ISSN ONLINE(2319-8753)PRINT(2347-6710)
ISSN ONLINE(2319-8753)PRINT(2347-6710)
Shilpi Dhankhar1, Shilpy Agrawal2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Science, Engineering and Technology
In past few years, VANET (Vehicular Ad-hoc Network) has become a remarkable area for research analysis and development. VANET is a subgroup of MANET (Mobile Ad-hoc Network). VANET and MANET both are wireless networks which are characterized as self-configured and autonomous ad-hoc networks. VANETs differ from MANETs in terms of dynamic topology and high mobility. Due to unstable connectivity, high mobility and network partitioning, information routing in VANETs becomes difficult and challenging, thus creating a need for efficient VANET routing protocols. This paper provides a summary on VANET and gives its routing protocols which focuses on vehicle to vehicle i.e. V2V communication. This paper aims at classifying protocols on the basis of routing information and comparing them using following parameters namely methodology used, benefits/strengths and limitations. The paper compares reactive and proactive routing protocols based on their advantages and disadvantages, also discussing the challenges and research related issues for the routing mechanisms that exist in VANETs
Keywords |
| Vehicular Ad-hoc Network (VANET), Routing Protocols, Reactive, Proactive, Issues |
INTRODUCTION |
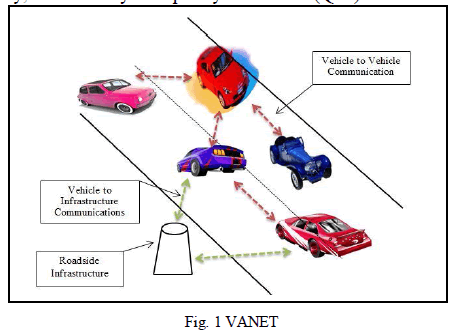
| VANETs are a special category of MANETs. VANET has two entities: roadside infrastructure and vehicles. In VANETs, vehicles act as the mobile nodes. The roadside infrastructure is fixed, hence act as distribution points for the vehicles [1]. The two types of wireless communications exist in VANET, Vehicle to Vehicle i.e. V2V and Vehicle to Roadside Infrastructure i.e. V2I as depicted in fig. 1. VANET differs from MANET in terms of following characteristics that are high mobility, dynamic topology, self-organized architecture, distributed communication, path restrictions and variable network size. These characteristics as stated before make the VANETs environment difficult for developing effective routing protocols. A vast number of applications exist in VANETs namely traffic efficiency applications, management applications, infotainment applications, but the two main applications are: passenger comfort applications and safety applications [5]. VANETs system design and implementation come across following difficulties such as: routing, security, privacy, connectivity and quality of services (QoS). |
 |
LITERATURE SURVEY |
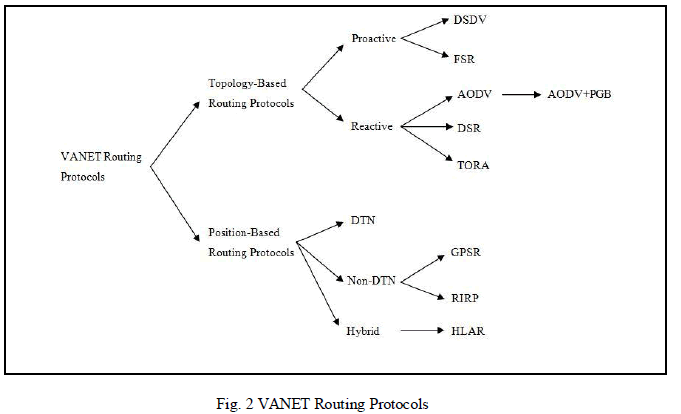
| Routing is a process of sending data packets from source node to destination node, therefore routing in ad-hoc networks is a critical issue. There are a number of routing protocols existing in various networks such as AODV (Ad-hoc On Demand Distance Vector routing), DSR (Dynamic Source Routing), DSDV (Destination Sequenced Distance Vector routing), FSR (Fisheye State Routing) and many more routing protocols will be discussed further in the paper. This paper focuses on the routing protocols of VANETs between vehicle to vehicle communication, the routing protocol classification and the related research open issues in VANET routing today on the basis of various aspects such as characteristics, quality of services, techniques used, routing algorithms, routing information, network architecture etc. VANET routing is broadly classified into following categories: multicast, broadcast, unicast, topology-based and position-based routing. This paper discusses only topology-based and position-based routing protocols looking at the protocol characteristics and techniques used [1]. |
| The paper has been divided into five sections where section I gives general VANET introduction and section II provides a brief introduction on the literature survey of this paper and section III provides discussions on information about various types of routing protocols. Routing protocols have been further divided into position-based and topology-based routing protocols. Section IV gives the discussions on research related open issues and section V gives the results which are a comparison of the different types of routing protocols in a tabular form. Finally, section VI provides conclusion of the paper and future scope of VANETs. |
DISCUSSIONS ON ROUTING PROTOCOLS IN VANETS |
