Keywords
|
| Quick response, Discrete-Wavelet Transform, Discrete-Fourier-Transform, discrete cosine-transform, singular-value decomposition |
INTRODUCTION
|
| Two important requirements in watermarking are perceptual transparency and robustness [1]. Transparency means that watermark should neither be noticeable to the viewer nor should introduce a significant degree of distortion in the host image. Robustness refers to the ability of watermark to resist intentional or unintentional image modifications such as filtering, geometric transformations, noise addition, etc. [2]. |
| The large number of digital multimedia data transmitted over internet through various applications which requires more security and authenticity due to rapid growth of multimedia and internet technology. The rapid expansion of the Internet and digital technologies in the past years has sharply increased the ease of the production and distribution of digital media [3]. The main idea of steganography is the embedding of secret information into data under the assumption that others cannot know the secret information in data. The main idea of watermarks is to check the logo embedded in data or not [4]. In this, the data hiding process is more important. Data hiding shows processes used to embed data, such as copyright information, various companies important documents etc. transfer over internet link and convert into various forms of media such as image, audio, or text with a minimum amount of perceivable degradation to the “host” signal; so that embedded data should be invisible and inaudible to a human observer, So that data can be prevent. Its goal is not to restrict or regulate access to the host signal, but rather to ensure that embedded data remain inviolate and recoverable. Data hiding in audio signals is especially challenging, because the human auditory system (HAS) operates over a wide dynamic range. The HAS perceives over a range of power greater than one billion to one and a range of frequencies greater than one thousand to one [5]. |
| Based on the type of document to be watermarked Text Watermarking: Line shift coding, word shift coding, feature coding. Visible Watermark: The information is visible in the picture or video. Typically, the information is text or a logo which identifies the owner of the media. Invisible Watermark: An invisible watermark is an overlaid image which cannot be se en, but which can be detected algorithmically. Dual Watermarking: Dual watermark is a combination of a visible and an invisible watermark. In this type of watermark, an invisible watermark is used as a backup for the visible watermark [4]. |
| QR Code is a type of 2-D (two-dimensional)Symbology developed by Denso Wave (a division of Denso Corporation at that time) and released in 1994. It is capable of handling all types of data, such as numeric and alphabetic characters, Kanji, Kana, Hiragana, symbols, binary, and control codes. Up to 7,089 characters can be encoded in one symbol. It has large Kanji- and Kana-holding Capability, and has error correction capability. Data can be restored even if the symbol is partially dirty or damaged [6]. In this paper, we present various method of watermarking depending upon the different technology based on QR Code. |
RELATED LITERATURE
|
| Mahasak Ketcham et al., [1] have proposed QR Code embedded technique for invisible watermarking by using DFT compare with DWT. The DFT allows a QR Code image to be broken up into different frequency bands by using blocks DFT that comparison between low-band coefficients and the DWT that use Haar Wavelet Transform method hierarchically decomposes a QR Code image into a series of successively lower frequency approximation sub band and their associated detail sub bands. Thitapa Poomvichid et al has proposed audio based data hiding by applying the QR Code technique and using an AI technique achieved the quality of this technique was watermarked image and the Sim value of the extracted watermark after certain attacks will be poor. The inaudibility and robust performance can be achieved. Shanjun Zhang et al., [3] have proposed a robust method of embedding QR code into the DWT domain of divided blocks of the still image. This technique was embedded information and extracted correctly even if the images are compressed to less percentage of the original according to the contents of the images. Ray-Shine Run et al., [4] has proposed reliable SVD-based image watermarking. It was solving the ambiguities situation and the false positive problem and he gets the best PSNR value. |
