Keywords
|
| Security, Face Verification, Authentication, Self Organizing Feature Maps, Dynamic Bayesian Networks, Nodal points |
INTRODUCTION
|
| Security system needs to be concentrated more in a new technology aspect. Facial authentication is used instead of traditional password authentication methods to improve accuracy. Face recognition technology is the least intrusive and fastest biometric technology. It works with the most obvious individual identifier, the human face. Instead of requiring people to place their hand on a reader or precisely positioning their eye in front of a scanner, face recognition systems unobtrusively take pictures of people faces as they enter a defined area. There is no intrusion or delay, and in most cases the subjects are entirely unaware of the process. They do not feel "under surveillance" or that their privacy has been invaded. Each human face consists of distinct features called Nodal points. These nodal points are extracted from the input image and matched with nodal points of image in database. Similarities between these features are plotted as edge weight in directed acyclic graph. The weights in this second layer represent conditional probabilities values between a facial region and a feature vector, or between two facial regions or between two feature vectors. These weights are updated often using the training set of facial images of the same input image. This method would produce a more precise result when compared to existing facial detection mechanisms. |
PRELIMINARIES
|
| Bayesian networks are a concise graphical formalism for describing probabilistic models. We have provided a brief tutorial of methods for learning and inference in dynamic Bayesian networks. In many of the interesting models, beyond the simple linear dynamical system or hidden Markov model, the calculations required for inference are intractable. Two different approaches for handling this intractability are Monte Carlo methods such as Gibbs sampling, and variational methods. An especially promising variational approach is based on exploiting tractable substructures in the Bayesian network. Face verification using DBN consists of ‘N’ number of face images for a given age (A) is stored in the database. Then the observations of images at various time periods (A+1, A+2, A+3…) are converted into Dynamic Bayesian Network (DBN). Once all feature vectors assigned to local areas of a face image are captured, they are viewed as Visual Observations (VOs). |
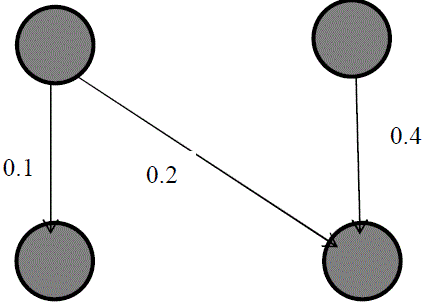 |
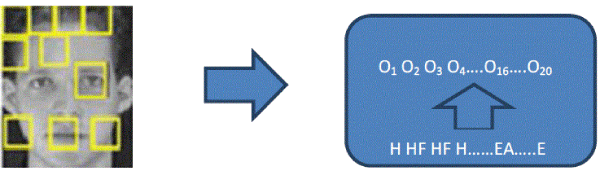
| Faceimage captured, are viewed as Visual Observations (VOs). Nine facial regions are considered: hair (H), between hair and forehead (HF), forehead (F), ears (EA), eyes (E), nose (N), cheeks (CH), mouth (M), and chin (C) are latent variables (or hidden states) and the block feature vectors Oi are the observables; all these variables represent vertices of a DBN which is an Hidden Markov Model (HMM). |
EXISTING SYSTEM
|
| I. VO Sequence Feature Extraction |
| A VO sequence is defined as a flow of symbols which represents either: temporal data, generated by some causal process or sequential data, where the generating mechanism of this sequence is unknown. Given a VO sequence as input, the first phase consists of selecting the VO sequence model which is a DBN that explains the VO sequence. A set of shapes is generated for different values of α that depend on the EDBN points’ density. Signatures vectors assigned to these similar shapes are computed and grouped together to form an equivalence class. The entire process is undertaken for all VO observation sequences forming the training set. In this application, one DBN is built for the same individual and its training is conducted via all facial images (at different ages) of an individual. |
