INTRODUCTION
|
| MANETS are the self-controlled and organizing groups consists of mobile nodes which can also acts as wireless connectors from one node to other to maintain a big network with big topology. It does not have any infrastructure means there will be no main/ central node. As in the recent trends advances in the wireless communications, the usage of either mobile or wireless networks has increasing gradually and also took a vital role in the various services like at Military, at disaster timings, at different monitoring sections etc., |
| In the MANETS main the drawback is topology changes which will cause the routing problem while communicating from one node to other. Along with these drawbacks some other limitations in MANETS are Limited capabilities of the mobile nodes, Limited battery consumption etc. The main limitation here we discuss about the time computation and the communication resources, while mobility of nodes are there. One of the important factor while designing the wireless or mobile networks is to know how the distributed algorithms are used to deploy the nodes carefully for the better performance based on the application. |
LIMITATIONS OF THE EXISTING ROUTING PROTOCOLS FOR MANETS
|
| In general we have three types of protocols. They are Proactive, Reactive and Hybrid Protocols. In the Proactive Protocol the control packets will send periodically to update the routing tables, by this the network becomes more typical and occurrence congestion in the network. Reactive Protocols used for the route discovery using control packets. The hybrid protocol is the combination of the both reactive and the Proactive protocols. Therefore the performance of both the protocols degrade when the network becomes highly dynamic due to the movements of the nodes, which will increase the packet delay and network congestion. Generally we have four different routing protocols use for the ADHOC networks. They are 1. DSDV Direct sequence distance vector routing protocol, it is the distance vector routing protocol which is a table driven routing protocol based on the BELLMAN-FORD algorithm mechanism. Those will also include the loops in the routing table. In the every table it maintains the information about the next hop, frequency table etc., |
| The On-demand routing protocols are the AODV (Adhoc On demand Distance vector), DSR (Dynamic source Routing), and TORA (Temporally Ordered Routing Algorithm) which share the on demand behavior by this they will initiate the routing activity only on the presence of data packets. Their routing mechanism is different. In AODV the table driven routing framework and the destination sequence numbers of the nodes will be maintained. In DSR uses the source routing. And the TORA uses the link reversal mechanism for routing purpose. Those have less routing load and less end –to- end delay. |
| Some factors may be used for analyzing the performance of the existing routing protocols |
Mobility of the Modes from one topology to other:
|
| If the nodes starts to move with high speed, the performance of all known routing protocols getdegraded. As the nodes will have to change their routing table (is they use proactive protocols) or it willbecome extremely difficult to deliver packet to the node because of the uncertainty of its position. |
Congestion control:
|
| Proactive protocols cannot be used, as the nodes keep on changing and so do the topologyof the network, so the control messages (which will be generated continuously to keep track of theposition of the nodes) will bring the network to its knees as a result of congestion. |
Power consumed:
|
| The mobile nodes run on battery power, so we have limited amount of power to route packetsand deal with the changing topology of the network. |
Packet delivering time:
|
| If we use reactive protocols the packet delivery time will increase since we haveto find the route on demand. So the whole process will be too slow. |
Security issues:
|
