ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
K.Adithya Narayanan, Monish Joel Singh, D.Kerana Hanirex, K.G.S. Venkatesan
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Our proposed approach tries to decrease the impact of SLA violation through a user discrimination approach and avoid entering the complex procedure of negotiation There will be no chance to get the unknown result or loss of result. We can measure the SLA violation in long term measuring. For simulations, we considered five different user types and five classes of virtual machines with different reliability level labels. A learning automaton is an adaptive decision-making unit located in a stochastic environment and the action selection is based on a specific Probability distribution which is updated according to environment the automaton receives by employing a particular action which hence increases the efficiency by reducing the maximum cost and by improving Quality of Service (QoS).
KEYWORDS |
| Qos(Quality of Service), SLA( Service Level Agreement) |
I. INTRODUCTION |
| In this project User satisfaction as a significant antecedent to user loyalty has been highlighted By many researchers in market based literatures. SLA violation as an significant factor can Decrease user’s agreement level. The amount of this reduce depends on user’s characteristics. So we have to present a new approach to reduce the impact of SLA violations on User’s satisfaction level, but not by decreasing number of SLA violations. Instead, we try to use Characteristics of users to decrease the impact of SLA violations on user satisfaction level. But Some of them are unknown to the service provider and selfish users are not interested to reveal Them truly. Most the works of literature ignore considering such characteristics and treat others Just based on SLA parameters. So, two users with dissimilar characteristics but similar SLAs have equal significance for the service provider. |
II. RELATED WORK |
| In this [1] reduce the number of samples that must be taken from the graph to construct the MCDS. [2] developed a model for the competitive interactions in service industries where firms cater to multiple customer classes or market segments with the help of shared service facilities or processes. [3] propose a new continuous action-set learning automaton and theoretically study its convergence properties and show that it converges to the optimal action. we first provide a mathematical framework for cellular learning automata and then study its convergence behavior. [5] we introduce asynchronous cellular learning automata and study its steady state behavior. Then an application of this new model to cellular networks has been presented.[6] we study a cellular learning automata model for which each cell has several learning automata.[7] providing quality of service and service level agreement facilities on top of unreliable, intermittent Cloud providers. [8] proposes a two-level resource management system with local controllers at the virtualcontainer level and a global controller at the resource-pool level.[9] a learning automata based data aggregation method in sensor networks when the environment's changes can not be predicted beforehand will be proposed. propose a solution to the problem of dynamic point coverage using irregular cellular learning automata.[11] discussing the use of the WTP methodology in 2 distinct contexts — cost-benefit analysis (CBA) and market research. we tackle the resource allocation problem within a datacenter that runs different type of application workloads, particularly non interactive and transactional applications.[13] introduced two classes of learning automata based algorithms for adaptive selection of value for inertia weight and acceleration coefficients. proposed model extends existing Push-Pull- Mooring Theory of consumer switching by incorporating the influence government policy, switching intention abortion factors.[15] extend prior research by developing a conceptual framework linking all of these constructs in a businessto- business (B2B) service setting. |
III. EXISTING SYSTEM |
| To demonstrate the usability of our approach, we provided some mathematical simulations in decisive situations. Decisive situation means a condition in which a service provider has faced with unexpected lack of resources and SLAviolation for some users is the foreseeable, Service provider has two options: neglecting the queued requests or forcing some existing VMs to discharge their resources. In the final case, service provider can assign the unconfined resources to the important queued requests. Together, cases would cause SLA violations, but the users who suffer from violations are different. Since users have different characteristics, so user satisfaction level under the two mentioned options will be different. Our approach presents a method to decide which VMs should be enforced to release their resources [12]. |
