Keywords
|
| Mobile Ad hoc Networks, hybrid strategy, LMA, CBR, CCBR |
INTRODUCTION
|
| In a MANET, the router connectivity may change frequently, leading to the multi-hop communication [5] paradigm that can allow communication without the use of BS/AP, and provide alternative connections inside hotspot cells. A dual-mode MS can operate in both the infrastructure (communicating directly to a BS or AP) and MANET modes using the WLAN interface. Due to the dynamic nature of MANETs [1], many authors have advocated for group communication as a key building block for context-aware programming in such networks. Each node depends on other nodes that are here (geographic dependency) right now (temporal dependency). To address the geographic dependency, highlevel, CGC and the abstractions proposed for MANETs often include a notion Temporal dependency can be analogously addressed by associating a notion of life-time with messages multicast leading to persistent locationsensitive messages. In location-based multicast addressing, the delivery of a message by a receiver is conditioned by three matches, namely in logical space, physical space, and time. Matching in terms of logical space means matching on message content, which is achieved based on content queries expressed by receivers as in contentbased publish/subscribe models. Matching in physical space and time is what captures the “here and now” nature of a mobile ad hoc network. In this hybrid strategy, where the expected load parameters are not known in advance or can vary over time, they did not consider the problem of Power Control and Packet Redundancy. In this kind of scenario [16], if a communication failure occurs within the path of the transmission nodes, with no acknowledgement, it is difficult to find the shortest path failure. Sometimes throughput is not [21]efficient because of communication overhead .Thus the problem is that, time delay can occur in both the algorithm by using in location based multicast addressing. |
RELATED WORK
|
| A. Content and context-based routing (CCBR): |
| In content and context-based routing (CCBR) [2], senders do not specify message recipients using a unicast or multicast address. Instead, they simply inject messages in the network, which determines their routing based on the nodes’ interests. The nodes identify the relevant classes of messages based on their content, e.g., using key-value pairs or regular expressions. Hence it is not the sender but the receiver which determines message delivery in CCBR. Complex [7] communication patterns frequently need to take the situation in consideration [8] when the information to be communicated is transmitted and received. The context of the publisher is encoded into the message published in the content-based version of the Publish-subscribe model. |
| B. Event-Based Middleware for Location-Aware Mobile Applications: |
| As we enter [3] the era of mobile application explosion, the importance of the programming model and the middleware architecture designed to support their development is becoming increasingly apparent. In order to lend support for the loose coupling of the mobile application components, the event-based programming model is an apt choice for the development. Nonetheless, in the existing event-based programming model middleware, there are challenges in [19] supporting the location-aware mobile applications where there is a necessity of dynamic collaboration of the highly mobile components at some location. To support [19] such collaboration, the event-based middleware may use location-independent announcement and subscription coupled with location dependent filtering and event delivery. An example is STEAM; an event-based middleware with a fully decentralized architecture is particularly well suited to deployment in ad hoc network environments. |
