INTRODUCTION
|
| Nowadays, the multimedia data cover more and more application domains, ranging from Digital libraries, ECommerce, Home entertainment, News programs, Re- mote sensing, to Multimedia editing. The comprehensive set of audiovisual Description Tools provided by the MPEG-7 [14, 15, 17, 20] standard is to create the descriptions (which are in the form of hierarchy) of the multimedia contents in order to facilitate the needed effective and efficient access to multimedia contents. Since the security requirements of multimedia data are left open in the present MPEG-7, researchers and developers need to explore their own methods to protect the sensitive contents (elements) in the multimedia data. The properties of the multimedia data and web-based applications cause several special security requirements. Multimedia data usually contain huge amount of elements many of which may have different security levels (e.g. a medical education video should prevent the unauthorized users from identifying the patients’ identities), as a result, the security system must support multilayer access control. In addition, the multimedia data are frequently played in real time. Thus, the method of protecting the relatively small number of elements (such as patient's face) among the huge amount of elements should be very efficient in order to meet the real time requirement. Besides, more and more multimedia applications are in the distributed environment, it is desirable to assign the access privilege (permission) to the hundreds of thousands remote users automatically. And last, the ideal security system should take into account and make full use of theproperties of the descriptions (called metadata) provided by the MPEG-7. |
| Several research works can be found in the literature relating to multimedia access control [1, 2, 3, 5, 19]. Some of these works [2, 3] lacks the ability of protecting areas in the frames and some are specific to certain form of multimedia data such as video [1, 3, 5] or image [10]. Another common shortcoming of these works is that they are basically the mandatory access control (MAC) the administrative cost of which is relatively higher. Also, the filtering rules of these systems have to be applied to every sub object to determine which sub object(s) is (are) accessible, which is time-consuming. Moreover, they did not take the full advantages of the MPEG-7. |
| Web applications become wide-spread and more and more companies take the advantage of them to increase their revenues. Web and distributed databases play the key role in most of these Web applications and thus it is critical to protect them from unauthorized access and malicious attacks. Web and distributed database security has aroused many researchers interests. Because of the high accessibility, Web and distributed databases tend to be more vulnerable and expose to various attacks from wide variety of sources. To address this issue, a more efficient and flexible security mechanism is required to systematically authenticate users, control network traffic, and provide efficient fine-grained access control. Web and distributed databases need a strong authentication system. In the Internet environment, the possibilities of impersonation increase. The identity of a remote user must be verified based on his/her IP address, password, and credentials to combat the repudiation attack. Compared with Mandatory Access Control (MAC) and Discretionary Access Control (DAC), Role-Based Access Control (RBAC) has several superior properties. It simplifies the security management and administration, and provides more access control functions 12]. However, current RBAC model is not suitable for the fine-grained multilayer access control. In order to satisfy multilayer access control requirements in the current RBAC model, much more roles have to be introduced and different versions of a same object (each of which corresponds to a specific security requirement) have to be generated and stored, which not only significantly increase the administrative costs but also cause the datum integrity problem (e.g. when the content of the different versions of the same object are found to be inconsistent, it is difficult to decide. which one contains the correct content). Based on the above observations, a Criterion-Based RBAC (CB-RBAC) model is proposed to support the web-based multilayer access control in MPEG-7. In theproposed model, we introduce a number of new components which are the secure permissions (SP), secure objects (SOb), secure operations (SOp) and secure users(SU). A secure permission is made up of a secure object and a secure operation. A secure object is composed of a number of secure sub objects each of which is a sub object embedded with a security criterion expression (working as a lock) (in the proposed CB-RBAC model, secure object sand secure sub objects are semantic descriptions rather than multimedia data themselves). A secure operation is an operation associated with a security criterion subset (its elements work as the relevant keys of the corresponding secure object). A secure user is composed of a user and security criterion subset (SCSS) the elements of which can be thought as user’s available keys. To assign the remote users to the roles, the digital credentials [6, 7, 8] are adopted to establish the trust. In the user-role assignment process, the multilayer security related attributes in the digital credentials are translated into a security criterion subset (whose elements specify the user’s security features) which is combined with a user to form a secure user. |
