Keywords
|
| Pixel Replacement, Gray scale, indexed, RGB, Stego image, MSE, PSNR |
INTRODUCTION
|
| Steganography is the art of hiding information imperceptibly in a cover medium. The word Steganography is of Greek origin and means covered or hidden writing. The main aim in steganography is to hide the very existence of the message in the cover medium. Steganography and Cryptography are counter parts in digital security. The obvious advantage of steganography over cryptography is that messages do not attract attention to themselves, to messengers, or to recipients. During the last decade, an exponential growth in the use of multimedia data over the Internet is seen. These include Digital Images, Audio and Video files. This rise of digital content on the internet has further accelerated the research effort devoted to steganography. The various applications of steganography include secure military communications, multimedia watermarking and fingerprinting applications for authentication purposed to curb the problem of digital piracy. Although these are not perfect applications of steganography, many steganographic algorithms can be employed for these purposes as well. |
| Faheem Ahmed and Rizwan [2] have introduced a new concept in data embedding. The authors have embedded text message and digital image in audio files. They have also presented a technique for embedding text message and/or digital image in another image. A lot of examples have been presented. Fridrich etal. [3] have studied quantitative stegnanalysis of digital images. They have estimated the length of the secret message. Rizwan and Faheem Ahmed [5] have made a comprehensive study on various types of steganographic schemes. Faheem Ahmed and Rizwan [6] have introduced and studied seven different steganographic techniques applying randomization concept. They have also computed the MSE and PSNR indices for these techniques. Structural similarity indices have also been determined.. |
TYPES OF DIGITAL IMAGES
|
| There are four basic types of images. |
| Binary Image : Each pixel is either black or white. Since there are only two possible values for each pixel, we only need one bit per pixel. Such images can therefore be very efficient in terms of storage. Images for which a binary representation may be suitable include text (printed or handwriting), fingerprints, or architectural plans. Figure 1 shows a black & white image and the contents of a section. |
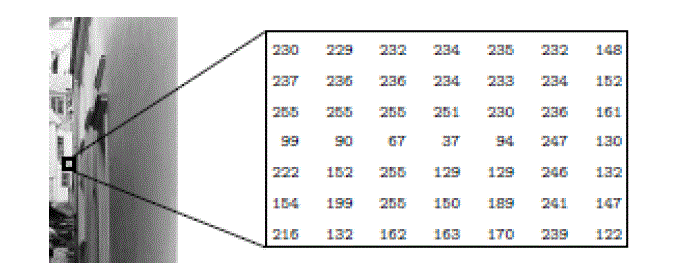
| Grayscale Image : Each pixel is a shade of gray, normally from 0 (black) to 255(white). This range means that each pixel can be represented by eight bits, or exactly one byte. This is a very natural range for image file handling. Other grayscale ranges are used, but generally they are a power of 2. Such images arise in medicine (X-rays), images of printed works, and indeed 256 gray levels is sufficient for the recognition of most natural objects. Figure 2 shows a gray level image and the contents of a section. |
