Keywords
|
| Encryption, Decryption, Selection, Crossover, Mutation, key, Fitness Value, XOR, Permutation, block cipher. |
INTRODUCTION
|
| Online transaction is nowadays most common practice in our daily life. So network security has become one of the most concern era. Cryptography is one of the techniques to communicate through insecure network securely. At the same time Genetic Algorithm (GA) is one of the newly emerging problem solving techniques which is gaining popularity due to its robustness. GA offers significant benefits over other optimization techniques in searching a large state space. |
| Cryptography is the art of processing information secretly. The basic element of cryptography is Algorithm for encryption and decryption of information and the other one is the key used. |
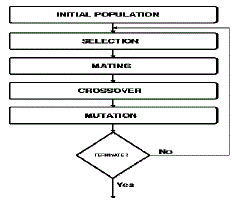
| Geneticalgorithms belong to the larger class of evolutionary algorithms (EA), which generate solutions to optimization problems using techniques inspired by natural evolution, such as mutation, selection, and crossover. Here we have used two point cross over. And the fitness function is used for taking decision of further movement. |
RELATED WORK
|
| In literature to date, there are many popular encryption technique are present namely DES, RSA etc.[1] And many GA based encryption algorithms have also been proposed. A. Tragha et.al [2] have describe a new symmetric block cipher system namely, ICIGA (Improved Cryptographic Inspired by Genetic Algorithm) which generates a session key in a random process. The block size and key length are variables and can be fixed by the end user in the beginning of the cipher process. ICIGA is an enhancement of the system GIC (Genetic Algorithm inspired Cryptography) [3]. There are various proposed methods for image encryption such as quad tree approach, cellular automata [4, 5]. There are wide applications of GA in solving non-linear optimization problems in various domains [6]. But very few papers exist which exploit the randomness in the algorithm for implementation of security. Chaos theory and entropy have large application in secure data communication and the desired disorder is provided by inherent nature of genetic algorithm [7, 9]. Mohammad SazzadulHoque et.al [10] have presented an intrusion detection system by applying GA to efficiently detect various types of network intrusions. They have used evolutionary theory to filter the traffic data and thus reduce the complexity [11]. There are several papers related to IDS all of which use GA in deriving classification rules [12, 14]. |
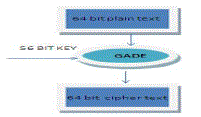
| In this paper we have made an attempt, to build an encryption algorithm inside which we have introduced genetic algorithm. It’s Strength lie in its key size i.e., 64 bit. |
PROPOSED ALGORITHM
|
| A. Proposed Encryption Algorithm |
| Step: 1 |
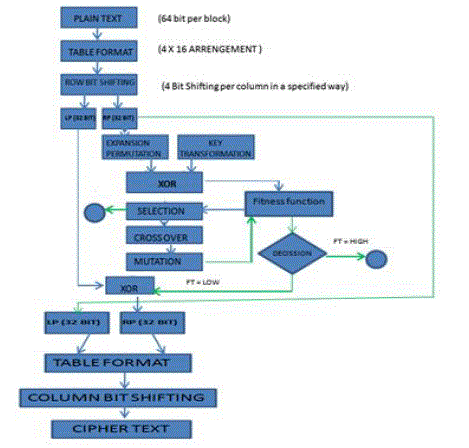
| Divide the plain text in 64 bits block each and encrypt each block. |
| Step: 2 |
| Arrange these 64 bits into 4 x 16 table format. For example: |
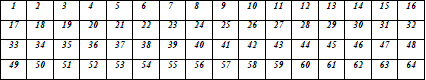 |
| Step: 3 |
| Four bit shifting per row in a cyclic fashion as highlighted |