| Since the nodes are mobile and there is no central authority to authenticate nodes, nodeauthentication is an important problem in ad hoc networks. Various kind of attacks are possible likepacket sniffing, man in the middle attack, node impersonation etc. |
Number of nodes to be used:
|
| As the number of nodes increases it becomes difficult to route the packets, since it becomes difficult to keep track of the nodes. |
Packet Injection Rate:
|
| It refers to the rate at which each node is injecting packet in the network. If thisis quite high then the network becomes congested easily. |
| To Enhance the Performance in AD-Hoc networks A Method is proposed |
| Generally a mathematical formula is used for the trajectory that consists of taking successive steps to Random walk. So the similar analysis is applied to the computers, technology, science, ecology etc. to know the processing time for the task to be completed. For instance, A node can trace it’s by using various routing algorithms and table and can form a topology leaving old group and moving to new group. This process can takes place randomly. Various properties are included in Random Walks like dispersal distributions, first-passage times and encounter rates, have to be studied extremely. |
| We have different types of random walks which will be more complicated like graphs, others on the line and plane or with higher dimension or with groups. RW also vary with time parameter. |
LAS VEGAS ALGORITHM
|
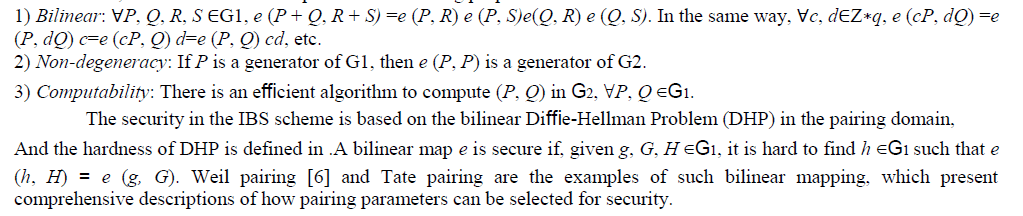
| It the randomized algorithm which will give the exact and accurate results i.e., which gives the information that it is failure. It means it does not verify the results, it only uses the resources for calculating Let us consider ‘A’ be the randomized algorithm which gives the answer, and we assume that ‘A’ is the Las Vegas Algorithm for the function F if for every input of ‘x’: |
 |
 |
| Proposed and Expected protocol which is called by the routing agent calls it will receive function as a handler of thepacket received from the upper layer. It uses special headers to find the immediately next hops bybroadcasting specially designed small control packets with range determined as single hop. The benefitof using single hop is to reduce congestion in the network. As soon as the send function is called, a timeris started in the background to maintain the queue. This queue is used to store addresses of the single hopneighbors that reply to the broadcast. The addresses are enqueued until the timer expires. Once the timerexpires check queue function is called, it dequeues the queue and check if the destination node is in therange. Like this it finds the all the next hops up to destination. If it finds the destination in its next hop then it immediately transfer the packet to the destination or else it will built the random function which calls and selects the node at random from the queue and then the packet will be forwarded. Computing the Running Time (Assumption) |
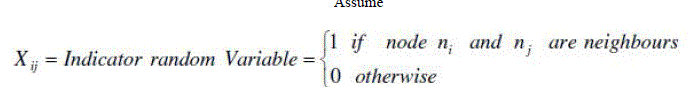 |
| When T=0 all the nodes will broadcast the information at one hop to calculate cost metric from their neighbor nodes Let Dij is the distance from two nodes i, j. There will be a function ‘f’ which will give the probability of the cost metric of the two nodes be n i and n j and at the time T=t and X=d |
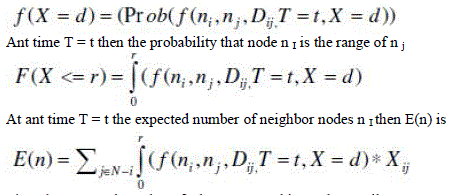 |
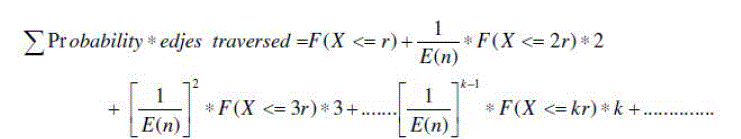 |
| Here the function ‘f’ follows the Poisson distribution because every event is independent and has the probability is fixed and equal. As the time “T” increases then the number of movements becomes infinity which will satisfy the criteria of Poisson distribution which shows that there will usage is in iteratively use of random algorithm which results in implementation which have the run time of O(R A), where the RA is the runtime in the Las Vegas Random Algorithm. |
ANALYSIS
|
