively. The data object of v is D, and its neighbouring sensor nodes’ data respectively D1, D2......, Dn. Among these n data objects, there are N data objects whose distance to D is not as much of than ÃÂõ, and min Pts ≤ N ≤n. After that the data density correlation degree of sensor node v to the sensor node whose data objects are in ÃÂõ-neighbourhood of D is as follows. |
 |
 |
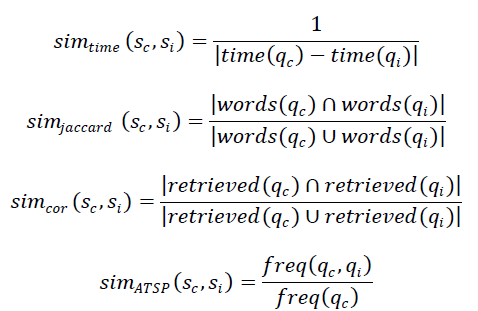 |
IV. METHODOLOGIES |
| The different Methodologies used here are |
| ïÃâ÷ Setting up Network Model |
| ïÃâ÷ Base station and agent selection Module |
| ïÃâ÷ Data Communication Module |
| ïÃâ÷ Data Density Correlation Degree Module |
| ïÃâ÷ Energy Efficient Module |
Setting up Network Model |
| Our first module is setting up the network model. We consider a large-scale, homogeneous sensor network consisting of resource-constrained sensor nodes. Analogous to previous distributed detection approaches; we assume that an identity-based public-key cryptography facility is available in the sensor network. Prior to deployment, each legitimate node is allocated a unique ID and a corresponding private key by a trusted third party. The public key of a node is its ID, which is the essence of an identity-based cryptosystem. Consequently, no node can lie to others about its identity. Moreover, anyone is able to verify messages signed by a node using the identity-based key. The source nodes in our problem formulation serve as storage points which cache the data gathered by other nodes and periodically transmit to the sink, in response to user queries. Such network architecture is consistent with the design of storage centric sensor networks. |
Base Station and Agent Selection Module |
| Our Second Module is Base Station and Agent Selection Module. |
| BASE STATION |
| ïÃâ÷ Base station has computer and sensor database to store collected sensor data MOBILE SINK |
| ïÃâ÷ Mobile sink travels in the sensing area and collects data from each sensors |
| ïÃâ÷ Upload the collected data to the base station |
Data Communication Module |
| Our Third Module is Data Communication Module. In this module the followings functions are takes place. |
| ïÃâ÷ End to end data communication |
| ïÃâ÷ When a node needs connection broadcast the request. |
| ïÃâ÷ Other nodes forward this message also record the node that they heard it from. |
Data Density Correlation Degree (DDCD) Module |
| Our Fourth Module is Data Density Correlation Degree (DDCD) Module. By using this module the cluster based approach is established. Using this cluster based approach the cluster head aggregates the raw data then the aggregated data are sent to the sink. |
Energy Efficient Module |
| Our Fourth Module is Energy Efficient Module. In this Module the following functions are takes place. |
| • Energy saving –W-LEACH Algorithm. |
| • Neighbours go to sleep when there is no transmission. |
| • Reduces the traffic load and conserve energy of the sensors. |
V. W-LEACH OR WEIGHTED LEACH |
| W-Leach is a centralized algorithm. As LEACH, an algorithm operates in cycles so that each tower should have two phases, namely a setting phase and a steady state phase. In the configuration phase, W-LEACH selects a number of sensors to be CHs. Each CH is selected based on a weight value which corresponds to each node. Unlike LEACH, whether a sensor is CH or not in the preceding rounds, is independent in W-LEACH. After all CHs are selected clusters are formed such that each sensor is assigned to its closest CH. Leach requires each CH collects data from all sensors in its group at its steady state phase, against W-Leach chooses only x% of sensors in each group to send data to their CH. Candidates for sending data to CHs are selected according to their weight. |
| Although the W-LEACH protocol has advantages in terms of an energy recovery but this protocol is based on knowledge of the location of nodes to select the nodes between transmission nodes and nodes remain in sleep. In addition it does not consider the mobility of sensor nodes after the "installation phase" of groups in a round while the W-LEACH protocol accompanies a lot of data loss in mobility environment focused on "hot spots". Because its application is limited to nodes fixed sensors. |