| Based on routing information, routing protocols are broadly categorized as topology-based and position-based routing protocols. In topology-based routing mechanism, we deal with the network layout/architecture of the nodes such that packet forwarding is possible using the information that is available about the nodes and links within the network whereas, location of nodes should be known in position based routing mechanism for packet forwarding. |
A. Topology-based Routing Protocols |
| Topology-based routing protocols make use of routing tables for storing the link information as a basis of packet forwarding from source node to destination node. These protocols are further categorized into two types based on the network architecture [1]: Proactive and Reactive routing protocols. |
| 1) Proactive Routing Protocols: Proactive routing protocols, also known as table-driven protocols, allow every network node to maintain a routing table for storing the route information to all other nodes, every next hop node is maintained in the table entry that comes in the path towards the destination from the source. The routing table of every node gets updated whenever a change in network topology occurs as a result of which more overhead cost is incurred. These protocols provide actual data to the network availability [1]. The shortest path algorithms are used by these protocols to find out which route has to be chosen. Destination Sequenced Distance Vector (DSDV) and Fisheye State Routing (FSR) protocols are examples of proactive routing protocols. |
| a) Destination Sequenced Distance Vector (DSDV) Routing Protocol: Based on the distance vector strategy using shortest path algorithm, DSDV [1] routing protocol implements a single route from source to destination which has been maintained in the routing table. A routing table is maintained for each node containing information of every accessible node in the network and total number of hops needed to succeed those nodes. The destination node initiates a sequence number to every entry in the table. Each node maintains the route reliability by broadcasting their routing table to the neighboring nodes. DSDV protocol does not allow cyclic routes, reduces control message overhead and excludes extra traffic caused by frequent update. The total size of routing table is reduced as DSDV keeps solely the best possible path to each node instead of multi paths. DSDV is not able to control the networks congestion that decreases the routing efficiency. |
| b) Fisheye State Routing (FSR) Protocol: FSR [1] is a table-driven routing protocol that maintains a topology map for each node and updates its routing table by collecting the latest information from its neighboring nodes. The updated data is broadcasted with different frequencies with higher frequencies rather than the farther ones to various different destination nodes based on the hop distance from the forwarding node. Since FSR helps every node in network to exchange the updated routing information with its immediate neighboring nodes partially, it reduces the consumed bandwidth and provides reduction of routing overhead. The drawbacks with the FSR are the increasing network size the number of routing tables that leads to complexity of storage and process overhead of routing table. Route establishment becomes difficult if destination node goes outside the range of source node. Even if there is any link failure, changes in routing table do not occur because FSR does not trigger any message for link failure. FSR works on basis of link state routing and Global State routing. |
| Thus the proactive routing protocol advantages can be abbreviated as follows, namely, |
| ïÃâ÷ Since route from source node to destination node is maintained via routing table, there is no need of route discovery process. |
| ïÃâ÷ Performance of proactive routing protocols is good in low mobility networks whereas reactive routing protocols have high mobility and density than the proactive routing protocols. |
| ïÃâ÷ In proactive protocols, increase in network overhead occurs when unused routes consume available bandwidth. |
| 2) Reactive Routing Protocols: Reactive routing protocols, also known as on-demand routing protocols. They are called so because on requirement of a route that does not exist from source node to destination node, the route discovery starts. This reduces the network traffic and saves bandwidth. Flooding of the network helps in route discovery mechanism by sending a route request message. Any node existing on the route towards the destination on receipt of the request message, sends back a route response message to the source node using unicast communication. These routing protocols have high route finding latency and are suitable for large sized mobile ad-hoc networks which are highly mobile and have frequently changing topology. The following sections illustrate few existing reactive routing protocols. |