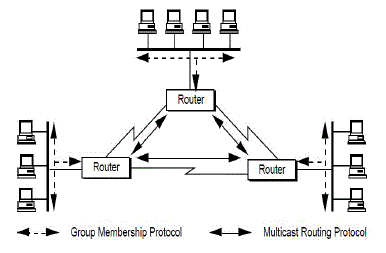
| C. On-Demand Multicast Routing Protocol: |
| In the field [2] of networking, multicasting has emerged as one of the most focused areas. As the technology and popularity of the Internet have grown, applications that require multicasting are becoming more widespread. In static networks the protocols used do not perform well in a dynamically changing ad hoc network environment. Multicast tree structures are fragile and must be readjusted continuously as connectivity changes. The frequent exchange of routing vectors or link state tables which are triggered by continuous topology changes yields excessive channel and processing overhead. Limited bandwidth, power constraints and mobility of network hosts make the multicast protocol design particularly challenging. ODMRP is mesh based forwarding instead of tree. It applies on demand multicast route construction and membership maintenance. ODMRP is effective and efficient in dynamic environments and scales well to a large number of multicast members. |
| D. Location Based Multicast Addressing: |
| In Location based multicast addressing [1] matches based on message space and the query space. Matching in terms of time means matching based on message persistence, which is defined as the lifetime determined by the application— within which a message is relevant for an interested receiver. Once this lifetime has elapsed, the message is considered obsolete and will not be delivered anymore. Matching in physical space and time is what captures the “here and now” nature of a mobile ad hoc network, i.e., its limited geographical scope and time span. Let us take a closer look at matching in physical space. A message space is associated with each message being multicast and defines a geographical range around the sender of that message; this space moves together with the sender, i.e., it remains centered on the sender. Symmetrically, a query space is associated with each receiver when indicating interest in receiving messages and defines a geographical range moving with the receiver. Message and query spaces can thus also be perceived as sender and receiver spaces, specific to messages and queries, respectively. |
| Message centric strategy The first, message-centric strategy uses geographically scoped gossiping to propagate messages within a defined geographical range around the sender (i.e., the message space), leaving the matching process to receivers. The components underlying in the Scoped Gossiping Service (SGS) are |
| SGS-BROADCAST(m, Δx, x) - disseminates message m to all hosts located within range Δx of position x. |
| SGS-DELIVER(m) - works as a callback and signals the reception of a message m. |
| Query centric strategies Query centric strategies rely on the preliminary propagation of receiver’s queries on content and location to allow sender and intermediate nodes to perform early matching and filtering of messages. The components underlying in the Gradiented Counter-based Routing (GCR) are GCR-CREATE(h,x,Δx,m) - broadcasts a route creation message m to all hosts h located within range Δx of position x. GCR-REGISTER(h,m) - works as a callback when a route creation message is received. This callback is triggered on all hosts located within range Δx of sender h and informs the upper layer that a route now exists to host h. |
| GCR-ROUTE(m,{h1, . . . ,hn}) - routes a message m to the set of hosts {h1, . . , hn}. This primitive assumes that each host called GCR-REGISTER beforehand. |
| GCR-DELIVER(m) - is used as a callback when a routed message m is received. |
