ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
Ms.M.Sabrabeebe1, Ms.C.Nancy Nightingale2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Web service composition is a web technology that combines information from more than one source into a single web application. This technique provides a special type of composition application that aims at integrating data from multiple data providers depending on the user’s request. In addition, DaaS (Data as a Service) composition may reveal privacy sensitive information. When enforcing a traditional privacy preserving model, such as privacy model and negotiation, the composed data would suffer from the problem known as the curse of privacy attacks. In this paper is used to propose a new dynamic privacy model in order to extend DaaS composition with privacy capabilities and to enable fast access to data resources on the Web. This dynamic privacy model makes it possible to dynamically reconcile the privacy capabilities of services when incompatibilities arise in DaaS composition. To validate the applicability of proposal through an implementation and a set of experiments.
KEYWORDS |
| Service Composition, DaaS Services, Privacy, Negotiation |
I. INTRODUCTION |
| Web services have recently emerged as a popular medium for data publishing and sharing on the Web. A web service is a software function provided at a network address over the web or the cloud, it is a service that is "always on" as in the concept of utility computing .Thereby providing a well-documented, platform independent and interoperable method of interacting with their data. DaaS (Data-as-a-Service) Services where services correspond to calls over the data sources. DaaS eliminates redundancy and reduces associated expenditures by accommodating vital data in a single location, allowing data use and/or modification by multiple users via a single update point. Initially used in Web mashups, the DaaS strategy is often used by commercial organizations. |
| Data as a Service or DaaS is a cousin of software as a service. The emergence of service-oriented architecture (SOA) has rendered the actual platform on which the data resides also irrelevant. This development has enabled the recent emergence of the relatively new concept of DaaS. A service provider that enables data access on demand to users regardless of their geographic location. Also called Data as a Service (DaaS), data services are similar to Software as a Service in that the information is stored in the cloud and is accessible by a wide range of systems and devices. Data services can enable the data to be accessed and/or updated by multiple users while ensuring a single point for updates. Potential drawbacks to data services include server downtime from the data service provider, data loss in the event of a disaster, and the security of the data, both in its stored location and in the transmission of the data among users |
| The DaaS approach delivers the following benefits: |
| Agility: Because data is easily accessible, customers can take immediate action and do not require in-depth understanding of actual data. |
| Affordability: Providers can construct a outsource in the presentation layer, which helps build highly affordable user interfaces and allows more feasible presentation layer change requests. |
| Data quality: Data accessibility is controlled through data services, which improves data quality, as there is a single update point. |
| 1.1 Web Service composition |
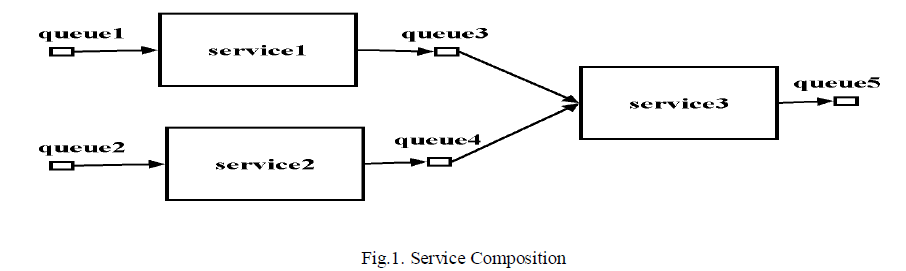
| Web service composition is a web technology that combines information from more than one source into a single web application. This technique provides a special type of composition application that aims at integrating data from multiple data providers depending on the user’s request. The automatic selection, composition, and interoperation of Web services to perform some task, given a high-level description of an objective. A web service is any piece of software that makes itself available over the internet and uses a standardized XML messaging system. XML is used to encode all communications to a web service. |
| For example, a client invokes a web service by sending an XML message, then waits for a corresponding XML response. Because all communication is in XML, web services are not tied to any one operating system or programming language Java can talk with Perl; Windows applications can talk with Unix applications. Web Services are self-contained, modular, distributed, dynamic applications that can be described, published, located, or invoked over the network to create products, processes, and supply chains. These applications can be local, distributed, or Webbased. Web services are built on top of open standards such as TCP/IP, HTTP, Java, HTML, and XML. Web services are XML-based information exchange systems that use the Internet for direct application-to-application interaction. |