| a) Ad-hoc On-demand Distance Vector (AODV) Protocol: AODV [1, 3, 11] protocol reduces flooding in the network and gives low network overhead comparing to the proactive protocols. This routing protocol minimizes the routing table by creating a route when a node needs to send information data packets to other nodes in the network, hence reducing the memory size required. The routing table keeps the entries of the recent active nodes and the next hop node of the route instead of keeping the whole route. AODV uses destination sequence numbers (DesSeqNum) for route discovery which eliminates looping in routes and provides dynamic updates for adapting the route conditions. AODV is more suitable for large networks and network having high dynamic topology. This protocol causes delay in route discovery process. When route failures occur, new route discovery is required causing additional delays thus decreasing the data transmission rate and increasing the network traffic. This causes more bandwidth consumption that is increased due to increasing number of nodes in the network which causes collision leading to packet loss problem. |
| Ad-hoc On-demand Distance Vector Preferred Group Broadcasting (AODV+PGB) Routing Protocol: AODV routing protocol with PGB (Preferred Group Broadcasting) algorithm [1, 9] reduces control message overhead and provides route availability in VANET environment which reduces the routing overhead in networks is considered to be an important issue and also achieving the routes consistency which is a desirable issue today. The performance of adhoc networks decreases with various upcoming issues such as the network throughput decreases when there are a large number of errors in the network and when the signals are weak from source node to destination node, the hidden terminals can easily interrupt the communication between the two nodes. PGB algorithm makes it possible for some nodes to again broadcast a route request data message. If even after rebroadcasting the message, no nearest node to destination is found, delay in route discovery process occurs. This protocol may cause packet duplication if at the same time, two nodes broadcast same data packet. |
| b) Dynamic Source Routing (DSR) Protocol: DSR [1, 3, 4, 12] routing protocol is a reactive protocol which implements routing process using low overhead and quick reaction to frequently changing topology to ensure successful packet delivery even if change in network happens. DSR is a multi-hop routing protocol decreases the network traffic by decreasing periodic messages. DSR provides two processes that are the route discovery mechanism and route maintenance process. During the discovery mechanism, when the source node requires to search a non-existing route, a route request message is send by it to all its neighbors. All nodes in- between that receive the request message broadcast it again except to the destination or if there is a direct route from the forwarding node towards the destination node. After which the source node receives back route reply message and that route is stored in the routing table of the source node for future use. If any failure in route occurs, the source is informed by sending a route error message back to the source node. In this protocol routing, each information packet consists of a list of nodes that exist in the path so that source node deletes the nodes on the route which have failed from its cache and stores another successful route to that destination and exchanges it with a correct route. If no such route exists, DSR again starts a new route discovery process. The benefits/advantages provided by DSR routing are best visible in networks with less mobility as it makes use of alternate routes before a new route discovery mechanism is initiated. Although multi- route discovery could cause further routing overhead/traffic due to addition of whole route information to each information packet of routing table, besides, as the network discovers large routes as well as additional nodes, the routing overhead increases quickly resulting in degradation of network performance. |