| Under our Criterion-Based RBAC (CB- RBAC) multilayer access control model, a secure user who is the member of a role possesses all the secure permission(s) assigned to the role. When a secure object is within a user’s granted secure permission, he/she can efficiently access (in the mode specified by the secure operation within the same secure permission) only those secure sub objects whose embedded locks are actuated open with the common elements in secure user’s SCSS and the corresponding secure operation’s SCSS. |
| The rest of the paper is organized as follows. We first briefly introduce the MPEG-7 standard in Section 2. Then in Section 3, the CB-RBAC model is presented. Section 4 focuses on secure object and secure operation generations. The secure user-role assignment process and Compact-Secure-Role-SCSS cookies are discussed in Section 5. Section 6 explains how the multilayer access control and non-multilayer access control are achieved. And finally, Section 7 concludes the paper. |
INTRODUCTION OF MPEG-7 STANDARD
|
| The MPEG-7 standard provides tools for effectively and efficiently describing the audiovisual contents. Descriptors (Ds), Description Schemes (DSs), and Description Definition Language (DDL) are three main components of the standard. Descriptors are representations of distinctive characteristics of the data, which signify something(the features) to somebody. They define the syntax and the semantics of the feature representation. Description Schemes specify the structure and semantics of the relationships between their components, which may be both Descriptors (Ds) and Description Schemes (DSs). Description Definition Language (DDL) is used to define the syntax of the MPEG-7 Description Tools (Ds and DSs)to allow the creation of new Description Schemes and Descriptors and the extension and modification of existing Description Schemes. DDL is a superset of XML Schema in which array and matrix data types (both fixed size and parameterized size) and built-in primitive time data types(basic Time Point and basic Duration) are added. Depending on the different applications, MPEG-7 descriptions may be stored in a database or transmitted along with the data described. |
| Two MPEG-7 properties lay the foundation of the CB-RBAC model. First, the CB-RBAC model benefits from the fact that the segment description (semantic description) in MPEG-7 can be decomposed and organized into a tree structure. As a description allows to be decomposed into a number of different parts each of which corresponds to a multimedia entity through a multimedia content locator, it is possible for us to separate further-protection needed entities from non-furtherprotection- needed entities (These definitions will be given in Section 4).Another property that makes the CB-RBAC model possible is the extensibility of the Description Schema inMPEG-7. The allowed extension can be the creation of new Description Schema or the modification of the existing ones. This property facilitates the CB-RBAC in two aspects. On one hand, with the proper extension of the Description Schema, more kinds of multimedia entities scan be described and thus fine-grained security level can be achieved. On the other hand, the extensibility allows the graceful embedding of the security information. |
THE CRITERION-BASED RBAC (CB-RBAC) MODEL
|
| The proposed CB-RBAC model is an extension ofRBAC96 [21]. The components of objects, operations, permissions, and users in RBAC96 are enhanced to be secure objects (SOb), secure operations (SOp), secure permissions (SP), and secure users (SU) respectively in theCB-RBAC. A secure object is composed of a number of secure sub objects each of which is a sub object embedded with a security criterion expression (working as a lock).A secure operation is an operation associated with a security criterion subset (whose elements are the relevant keys with respect to the locks embedded in the secure sub objects of the corresponding secure object). A secure object and the relevant secure operation constitute a secure permission. A secure user is a user with a security criterion subset (SCSS) the elements of which specify the user's security features and can be regarded as the user's available keys. To achieve the multilayer access control, the embedded security information (security criterion expressions and security criterion subsets) and the normal Boolean operations are used. |
 CB-RBAC MODEL CB-RBAC MODEL |
| Figure 1 is the logical details of the proposed CB-RBAC model. The components in the model include: In the proposed CB-RBAC, S (a set of sessions), U (asset of users), R (a set of roles), Op (a set of operations),Ob (a set of objects), RH (role hierarchy), and the constraints are the same as those in RBAC96 model. A set of predefined security criteria plays an important role in the CB-RBAC model. A security criterion is a criterion used to specify the secure user’s security features and the object’s (and the sub object’s) security attribute(s). Each security criterion is represented by a Boolean variable denoted by is (The Boolean operations“^” (logic and), “_” (logic or), and “−” (negation) are applied to security criteria in this paper). |
| For example, a security criterion s3 can be defined to indicate the secure users of professional nurses. Whens3 or s3 is included in the description of a secure object(secure sub object) to specify its security attributes, the fact of whether a secure user is a professional nurse (e.g. whether s3 is used to specify the secure user’s security features) is considered to determine whether the secure user is allowed to access that secure object (secure sub object).A set of security criteria s1, s2, . . . , sn in an application domain is predefined according to the system security policy and the security requirements. The goal is that the security features of all kinds of secure users and the security attributes of all the possible objects and sub objects can be properly expressed with these security criteria. The total security criteria and their complements in an application domain form a security criterion set (SCS).Usually, plurality security criteria may be involved in specifying the security features of a user. These security criteria form a set (a subset of SCS, called security criterion subset (SCSS)) which is combined with the user to form a secure user. Another SCSS, which is associated with an operation, is made up of all the relevant keys with respect to the locks embedded in the secure sub objects of the corresponding secure object. |