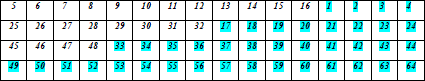 |
| Step: 4 |
| Now divide into two block (32 bits per block). Left part(LP) and Right part(RP). |
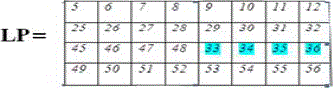 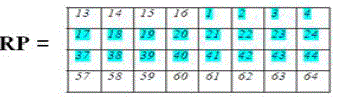 |
| Step: 5 |
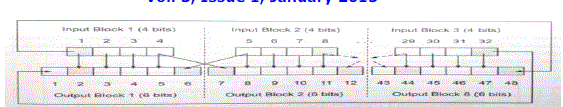
| Perform Expansion permutation with RP.As shown: |
| Here some bits from the input are duplicated at the output; e.g. the fifth bit of the input is duplicated in both the sixth and eighth bit of the output. Thus, the 32-bit half-block is expanded to 48 bits. |
| Step: 6 |
| Now generate key of 48 bit (Explained later). |
| Step: 7 |
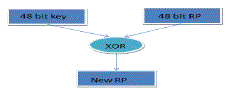
| Apply XOR with 48 bit key and 48 bit RP to get new RP of 48 bit. |
| Step: 8 |
| Now with the result apply genetic algorithm operations like selection, crossover and mutation. |
| Fitness Function: |
| From new 48 bit RP make 4 x 12 table. Let the table be: |
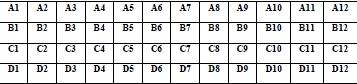 |
| Fitness will be calculated for each row of the above table. The fitness function will count the number of ones in each row. If the number of one’s is 6 then fitness is 6 for that row. Similarly calculate for other rows. Then finally count the total fitness. Now perform selection. |
| Selection: |
| Consider 1st and 3rd row as 1st pair of parent and other as 2nd pair of parent. |
| Let the new RP of 48 bit in 4 x 12 table as: |
| Before selection:- |
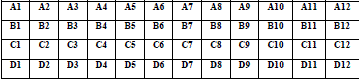 |
| After selection:- |
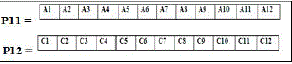 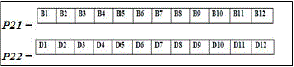 |
| Crossover (Two point crossover): |
| We will randomly choose any two numbers from 1 to 12 as cross over point and implement crossover. Here the points are (3,9). |
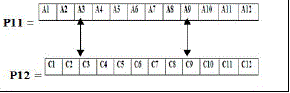 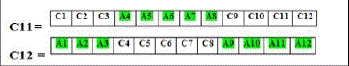 |
| Similarly the other two parent pair will also create another two child. |
| Mutation: |
| We will randomly choose any one numbers from 1 to 12 as mutation point and implement. Here the point is 6(let). Shown the result after mutation. |
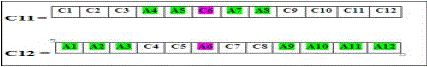 |
| Now combine C11, C12, C21 and C22 to get RP. |
| Now again calculate Fitness same way. If the new fitness is lower then go to next step else again perform mutation, selection, and crossover. |
| Step: 9 |
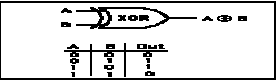
| Perform XOR operationwith LP of step 4 and the result of step 8 which is new RP. XOR gate work as:- |
| Step: 10 |
| And the RP of step is taken as LP. |
| Step: 11 |
| Now recombine LP of step10 and RP of step 9 to transform in 16 x 4 table. |
| Step: 12 |
| Four bit shifting per column in a cyclic fashion as given below. |
 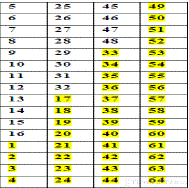 |
| Step: 13 |
| The resultant is the original cipher text. |
| B. Proposed Key Generation Technique: |
| Step: 1 |
| At first random 64 bit are taken. And arrange them into table of 8 x 8format. |
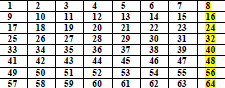 |
| Note: |
| For 1st block of 64bit plain text the key creation will discard 8th column for next 64 bit it will discard 7th column so as on. And from 9th block again start from 8th column and continue. |
| Step: 2 |