| c) Temporally Ordered Routing Algorithm (TORA) Protocol: TORA [1] is a distributed routing protocol. TORA uses multi-hop routes during routing mechanism. This protocol reduces the communication overhead to adapt with frequent network changes and does not include implementation of shortest path algorithm and therefore, routing doesn’t represent a distance. This protocol creates a directed graph which has the source node as its tree root node. This protocol consists of tree structure in which packets should run from higher nodes to lower nodes. As a node broadcasts data packets to its destination node, its neighbors send back a route reply message if its packets run from higher levels to lower level to the destination, otherwise it only rejects the data. The protocol follows loop free routing and multi path routing as the information moves down to the destination node and does not move back upward to the forwarding node. TORA provides a route towards each node of the network topology, also reducing control message broadcast which are the main advantages of TORA. In this routing mechanism, routing overhead/traffic is caused during route maintenance among network nodes in high dynamic VANETs. |
| Topology-based routing protocols are not much suitable in case of vehicular ad-hoc networks since: |
| ïÃâ÷ Topology routing protocols are not very scalable. |
| ïÃâ÷ Route finding latency for topology routing protocols is high. |
| ïÃâ÷ The unused paths stored in routing tables occupy available bandwidth unnecessarily. |
| ïÃâ÷ AODV consumes extra bandwidth due to periodic beaconing. |
| ïÃâ÷ Topology routing protocols do not perform good for high mobility networks. |
| ïÃâ÷ Topology routing protocols give worse performance in small networks. |
B. Position-based Routing Protocols |
| Position-based routing protocol [10] depends on the position/location data during the routing mechanism. The source node sends information data packet to the destination making use of the packets location instead of utilizing the network address. During this protocol mechanism, every node decides its position and that of their neighboring nodes through help of Geographic Position System (GPS) which is a position determining service. The node determines the location of its neighbor inside the radio range of the current node. Once the source node sends its data packet, it saves the location of the destination in the header of the packet that aids in sending the data packet to the destination node with no need of route discovery, route maintenance or any awareness of topology. Hence, position-based routing protocols are considered to be appropriate and stable for highly mobile VANET environments with topology-based routing protocols. Position-based protocols are categorized as namely, DTN i.e. Delay Tolerant Network, Non-DTN i.e. Non Delay Tolerant Network and Hybrid protocols. |
| 1) Delay Tolerant Network (DTN) Routing Protocol: DTN [1] routing protocol is an efficient protocol for networks with characteristics such as rapid disconnectivity during communication, massive/huge scalability, large unavoidable delays, restricted bandwidth, high fault tolerance rates and power constraints. DTN protocol uses a store, carry and forward strategy within the network where all the nodes help each other in forwarding the data packets. Each node features restricted transmission range, thus packet transmission takes long delays. DTN may be a mobile node that creates routes towards other nodes in the network once they are in the current nodes’ transmission range. In DTN protocol, we cannot ensure that disconnectivity will not occur, so the data packets are cached for some time duration with other nodes on the route i.e. intermediate nodes. To form a routing protocol for DTN network having such characteristics is an important issue. |
| 2) Non Delay Tolerant Network (Non DTN) Protocols: The Non-DTN [1] protocols are a type of position-based routing protocols that do not take into account the disconnectivity problem instead assume that a large amount of nodes exist to attain successful communication, which implies that the protocol is more appropriate for dense networks. The source node forwards the message to the closest neighboring node to the destination node. This strategy can also fail, if no such nearest neighboring node exists but only the current/forwarding node. This failure is handled by using different strategies of Non-DTN routing protocols such as: |