| The security criterion expression (SCE) (work as a lock) embedded in a secure sub object is used to specify the security attributes of the secure sub object. A security criterion expression (SCE) is a Boolean expression in terms of security criteria, s1, s2, . . . , sn. |
| A secure sub object (SSO) is the combination of a sub object (a description of a multimedia element) and the embedded SCE which specifies the security attributes of that sub object. The existing partial order relations between the secure sub objects are called secure sub object hierarchy (SSOH):SSOH _ SSO × SSO. |
| A secure object (SOb) is composed of a number of secure sub objects which are organized in a tree structure(secure sub object hierarchy).The operations operate on secure objects are secure operations (SOp) each of which is an ordinary operation associated with a SCSS (called SOp’s SCSS) whose elements are made up of all the relevant keys (security criteria) with respect to the locks (SCE) embedded in the corresponding secure object: Sop _ Op × SCSS.A secure permission (SP) is an allowed access mode ofa secure operation (Sop) on a secure object (Sob): SP _Sop × Sob. A secure user (SU) is a user combining with a SCSS(called SU’s SCSS) whose elements specify the user’s security features: SU _ U × SCSS. |
| The new components Sob, Sop, SP, and SU are the enhanced versions of their corresponding counterparts in the RBAC96. The enhancement is transparent to the other components such as roles and sessions. As a result, the common administrative functions in the CB-RBAC system are identical (or very similar) to those in RBAC96. Note: The abbreviations SCE, SCSS, SOb, and Sopare used to present both singular and plural forms in this paper. |
SECURE OBJECT AND SECURE OPERATION GENERATIONS
|
| Secure Object Generation |
| In the CB-RBAC model, an “object” can be either a common object (A passive entity that contains or receives information) or a metadata element (a description of a multimedia entity). In MPEG-7, each description of a multimedia entity contains a multimedia content locator pointing to the corresponding multimedia entity and the accessing information (e.g. Time Point, Duration, and Quality etc.) to specify the accessing mode to the multimedia entity. Besides, the metadata (descriptions) and the corresponding multimedia entities have a one-to-one relation and they can always be assigned the same security attribute (level). Therefore, if a description is accessible (inaccessible), its corresponding multimedia entity is also accessible (inaccessible). In other words, a multimedia entity can be effectively protected by protecting its corresponding description. In the following discussions, all the objects and the sub objects refer to the descriptions (metadata) of the multimedia data unless they are indicated explicitly otherwise. |
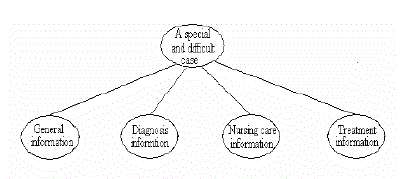 The original description tree of a multimedia Archive The original description tree of a multimedia Archive |
| Basically, objects (the same are the sub objects) can be classified into no-further-protection-needed objects to which all authorized users can access and further-protection-needed objects all or part(s) of which is (are)accessible only for those authorized users who have certain security features. In the original description tree of a multimedia file (object), if a leaf description node includes the description of multiple further-protection-needed sub objects or a furtherprotection- needed sub object and anon-further-protection-needed sub object, the description node must be decomposed further. The purpose of the decomposition is to guarantee that every further-protection needed sub object can be protected independently. As we discussed in section 2, MPEG-7 supports this kind of de composition. After the decomposition, a proper SCE is selected and embedded into each sub object of the description tree in the depth-first, post-order. A predefined table called the Content-SCE table is used to simply the SCE assignment to the leaf nodes. If the content of a leaf node belongs to a Group of further-protection-needed content in the Content-SCE table, the corresponding SCE of the Group of further-protection-needed content is adopted as that leaf node’s SCE. If the content of the leaf node does not belong to any Group of further-protection-needed content, the constant false, F, is adopted as the SCE for that leaf node (which implies that the leaf node is a non-further-protection-needed sub object). The SCE of each non-leaf node (interior and root) is formed by logic „OR’ of all of its direct children’s SCE (the results are simplified into the form of Sum of Products (SoP) with the products sorted according to the number of the products’ terms. Each record in the Content-SCE table contains two fields: Group of further-protection-needed content and Security criteria expression (SCE) which is created in ad once for a specific application domain by the following steps: |
| 1) Find out all the further-protection-needed sub objects in that application domain, which are the collection of all the possible further-protection-needed leaf nodes in all the objects. |