| In our work the W-LEACH WITH BECON RESPONDER outperforms W-LEACH in terms of environment, field of use in underground and Mobility to extended Network lifetime. W-LEACH BECON RESPONDER is based on a number of neighbors to reorganize node density after that it selects active nodes and those which remain asleep in a BECON RESPONDER manner. After the text edit has been completed, the paper is ready for the template. Duplicate the template file by using the Save As command, and use the naming convention prescribed by your conference for the name of your paper. In this newly created file, highlight all of the contents and import your prepared text file. You are now ready to style your paper; use the scroll down window on the left of the MS Word Formatting toolbar. |
| Weighted LEACH: it’s an extended LEACH to challenge uniform and non-uniform network. In set up phase, the base station based on density of nodes to divide member nodes in two groups. One group member nodes transmit their data while the member nodes in the other group remain asleep. The selection of nodes which remain asleep is centralized. Weighted Low Energy Adaptive Hierarchy (W-LEACH) is an extension of LEACH to efficiently handle non-uniform sensor distribution in WSNs. It increases the lifetime of the network. But this protocol is centralized because the base station is the only responsible for selecting sleeping nodes and active nodes. In addition, the base station needs the location node to manage the density of nodes after it informs each node with an additional traffic. In this paper, we propose later a BECON RESPONDER algorithm which weighs LEACH without nodes’ maps. |
| WEIGHTED LEACH: |
| 1. Proposes clustering of sensors + cluster leaders. |
| ïÃâ÷ Can aggregate data in single (local) cluster. |
| ïÃâ÷ Rotating cluster head balances energy consumption. |
| ïÃâ÷ Cluster formation distributed and energy efficient. |
| 2. Time is divided into rounds. |
| 3. A node self-elects itself as the cluster head. |
| 4. Higher residual energy, higher probability to be head. |
| ïÃâ÷ Close-by sensors join this cluster-head. |
| ïÃâ÷ Cluster head does TDMA scheduling and gathers data. |
| ïÃâ÷ Gathered data compressed based on spatial correlation. |
| ïÃâ÷ Transmits data to Base Station (@ higher power) |
| 5. In the next round, another cluster head elected. |
| ïÃâ÷ Probabilistic load balancing. |
| ïÃâ÷ Network lifetime can increase manifolds. |
| The Advantages of W-LEACH are, |
| ïÃâ÷ Energy saving: |
| ïÃâ÷ Neighbours go to sleep when sense transmissions |
| ïÃâ÷ Reduces control overhead by sending multiple data |
| ïÃâ÷ With the help of data aggregation process we can enhance the robustness and accuracy of information which is obtained by entire network, certain redundancy exists in the data collected from sensor nodes thus data fusion processing is needed to reduce the redundant information. |
| ïÃâ÷ Another advantage is those reduces the traffic load and conserve energy of the sensors. |
| ïÃâ÷ Achieves performance superior to existing protocols in terms of energy efficiency, packet delivery ratio (PDR), and latency. |
| ïÃâ÷ Simulation results also show better performance than that of two recent proposals for routing around dead ends. |
 |
W-LEACH with becon responder algorithm |
| In W-LEACH with BECON RESPONDER, The selection of CHs and form clusters are as in LEACH. Each sensor node N (i) elects itself to be cluster head with a probability as In the following chart, we assume that node N2 is elected CH and N1, N2 are not cluster head. So N2 spreading ADV CH to inform its neighbours that it becomes a CH. Then N1, N3 aggregates the ADV CH messages from CHs and choose its nearest CH. Then it transmits a BECON REQ message to its CH and received BECON REQ message from other member nodes to determine their neighbours’ nodes and the distance corresponding to every neighbour. The CH, in its turn, receives the BECON REQ message to form its cluster and create EMERGENCY Schedule. Then it spread s EMG message to inform their member nodes when can transmits there data. Member nodes after receiving they calculate the number of nearest neighbours to a lower maximum distance determined. If this number is less than a limited number the node goes to sleep during this round as N3. Else the nodes calculate their Time Slot to transmit their data as N1dierily. |
VI. NS2 W- LEACH IMPLEMENTATION |
Purpose |
| What is necessary to install and run the W-LEACH protocol on version 2.35 of ns2? At the time of this writing, this is the newest version of ns2. The WLEACH implementation was written as a stand-alone application. Thus, in the past a version compiled for WLEACH may or may not work for other protocols. In addition, the original version of WLEACH was compiled for version 2.5b which is an outdated version of ns2. |