 |
| 1.2 Challenges |
| Two factors exacerbate the problem of privacy in DaaS. First, DaaS services collect and store a large amount of private information about users. Second, DaaS services are able to share this information with other entities. Besides, the emergence of analysis tools makes it easier to analyze and synthesize huge volumes of information, hence increasing the risk of privacy violation. In the following, we use our epidemiological scenario to illustrate the privacy challenges during service composition. |
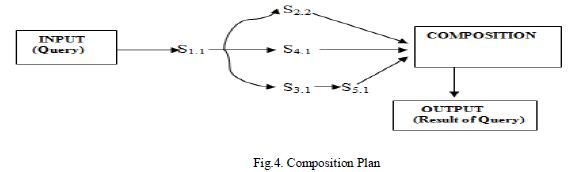
| Challenge 1: Privacy Specification. Let us consider services S4.1 and S5.1 in. The scientist considers both input and output parameters of S4.1 (i.e., SSN and DNA) as sensitive data. Let us now assume that this scientist states the following hypothesis: ”weather conditions” has an impact on H1N1 infection.” For that purpose, he/she invokes S5.1. The scientist may want to keep S5.1 invocation as private since this may disclose sensitive information to competitors. The aforementioned first challenge puts in evidence the need for a formal model to specify private data is and how it will be defined. |
| Challenge2: Privacy within compositions. Component services (that participate in a composition) may require input data that cannot be disclosed by other services because of privacy concerns. They may also have conflicting privacy concerns regarding their ex- changed data. For instance, let us assume that S1.1 states to disclose its data (SSN) to a third-party service for use in limited time. S3.1 meanwhile attests that it uses collected data (SSN) for an unlimited time use. Then, S1.1 and S3.1 have different privacy constraints regarding the SSN. This will invalidate the composition in terms of privacy concerns. |
| Challenge 3: Dealing with incompatible privacy policies in compositions. The role of the mediator is to return composite services with compatible component services with respect to privacy. |
| 1.3 Contributions |
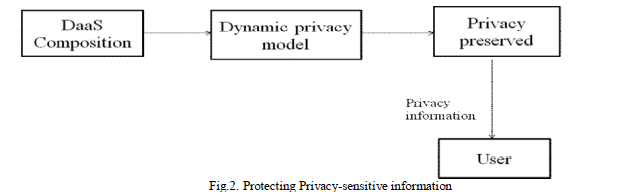
| Dynamic Privacy Model: This model deals with privacy in the web service composition. To protecting the composition results from the privacy attacks before the final result is returned to the user. |
 |
| DaaS Composition: Data as a Service (DaaS) is an information provision and distribution model in which data files (including text, images, sounds, and videos) are made available to customers over a network, typically the Internet. DaaS offers convenient and cost-effective solutions for customer- and client-oriented enterprises. DaaS eliminates redundancy and reduces associated expenditures by accommodating vital data in a single location, allowing data use and/or modification by multiple users via a single update point. Initially used in Web mashups, the DaaS strategy is often used by commercial organizations. Data as a Service or DaaS is a cousin of software as a service (SaaS). The emergence of service-oriented architecture (SOA) has rendered the actual platform on which the data resides also irrelevant. |
| This development has enabled the recent emergence of the relatively new concept of DaaS. The service provider that enables data access on demand to users regardless of their geographic location. Also called Data as a Service (DaaS), data services are similar to Software as a Service in that the information is stored in the cloud and is accessible by a wide range of systems and devices. Data services can enable the data to be accessed and/or updated by multiple users while ensuring a single point for updates. Potential drawbacks to data services include server downtime from the data service provider, data loss in the event of a disaster, and the security of the data, both in its stored location and in the transmission of the data among users. |
| Privacy Compatibility Checking: Capable of both assessing the compatibility and identifying incompatibility of service. Some personal information may be gathered when you register. During registration, this model asks for your email address and certain other personal information. |
| Privacy Compatibility Matching: To check the privacy compatibility of privacy policy and privacy requirement.PCM check the in assertions in Privacy Requirements with assertion in Privacy Policy for example assertion is service feature, preference, capability and requirements. |