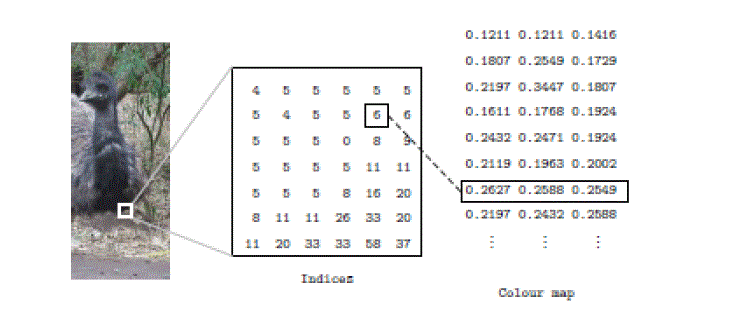
| Indexed Image : Most colour images only have a small subset of the more than sixteen million possible colours. For convenience of storage and file handling, the image has an associated colour map or colour palette, which is simply a list of all the colours used in that image. Each pixel has a value which does not give its colour (as for an RGB image), but an index to the colour in the map. It is convenient if an image has 256 colours or less, for then the index values will only require one byte each to store. Some image file formats (for example, Compuserve GIF), allow only 256 colours or fewer in each image, for precisely this reason. An indexed image and its contents are given in figure 3. |
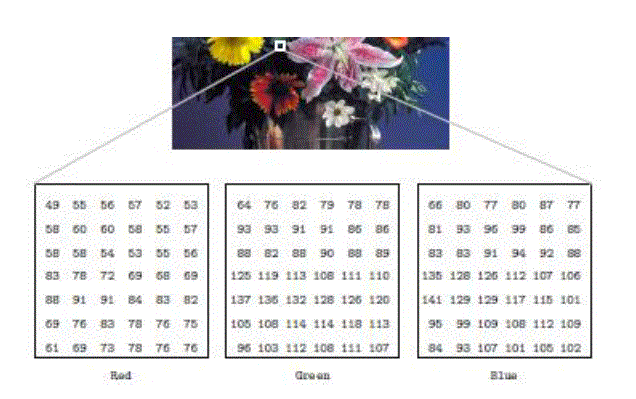
| True colour or RGB Image : Here each pixel has a particular colour; that colour being described by the amount of red, green and blue in it. If each of these components has a range 0 - 255, this gives a total of 2553 = 16, 777, 216 different possible colours in the image. This is enough colours for any image. Since the total number of bits required for each pixel is 24, such images are also called 24-bit colour images. Such an image may be considered as consisting of a stack of three matrices; representing the red, green and blue values for each pixel. This means that for every pixel there correspond three values. Figure 4 shows a colour image and part of its contents. |
EMBEDDING TEXT IN AN IMAGE USING NATURAL NUMBER INCREMENTS
|
| In this technique, we consider the usual natural sequence of numbers 1,2,3,4,5,6,…. and generate a sequence 1, 3, 6, 10, 15, 21, 28, 26, 45, 55, . . . by adding 2, 3, 4, 5, 6, 7, 8, . . . to each generated nuber. Then, hide each character of secret message in the above pixel locations. The resulting original image and the stego image after hiding 512 bytes of secret text are shown in figures 5, 6, 7 and 8. |
EQUAL / NEAREST VALUE PIXEL REPLACEMENT POINT OPERATIONS IN EACH COLUMN
|
| In this method, we find gray level that is equal or closest to each text value in each column, and replace that gray level with the text value. |
| For Example let the cover image be |
 |
| and let the text to be embedded is |
| 4 9 3 6 2 |
| The above text is then embedded in the cover image as follows: The first text is 4 which is near equal to 5 in first column of image, the second text 9 is near equal to 8 in second column, the third text 3 is near equal to 2 in third column, and so on. So the cover image becomes |
 |
| The above technique is applied on lena.tif 512x512 grayscale image, lena.gif 512x512 indexed image and lena.jpg 512x512 color image and the orginal, stego image embedded with 512 bytes of text are shown in the figures 9, 10 and 11. |
EQUAL / NEAREST VALUE PIXEL REPLACEMENT POINT OPERATIONS IN ENTIRE IMAGE
|