| Hybrid strategies The thought process behind the hybrid strategy is to broadcast both messages and queries, but only up to half the distance of their respective spaces. The SGS layer is used to transmit the messages if the receiver is located within half the message space. The GCR layer is used instead if the receiver is located outside the half message space (but still inside the complete message space). We present an analysis of these algorithms, qualifying and quantifying their expected differences and expressing their break-even points based on the communication patterns induced by applications. |
PROPOSED ALGORITHM
|
| A. Markov Chain Process Used In Feedback Mechanisms |
| In this module, we are going to construct a feedback mechanism to reduce the packet redundancy from the Ad hoc networks to provide a high degree of mobility for all network components, including users and routers. Due to such unconstrained mobility, the path between any two users is subject to change during a session. This module is developed for node creation and more than 30-50 nodes placed in a particular distance. Mobile nodes are placed in an intermediate area in the distributed network. Each node knows its location relative to the sink. The maximum dimension of each node is set as x=4000 and y=4000. The size of the nodes is set at 35 and the ultimate time simulation is 10 ms and the speed of network for the nodes are set at 10-15 m/s. |
| Route updating in multicast routing protocols can be done in one of three ways: |
| Store and update: Store the information in a routing table and update it by listening to routing messages, as in the protocol. |
| Delete all and refresh: Discard all old routes (timeout) and start over; ideally, the frequency of the updates is matched with the frequency of changes in topology but is difficult to implement; and protocol for route updating. |
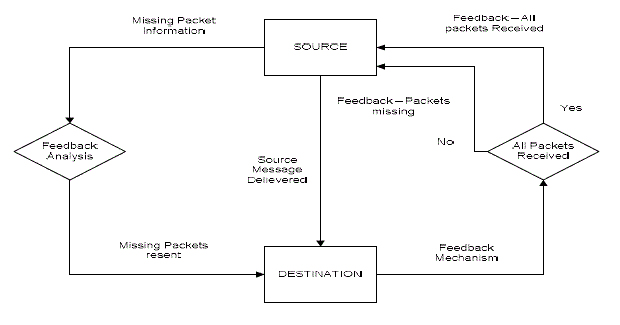
| Sender-initiated: Receivers return acknowledgments for correctly received packets; timers can be used to detect packet losses at the sender. However, if every receiver sends an acknowledgment for a packet it receives, feedback implosion can occur. |
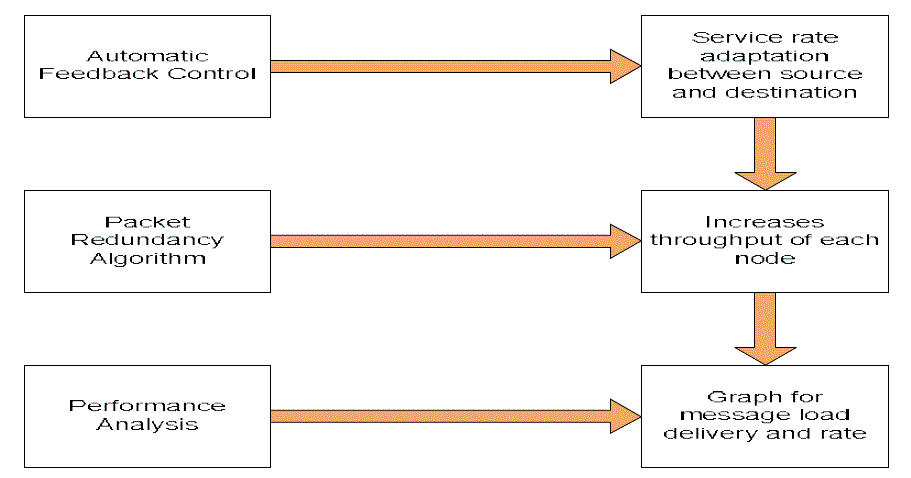
| B. Automatic Feedback Control System |
| By modeling the packet dispatching at the source and the packet receiving at the destination as Markov chains and applying the concept of automatic feedback control to characterize the service rate adaption between the source and destination of the flow, we first develop a general theoretical framework to depict the complicated packet delivery process in the challenging MANET environment. |
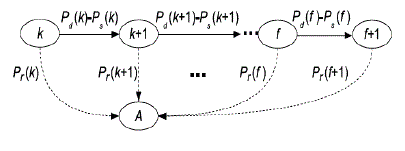
| C. Path Identification(2hf) Scheme |
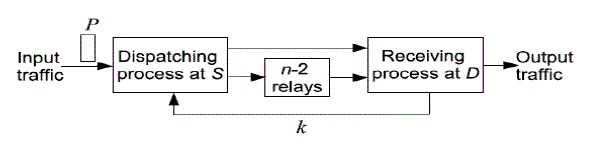
| When the source S wins the transmission opportunity at the current time slot, S first overhears the channel for a specified interval of time to check whether the node D is inside the one-hop transmission range. |
| Step1: If S hears the reply from D within the specified time interval, it initiates a handshake with D and then transmits a packet directly to D. |
| Step2: If no broadcasting reply is overheard during the specified time interval, a receiving node (say R) is randomly selected among the nodes within the one-hop transmission range of S based on a mechanism similar to the selection of transmitting node. |
| Step3: Suppose that the packet P is the packet locally generated for which S is currently delivering copies, S first initiates a handshake with R to check whether R has already received a copy of P before |
| Step4: . If not, S delivers out a new copy of P to R if only less than f copies of P have already been delivered out from S by now; otherwise, S remains idle for this time slot. |
| Step5: S initiates a handshake with R to check if S carries a packet P∗ destined for node R with SN(P∗) = RN(R). If so, S delivers the packet P∗ to node R; otherwise, S remains idle for this time slot. |