| Ahmad A. Mohammad et al., [5] has proposed SVD based watermarking algorithm for ownership protection. This proposed algorithm was more robust and solves the false-positive detection flaw in most SVD-based techniques. Bai Ying Lei et al., [6] has proposed a blind and robust audio watermarking technique combined with SVD, DCT and synchronization code technique achieves very low error probability rates. With traditional and SVD based algorithms show better performance from our algorithm. Veysel Aslantas et al., [7] has proposed optimal robust image watermarking technique based on SVD using the differential evolution algorithm effectively to improve the quality of the watermarked image and the robustness of the embedded watermark against various attacks. Chin-Chen Chang et al., [8] has proposed SVD-based watermarking scheme a good performance of the proposed scheme both in robustness and security can be achieved. Fangjun Huang et al., [9] has proposed watermarking method was combinesthe SVD and DCT. It was should achieve the highest possible robustness without degrading image quality. |
CLASSIFICATION OF WATERMARKING
|
| In this section, the detail classification of watermarking scheme can be explain and given as follows. |
| 1) Digital Image Watermarking: In present scenario most of the research in digital watermarking is focused on image watermarking. There might be many reasons behind it such that as these days many images are available on the internet at free of cost without any copyright protection mechanisms [7]. |
| 2) Digital Video Watermarking: A video sequence consists of still images therefore all the watermarking Methods applied on image could also be applied on video sequences [7]. |
| 3) Digital Audio Watermarking: In case of audioSignals, “watermarking” can be defined as follows “Robust and inaudible transmission of additional data along with audio signals”. Audio watermarking is based on the Psychoacoustic approach of perceptual audio coding techniques [7]. |
| Another classification of watermarking system is based on the domain in which the watermark is embedded. If watermark is embedded by modifying the intensity value of the pixels then it is called spatial domain watermarking, if the frequency coefficients are changed then it is called transform domain watermarking system. Many transformation techniques are used for transforming image from spatial to frequency domain which includes Discrete Fourier Transform (DFT), discrete cosine Transform (DCT), Discrete wavelets transform (DWT) and Discrete Hadamard Transformation (DHT) [7]. |
METHOD
|
| A .QR Code |
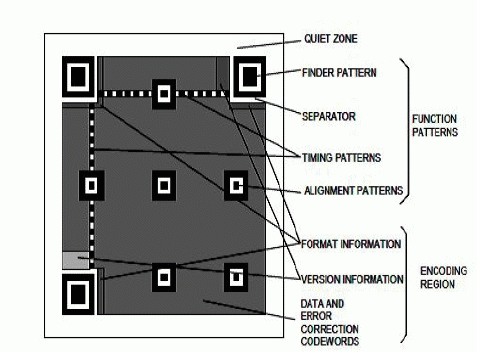
| QR Code is a matrix symbol that consists of an array of nominally square modules arranged in an overall square pattern. QR Code includes unique finder pattern located at three corners of the symbol and intended to assist in easy location of its position, size and inclination. A wide range of sizes of symbol is provided together with four levels of error correction. Symbol structure of QR Code is as following [8]. |
| In version 1 measures 21 modules × 21 modules, Version 2 measures 25 modules × 25 modules and so on increasing in steps of 4 modules per side up to Version 40 which measures 177 modules × 177 modules. Four levels of Reed- Solomon error correction (referred to as L, M, Q and H in increasing order of capacity) allowing recovery for the code words in 7%, 15%, 25% or 30% respectively [8].Barcodes, which are considered as an automatic recognition method with high-speed reading, high accuracy, low-cost and high-reliability, is widely applied in commodity labels, data security, anti-counterfeiting, electronic commerce and many other fields. It can be classified into two types, onedimensional (1D) barcode and two-dimensional (2D) barcode [7]. |
| Above figure shows the structure of both 1D and 2D barcode which are used in digital watermarking technique for data hiding purposein this section we are also going to study various methodology of watermarking scheme based on technology used for different approach: |
| DFT transform is a typical scene for image processing and digital signal processing that calculate by using Log-Polar coordinate which can be defined as [15] |
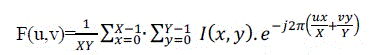 (1) (1) |
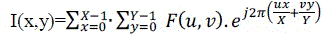 (2) (2) |
