Keywords
|
| Cluster head; LEACH protocol; wireless sensor networks; routing protocol |
INTRODUCTION
|
| Wireless Sensor Network consists of nearly about hundred and thousands of small tiny devices, which are distributed autonomously, called as sensor nodes. These nodes used to monitor physical or environmental conditions such as temperature, acoustics, sound, pressure, vibration and motion. Since the nodes are battery operated, the energy plays an important role in WSN. As a result, many more protocols have been proposed for initializing the energy consumption of these sensor nodes. |
| Typically, each and every node in a sensor network consists of one or more sensors, a radio transceiver or other wireless communication devices, a very small microcontroller and the energy source. As in most of the cases of WSN applications, energy plays an important role, since energy source is a battery. The important goal is preserving the consumed energy of each node, which should be considered, while making a routing protocol for wireless sensor network. |
| In WSN the main objective behind the routing protocol is to make the network more useful and much efficient. Routing protocol is categorized into 3 parts based on the structure of network, which are flat routing; hierarchical routing and location based routing. In flat routing, for collecting or generating the data and routing to the destination, all the sensor nodes of the network performs the same functionality and works together. The directed diffusion protocol and (SPIN) Sensor Protocol for Information via Negotiations protocol are some of the examples which belong to this flat routing. In the hierarchical routing, the whole network is partitioned into many clusters for the improvement of scalability and utilizations of the energy of the nodes efficiently. LEACH protocol is an example for this. Whereas in location based routing, each and every nodes locations are monitored continuously, for finding the routing path for the communication purpose. Global Positioning System (GPS) devices are used along with network nodes. Examples are GRS (Geographic Adaptive Routing). Many routing protocol have been proposed in the literature such as LEACH protocol. |
| LEACH is Low Energy Adaptive Clustering Hierarchy. It is considered as the very most popular routing protocol which uses the cluster based routing for minimizing the energy consumption. In this paper we propose an enhanced variant LEACH protocol that will further improve the consumption and making it energy efficient. |
| In section II -we discuss in details the Leach protocol, section III -disadvantages of the Leach protocol, section IVcontains related work, section V- we introduce our proposed protocol and section VI- conclusion. |
LEACH PROTOCOL
|
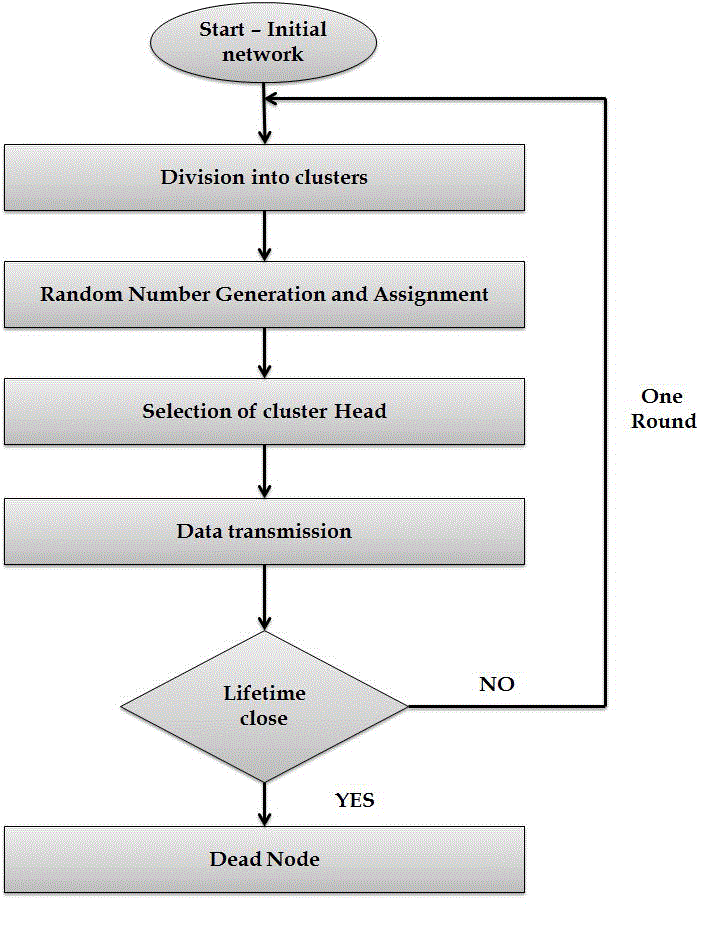