| D. Selection of Transmission Node |
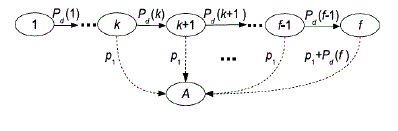
| Based on this intrinsic feature of automatic updating for parameter k, we can model the packet delivery process of the tagged flow as an automatic feedback control system, where the packet dispatching process at S and the packet receiving process at D can be defined by the two absorbing Markov chains. The automatic feedback control system defined for the packet delivery process of tagged flow where the parameter k is automatically updated to adjust to the service rates at the S and D. |
| D .Transmission Of Data Based On Group Scheduling |
| According to the protocol interference model, multiple links could simultaneously transmit if they are sufficiently far away from each other. To support as many simultaneous link transmissions as possible while ensuring an acceptable interference among the process nodes, we consider here a transmission group based scheduling scheme. The same transmission group and each of them can simultaneously support a transmitting node in it without interfering with each other. It is notable that for the transmission-group based scheduling with parameter α, there will be in total α2 distinct transmission-groups, where each cell belongs to one distinct transmission-group. If all transmission-groups alternatively become active, then transmission group becomes active in every α2 time slots. |
| E. Advantages |
| We may have a very significant per node throughput capacity improvement and may achieve its maximum possible value through adopting a bigger υ (and thus a larger transmission range) for each node, which is different from what is generally believed in literature that a smaller υ usually results in a higher throughput capacity. |
CONCLUSION AND FUTURE WORK
|
| The issues such as throughput efficiency, communication overhead, inability of varying load parameter values, packet redundancy occurrence, and mobility have long remained the important challenges in effective implementation of the mobile ad-hoc networks. In order to address the above mentioned challenges, the hybrid strategy in combination with the Markov chain is used in the location based multicast addressing in mobile ad-hoc networks. (MANET). The Markov chain allows the mobile ad-hoc network to implement automatic feedback control mechanism whereby each receiving node provides a feedback consisting information regarding the missing packets of the transmitted message or positive feedback of the successful receiving of the message to the source node. This in turn increases the efficiency of the MANET avoiding the client starvation and also improving the throughput efficiency and the optimal performance of the networks. |
| |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
 |
 |
 |
| Figure 4 |
Figure 5 |
Figure 6 |
|
| |
References
|
- Adrian Holzer, Patrick Eugster, Beno?ˆt Garbinato, “Evaluating Implementation Strategies for Location-Based Multicast Addressing” IEEE TRANSACTION MOBILE COMPUTING, VOL. 12, NO. 5, pp 855-866 ,MAY 2013.
- S. Castelli, P. Costa, and G.P. Picco, “HyperCBR: Large-Scale Content-Based Routing in a Multidimensional Space,” Proc. IEEEINFOCOM, 2008.
- S.J. Lee, M. Gerla, and C.C. Chiang, “On-Demand Multicast Routing Protocol,” Proc. Wireless Comm. and Networking Conf., 2009.
- R. Meier and V. Cahill, “On Event-Based Middleware for Location-Aware Mobile Applications,” IEEE Trans. Software Eng.,vol. 36, no. 3, pp. 409-430, May/June 2010.
- A. Goldsmith, M. Effros, R. Koetter, M. Medard, A. Ozdaglar, andL. Zheng, “Beyond shannon: the quest for fundamental performance limits of wireless ad hoc networks,” IEEE Commun. Mag., vol. 49,no. 5, pp. 195–205, May 2011.