| 2) According to the system security policy and the content of the sub object, define the protection criterion combination for each further-protection-needed sub object in the form of SCE. |
| 3) Aggregate the further-protection-needed sub objects according to their corresponding SCE. That is, the furtherprotection- needed contents with the same CE are aggregated into the same group of further protection-need contents. |
| Note that all the SCE in Content-SCE table are of the form of Sum of Products (SoP) with the products sorted according to the number of the products’ terms. |
| Example 1 Suppose that a federated digital library contains multimedia archives about special and complicated medical cases which are referenced by doctors, nurses and researchers (special doctors). Every multimedia archive, properly described by the tools provided in MPEG-7, includes general, nursing care, diagnosis, and treatment information in the heterogeneous form (text, image, audio, and video). The descriptions of the multimedia archives provide the means for accessing the whole multimedia archive or its element(s) (The descriptions are used to represent the corresponding multimedia archives or their elements in the following discussion, which does not lose the generality). The original description tree of a multimedia archive is shown in Figure 2 (each node in the description tree corresponds to a piece of multimedia datum). |
| There are leaf nodes that describe multiple further protection-needed sub objects or a further protection needed sub object and a non-further protection needed sub object. These leaf nodes should be decomposed. To find out all the further-protection-needed contents (sub objects), we need to establish the system security policy.The security policy is derived from existing laws, ethics, regulations, and generally accepted practices. The multilayer access control related security policy is that different users (e.g. doctors, nurses and researchers) should be able to access only the useful and necessary information according to their positions and responsibilities. The system security policy of the Example 1 can be as follows. |
| 1) All of the secure objects (the multimedia archives and the corresponding descriptions) are accessible only to those secure users who are the member of the roles to which the secure permissions (which include those secure objects) have been assigned. |
| 2) Some contents of these secure objects are restricted to certain kinds of secure users. The contents and the corresponding restrictions in this example include: |
| a. The patient’s sensitive personal information(such as health card number) is only accessible to those nurses who are responsible for patient record administration. |
| b. Nurses are not allowed to access the contents of diagnosis and treatment. |
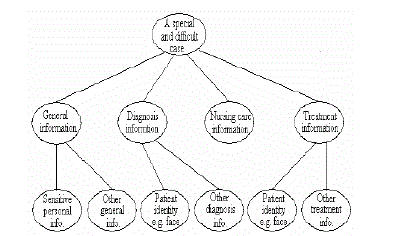 The decomposition of a multimedia archive description tree The decomposition of a multimedia archive description tree |
| c. Researchers are not able to access to the patient’s identity. Based on the above security policy, the possible furtherprotection- need contents (sub objects) can be generated. They are patient’s personal information, patient’s identity, diagnosis information (except identity),and treatment information (except identity). From the above security policy, we can also determine the relevant security criteria in this example: |
| 1) s1, indicating nurses who are responsible for patient record administration. |
| 2) s2, indicating researchers (special doctors). |
| 3) s3, indicating nurses. |
| 4) s4, indicating clinic doctors. |
| Thus, the security criterion set (SCS) of this example is {s1, s2, s3, s4, s1, s2, s3, s4}. The Content-SCE table, which includes all the further protection-needed contents and their related security criterion expressions (SCE), is produced (see Table 1) according to the system security policy. Note that the further-protectionneeded contents are integrated according to their SCE in the Content-SCE table.With the information of all the possible further-protection-needed contents (sub objects), the original description tree is decomposed further so that every further protection-needed content is described independently (see Figure 3). |
| From Table 1 and Figure 3, the secure object can be produced by embedding a SCE into each node according to the discussion above (see Figure 4). The number beside each node indicates the order in which the SCE are embedded. |
| Secure Operation Generation |
| To generate a secure operation, the corresponding security criterion subset must be generated first. The security criteria within a SOp’s SCSS are the collection of the security criteria appeared in the SCE of the corresponding |
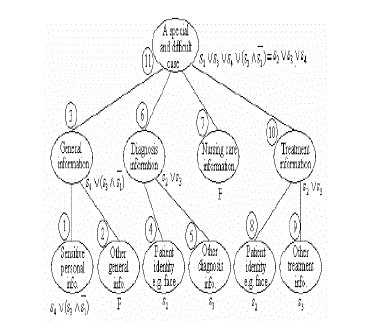 |
| The secure object of a medical multimedia Archive secure object. Hence the security criterion subset in a secure operation is made up of all the security criteria appeared in the SCE of the corresponding secure object. These security criteria are the relevant keys to determine the state of the SCE (locks) within the secure object. Each SOp’s SCSS corresponds to a specific secure object. The SOp’s SCSS of the secure object in Figure 4 is{s1, s2, s3, s4}. |
Achieving fine-grained access control
|
| In the Criterion-Based Access Control model, anThe security criterion expressions embedded in a secure object can be regarded as locks, while the security criteria in the security criterion subset can be considered as keys. When a secure user accesses a secure object, he/she uses the available keys to actuate the locks. Whether the secure user is allowed to access the secure sub object (the cell, column, or row) depends on the state of the corresponding locks. |