| Now truncate the 8th column of the table,the result will be of 56 bit key. |
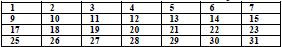 |
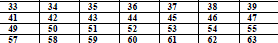 |
| Step: 3 |
| Arrange 56 bit into table of 8 x 7 format. And truncate mid or 4th row. |
 |
| Step: 4 |
| Now the key of 48 bit is ready to use. Shown in 4 x 12 format. |
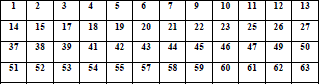 |
| C. Implementation in JAVA |
| We can implement the above algorithm in JAVA to get the result. The files uses for the algorithm are: |
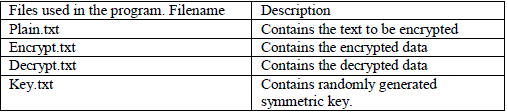 |
| Here in this paper an encryption technique is introduced which will prove to be a strong encryption technique for the unauthorized party to break the code. Here the key needed to share very efficiently as strength lie in key mostly. In near future it can prove to be a popular genetic-encryption technique. |
| Here the randomness of genetic algorithm and secrecy of cryptography has made this algorithm strong one. And the key transformation process also improved its efficiency. Although many of its steps and key generation techniques are inspired from DES algorithm but flavour of GA makes it unique. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
 |
 |
 |
| Figure 5 |
Figure 6 |
Figure 7 |
|
| |
References
|
- Atul Kahate, “Cryptography and Network Security- Second Edition”.
- Tragha A., Omary F., Mouloudi A., “ICIGA:Improved Cryptography Inspired by Genetic Algorithms”, Proceedings of the International Conference on Hybrid Information Technology (ICHIT’06), pp. 335-341, 2006.
- X. F. Liao, S. Y.Lai and Q. Zhou. Signal Processing. 90 (2010) 2714–2722.
- H. Cheng and X. Li. IEEE Transactions on Signal Processive. 48 (8) (2000) 2439–2451.
- O. Lafe. Engineering Applications of Artificial Intelligence. 10 (6) (1998) 581–591.
- R. J. Chen and J. L. Lai. Pattern Recognition. 40 (2007) 1621–1631
- S. Li, G. Chen and X. Zheng. Multimedia security handbook. LLC, Boca Raton, FL, USA: CRC Press; (2004) [chapter 4].
- Y. Mao and G. Chen. Handbook of computational geometry for pattern recognition, computer vision, neural computing and robotics. Springer; (2003).
- H. S. Kwok, W. K. S. Tang, Chaos Solitons and Fractals, (2007) 1518–1529.
- Mohammad SazzadulHoque, Md. Abdul Mukit and Md. Abu NaserBikas,An Implementation of Intrusion Detection System Using GeneticAlgorithm, International Journal of Network Security & Its Applications (IJNSA), Vol.4, No.2, March 2012
- L.M.R.J Lobo, Suhas B. Chavan, Use of Genetic Algorithm in Network Security, International Journal of Computer Applications (0975 – 8887)Volume 53– No.8, September 2012
- W. Lu, I. Traore, “Detecting New Forms of Network Intrusion Using Genetic Programming”. Computational Intelligence, vol. 20, pp. 3, Blackwell Publishing, Malden, pp. 475-494, 2004.
- M. M. Pillai, J. H. P. Eloff, H. S. Venter, “An Approach to Implement a Network Intrusion Detection System using Genetic Algorithms”, Proceedings of SAICSIT, pp:221-228, 2004.
- S. M. Bridges, R. B. Vaughn, “Fuzzy Data Mining And Genetic Algorithms Applied To Intrusion Detection”, Proceedings of 12th AnnualCanadian Information Technology Security Symposium, pp. 109-122, 2000
|