| Let cover be the image and message be the text to be embedded. The embedding is done as follows. The first character of message 72 is embedded at the nearest gray level 58 which is near equal in the entire image, the second character 101 is embedded at 103 which is near equal in the entire image and so on as shown in the following example. |
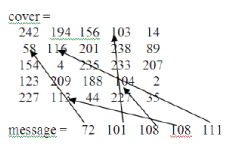 |
| The image with embedded text is |
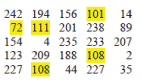 |
| The above technique is applied on lena.tif 512x512 grayscale image, lena.gif 512x512 indexed image and lena.jpg 512 x 512 color image and the orginal, stego image embedded with 512 bytes of text are shown in the figures 12, 13 and 14. |
EMBEDDING TEXT AT RANDOM LOCATIONS IN IMAGE
|
| The embedding is done as follows. First 512 ( number of text characters to be embedded ) random numbers are generated. The first character of message 72 is embedded at the first random number 4th location in image, the second character of message 101 is embedded at the second random number 1st location in image, the third character of message 108 is embedded at the third random number 3rd location in image and so on as shown in the following example. |
 |
| message = ‘Hello’= [ 72 101 108 108 111 ] |
| random numbers generated = 4 1 3 2 2 |
| Inserting the above text values at the memory locations of random numbers, we obtain |
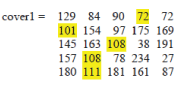 |
| The above technique is applied on lena.tif 512x512 grayscale image, lena.gif 512x512 indexed image and lena.jpg 512x512 color image and the orginal, stego image embedded with 512 bytes of text are shown in the figures 15, 16 and 17. |
| The Peak Signal to Noise Ratio (PSNR), Mean Square Error (MSE) are performance parameters to measure the quality of image. |
| • MSE: It is defined as square of error between cover stego-image. The error indicates the distortion in an image.MSE can be calculated by using two dimensional mathematical equation described as follows: |
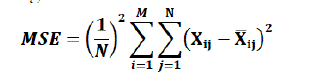 |
| where Xij = the value of pixel in cover image and =the value of pixel in stego-image and N is the size of image. |
| PSNR: It is a measure of quality of image. PSNR can be calculated by using the mathematical formula given below: |
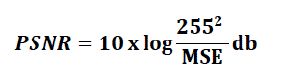 |
| The computed values of the PSNR and MSE indices, by considering the three different types of images and using four distinct methods introduced in this article are presented in table 1. |
| The histograms of the computed values of PSNR and MSE indices for each of the above techniques for all three types of images are presented in figures 18 and 19. |
| To do this, we require two software (i) coagula and (ii) Sonic visualizer. |
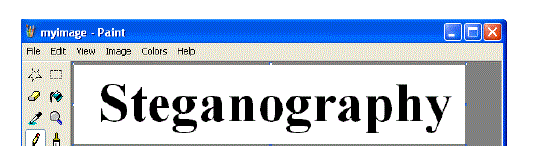
| In MS Paint, create a secret text message and save it as bmp file, say mytext.bmp as shown below. |
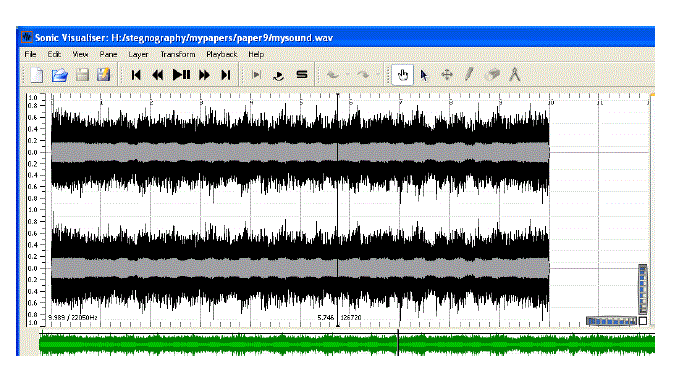