| a) Greedy Perimeter Stateless Routing (GPSR): GPSR [1, 8] follows greedy routing mechanism for routing in VANETs. During this protocol routing, every node sends a data packet to different intermediate nodes that are close to destination node, until the data reaches the destination. If there are not any neighboring nodes nearer to message’s destination, it makes use of perimeter forwarding technique to come to a decision to which node the message should be delivered. GPCR is a stateless routing protocol which keeps information about its first hop neighbors’ position that increases scalability of protocol over the shortest path ad hoc routing protocols. A benefit of GPSR routing protocol is the dynamic forwarding packet decision it takes. This routing protocol comes across link failures that occur because of frequently changing topology of network and high mobility of the network. This drawback is handled via perimeter forwarding which causes huge data loss and because a large number of hops that is caused in perimeter forwarding technique, more latency time is taken. The information that is embedded in the packet header does not get updated, if destination node acquires a new position. |
| b) Reliability Improving Position-based Routing (RIPR): RIPR [1], a position-based routing algorithm, was created to be used in vehicular ad hoc network routing. RIPR algorithm tries to solve the problem of link failures which are found during routing process. This protocol determines the vehicle speed and direction in which it moves on the roads. Here, the source selects a nearby node to send the data determining the mobility for the intermediate nodes. The source node creates a routing table storing positions with mobility speeds of neighboring nodes. This algorithm is used to select the forwarding node that aids in choice of next intermediate node, is done using characteristics of the route and therefore the position of node after the exchange of message [1] is done. The protocol therefore, helps in avoiding the problem that does not allow a node to select its neighbor node as intermediate node which arises when no nearer node to the destination exists. Two types of techniques are used by RIPR protocol: greedy technique and perimeter technique similar to GPSR protocol. RIPR also uses characteristics of the route and considers the position of the nodes. The advantages of the RIPR protocol are that it reduces link failure drawback that occurs due to storage of the data of wrong intermediate node. |
| 3) Hybrid Position-based Routing: Hybrid routing is the position-based routing that reduces control overhead/traffic and do not want to maintain the table since they make use of the location information about the neighboring nodes and destination node which makes position-based routing more scalable. Some limitations are as follows that restrict the use of position-based routing [1]: |
| ïÃâ÷ According to the positional accuracy, the position routing protocol performance may decrease as the precise location information is a factor to have a better performance in the position routing. |
| ïÃâ÷ If no nearest neighboring node to the destination exists, position routing may lead to link failures. |
| Researchers developed hybrid schemes merging the characteristics of more than one routing protocols, such as merging of two position-based routing protocols: DTN and Non-DTN routing protocols; or merging of position-based routing protocols along with one or more topology-based routing protocols. The hybrid positional routing protocols make use of advantages of two or more schemes. |
| a) Hybrid Location-based Ad-hoc Routing (HLAR) Protocol: HLAR [1] is an efficient position-based routing protocol is a scalable protocol that uses the positional information and helps in reduction of the routing control overhead in comparison to on-demand routing. HLAR protocol can act as on-demand routing protocol when either information of position is limited or is not sufficient enough and can overcome the problem where no nearer neighboring nodes to the destination node exist. HLAR also works as reactive routing protocol and helps in route discovery process. When we do not get a route to the destination node, then the source node adds the data packet of its position and position of destination node to route request message to search for the nearest node existing to the destination. If any such node exists, then a route request message is further forwarded to it and if a closest node to the destination is found, then the source node broadcasts a request message to all of its neighboring nodes. The mechanism is then repeated by the source node until the destination node is reached. Since the intermediate node does not have backward link to the source node, HLAR does not ensure if a reliable route exists. |
DISCUSSIONS ON ISSUES IN VANETS |
| Based on our survey on routing protocols of VANET, we found that few challenges and open research issues exist in routing of VANETs which is the most important area for research today. These open issues and challenges in VANET routing such as driver’s behaviour, loss of signal, interferences caused by tunnels and high buildings [5, 6] have been discussed in this section. |