| A security criterion expression is evaluated in the following two steps. First, substitute all the security criteria in the security criterion expression with(sub) object’s security attributes and security level are implied by indicating users who do not have access rather than explicitly defining them. The system becomes simpler because one mechanism is used to define both the user’s security attributes and the (sub) object’s security attributes. |
| The security criterion expressions embedded in a secure object can be regarded as locks, while the security criteria in the security criterion subset can be considered as keys. When a secure user accesses a secure object, he/she uses the available keys to actuate the locks. Whether the secure user is allowed to access the secure sub object (the cell, column, or row) depends on the state of the corresponding locks. |
| A security criterion expression is evaluated in the following two steps. First, substitute all the security criteria in the security criterion expression with true, T, or false, F, according to the following rules: all the security criteria in a security criterion expression that also appear in the secure user’s security criterion subset have the value true, T, while other security criteria have the value false, F. Second, the security criterion expression is evaluated according to the normal evaluation procedure in Boolean algebra. The evaluation value T of a security criterion expression implies that users with security attributes specified by these security criteria are not allowed to access the corresponding secure sub object, according to the sub object’s security criterion expression transformed from the authorization rules. On the contrary, a false evaluation value, F, of the security criterion expression implies that the security criterion expression (actually the authorization rules) does not prevent these secure users from accessing this sub object |
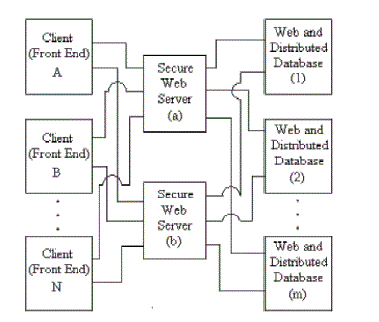 Logical Structure Of The Unified Data Base Logical Structure Of The Unified Data Base |
SECURE USER-ROLE ASSIGNMENT ON THE WEB
|
| It is the security administrator’s responsibility to assign secure users to roles and to generate the proper SCSS(which are embedded in the secure users to specify their security features) according to the system security policy and the users’ relevant characteristics. However, manually assigning users to roles and generating the prepress is a formidable task for the hundreds of thousands of the remote users in the web applications. A mechanism that can automatically generate the proper SCSS and assign the remote users to roles is of great importance. The mechanism requires a proper means to establish the trust between the remote secure users and the server(s). |
| Digital Credentials [9] are the digital equivalent of paper documents and other tangible objects traditionally used for establishing a person’s privileges, characteristics, identity, and so on. Users can establish trust in such away that only the needed attributes of the digital credentials are provided. When digital credentials are used for the purpose of the secure user-role assignment in the proposed CB-RBAC model, a set of security policies (authorization rules) provides the guide for the assignment and a Credential-criterion table specifies the mapping relations between the attributes of the credential and the security criteria (The relevant attributes of a user’s available digital credentials determine the elements (security criteria) of the security criterion subset associated with |
Digital Credential Based Security
|
| Policy for Secure User-role Assignment For each role in the system, the security policy must specify which digital credential(s) is (are) needed if a remote secure user is assigned to this role. The role hierarchy in CB-RBAC has exactly the same properties as that inRBAC96: senior role inheriting junior role’s permissions; junior role inheriting senior role’s users [22]. Because of the second property, authorization rules that are valid to assign a user to a senior role must also be valid to assign him/her to its junior roles. To simplify the set of the authorization rules, the rules specified for the senior roles need not be repeated for the junior roles; and the security policy (authorization rules) can be established for every role (to which secure users need to be assigned) from most senior roles to most junior roles. According to the authorization rules, a secure user is assigned to one or more roles based on his/her available credential(s) and request. Usually, the secure user is assigned to those role(s) which include(s) as much as possible permission according to the security policy and his/her available credential(s) to facilitate the subsequent transactions the user might perform. This strategy does not violate the least privilege principle, because the determination is made in each session to activate only the role(s) necessary for the user’s work. To simplify the discussion, we do not consider the possible existing constraints (which will not lose gener ality) about secure user-role assignment and define the assignable role(s) formally. |
| Definition 1 (Assignable role): According to the secure user's available digital credentials and the system security policy, all the roles to which the secure user can be assigned are called assignable roles with respect to that secure user. Suppose that a role hierarchy contains five roles for a digital library (see Figure 5). The credential group beside each role reflects the security policies for the secure user-role assignment. The secure permissions (SP) within each role are the secure permissions assigned to the role. If a remote secure user applies for a secure permission,SP4, the system checks the digital credentials provided by the user and assigns him/her to the proper role(s) in the following steps: |
