ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Sakshi Sanjay Deshmukh, Dr.G.R.Bamnote
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Cloud computing is one of the renowned and fascinating technology all over the world. It consists of various hardware and software resources made available on internet. Many times large number of sensitive data available on cloud. With the growth of the cloud users malicious activity in the cloud has been increased day by day. Millions of people are using services over cloud database, so it becomes more secured and integrity of data should be maintained. The proposed system consists of creation of multiple virtual clouds. Security of data over cloud would be maintained by using various encryption algorithms. Concurrent and secured sharing of data on cloud database would be maintained.
KEYWORDS |
| Cloud, Encryption, Decryption, Virtual clouds |
I. INTRODUCTION |
| Cloud computing has been conceived as the next generation pioneer for IT Enterprise. In modern era of networking system, Cloud computing is one the most precious and developing concept for both the developers and the users. Cloud computing is a preferable platform for those people who are mostly interrelated with the networking environment. It offers dynamically scalable resources provisioned as a service over network. Cloud computing refers to manipulate, configure, and access various applications online [1]. From past few years the world of computation has changed from centralized system to distributed systems. Generally, in Cloud computing services, data maintenance provided by some vendor which leaves the client/customer unaware of where the processes are running or where the data is stored [4]. Logically, the client has no control over it. Internet is the communication media for Cloud computing. In the Cloud computing environment, various services and information are shared among all of the servers and clients. As a result files or data stored in the cloud many times publicly accessible. Therefore, there is possibility that all files or data become more prone to attack. So it is very easy for an intruder to disturb the original form of information [15]. Thus, it is important to protect the data or files in the midst of unsecured processing. From the security viewpoint, various risks and issues are discussed for data over cloud. There are various threats associated with the security but one of the major issues is the security of data being stored on the provider's cloud and privacy while the data is being transmitted. Although Cloud computing has achieved a great success in various industries whether it is a software industry, a Government Organization or a Healthcare sector, but this transition to Cloud computing has various concerns on a critical issue for the success of information systems, communication and information security. There are various risks associated with the security but one of the major issues is the security of data being stored on the provider's cloud database and privacy while the data is being transmitted [19]. So to make Cloud computing technology more secure; for concurrent access to data on cloud database and for independent access of data on cloud database; a framework is proposed to encrypt the data over cloud database using various encryption algorithms. |