| For the simulation of the any network scenario NS2 will be used. First of all the nodes are created using the Tcl script and the initial position are fixed. The traffic type to be simulated on the networkis attached to the node via transport layer agent. On top of this transport layer agent the application layeragents like CBR or FTP are attached. Since the proposed protocol deals with only routing, the majorconcern is only with layer three simulations and implementation. With routing strategies (i.e.) the routingof the packets received from the upper layer or previous hop and delivers them at the destination nodewith no guarantee. Functionalities of other layers are taken care of by the upper and lower layer agents ofNS-2. A node can only act as a source or sink at application layer level. The agent acting as source willgenerate traffic at application layer. This traffic is transferred to the transport layer which further attachesits own transport header to it. This packet is then received by RTagent after it has been de-multiplexed bythe Demux agent. The RTagent is responsible for delivering it to the routing layer. The network layeragent, if busy enqueues this packet upon receiving whereas it calls the recv(receive) function if free. The receiver function consists of two arguments among those one is Packet Pointer and the other one is Packet Handler. In the Network layer the predetermined routing protocols will be used those are registered using Tcl Scenario. |
CONCLUSION
|
| In this we discuss about the routing protocols which will be used for the routing in AD-Hoc network. By using those what will be the drawbacks like routing tables will be maintained and the some delay will be there for the immediate updating of the next hops. To overcome this Las Vegas Algorithm is used for the packet forwarding from the source nodes to destination node.Oblivious routing is atype of distributed routing suitable for dynamic packet arrivals. In oblivious routing, the path for a newlyinjected packet is selected in a way that it is not affected by the path choices of the other packets in the network. Gives an existential result that shows that for any network there exists an oblivious routingalgorithm with congestion within factor log3 n from that of the optimal off-line centralized algorithm,where n is the number of nodes. This oblivious algorithm constructs a path by choosing a logarithmicnumber of random intermediate nodes in the network. |
| |
References
|
- M.S. Corson, J. Macker, Mobile ad hoc networking: routing protocol performance issues and evaluation considerations. Internet RFC January1999, http://www.ietf.org/rfc/rfc2501.txt.
- M.S. Corson, J.P. Macker, G.H. Cirincione, Internet-based mobile ad hoc networking,IEEE Internet Computing (4) (1999) 63±70
- Charles E. Perkins and PravinBhagwat. Highly dynamic Destination-Sequenced Distance-Vector routing (DSDV) for mobile computers. InProceedings of the SIGCOMM ’94 Conference on Communications Architectures, Protocols and Applications, pages 234–244, August 1994. Arevised version of the paper is available from http://www.cs.umd.edu/projects/mcml/papers/Sigcom m94.ps.
- C. PerkinsAd hoc On-Demand Distance Vector (AODV) RoutingRFC3561[ S]July 2003
- David B. Johnson, David A. Maltz and Yih-Chun Hu. The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks. Internet-Draft,draft-ietfmanet- dsr-10.txt, July 2004
- Vincent D. Park and M. Scott Corson. Temporally-Ordered Routing Algorithm (TORA) Version 1: Functional specification. Internet-Draft,Draft-ietf-manet-tora-spec-00.txt, November 1997.
- Yuan Peiyan , LI Layuan , Performance Evaluation and Simulations of Routing Protocols in Ad Hoc Networks, BWAN’06, InternationalWorkshop on Broadband Wireless Access for ubiquitous Networking, September 20, 2006, Alghero, Italy
- AzzedineBoukerche, Performance Evaluation of Routing Protocols for Ad Hoc Wireless Networks, Mobile Networks and Applications 9, 333–342, 2004 Kluwer Academic Publishers. Manufactured in The Netherlands.
- J.Hromkovic, Design and Analysis of Randomized Algorithms, Springer 2005.
- "Las Vegas algorithm", in Dictionary of Algorithms and Data Structures [online], Paul E. Black, ed., U.S. National Institute of Standards and Technology. 17 July 2006.
|