| Next open the mytext.bmp file in coagula and render the image without blue/noise. Then select File/Save sound as and give a file name say mysound.wav. Lastly, open this mysound.wav file in sonic visualizer which looks like an ordinary sound file as shown in figure 21. |
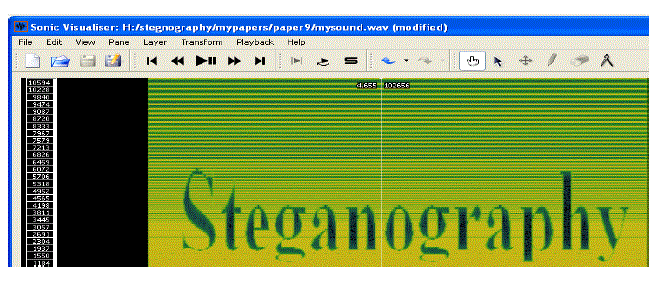
| Select Layer Menu/ Add spectrogram / All Channels mixed to reveal the secret message inside the audio file as shown. |
CONCLUSION
|
| Steganographic techniques have been used with success for centuries already. However, since secret information usually has a value to the ones who are not allowed to know it, there will be people or organizations who will try to decode encrypted information or find information that is hidden in them. Governments want to know what civilians or other governments are doing, Companies want to be sure that trade secrets will not be sold to competitors and most persons are naturally curious. Many different motives exist to detect the use of steganography, so techniques to do so continue to be developed while the hiding algorithms become more advanced. Secrets can be hidden inside all, hide information inside images, as this is relatively easy to implement. However, there are tools available to store secrets inside almost any type of cover source. |
| Many different carrier file formats can be used, but digital images are the most popular because of their frequency on the Internet. For hiding secret information in images, there exist a large variety of steganographic techniques; some are more complex than others and all of them have their own merits and demerits. Distinct applications have different requirements of the steganographic technique used. For example, some applications may require absolute invisibility of the secret information, while others require a larger quantity of secret message to be hidden. After giving an overview of image steganography, its uses and techniques are presented in this article. Some new techniques of embedding a text message in various types of digital images are introduced. |
| This paper has given a brief comparison on applying steganography on various types of images like black & white, gray level, indexed and RGB. Instead of hiding text in least significant bits, steganography is applied on direct pixel values itself and the actual and stego images in each type are given for comparison. Further, hiding of text in an audio file is also discussed. |
Tables at a glance
|
 |
| Table 1 |
|
| |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
|
 |
 |
 |
 |
 |
| Figure 6 |
Figure 7 |
Figure 8 |
Figure 9 |
Figure 10 |
|
 |
 |
 |
 |
 |
| Figure 11 |
Figure 12 |
Figure 13 |
Figure 14 |
Figure 15 |
|
 |
 |
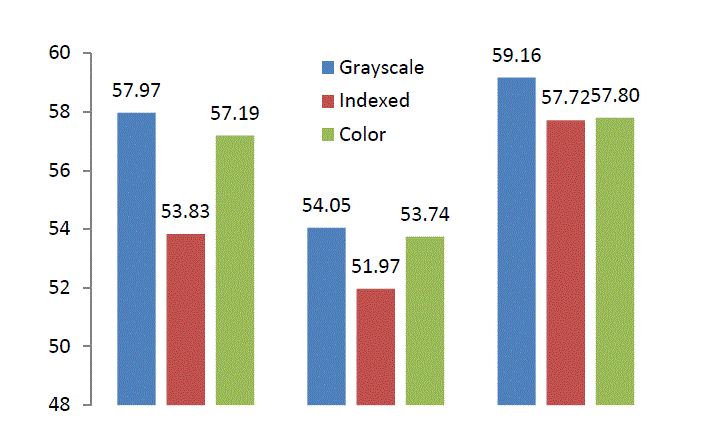 |
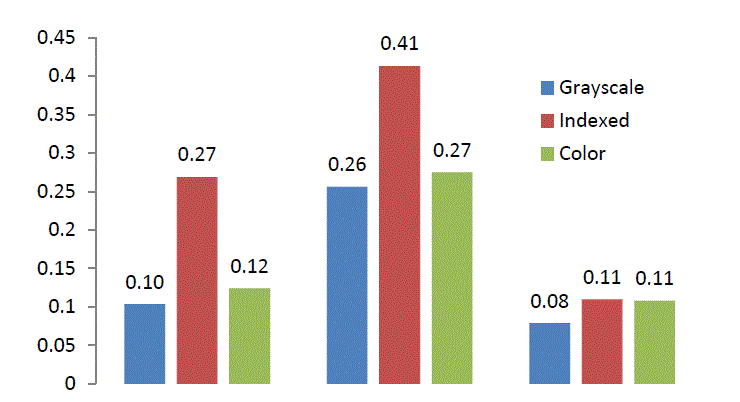 |
| Figure 16 |
Figure 17 |
Figure 18 |
Figure 19 |
|
 |
 |
 |
| Figure 20 |
Figure 21 |
Figure 22 |
|
References
|
- Abdullah Wahbeh H, Mohammed Al-Kabi., “Comparative Assessment of the Performance of Three WEKA Text Classifiers Applied to ArabicText”, Vol. 21, No. 1, pp. 15- 28, 2012.