| For F (u, v) is coefficient from QR Code image that uses Fourier transform by I(x, y). QR Code image is hidden digital watermark in F’ (u, v) [15]. Fourier transform can be defined in frequency domain as |
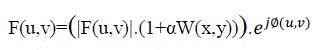 (3) (3) |
| |F (u, v)|and Φ (u, v) are Fourier spectrum and Phase angle in F (u, v).α is an amplitude factor in QR Code image is hidden digital watermark that in I' (x, y)[15]. Inverse Fourier transform can be defined as |
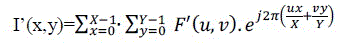 (4) (4) |
| C. Singular value decomposing (SVD) |
| SVD decomposes an mxn real matrix A into a product of 3 matrices A=USV T where U and V T are mxn and nxn orthogonal matrices, respectively. S is an nxn diagonal matrix. The elements of S are only nonzero on the diagonal and are called the SVs of A. The watermarking procedures are described as follows [9] |
| Watermark embedding: Without loss of generality, let the size of the host image (I) and watermark (W) is NxN |
| 1. Apply SVD to the host image: |
| I = USVT (1) |
| 2. Modify the S with the W: |
| SM=S+kW(2) |
| 3. Apply SVD to the SM |
| SM = UWSWVT W (3) |
| 4. Compute watermarked image: |
| IW = USWVT (4) |
| Watermark Extracting: In general, the extraction process is the inverse of the embedding procedure. In watermark extraction, a possibly distorted watermark W * is extracted from the possibly distorted watermarked image by I* W essentially reversing the above watermark embedding steps. The watermark extraction can be described as follows: |
| 1.Apply SVD to the watermarked (possibly distorted) image: |
| I* W =U*S* WV*T (5) |
| 2. Compute possibly corrupted S* M: |
| S* M = UWS* WVT W (6) |
| 3. Extract the watermark (possibly distorted) image: |
| W* = (S* M-S) / k (7) |
| C. Discrete Wavelet Transform (DWT) |
| Discrete Wavelet transform (DWT) is a mathematical tool for hierarchically decomposing an image [10]. It is useful for processing of non-stationary signals. The transform is based on small waves, called wavelets, of varying frequency and limited duration. Wavelet transform provides both frequency and spatial description of an image. Unlike conventional Fourier transform, temporal information is retained in this transformation process [11]. |
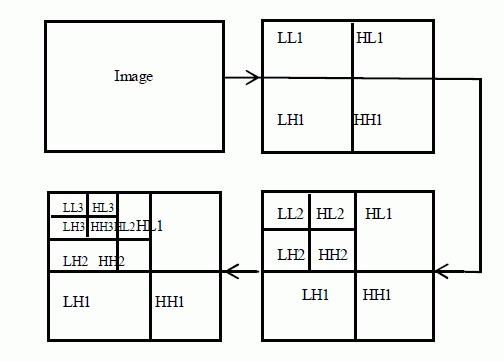
| The basic idea of discrete wavelet transform (DWT) in image process is to multi-differentiated decompose the image into sub-image of different spatial domain and independent frequency district [12] [13]. Then transform the coefficient of sub-image. After the original image has been DWT transformed, it is decomposed into 4 frequency districts which is one low-frequency district(LL) and three high-frequency districts (LH,HL,HH). If the information of low-frequency district is DWT transformed, the sub-level frequency district information will be obtained. A two-dimensional image after three-times DWT decomposed can be shown as Fig.4. Where, L Represents low-pass filter, H represents high-pass filter. An original image can be decomposed of frequency districts of HL1, LH1, and HH1. The low-frequency district information also can be decomposed into sub-level frequency district information of LL2, HL2, LH2 and HH2. By doing this the original image can be decomposed for n level wavelet transformation [14]. |
| DWT is currently used in a wide variety of signal processing applications, such as in audio and video compression, removal of noise in audio, and the simulation of wireless antenna distribution [15]. |
CONCLUSION
|
| In this paper, we proposed methods of embedding a digital watermark QR Code in a still image which is spread online. The proposed method is highly robust to compression and additive noise. We also explain QR code and detail classification of digital watermarking. |
ACKNOWLEDGMENT
|
| The satisfaction that accompanies that the successful completion of any task would be incomplete without the mention of people whose never-ending cooperation made it possible, whose constant guidance and encouragement crown all efforts with success. I am grateful to our project guide Prof. N. M. Kazi for the guidance, inspiration and constructive suggestions that helpful us in the preparation of this seminar. Last but not the least, I am thankful to all my friends and well-wishers to whom I am indebted for their constant help, encouragement and without whom this seminar would not have been a success. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
| |
References
|
- F. Hartung, and M. Kutter, “Multimedia watermarking techniques”, Proc. IEEE, vol. 87, no. 3, 1999, pp.1079–1107.