| LEACH protocol is the first hierarchical cluster based routing protocol, proposed by Wendi. B. Heinemann, et al. for wireless sensor network. It divides the nodes into clusters, and a dedicated node in cluster with extra privileged called CH (Cluster Head). Leach selects the CH randomly and assigns these nodes by following the policy of round robin management for ensuring fair dissipation of energy between nodes. The CH is then responsible for creating and manipulating the TDMA (Time Division Multiple Access) schedule and in order to reduce the amount of information transmitted to the BS( Base Station), the CH aggregates the data from the nodes where these data is needed using the CDMA (Code Division Multiple Access). All the other nodes are the members of cluster. |
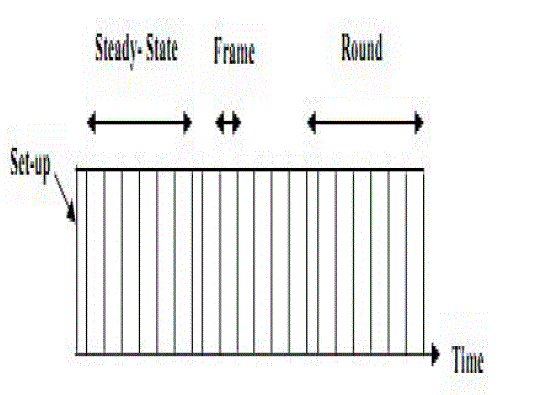
| LEACH is divided into rounds: |
| A .Set-up phase |
| B. Steady state phase |
SET-UP PHASE
|
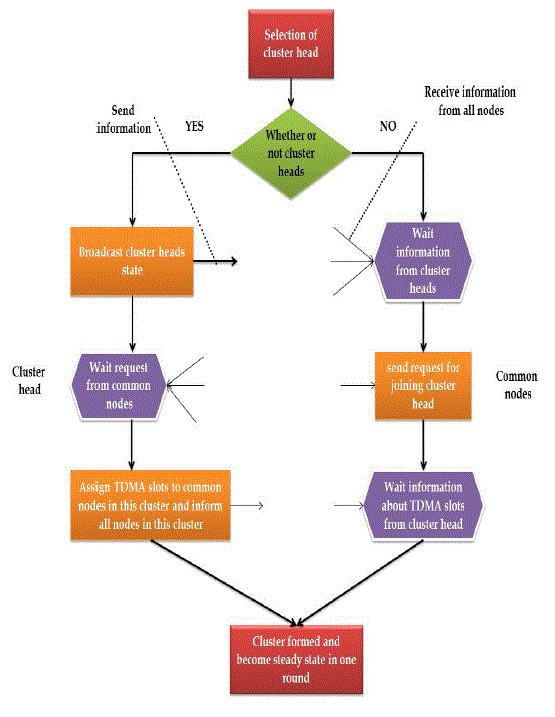
| Each node decides independently if it will become a CH or not. The decision takes into account the node that hasn’t been a CH for longer time is more likely to choose it-self rather than the nodes which have been a CH recently. By sending the advertisement packets or broadcasting the ADV messages to all non CHs, the CH informs that they become the cluster heads. With the strongest received signal strength, the non-CH nodes pick the advertisement packet. |
| The members nodes informs the CH, that they have become a member to that cluster by sending “join packet” contain their IDs using the CSMA. So, the CHs know or get the information about their member nodes and their IDs. On this basis of all received messages within the cluster, CH creates a TDMA schedule. Randomly pick a CSMA code, and broadcast the TDMA table to cluster members. After that steady state phase begins. |
A. STEADY STATE PHASE
|
| All the non-CH nodes start transmitting the data, after allotment of the TDMA slots, to the CH. The nodes will keep its antenna in ON state only when the data transmission begins. In the other time, it remains OFF in order to save power. The CH will always be in the ON state. Once all the information is received from the nodes (non-CH) by the CH, it does an intelligent data aggregation on the received data and sends it to the BS. |
DISADVANTAGES OF LEACH PROTOCOL
|
| LEACH suffers from many drawbacks which are: |
| 1. Random selection of the cluster head; that does not consider the energy consumption. |
| 2. Some cluster contains more number of nodes and some less. |
| 3. Unable to cover the large area. |
| 4. Non-uniformly distributed CHs; where some CH s is located at the edge of the cluster. |
| 5. Different size of the cluster, which leads to difference in the frequency of sending data from node to CH and CH to base-station, differs. |
RELATED WORK
|
LEACH-V
|
| In V-LEACH the cluster contains; CH (it is the responsibility of the CH towards sending data that is received from the cluster members to the BS), vice-CH (in case if the CH dies, the node will become the cluster head); cluster node (collects data from environmental surrounding and sends the data to the CH). But in original LEACH, the CH remains always in ON for receiving data from cluster members, aggregate the data and then send it to the base station, which might be located at a far distance from the BS. The CH dies earlier than other nodes because of the operations it performs of sending, receiving and overhearing. Hence the cluster will be useless and there will be no data transmission. It has the advantage that there will be no need of electing a new CH every time. |