| Negotiation to Reach Compatibility: The mediator basically discards any composition plan which is subject to privacy incompatibility from the set response. The main idea behind avoiding empty responses is to reach a compatible through a privacy-aware negotiation mechanism. Dynamically reconcile the privacy capabilities of services when incompatibilities arise in a composition. |
II. FORMAL MODEL FOR PRIVACY SPECIFICATION |
| A. Privacy Specification Model |
| In order to define an expressive model of privacy for web services, it is necessary first to examine the nature of data and to formally describe what we mean by privacy so that can argue that we protect such private data. In this case, the term privacy relates to the right of an entity to determine why, for whom, and for how long some information should be released. Due to the privacy subjectivity, each service has to identify which data are considered as private (noted as rs). If S provides some private data rs, then a set of privacy requirements applies to rs, and if S collects some private data rs, then a set of privacy policies also applies to rs. |
| 1) Privacy Rule: A privacy rule Ri is defined by a tuple (Ti, Di, Gi) where Ti is the topic of Ri giving the privacy facet. For instance, the topic can describe: 3 purpose, recipient, or retention. Purpose topic states the intent for which a given private data rs (collected or provided by S) will be used; the recipient topic mentions if and to whom rs can be revealed the retention topic specifies until when rs is stored by a third-party service. Then, for each topic Ti, a set Di defines the value domain of the topic. The definition of Di is based on an ontology domain. For example, we consider the privacy ruleR1 that corresponds to the topic T1 = recipient and the domainD1 = {public, government, private-lab, research-lab, hospital, university}. To define Gi ={total, partial} as a granularity indicator, which states whether or not the data in rs, to which Ri applies, represent the totality of the service input or output. In this paper, for the sake of simplicity, we only consider the case where Gi=total.4 The definition of privacy rules, called Rule Set (RS), is described independently of any private data. |
| 2) Privacy Assertion: The application of a rule Ri = (Ti, Di, Gi) to private data rs is a privacy assertion noted as A(Ri, rs) = pf. S specifies its privacy concerns for rs through A(Ri, rs). For example, let consider rs=DoB and R1 which corresponds to the topic T1 =recipient and the domain D1. A privacy assertion applied to rs = DoB through R1, which states that rs will be shared with government agencies and research-lab. |
| 3) Privacy Requirements PRS: A service S providing some private data rs as its output specifies a set of privacy requirements, denoted as PRS, in terms of usage expectations. |
| 4) Privacy Policy PPS: A service S requesting some private data rs’ (where rs’ = rs referring output data of S)as input specifies its privacy policy, noted PPS, stating how S is going to use rs’. |
| B. Privacy Annotation for DaaS |
| The web service description language (WSDL) standard gains considerable momentum as the language for web service description. However, WSDL provides no support for privacy description of services. Existing standards such as WS-security focus on “on an access control-oriented of privacy and do not offer the possibility for describing requirements and policies as with our model. Moreover, policy adaptation is not supported. In order to describe the privacy concerns of web services [8]. To exploit its extensibility elements to associate service operations, inputs, and outputs with their corresponding PRS and PPS. More precisely, we extend the operation, input and output elements with a privacy-reference attribute that contains a link to a privacy file, thus keeping a clear separation between the functional description of the service and its privacy concerns. |
III. SYSTEM ARCHITECTURE |
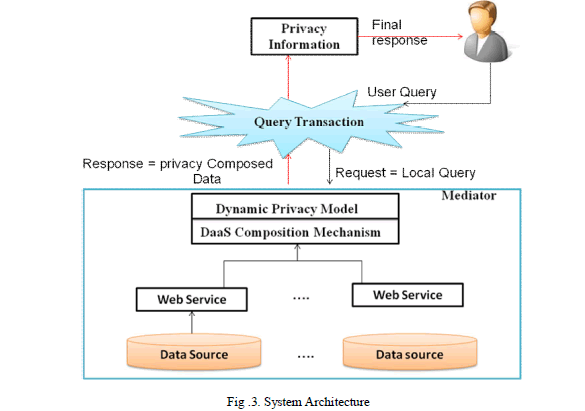
| The approach presented in this paper is implemented as a project which deals with the privacy preservation issue in P2P data sharing environments. This research where the need of data sharing is apparent for making better a health environment of people. To support the decision process multiple data sources such as the patient data, his social conditions, the geographical factors, etc. The data sources are provided by DaaS services and are organized with peers. DaaS services differ from traditional Web services, in that they are stateless i.e. they only provide information about the current state of the world but do not change that state. |