 |
| II. Face DBN |
| A DBN represents a formalism that extends Bayesian networks to model probability distribution on collections of random variables Z1, Z2, Z3, .The weights in this DBN represent conditional probabilities values between a facial region and a feature vector, or between two facial regions or between two feature vectors. These weights are incrementally updated and learned using the training set of facial images of the same individual. |
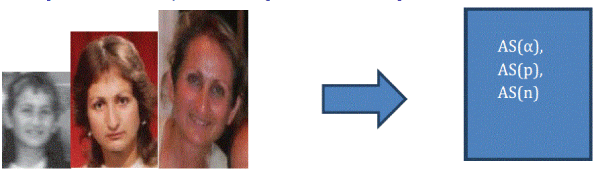
| III.α-Shapes Signature Vectors for p different α-values |
| The α-shape concept represents a formalization of the intuitive notion of “shape” for spatial point set data. The α-shapes define a hierarchy of shapes from a set of points (EDBN) that allows features’ multi scale modeling that are very useful in macromolecule structure exploration as well as in facial aging. A α-shape is a concrete geometric object that is uniquelydefined for a particular set of points. The construction of α-shapes is based on the notion of “ball” known also as “generalized disk”. The notion of a generalized disk is defined as follows. |
| 1) If α >0 but very large, then the generalized disk is a half-plane (very large radius). |
| 2) If α > 0 but not large, then the generalized disk is a closed ball of radius √a. |
| 3) If α <0, the generalized disk is the complement of a closed ball of radius √−α. |
 |
| Classification |
| Aset of shapes is generated for different values of α that depend on the EDBN points’ density. Signatures vectors assigned to these similar shapes are computed and grouped together to form an equivalence class. The entire process is undertaken for all VO observation sequences forming the training set. Since there are several different α values assigned to the same object; a set of signature vectors is generated. This set of vectors is represented by its mean vector. In other words, for a given TDBN, this classification problem consists of assigning an equivalence class to an input set of signature vectors characterized by its mean vector. |
| Diagram showing an individual’s face (at different ages) as an AR-HMM that is embedded in an EDBN whose p α-shapes signature vectors assignedto the individual’s DBN are extracted. These signature vectors form the equivalence class representing the individual’s face. |
| The cost of the topological feature extraction whose complexity varies linearly with the number of featuresare selected. This methodology allows viewing a DBN as a geometrical object captured by a hierarchy of α-shapes. Topological features can therefore unfold, and be utilized to improve classification accuracy. |
THE PROPOSED FACE VERIFICATION SYSTEM
|
| xThe proposed methodology allows viewing a DBN as a geometrical object captured by a hierarchy of α-shapes. Topological features can therefore unfold, and be utilized to improve classification accuracy. This symbiosis between a traditional DBN and a topological DBN represents an exploratory endeavor to connect discrete structures with continuous structures. |
| The proposed face verification system is described as in the following stages: |
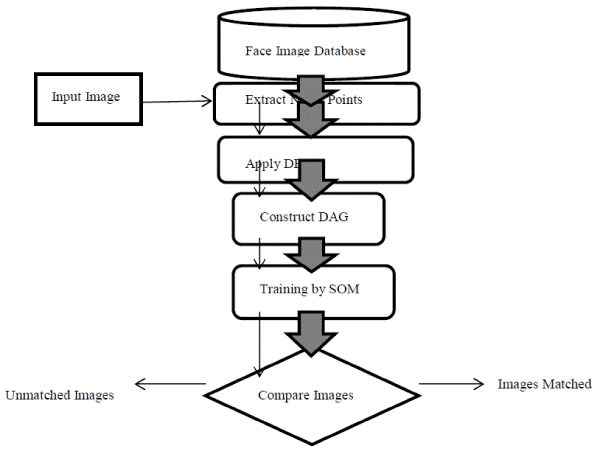
| Stage 1-Extract nodal points: |
| Every face has numerous, distinguishable landmarks, the different peaks and valleys that make up facial features. These landmarks are called as nodal points. Extraction of nodal points is the first step in our face verification system. |
| Stage 2-DBN and Construction of DAG: |
| The weights in this DBN represent conditional probabilities values between a facial region and a feature vector, or between two facial regions or between two feature vectors. These weights are incrementally updated and learned using the training set of facial images of the same individual. |