- Abdullah Wahbeh H, Qasem Al-Radaideh A, Mohammed Al-Kabi N, and Emad Al-ShawakfaM., “A Comparison Study between Data MiningTools over some Classification Methods”.
- Artur Ferreira., “Survey on Boosting Algorithms for Supervised and Semi-supervised Learning”.
- Christophe Giraud-Carrier., “Meta learning - A Tutorial”.
- ChristophGoller, Joachim Löning., Thilo Will, Werner Wolff., “Automatic Document Classification: A thorough Evaluation of variousMethods”
- Falguni Patel N, Neha Soni R., “Text mining: A Brief survey”, Volume-2 Number-4 Issue December-2012.
- Ian Witten H, Eibe Frank, Mark Hall A., “Data Mining Practical Machine Learning Tools and Techniques”.
- Kalaiselvi P, Nalini C., “A Comparative Study of Meta Classifier Algorithms on Multiple Dataset”, International Journal of Advanced Researchin Computer Science and Software Engineering, Volume 3, Issue 3, March 2013.
- KaushikRaviya H, BirenGajjar., “Performance Evaluation of Different Data Mining Classification Algorithm Using WEKA”.
- Mahendra Tiwari, Manu BhaiJha, OmPrakashYadav., “Performance analysis of Data Mining algorithms in Weka”, IOSR Journal of ComputerEngineering (IOSRJCE), ISSN: 2278-0661, ISBN: 2278-8727 Volume 6, Issue 3, PP 32-41, (Sep-Oct. 2012).
- Nikita Bhatt, Amit Thakkar, Amit Ganatra., “A Survey & Current Research Challenges in Meta Learning Approaches based on DatasetCharacteristics”, Volume-2, Issue-1, March 2012
- Mrs. Sayantani Ghosh, Mr. Sudipta Roy, Prof. Samir Bandyopadhyay K., “A tutorial review on Text Mining Algorithms, Vol. 1, Issue 4, June2012.
- ShaidahJusoh, HejabAlfawareh M., “Techniques, Applications and Challenging Issues in Text Mining”, Vol. 9, Issue 6, No 2, November2012.
- Shilpa DhanjibhaiSerasiya, Neeraj Chaudhary., “Simulation of Various Classifications results using WEKA”, International Journal of RecentTechnology and Engineering (IJRTE) ISSN: 2277-3878, Volume-1, Issue-3, August 2012.
- Quan Sun, Pfahringer, “Pairwise meta-rules for better meta-learning-based algorithm ranking Machine learning”, Springer US, MachineLearning, 93(1):141-161, 2013.
|
| BIOGRAPHY |
| H. Faheem Ahmed earned his M.Tech. degree in Information Technology from Punjabi University and M.Phil. degree in Computer Science from Manonmaniam Sundaranar University. He is pursuing Ph.D. in Computer Science. He has guided 50 M.Phil. research scholars in Computer Science. He is currently the Head of the Department of Computer Science and Applications, Islamiah College, Vaniyambadi and is serving the institution for the past 28 years. His research interest includes Steganography and Image processing. He has published 8 research articles and authored one book. |
| U. Rizwan earned his Ph.D. degree in Mathematics from the University of Madras. He is currently the Head of the Department of Mathematics, Islamiah College, Vaniyambadi and is serving the Institution for the past 26 years. He has published 43 research articles in journals of international repute. He has authored 7 books and is also the editor of two international journals. He has guided 30 M.Phil. Mathematics research scholars and one M. Tech. (IT) candidate. He is guiding Ph. D. research scholars in Mathematics and Computer Science. His research interest includes Image Processing, Hacking algorithms, Stochastic Processes, Fuzzy Logic, etc. He is the member of the board of studies in PG Mathematics of Thiruvalluvar University, Vellore. He is also an academic auditor. |