II. RELATED WORK |
| Luca Ferretti, Michele Colajanni, and Mirco Marchetti proposed a novel architecture for describing possibility of executing concurrent operations on encrypted data and integrates cloud database services with data confidentiality [1].Sushmita Raj, Milos Stojmenovi and Amiya Nayak proposed a new decentralized access control scheme .In that cloud verifies the authenticity of unknown user before storing data [2]. Julisch K. & Hall. M. proposed importance of Virtualization, Web Service, Service Oriented Architecture and Application Programming Interfaces for cloud computing [13].Gellman discussed standards for collection, maintenance and disclosure of personal information over cloud[20]. Jarabek and Hyde described possible attacks on cloud data [12][15].Guo Yubin et al, had done work on storage solution for No SQL database using homomorphic encryption algorithms. Data querying Protocol described in this work and algorithms for data manipulation are given also[5].Ming Li et al, proposed a novel framework of secure sharing of personal health records over clouds. Considering partially trustworthy cloud servers, patients will be able to maintain their own privacy through encrypting their PHR files to allow fine-grained access [6].Omer K. Jasim et al, discussed the various encryption symmetric key algorithms and asymmetric key algorithms. They also discussed the performance of encryption algorithms on a cloud environment for input blocks of different sizes and how the change in the size of the files after encryption is complete [7].T. Sivasakthi and Dr. N. Prabakaran proposed use of digital signature for authentication purpose in cloud computing. The propose work assured to secure the information in cloud server[3].Sanjoli Singla, Jasmeet Singh proposed a design that can help to encrypt and decrypt the file at the user side that provide security to data at rest as well as while moving. For this Rijndael encryption algorithm along with EAP-CHAP used [4].Kuyoro S. O.described key security considerations and challenges which are currently faced in the Cloud computing [8]. J. Bethencourt et al, discussed Attribute Based Scheme (ABE). For this, a user has a set of attributes in addition to its unique ID. There are two classes of ABEs that are In key-policy and Cipher text-policy [17]. ENISA(European Network Information and Security Agency)investigated the different security risks related to adopting cloud computing along with the affected areas, various risks, impacts, and vulnerabilities in the cloud computing may lead to such risks[18]. Balachandra et al, discussed the security SLA‟s specification and objectives related to data locations, segregation and data recovery[16].Kresimir et al, discussed high level security concerns in the cloud computing model[14]. Bernd et al, discussed the how security weaknesses existing in the cloud platform and how they affect the client data. [20]. Cloud Security Alliance (CSA) had given TOP threats to cloud computing [19].Service Level Agreements (SLA) also defined many times for data on the cloud [20]. |