| A. Dynamic Topology and High Mobility: Vehicles are the mobile nodes in VANETs and move according to the road pathways which restricts the mobility of the nodes. This causes the disruptions in communications and changing topology. For routing protocol development, we should traumatize dynamic topology. A solution to give effective information dissemination not withstanding fast changing topology may be broadcast based communication. |
| B. Fault Tolerance: Since a VANET has fast changing topology; several vehicles could enter or exit the network periodically. If during the communication, a node leaves the network, a new route should be created by the routing protocols to manage the network. This problem can be solved if the route failure is known in advance, this requires lot of updated information exchange leading to un-scalable communication. |
| C. Flexibility and Scalability: Area decides the number of vehicles, for e.g. number of vehicles in rural area is low without road side units, it becomes difficult to maintain the network connectivity. For development of the road side units, large investments are required, therefore less power constraints can be used by increasing communication ranges with higher transmission power to form every node reach its destination without support of the roadside units. On the contrary, urban area is very large and crowded having a huge range of vehicles running. The routing protocols need to reduce the overhead and control of data packets as a larger number of vehicles need to communicate. It should provide safety communication rather than control overhead. |
| D. Delay Constraints and Real-time Transmission: To deal with sudden occurring situations, drivers do not have enough time to respond as the information is distributed in the real time. If information is received on time, accidents can be avoided. Hence the routes are to be maintained and constructed for real time applications. |
| E. Security Enhancement: Security [2] stands the most important and challenging issue in safety applications of VANETs. If no security is provided in routing protocols, a malicious node can enter the network and cause damage. This could lead in misleading of information which can be used by terrorists to trap innocent people as dead end tunnel. So in turn to protect the information; authentication, integrity and non-repudiation must be achieved such that there is no entry of any unauthorized vehicle into the network and no modification of the data packets is allowed during the communication. Hence, security is an important issue as future research area. |
RESULTS |
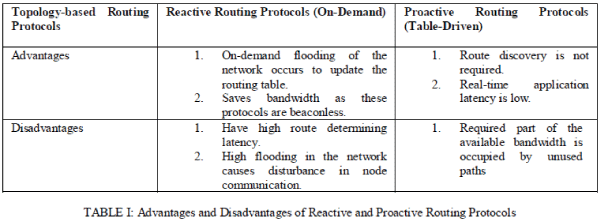
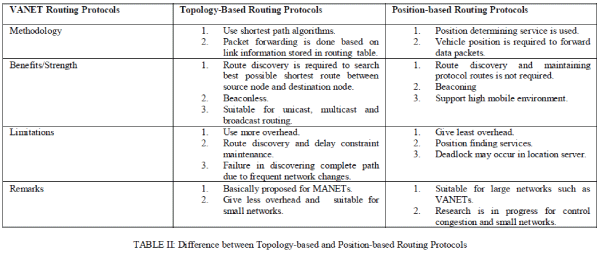
| Fig. 2 gives division of the routing protocols as discussed above in the paper based on which the results have been derived in the form of comparisons. The result of the study on routing protocols has been given as a comparison of the routing protocols in the form of tables discussing their advantages and disadvantages. Table I gives comparison between the reactive and proactive routing protocols stating their advantages and disadvantages [7] and Table II gives the difference between the topology-based and position-based routing protocols. |
 |
 |
 |
CONCLUSIONS |
| This paper has provided a summary of VANETs i.e. vehicular ad hoc networks discussing their characteristics and motivations with a study of VANET routing protocols that target vehicle to vehicle communication. This paper provides two categories of VANET routing protocols that exist since previous couple of decades, giving a brief discussion of the protocol working and their important benefits/advantages and disadvantages along with limitations. This survey paper has given differences among major classifications of routing protocols. In this brief study on various VANET routing protocols; different related research issues and challenges/difficulties are represented that require more effort and research to address them. |
ACKNOWLEDGEMENT |
| I would like to express my gratitude towards my mentor Ms. Shilpy Agrawal, Assistant Professor in Department Of Computer Science and Engineering at ITM University, Gurgaon for her kind co-operation and encouragement which helped me to understand the vast topic of Vehicular Ad-hoc Networks. I would like to thank my family as well, for their continuous support and encouragement. |
References |
|