| Stage 3-Self Organized Feature Maps: |
| Each input vector from the training set is presented to the NN, and learning continues either some fixed number of cycles or while the difference between an input and the weights vectors reach some epsilon value. The difference between adjacent neurons decreases with time, and hence they organize into groups (maps) which correspond to one of the classes from the learning set. |
| Stage 4-Verification Process: |
| At this step, the differences between the input vector and all neurons vectors are calculated. After that, the NN chooses the winner-neuron, i.e., the neuron whose weights vector is the most similar to the input vector. |
 |
CURRENT & FUTURE USES OF FACE VERIFICATION SYSTEM
|
| `All Of this makes Face Verification Ideal For High Traffic Areas Open To The General Public, Such As: |
| i)Airports And Railway Stations |
| ii) Voting |
| iii) License Renewal |
| iv) Public Transportation |
| v) Financial Institutions |
| vi)Government Offices |
| vii) Businesses Of All Kinds |
CONCLUSION
|
| Thus, an efficient face verification technology is proposed for identifying human faces across ages which can reduce human effort in a great concern by eliminating the necessity of updating age databases periodically. Government agencies may use this system for Online voting system, License renewal and other state and central governance applications. The main feature of this proposed concept is that it can accept dynamic constraints thus improving the performance of the system with no single extra virtual samples needed to be generated. In addition to that it shows higher robustness against expression variance and partial occlusions. Also, it can provide partial invariance to translation, rotation, scale, and deformation in the image sample combined with other neural networks methods, so that more and more face recognition algorithm will use SOM in the future. |
References
|
- D. Bouchaffra, “Topological dynamic Bayesian networks: Application to facial aging,” in Proc. of IEEE Comput. Soc. Comput. Vis.PatternRecognit. Workshops, San Francisco, CA, Jun. 2010, pp. 1–8.
- D. Bouchaffra, “Topological dynamic Bayesian networks,” in Proc. 20th Int. Conf. Pattern Recognit., Istanbul, Turkey, Aug. 2010, pp.898–901.
- D. B. Percival and A. D. Walden, Wavelet Methods for Time Series Analysis. Cambridge, U.K.: Cambridge Univ. Press, 2006.
- Ricanek and T. Tesafaye, “MORPH: A longitudinal image database of normal adult age-progression,” in Proc. IEEE 7th Int. Conf.Autom. FaceGesture Recognit., Southampton, U.K., Apr. 2006, pp.341–345.FG-Net Aging Database.(2000) [Online]. Available: http://www.sting.cycollege.ac.cy/~alanitis/fgnetaging/Alpha-Shapes Software. (2002)
- Ramanathan.N and Chellappa.R (2010) “Face Recognition Using SOM”, in IEEE Conference on Computer Vision and PatternRecognition,Vol 7,No.21, pp. 612-624.
- NarayananRamanathan, and Rama Chellappa(2006) “Face Verification Across Age Progression”, IEEE Conference on Image Processing, Vol. 15, No. 11,pp. 3349-3361.
- Anil Kumar Sao and Yegnanarayana.B (2007) “Face OnVerification Using Template Matching”, IEEE Transactions Information Forensics . AndSecurity, Vol 2, No. 3, pp. 636-641.
- Chih-HsuehDuan, Chen-Kuo Chiang and Shang-Hong Lai(2013) “Face Verification With Local SparsE Representation”, IEEE Signal ProcessingLetters, Vol. 20, No. 2, pp. 177-180.
- Hahn-Ming Lee, Chih-Ming Chen(2013) and YungFeng Lu “ A Self-Organizing HCMAC Neural-NetworkClassifier”, IEEE TransactionsOn Neural Networks, Vol. 14, No. 1, pp. 15-27.
- Hua Huang and Huiting He (2011) “Super-Resolution Method for Face Recognition Using Nonlinear Mappings on Coherent Features”, IEEE TransactionsOn Neural Networks, Vol. 22, No. 1, pp. 542-553.
|