- L. X. Cai, X. S. Shen, J. W. Mark, and L. Cai, “Capacity analysis and MAC enhancement for UWB broadband wireless access networks,”Elsevier Comput. Netw., vol. 51, no. 11, pp. 3265–3277, Aug. 2007.
- J. Zhang, J. Chen, and Y. Sun, “Transmission power adjustment of wirelesssensor networks using fuzzy control algorithm,” Wireless Commun.Mobile Comput., vol. 9, no. 6, pp. 805–818, June 2009.
- Y. Zhuang, J. Pan, and L. Cai, “Minimizing energy consumption with probabilistic distance distributions in wireless sensor networks,” in 2010INFOCOM.
- M. Grossglauser and D. N. Tse, “Mobility increases the capacity of ad hoc wireless networks,” in 2001 INFOCOM.
- A. E. Gamal, J. Mammen, B. Prabhakar, and D. Shah, “Optimal throughput-delay scaling in wireless networks—part I: the fluid model,”IEEE Trans. Inf. Theory, vol. 52, no. 6, pp. 2568–2592, June 2006.
- J. Mammen and D. Shah, “Throughput and delay in random wirelesss networks with restricted mobility,” IEEE Trans. Inf. Theory, vol. 53, no. 3, pp. 1108–1116, 2007.
- R. M. de Moraes, H. R. Sadjadpour, and J. Garcia-Luna-Aceves, “Throughput-delay analysis of mobile ad-hoc networks with a multicopy relaying strategy,” in 2004 SECON.
- D. M. Shila and Y. Cheng, “Ad hoc wireless networks meet the infrastructure: mobility, capacity and delay,” in 2012 INFOCOM.
- E. Perevalov and R. S. Blum, “Delay-limited throughput of ad hoc networks,” IEEE Trans. Commun., vol. 52, no. 11, pp. 1957–1968, Nov. 2004.
- X. Lin, G. Sharma, R. R. Mazumdar, and N. B. Shroff, “Degenerate delay-capacity tradeoffs in ad-hoc networks with brownian mobility,” IEEE/ACM Trans. Netw., vol. 52, no. 6, pp. 2777–2784, June 2006.
- M. J. Neely and E. Modiano, “Capacity and delay tradeoffs for ad-hoc mobile networks,” IEEE Trans. Inf. Theory, vol. 51, no. 6, pp. 1917– 1936, June 2005.
- R. Baldoni, R. Beraldi, G. Cugola, M. Migliavacca, and L. Querzoni,“Structure-Less Content-Based Routing in Mobile Ad HocNetworks,” Proc. Int’l Conf. Pervasive Services, 2005.
- D. Braginsky and D. Estrin, “Rumor Routing Algorthim for Sensor Networks,” Proc. First ACM Int’l Workshop Wireless Sensor Networks and Applications, 2002.
- A. Carzaniga, D.S. Rosenblum, and A.L. Wolf, “Achieving Scalability and Expressiveness in an Internet-Scale Event Notification Service,” Proc. 19th Ann. ACM Symp. Principles of Distributed Computing, 2000.
- M. Cilia, L. Fiege, C. Haul, A. Zeidler, and A.P. Buchmann,“Looking into the Past: Enhancing Mobile Publish/Subscribe Middleware,” Proc. Second Int’l Workshop Distributed Event BasedSystems, 2003.
- Jiajia Liu,Xiaohong Jiang,Hiroki Nishiyama,Nei Kato, “Throughput Capacity of MANETs with PowerControl and Packet Redundancy” IEEE transaction on wireless communications vol12,No.6,pp 3037-3041,june 2013.
- J. Andrews, S. Shakkottai, R. Heath, N. Jindal, M. Haenggi, R. Berry,D. Guo, M. Neely, S. Weber, S. Jafar, and A. Yener, “Rethinking information theory for mobile ad hoc networks,” IEEE Commun. Mag.,vol. 46, no. 12, pp. 94–101, Dec. 2008.
|