III. SECURITY ISSUES TO CLOUD DATABASE |
| Following are the security issues to be fulfilled while working with cloud database: |
| a) Privacy and Confidentiality |
| Once data get dispatched on the cloud database, there will be limited access to that data. Privacy of sensitive data should always be maintained. Appropriate privacy policies and procedures should be there to assure the cloud users of the data safety [3]. |
| b) Data integrity |
| Integrity of data should be maintained with security. Cloud service providers should implement mechanisms to ensure data integrity and be able to tell what happened to a certain dataset and at what point [6]. |
| c) Data location and Relocation |
| High degree of mobility can be offered by Cloud computing. There should be a contractual agreement, between the Cloud provider and the consumer that data should stay in a particular location or reside on a given known server. |
| d) Data Availability |
| When data is available on different locations or clouds, integrity of data on cloud database would be maintain. Uninterruptable data should be provided. |
IV. SYSTEM ANALYSIS |
Existing System Issues: |
| Original data must be accessible only to the trusted parties that do not include cloud providers, intermediaries and internet [13]. In any trusted parties data must be encrypted. Satisfying these goals has different level of complexities depending on type of cloud. It was also a time consuming task to encrypt data on cloud database and access it [8]. |
Disadvantages of Existing System: |
| Implementation of encryption becomes difficult due to computational complexity. |
| Security was less. |
V. PROPOSE SYSTEM DESIGN |
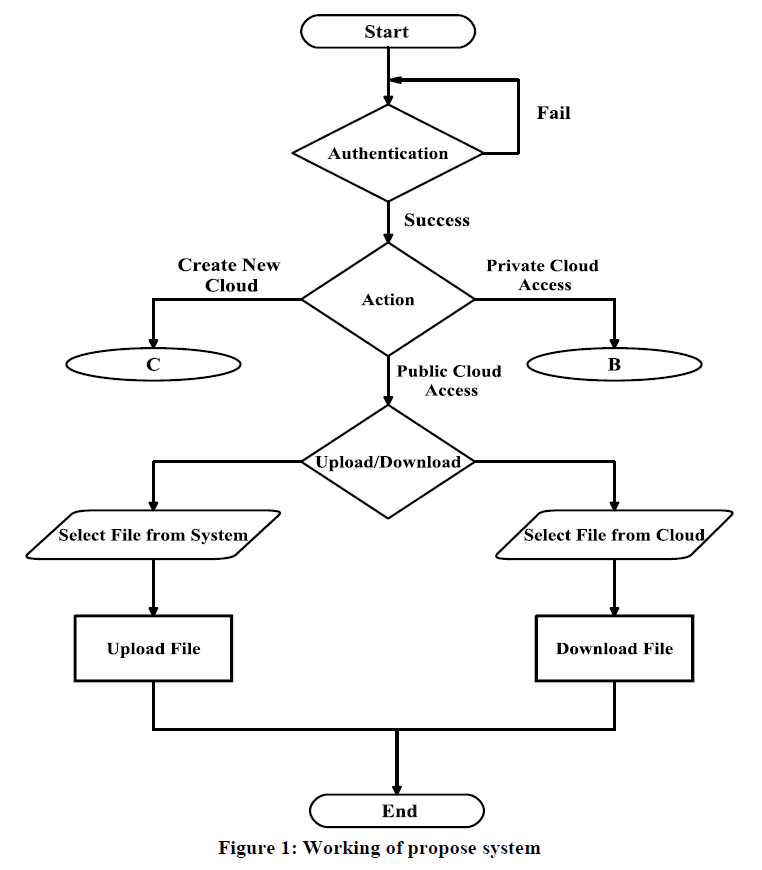
| User has to go through following steps as shown in Figure 1; while dealing with proposed work. |
| o Authentication is checked; if it is successful then User is able to create a new cloud, having access to Public cloud and having access to Private cloud. |
| o If user selects „Public Cloud Access‟ then he will be able to Upload plain/encrypted data file on public cloud and Download plain/encrypted data file from Public cloud. |
 |
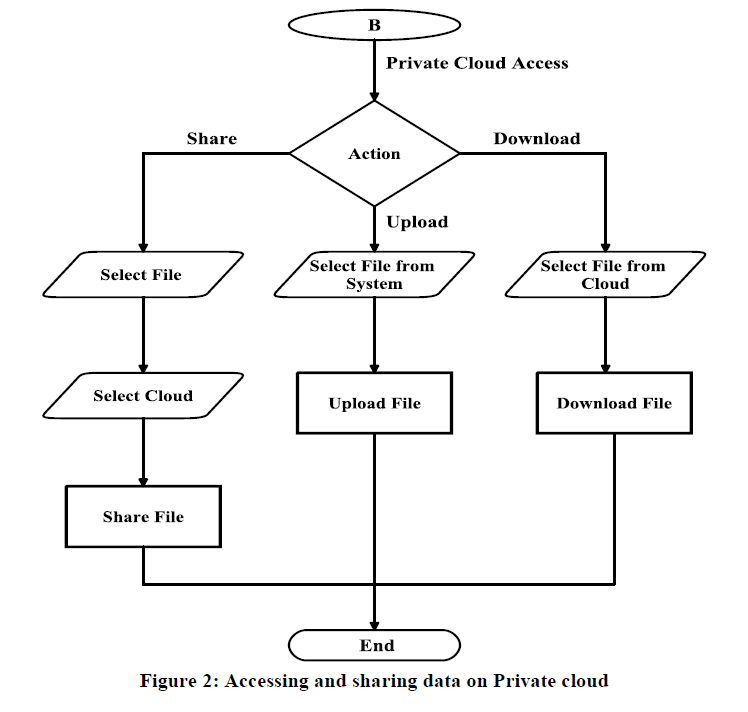
| If User/Client will choose „Private Cloud Access‟ then following steps takes place and as shown in Figure 2. |
 |
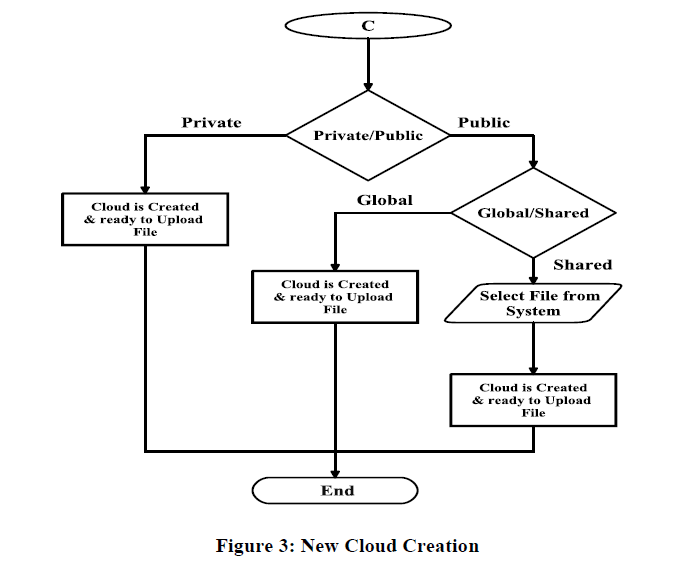
| If User/Client has to Create a New Cloud then he has to follow steps shown in Figure 3. |
| o If User will select „Create New cloud‟ then he will be able to create new virtual cloud as per requirement. |
| o If User will choose a „Private cloud‟ option then it is created and file uploaded on his personal cloud and accessible to him only. |
| o If User choose a „Public cloud‟ option in which global cloud will be created directly and shared cloud get created after members (users) of that cloud selected by owner. |