- V. Aslantas, “Optimal SVD based Robust Watermarking using Differential Evolution Algorithm”
- Chih-Chin Lai, “An improved SVD-based watermarking scheme using human visual characteristics”, Department of Electrical Engineering, National University of Kaohsiung, Kaohsiung 81148, Taiwan
- G.Prabakaran, R.Bhavani, M.Ramesh “A Robust QR- Code Video Watermarking Scheme Based on SVD and DWT Composite Domain“Department of computer science Engineering, Annamalai University, Tamilnadu, India.
- Thitapa Poom vichid, Pantida Patirupanusara and MahasakKetcham, “The QR Code for Audio Watermarking using Genetic Algorithm” International Conference on Machine Learning and Computer Science (IMLCS'2012) August 11-12, 2012 Phuket (Thailand).
- Shanjun Zhang1 * and Kazuyoshi Yoshino2, “DWT-Based Watermarking Using QR Code” By a grand of Research Institute for Integral Science, Kanagawa University.
- Lakshmi ChetanaVemuri, Gogineni Krishna Chaitanya, Narasimham “Geometric Invariant Digital Image Watermarking Techniques for QR code”, International Journal of Computer Science and Information Technologies, Vol. 3 (1) , 2012, 3037 – 3041.
- “Denso wave incorporated,” http://www.denso-wave.com/qrcode/index.html
- R. Liu, and T. Tan, “An SVD-based watermarking scheme for protecting rightful ownership”, IEEE Trans. Multimedia, vol. 4, 2002, pp.121- 128
- W. Hong and M. Hang, Robust Digital Watermarking Scheme for Copy Right Protection, IEEE Trans. Signal Process, vo.l2, pp. 1- 8, 2006.
- Nikita Kashyap, “Image Watermarking Using 3-Level Discrete Wavelet Transform (DWT)” Department of Electronics & Telecommunication Engineering, Shankaracharya Technical Campus, Bhilai, India.
- GhoutiL, BouridaneA and Ibrahim MK, “Digital image watermarking using balanced multiwavelets” , IEEE Transactions on Signal Processing, 54(4), pp. 1519-1536, 2006.
- Reddy AA, Chatterji BN, “A new wavelet based logowatermarking scheme”, Conf. Pattern Recognition letters, 26(7), pp. 1019-1027, 2005.
- Mei Jiansheng, Li Sukang1 and Tan Xiaomei, “A Digital Watermarking Algorithm Based On DCT and DWT” Nanchang Power Supply Company, Nanchang, China
- Blossom Kaur, AmandeepKaur, Jasdeep Singh,
- Steganographic Approach for hiding Image in DCT Domain, International Journal of Advances in Engineering & Technology, July 2011
- SuppatRungraungsilp, MahasakKetcham, TaneeWiputtikul, KanchanaPhonphak and SartidVongpradhip, “ Data Hiding Method for QR Code Based on Watermark by comparing DFT with DWT Domain”.
|