| 1) Find out the role(s) ri(i = 1, 2, . . .) that contains(contain) the applied secure permission. In this ex ample, we get role2. |
| 2) If ri(i = 1, 2, . . .) or any of its (their) ancestor role(s)is (are) assignable role(s), go to 3; otherwise go to4. For this example, if C4^C5 or C4^C6 is provided,role2 is assignable; if C11^C12 is provided, role5, the role2’s parent, as well as role 2 is assignable 3) If there is an assignable role r which is the ancestor of all the other assignable roles, the secure user is assigned to this role r. For example, if the user provides C4 (medical member credential), C6 (master card credential), C11 (VIP member credential), andC12 (specialist credential), he/she is assigned to role5(The relevant assignable roles are role2 and role5.Role5 is the parent of role2).Otherwise, the user is assigned to those assignable roles or any of its (their) ancestor role(s)) which haveno parent assignable roles. For example, if a secure user provides C1, C4^C5, and C7 to apply the secure permission SP3, he/she will be assigned to role2 androle3 (The assignable roles are role1, role2 and role3.Role2 and role3 have no parent assignable roles). |
| Refuse the user’s application. |
| In the above process of the secure user-role assignment, those digital credential attributes which refer to multilayer access control need to be translated into a SCSS to specify the secure user’s security features. To record these attributes, the system stores a table (Credential-criterion table) which maps the multilayer security related attributes of every digital credential to the corresponding security criteria. Table 2 is an example of the digital credential C4 which has three multilayer security related attributes: “Profession”, “Administration on patient’s record”, and “Research”.When a remote secure user submits C4 and C6 to apply for the secure permission SP4 (whose secure objectis shown in Figure 4), if the “Profession” attribute of C4is “Doctor”, the “Administration on patient’s record” attribute is “No”, and the “Research” attribute is “No’, thesecure user will be assigned to role 2 and his/her SU’Sscss is {s1, s2, s4}. z |
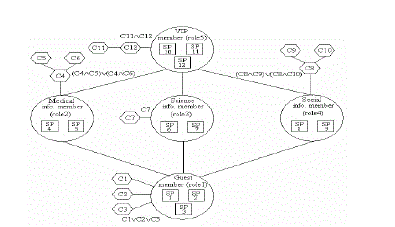 The digital credentials for remote secure user role assignment in Example 1 The digital credentials for remote secure user role assignment in Example 1 |
MULTILAYER AND NON-MULTILAYER ACCESS CONTROLS IN CB-RBAC
|
Multilayer Access Control
|
| In CB-RBAC, a secure user is granted secure permissions in the same way as a user is granted permissions in RBAC96. The secure user possesses all the secure permissions assigned to the roles of which he/she is a member. When he/she accesses to a secure object (which is in one of his/her granted secure permissions) in the mode defined in the corresponding secure operation, he/she can only access those secure sub objects whose embedded SCE(locks) are actuated open by the common security criteria in his/her SCSS (available keys) and the corresponding Sop's SCSS (relevant keys).The procedure of determining whether a secure sub object (SSO) should be protected is performed by evaluating its embedded SCE according to the common elements in the corresponding Sop's and SU’s SCSS. The evaluation of a security criterion expression (SCE) can be done by the following two steps. First, substitute all the security criteria in the SCE with true, T, or false, F, according to the following rules: all the security criteria in SCE that are not the common elements in Sop's SCSS and SU’s SCSS have the value of false, F; and all the security criteria appear in SCE and the intersection of Sop's SCSSand SU’s SCSS have the value true, T. Second, the SCE is evaluated according to the normal evaluation procedure in Boolean algebra. For example, if the common elements of Sop's SCSS and SU’s SCSS are s1, s2 and s3, the evaluation values of the expressions s1 _ s4, s1 ^ s2, s2 ^ s3,s2 _s4, and s3 ^s4 are T _ F=T, T ^ F = F, T ^ T = T,F _ F = F, and T ^ F = F respectively. The true, T, evaluation value of a SCE implies that the protective criteria of the corresponding secure sub object (SSO) are satisfied and the secure sub object is not accessible. On the contrary, when the evaluation value of the SCE is false, the criteria of protecting the related secure sub object are not contented and the secure sub object is accessible. |
| The multilayer access control is achieved by traverse the SOb in the depth-first preorder. Each SCE is evaluated by the common elements in the related SOp’s andSU’s SCSS. Note that whenever the evaluation value of a node (secure sub object) is false, F, the children of that node need not be evaluated (which are called early termination) and the node as well as its child nodes are accessible. Especially, if the root is evaluated false, F, (which means there are no furtherprotection- needed sub objects in that Sob), all the rest nodes in the Sob need not be evaluated. In addition, the evaluation of each SCE is performed in such a way that all its products are evaluated one by one from shorter-termproduct to longer term-product and the short-circuit evaluation is adopted, which raises the efficiency in two aspects. On one hand, since the security criteria not in the intersection of SOp’sSCSS and SU’s SCSS always have the value of false, F, in aSCE when the SCE is evaluated and all the SCE are in the form of Sop and their products had been sorted according to the number of the terms (criteria) in these products, the products whose number of terms (criteria) is larger than the number of the common elements in Sop's SCSSand SU’s SCSS will always be evaluated as false, F. Therefore, these products whose number of terms is bigger than the number of the common elements of Sop's SCSS andSU’s SCSS need not be evaluated. On the other hand, the evaluation process can stop whenever one product (whose term number is smaller or equal to the number of the common elements of Sop's SCSS and SU’s SCSS) in a SCE is evaluated true, T, (which results in the evaluation value of the whole SCE true, T). The above properties usually can reduce the computational expense significantly. It is time to explain why the intersection of a secure operation's and a secure user’s SCSS is used to evaluate the corresponding secure object instead of using the secure user’s SCSS only. Note that the elements of a secure user's SCSS are user’s available security criteria many of which may have nothing to do with the SCE evaluation of a specific SOb. This means that there may be some redundant elements in the secure user’s SCSS with respect to a specific secure object. Because the redundant security criteria increase the computational expense in the process of the SCE evaluation, we eliminate them by using the intersection of a secure operation’s and asecure user’s SCSS. For example, a secure user’s SCSS is {s1, s2, s3, s4, s6} and the secure operation’s SCSS is {s5, s6, s7, s8, s9}. If {s1, s2, s3, s4, s6} is used to evaluate SCE, s5 _ (s6 ^ s7) _ (s7 ^ s8 ^ s9), every term of the SCE has to be evaluated. If the intersection of the two SCSS {s6} is used to evaluate the same SCE, according to the shortcircuit evaluation discussed above, only the first product s5 needs to be evaluated to get the evaluate ion value of the whole SCE.In Example 1, when a remote secure user applies for the secure permission SP4 with digital credentials C6 (which has no multilayer security related attributes) and C4(whose multilayer security related attributes are shown in Table 2), the user is assigned to the role2 with theSCSS, {s1, s2, s4}. The secure operation’s SCSS in theSP4 is {s1, s2, s3, s4}. Thus, {s1, s4} should be used to evaluate the corresponding secure object. the result (the shaded nodes are inaccessible (partially or completely) to this secure user). Note that the SCE of the nodes 4, 5, 8, and 9 are not evaluated because the early termination in nodes 6 and10 (their SCE evaluation values are “F”). |
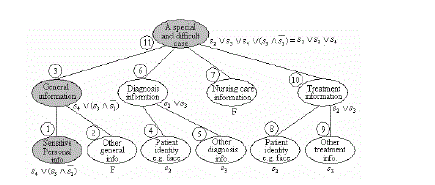 The accessible and inaccessible sub objects of multimedia archive The accessible and inaccessible sub objects of multimedia archive |
The Non-multilayer Access Control
|
| In the proposed CB-RBAC model, every SCE within sob is a fixed expression unless the contents of the description or the system security policy changes. The security levels of its secure sub objects are determined by the embedded SCE as well as the common elements in the related Sop's and SU’s SCSS. When there is no common elements in the related Sop's and SU’s SCSS, none of the secure sub objects in the related Sob needs further protection (because all the SCE in the Sob are evaluated false), which means that all the security criteria specifying secure user’s security features have nothing to do with the evaluation of SCE of that Sob. Especially, when aSU’s SCSS is set to NULL, the non-multilayer access control is achieved for that secure user. |
| The proposed model also supports the non-multilayer access control for multiple secure users. By embedding the constant “F” into the root of those objects which donot include any further-protection-needed sub object, the special secure objects are formed. When these secure objects are accessed, the evaluation value of their roots are false, F, which results in that the whole secure objects are accessible. As a result, the non-multilayer access control is achieved for all the secure users. |
CONCLUSION
|
| This paper presents a CB-RBAC model to support web based multimedia multilayer access control in MPEG-7 by introducing the secure users (SU), secure objects(SOb), secure operations (SOp) and secure permissions(SP). The proposed model takes advantage of the properties of MPEG-7 standard to generate a secure object by embedding a security criterion expression (SCE) into each of its sub object (a multimedia semantic description). A secure operation is created by associating a security criterion subset (its elements are the collection of security criteria appeared in the SCE of the corresponding Sob)with an ordinary operation. Similarly, a secure user is the user combining with a proper SCSS.With the cooperation of a secure user, a secure operation and a secure object, the multilayer access control is achieved through a powerful but simple mechanism. A secure sub object’s security level depends not only on the embedded security criterion expression (SCE) but also on the common elements of the relevant Sop's and SU’s SCSS, which results in flexible multilayer access control system. In addition, the method of using digital credentials and Compact-Secure-Role-SCSS cookies is effective and secure for web-based applications. Addressing network security and database security simultaneously leads to efficient unified security system. The information used for authentication can be reused for the preliminary access control and fine-grained access control. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
 |
 |
 |
| Figure 5 |
Figure 6 |
Figure 7 |
|
References
|
- W. Aref, M. Hammed, A. C. Catlin, L. Llyas, T.Ghanem, A. Elmagarmid, and M. Marzouk, “Video query processing in the VDBMS tested forvideo database research,” in Proceedings of the First ACMInternational Workshop on Multimedia Databases, pp. 25-32, New Orleans, LA, USA,2003.