LEACH-C
|
| LEACH doesn’t take the responsibility of the placement and the number of cluster heads. In this an enhancement over the LEACH was proposed. The protocol is known as the LEACH-C which uses a centralized clustering algorithm and after that following the same steady state phase as the original LEACH. At the time of set-up phase of LEACH-C, each and every node sends its current location and residual energy information to the BS. Once the energy cost of communication with BS become higher than energy cost of cluster formation. LEACH-C no longer performs good performance and dependence of BS location becomes a major disadvantage. |
LEACH-M
|
| It is an improved version of LEACH called multihop leach (LEACH-M). No matter the distance from the CH to BS, the CH communicates with the BS. So it will consume a lot of energy. The focus will be on the heterogeneous sensor networks, in which two types of sensors are displayed: Higher capacity sensor and simple sensors. The sensors which have large capacity processing capabilities and communicates very intensively and acts as cluster head, while others which are simple sensors have limited power, affiliated to the closest CH in their neighborhood and communicates with it directly |
LEACH-F
|
| In this proposed that, the number of clusters throughout the network is fixed. Cluster Head nodes can rotated within clusters of the same network. Here, data transmission phase is same as that LEACH. The energy consumption minimization is not fixed in this proposed protocol. It also violates the flexibility to mobility of sensor nodes and scalability of network. |
Energy-LEACH
|
| It makes the cluster head selection method efficient by making the residual energy of the cluster head nodes as vital factor. It decides whether these cluster nodes turn into the cluster head or not in the next round. Energy –LEACH will make better election process of cluster head nodes. This will results in longer lifetime and energy saving compared to conventional LEACH protocol. |
PROPOSED WORK
|
Energy –LEACH Protocol
|
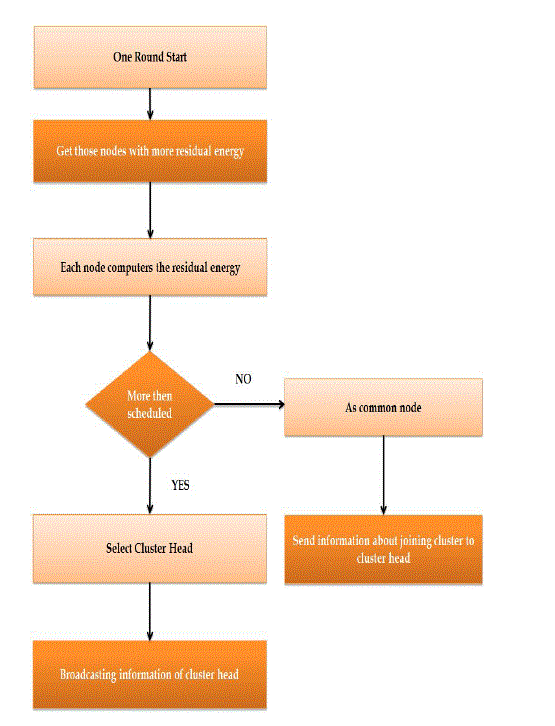
| Energy-LEACH protocol improves the cluster head selection procedure. It makes residual energy of node as the main matrix which decides whether these nodes turn into cluster head or not in the next round. In first round communication, every node has the same probability to turn into cluster head, n (n=p×N) nodes are randomly selected as cluster heads, and then, the residual energy of each node is different after one round communication. We select n nodes with more residual energy as cluster heads in next round communication, and so on until all nodes are dead. Same as the LEACH protocol, energy-LEACH protocol also divides into many rounds, and each round contains cluster formation phase and cluster steady phase. |
| (1) In cluster formation phase, each node decides whether to turn into cluster head or not by comparing with residual energy? |