The following goals have been achieved: |
| ïÃâ÷ Merged and compiled ns2.35 to support WLEACH protocol. |
| ïÃâ÷ Modified code to allow for support of all protocols including LEACH without |
| ïÃâ÷ Recompilation. |
| ïÃâ÷ Validated running of all demos using the ns2.35. |
| ïÃâ÷ Executed LEACH simulation included in the uAMPS changes package (tcl/ex/wireless.tcl) |
VII. CHANGES IN ADDING W-LEACH SUPPORT |
 |
Special Changes |
| Some changes are significant enough in nature to list explicitly. This does not mean that you need to make these changes if you follow the procedure listed below. These changes could, however, affect the performance or results of the program and are thus listed here so that you can be aware of them when you run your simulations. |
 |
VIII. EXPERIMENTAL RESULTS |
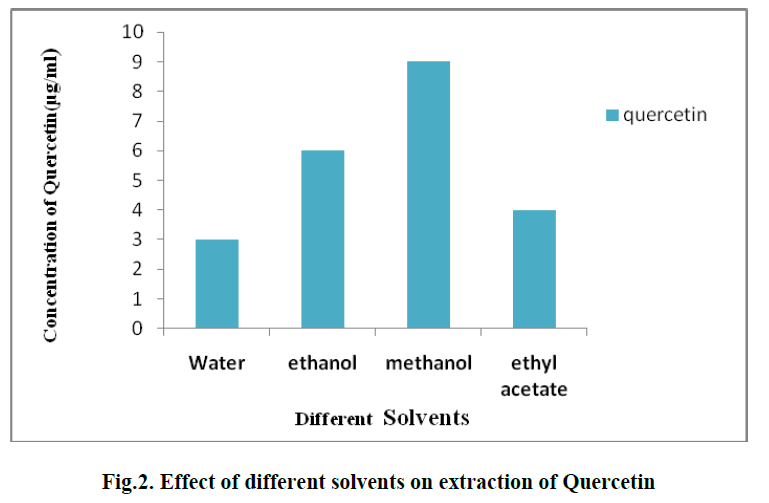 |
| Figure 2 represents the comparison of packet delivery ratio withW-Leach and DDCD. Here x-axis represents the number of packets and the y-axis represents the time period. DDCD algorithm is represented Red in colour while the greeen colour represents the W-Leach. |
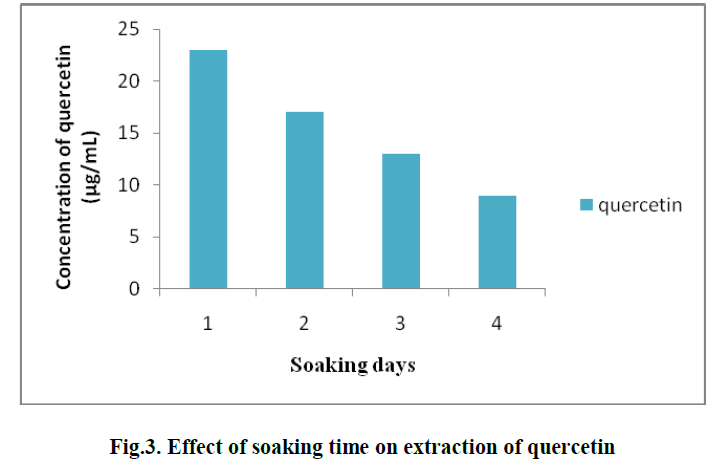
| Figure 3 represents the comparison of End to End delay with DDCD and W-Leach. Here also the x-axis represents the number of packets and y-axis represnts the time taken to deliver the packets. The graph clearly shows that Wleach takes the less average time to reach the destination when compared to DDCD. |
 |
| Figure 4 represents the overall data density analization. Here x axis represents the number of packets and the yaxis represents the time period. The graph shows that the delivery of packets is much faster than the DDCD. And the data density occurs less in W-Leach. Hence it travels faster than the DDCD. |
 |
| Figure 5 represents the comparison of energy utilization with DDCD and W-Leach. X-axis represents the total number of packets and the y-axis represents the time period. Here the graph shows that the W-Leach consumes less amount of Energy for transmitting the packets when compared to DDCD. |
 |
IX. CONCLUSION |
| The main contributions of this paper are the introduction of the data density correlation degree (DDCD) clustering method. The pseudo code of the DDCD clustering method is given as well. The proposed algorithm provides energy efficient path for transmission and maximizes the life time of a sensor nodes. With the use of DDCD clustering method we can minimize the packet loss ratio and end to end delay. So that the packet delivery ratio has been increased. By using W-LEACH algorithm we can get more energy efficiency. |
| We have presented comprehensive data aggregation algorithms in wireless sensor networks. All of them focus on optimizing important performance measures such as network lifetime, data latency, data accuracy and energy consumption. Efficient organization, routing and data aggregation construction are the three main focus areas of data aggregation algorithms. We have described the main features, the advantages and disadvantages of each data aggregation algorithm. We have also discussed special features of data aggregation such source coding. The trade-offs between energy efficiency, data accuracy and latency have been highlighted. Most of the existing work has mainly focused on the development of an efficient routing mechanism for data aggregation. However, the performance of the data aggregation protocol is strongly coupled with the infrastructure of the network. There has not been significant |
| research on exploring the impact of heterogeneity and mode of communication on the performance of the data aggregation protocols. Although, many of the data aggregation techniques presented look promising, there is significant scope for future research. Combining aspects such as energy, data latency and system lifetime in the context of data aggregation is worth exploring. A systematic way of the relation between energy efficiency and system lifetime is an avenue of our research. Analytical results on the bounds for lifetime of sensor networks are another area worth exploring. Existing work has provided bounds on lifetime for networks with specific network topologies and source behaviours. It would be interesting to extend this work to more general network topologies. |
References |
|