- E. Bertino, E. Ferrari, and A. Perego, Max: An Access Control System for Digital Li-braries and the Web, http://semioweb.mshparis.fr/euforbia/download/max.pdf
- E. Bertino, M. Hammad, W. Aref, and A. Elmagarmjd, “An access control model for video database systems,” in Proceedings of the NinthInternational Conference on Information and Knowledge Management, pp. 336-343, McLean, Virginia, United States,2000.
- E. Bertino, P. A. Bonatti, and E. Ferrari, “TRBAC:A temporal role-based access control model,” ACM Transactions on Information and SystemSecurity(TISSEC), vol. 4, issue 3, pp. 191-233, Aug. 2001.
- E. Bertino, J. Fan, E. Ferrari, M. S. Hacid, A. Elmagarmjd, and X. Zhu, “A hierarchical access control model for video database system,” ACMTransactions on Information System, vol. 21, no. 2, pp. 155-191, 2003.
- M. Blaze, J. Feignhbaum, and J. Lacy, “Decentralized trust management,” IEEE Symposium on Security and Privacy, pp. 17-28, Oakland, CA,May 1996.
- M. Blaze, J. Feignhbaum, and A. D. Keromytis,“KeyNote: Trust management of public-key infrastructures,” in Security Protocols, 6thInternational Workshop, pp. 59-63, Cambridge UK, 1998.
- M. Blaze, J. Feignhbaum, J. Ioannidis, and A. D.Keromytis, The KeyNote Trust Management System, Version 2, Internet Drafft RFC 2704, Sep.1999.
- S. Brands, A Technical Overview of Digital Credetials, http://www.xs -4all.nl/#brands/,1999.
- E. Fernandez-Medina, G. Ruiz, and S. De CapitanidiVimerati, “Implementing an access control system for SVG documents,” in Lecture Notesin Computer Science, pp. 741-753, Catania, Italy, 2003.
- A. Freier, P. Karlton, and P. Kocher, The SSL Protocol Version 3.0, internet Draft, Mar. 1996.
- V. Gligor, “Characteristics of role-based access control, symposium on access control models and technologies,” in Proceedings of the FirstACM Workshop on Role-based Access Control, no. 10, pp. 9-14, Gaithersburg, Maryland, United States, 1996.
- HTTP Cookies: http://www.netsc -ape.com/newsref/std/cookies spec.html.
- ISO/IEC JTC1/SC29/WG11N5525, MPEG-Overview (Version 9),http://www.chiariglione.org/mpeg/standards/mpeg7/mpeg-7.htm
- H. Kosch, Distributed Multimedia Database Technologies Supported by MPEG-7 and MPEG-21, CECPress, Boca Taton London, New YorkWashington, D.C., 2004.
- D. M. Kristol, L. Montulli, HTTP State Management Mechanism, Draft-ietf-http-state-man-mec.txt, 1999.
- B. S. Manjunath, P. Salembier, and T. Sikora, Introduction to MPEG-7 Multimedia Content Description Interface, John Wiley & Sons, Ltd.,2002.
- K. Moore, and N. Freed, Use of HTTP State Management, Draft-ietf-http-state-man-mec-12.txt.
- L. Pan and C. N. Zhang, “Using metadata to protect the audiovisual contents in MPEG-7 applications, in SAM‟04, pp. 287-293, Las Vegas,Nevada, USA, 2004.
- P. Salem bier and J. R. Smith, “MPEG-7 multimedia description schemes,” IEEE Transactions on Circuits and Systems for Video technology,vol. 11, no. 6, pp.748-759, 2001.
- R. Sandhu, E. Coyne, H. Feinstein, and C. Youman,“Role-based access control models,” IEEE Computer, vol. 29, no. 2, pp. 38-47, 1996.
- R. Sandhu, V. Bhamidipati, and Q. Munawer, “TheARBAC97 model for role-based administration of roles,” ACM Transactions on Information and Systems Security (TISSEC), vol. 2, no. 1, pp. 105-135,1999.
|