| When such a service is executed, it accepts from a user an input data of a specified format (“typed data”) and returns back to the user some information as an output. DaaS services are modeled by RDF views. Figure 3 summarizes the architecture of this project. The Multi-Peer Query Processing component is in charge of answering the global user query. The latter has to be split local queries (i.e., sub-queries) and has to determine which peer is able to solve a local query. Each sub-query is expressed in SPARQL. Each peer handles a Mediator equipped with a Local Query Processing Engine component. The mediator exploits the defined RDF views within WSDL files to select the services that can be combined to answer the local query using an RDF a query rewriting algorithm [2]. Then, it carries out all the interactions between the composed services and generates a set of composition plans to provide the requested data. |
 |
| Then, it carries out all the interactions between the composed services and generates a set of composition plans to provide the requested data. It deals with privacy not only at the data level (i.e., inputs and outputs) but also service level. In this paper to build upon this model two other extensions to address privacy issues during DaaS composition. The privacy model described in this paper is based on the model. |
IV. DAAS COMPOSITION |
| To Combines information from more than one service into a single web application. Combining data from different sources could potentially reveal privacy-sensitive information. To securely integrate data from different sources could potentially reveal privacy-sensitive information. To securely integrate private data from different data providers, whereas the integrated data still retains the essential information |
| A web service is any piece of software that makes itself available over the internet and uses a standardized XML messaging system. XML is used to encode all communications to a web service. For example, a client invokes a web service by sending an XML message, and then waits for a corresponding XML response. Because all communication is in XML, web services are not tied to any one operating system or programming language--Java can talk with Perl; Windows applications can talk with Unix applications. Web Services are self-contained, modular, distributed, dynamic applications that can be described, published, located, or invoked over the network to create products, processes, and supply chains. |
 |
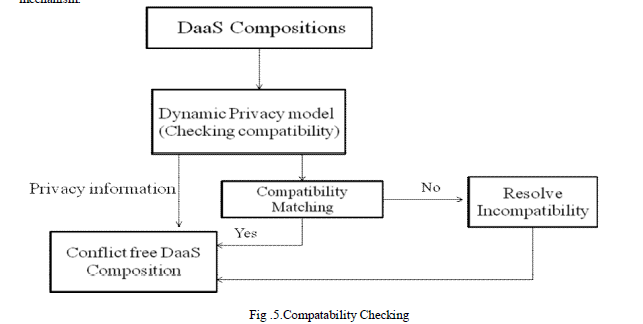
V. THE PRIVACY COMPATIBILITY CHECKING |
| This method is Capable of both assessing the compatibility and identifying incompatibility of service. Some personal information may be gathered when you register. During registration, this model asks for your email address and certain other personal information. To introduce the notion of compatibility between privacy policies and requirements. Then define the notion of privacy subsumption and present our cost model based privacy matching mechanism. |
 |
VI. PRIVACY COMPATIBILITY MATCHING |
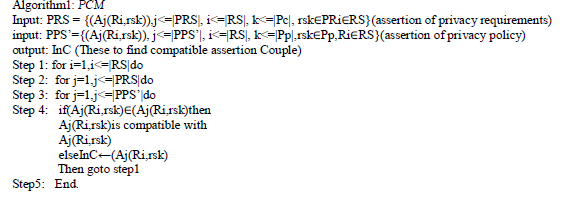
| To check the privacy compatibility of privacy policy and privacy requirement in DaaS Composition Privacy Compatibility Matching (PCM) check the in assertions in Privacy Requirements(PR) with assertion in Privacy Policy (PP) The example of assertion are service feature, preference, capability and requirements. |
| 6.1PrivacySubsumption: Let us consider a rule Ri = (Ti,Li,Di,Si). Defining an assertion A(Ri, rs) =( pf, g) for involving assigning value(s) from Di to the propositional formula pf of A. The value in Di. are related to each other. |
 |
VII. NEGOTIATION TO REACH COMPATIBILITY |
| The mediator basically discards any composition plan which is subject to privacy incompatibility from the set response. The main idea behind avoiding empty responses is to reach a compatible through a privacy-aware negotiation mechanism. Dynamically reconcile the privacy capabilities of services when incompatibilities arise in a composition. Compared to, in this paper, we revise the previous idea of negotiation and provide many improvements. The negotiation decision is cautiously taken according to a utility-based cost function defined by a service provider. |
VIII. CONCLUSION AND FUTURE WORK |
| In this paper, the proposed a dynamic privacy model for web services. This model deals with privacy at the DaaS. Composition to tackle the incompatibilities between privacy policies and requirements. Further, dynamic privacy must reveal with privacy sensitivity information whenever the privacy attack occur. Although privacy cannot be carelessly negotiated, it is still possible to negotiate apart of privacy policy for specific purposes. In any case, privacy policies always reflect the usage of private data as specified or agreed upon by service providers. As a future work, the aim at designing technique for protecting the composition results from privacy attacks in cloud computing. |
References |
|