| (2) Some nodes with more residual energy turn into cluster heads and send cluster head information to inform other nodes. The other nodes with less residual energy turn into common nodes, and send information about joining cluster to a cluster head? |
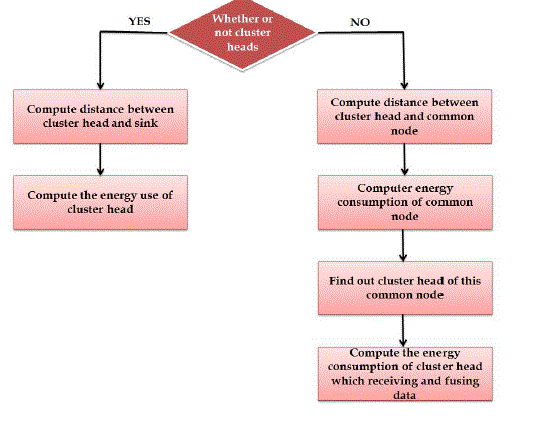
| (3) In cluster steady phase, nodes in a cluster send data according to TDMA table, and cluster heads receive, fuse and send data to sink. After a period of time, the network reforms the cluster head selection procedure in a new round. In cluster formation phase, the flow chart of whether a node turns into cluster head or a common node is shown in Figure. |
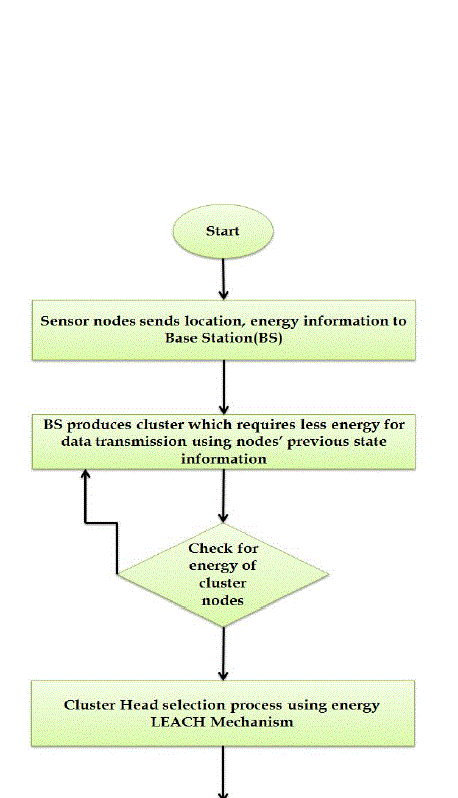
| The proposed work is designed to provide the energy efficient performance in such a way that it offers the advantages of the Energy –LEACH and Multihop-LEACH. It works like a Energy-LEACH in the first phase of Conventional LEACH (i.e. Cluster set-up phase) and it also provide the functionality of Multihop-LEACH in the Second phase of Conventional LEACH (i.e. Steady state phase) |
| The procedure of the proposed algorithm is shown in the flowchart and also elaborated First, all the nodes are linked in the network with the provision of the predetermined energy standard. Each node sends the location and energy information to the base station; it produces the cluster based on nodes current and previous state energy measures. After this the selection process carried out (i.e. set-up and steady state phase). This set-up phase follows the mechanisms of Energy-LEACH protocol and steady-state phase follows the mechanisms of Multihop-LEACH protocol. |
| After completion of each round, again the whole procedure starting from cluster head election and all other things carried out. |
CONCLUSION
|
| In this reviews paper, we have discussed conventional LEACH protocol for a Wireless Sensor Networks. This paper also gives brief introduction to the variants of LEACH protocol. The purpose of proposed approaches is to improve the Cluster Head Election process by modifying it. The simulation of proposed work is carried out using Network Simulator (NS-2.27). |
| |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
 |
 |
 |
| Figure 4 |
Figure 5 |
Figure 6 |
|
| |
References
|
- National Inst. Of Standard and Technology, “Federal Information Processing Standard Publication 197, the Advanced Encryption Standard (AES),” Nov. 2001.
- J. Daemen and V. Rijmen, “AES Proposal: Rijndael,” AES Algorithm Submission, Sept.1999.
- Jagadguru Swami Sri BharatiKrishnaTirthji Maharaja: Vedic Mathematics: Sixteen Simple Mathematical Formulae from the Veda, pp. 5-45. MotilalBanarasidas Publishers, Delhi (2009).
- Huddar, S.R.; Rupanagudi, S.R.; Kalpana, M.; Mohan, S., “Novel high speed Vedic mathematics multiplier using compressors,” in Automation, Computing,
- Communication, Control and Compressed Sensing (iMac4s), 2013International Multi-Conference on, vol., no., pp.465,469, 22-23 March 2013.
- William Stallings, Cryptography and Network Security, Principles and Practices, 4th ed. Pearson Education, pp. 134-161, 2006.
- Charlie Kaufman, Radia Perlman, Mie Speciner, Network Security, Private Communication in a Public World, 2nd ed. Pearson Education, pp. 41-114, 2006.