 |
VI. PROPOSE SYSTEM IMPLEMENTATION |
o User Registration: |
| Many numbers of users will be able to do registration and create their virtual Private clouds by default when registrations get completed. |
| Input: Information of user will be taken for generation of User-id and Password. |
| Output: User gets registered and Virtual Private cloud will be created for registered user. |
o Virtual Cloud Creation: |
| After registration, users have to Log-in and options will be provided for creation of shared (Public) or Private cloud. Input: User-id, password, select option for Shared or Private cloud. |
| Output: Shared or Public cloud created for specific user. |
o Upload Data over cloud: |
| Input: Select cloud name for keeping user‟s data file. |
| Output: User‟s data will be kept on particular cloud for future purpose. |
o Download Data from cloud: |
| Input: Select cloud name from which client has to get data which is present over cloud. |
| Output: Client will be provided with required data from selected cloud. |
o Encryption of Plain Data File: |
| Input: Generated key and Plain Data File from System. |
| Output: Encrypted file in Human Unreadable format. |
o Decryption of Encrypted Data File: |
| Input: Same key used for Encryption and Encrypted Data File. |
| Output: Decrypted Data File in Human Readable format. |
VII. EXPERIMENTAL RESULTS AND DISCUSSIONS |
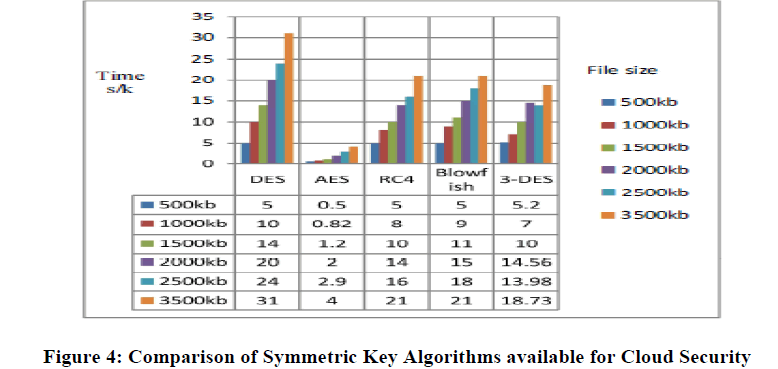
| Comparisons of symmetric key algorithms are as shown in Figure 4 and the following results can be concluded: |
| i. The running time is faster on the cloud network. |
| ii. Running time is proportional to the input file size as shown in Figure 4; more the file size more the time. |
| iii. It has been observed that AES encryption technique is the fastest symmetric encryption method and it can be analyzed from Figure 4.Here it is shown that it requires less time for processing and encrypting data on cloud database. |
 |
VIII. CONCLUSION AND FUTURE WORK |
| Cloud computing offers real various alternatives to IT departments for improved flexibility and lower cost. Many services are readily accessible on a pay-per-use basis and offer great alternatives to businesses that need the flexibility to rent infrastructure on a temporary basis or to reduce capital costs. Proposed a framework which encrypts data before it is uploaded on to the cloud and it also create secured, concurrent and independent encrypted data over cloud. Use of AES algorithm provides secure transfer of Data File within few seconds. Thus, if used securely, cloud computing provides a user with amazing benefits and overcomes its only disadvantage of security thread. In future, Mechanism to be implemented to Compress large size files automatically so that it will take less space on cloud database . The work will have to be done to detect duplicate copies of same data on cloud database. System will have to be deployed on server nodes globally, so that it can be access from anywhere. |
|