- T. K. Moon, “Rudiments of Number Theory and Algebra,” in Error Correction Coding Mathematical Methods and Algorithms, 1st Ed. New Jersey: John Wiley & Sons, 2005, pp. 175-188,193-209.
- Ahmad, N.; Hasan, R.; Jubadi, W.M; “Design of AES S-Box using combinational optimization”, IEEE Symposium on Industrial Electronics &Applications (ISIEA), pp. 696-699, 2010.
- Berent, Adam. “Advanced Encryption Standard by Example”, Document available at URL http://www.networkdls.com/Articles/AESbyExample.pdf (April 1 2007) Accessed: June 2013.
- Li, Hua, and ZacFriggstad. “An efficient architecture for the AES mixes columns operation.” Circuits and Systems, 2005.ISCAS 2005.IEEE International Symposium on.IEEE, 2005.
- Khandekar, P.D.; Subbaraman, S., “Low Power 2:1 MUX for Barrel Shifter,” Emerging Trend in Engineering and Technology, 2008. ICETET’08.First International Conference on, Vol., no., pp.404, 407, 16-18 July 2008.
- R.K.Bathija, R.S.Meena, S. Sarkar, Rajesh Shah Tinjrit, “Low power high speed 16*16 bit Multiplier using Vedic mathematics”, International journal of computer Application, volume 59, December 2012.
- Huddar, S.R.; Rupanagudi, Ramya R.; Yadav S.; Jan S., “Novel Architecture for Inverse Mix Columns for AES using Ancient Vedic mathematics on FPGA,” International Conference on advances in Computing, Communication and informatics (ICACCI). IEEE 2013.
- Ambika R, C. S. Mala, S. K. Pushpa, “FPGA Implementation of AES using Vedic Mathematics,” International Journal in Innovative in Engineering and Science, ISSN (Online) 2347-3207.
- Divan Raimagia, CharviChanda, “To make trust relationship between BGP speakers with help of secure private key”, Engineering (NUiCONE),2012Nirma University International Conference DOI: 10.1109/NUICONE.2012.6493249 Publication Year: 2012, Page(s): 1 - 7.
- Lovedeep Kaur, “Review for LEACH protocol|”, July2014, International Journal of Latest Scientific Research and Technology.
- Nikita Sehgal, Gurwinder Kaur, “Improved Cluster Head Selection Using Enhanced LEACH Protocol”, International Journal of Engineering and Innovative Technology (IJEIT) Volume 3, Issue 3, September 2013.
- Wu Xinhua, Wang Sheng, “Performance Comparison of LEACH and LEACH-C Protocols by NS2”, 2010 Ninth International Symposium on Distributed Computing and Applications to Business, Engineering and Science 978-0-7695-4110-5/10 © 2010 IEEE DOI 10.1109/DCABES.2010.
- S. H. Gajjar, K. S. Dasgupta, S. N. Pradhan, K. M. Vala, “Lifetime Improvement of LEACH Protocol for Wireless Sensor Network”, 2012 NIRMA UNIVERSITY INTERNATIONAL CONFERENCE ON ENGINEERING, NUiCONE-2012, 06-08DECEMBER, 2012 ,978-1-4673- 1719-1/12 © 2013 IEEE.
- Raj Kumar, Dr. Mukesh Kumar, “LEACH: Features, Current Developments, Issues and Analysis”, International Journal of Computer Science and Communication Engineering, Volume 1 Issue 1 October 2012.
- Kajal V. Shukla, “Research on Energy Efficient Routing Protocol LEACH for Wireless Sensor Networks”, International Journal of Engineering Research & Technology (IJERT) Vol. 2 Issue 3, March - 2013 ISSN: 2278-0181.
- M.Shankar, Dr.M.Sridar, Dr.M.Rajani, “Performance Evaluation of LEACH Protocol in Wireless Network”, International Journal of Scientific &Engineering Research, Volume 3, Issue 1, January-2012, ISSN 2229-5518.
- SudhanshuTyagi, Sumit Kumar Gupta, SudeepTanwar, Neeraj Kumar, “Enhanced heterogeneous LEACH protocol for life time enhancement of WSNs”, 978-1-4673-6217-7/13/$31.00c 2013 IEEE.
- NishitaPayar, Prof. Chandresh R. Parekh, “Ee-Leach(Low Energy Adaptive Clustering Hierarchy) Modified Protocol”, Int. Journal of Engineering Research and Applications, ISSN : 2248-9622, Vol. 4, Issue ( Version 7), May 2014, pp.05-10.
|