| The branch and bound method it that is similar to the BFS method, it can be generated using the sub nodes. In some cases the time complexity is too low in a branch and bound technique, so we are using the various optimal solutions to satisfy the problem [15]. Branch and bound is a methodical system for solving optimization inconvenience B&B is relatively a general optimization technique that applies where the greedy method and dynamic programming fail. Nevertheless, it is much slower. Certainly, it frequently leads to exponential time complexity in the worst case. The drawbacks are : |
| (1) The service cost is more. |
| (2) The Quality of Service is low, because of SLAproblem. |
| (3) In existing system we have to use a genetic algorithm, A Genetic Algorithm (GA) is a search heuristic that mimics the process of natural selection, in order to find the SLA violation problem [19]. |
IV. PROPOSED SYSTEM |
| In Proposed System, Clearly the user based approach tries to satisfy more risk, unfavourable users pay a lesser amount of penalty,while this is not the case for random approach, The total number of paid penalties in random approach is greater than user based approach [19]. This simulation contains user types with different Willingness To Pay(WTP), but similar risk aversion. The average WTP of the users which their requests arc assigned to virtual machines from different classes using the user based approach. Comparing the results, we can see the requests from users with higher WTP are assigned to virtual machines with higher reliability. This helps service provider to satisfy the users with higher WTP and improve its profitability. Supple and dependable management of SLA agreements is of principal importance for both Cloud providers and consumers [20]. |
V. PROPOSED SYSTEM ARCHITECTURE |
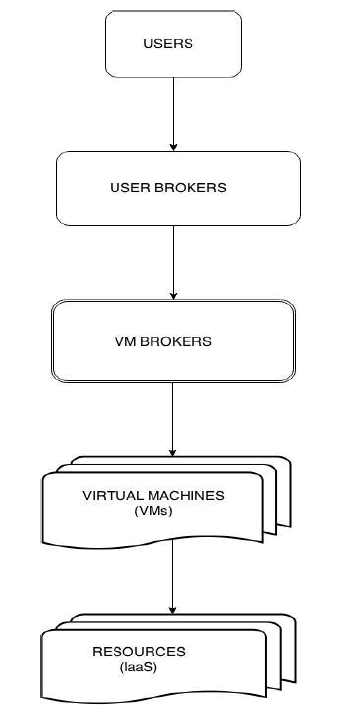 |
A. Finite Action-Set Learning Automaton |
| A learning automaton is an adaptive decision-making unit located in a stochastic environment,FALA is type of variable LA that its action-set is always considered to be finite. This type of LA has been studied extensively in many applications. The learning algorithm will be called linear reward- penalty or LR_p if (a=b). In case of a >> b (a is much greater than b) , we call it the learning reward-exponently or and finally if they are called linear reward-Inaction algorithms [26]. |
Algorithm: 1 Finite Action Learning Automaton Function |
| Input: VM_ID: ID of the VM to deploy in a high availability node MðÞ: Deployment profile function |
| Output: Satisfaction degree of constraint |
| 1: host ID: ¼ M(VM_ID) |
| 2: satisfaction: ¼ 0; |
| 3: if (Host Is HAServer (host_ID)) then |
| 4: Satisfaction: ¼ 1:0; |
| 5: return satisfaction; |
| 6: end if |
| 7: if (HostHasRAID(host_ID)) then |
| 8: satisfaction þ ¼ 0:2; |
| 9: end if |
| 10: if (Host Has Redundant Power Supply (host_ID)) then |
| 11: satisfaction þ ¼ 0:2; |
| 12: end if |
| 13: if (Host Has Multiple Network (host_ID)) then |
| 14: satisfaction þ ¼ 0:2; |
| 15: end if |
| 16: return satisfaction; |
| The implementation details of the HighAvail constraint are not revealed to the consumer as they are specific to each cloud infrastructure. Whenever one or more assumptions regarding the high availability of the hardware are outdated, possibly due to major changes in the infrastructure (e.g., all hosting nodes become equipped with RAID),we have to provide new implementations for the affected utility functions [28]. |
| Administrative constraints are also realized as utility functions. These constraints serve a dual purpose as they can introduce high-level policies and assist in administration tasks. For instance, EmptyNode relieves a hosting node of VMs. ReduceDist enforces the high-level policy of clustering VMs of the same user on hosts that may not be far apart in terms of network hops; this is done to limit major traffic to be routed over long-haul physical networks. We have realized both user and administration constraints as utility functions in similar fashion to Algorithm 1;for brevity, we omit their detailed discussion here. Such functions are expected to work in a plug-and-play fashion [29]. |
Advantages: |
| (1) The proposed system reduces the maximum cost. |
| (2) It improves the Quality of Service (QoS). |
| (3) It also Improves the Quality of Service (Qos) between cloud server and client. |
| (4)The proposed system uses complex algorithm to improve the QoS. |
VI. RESULT ANALYSIS |
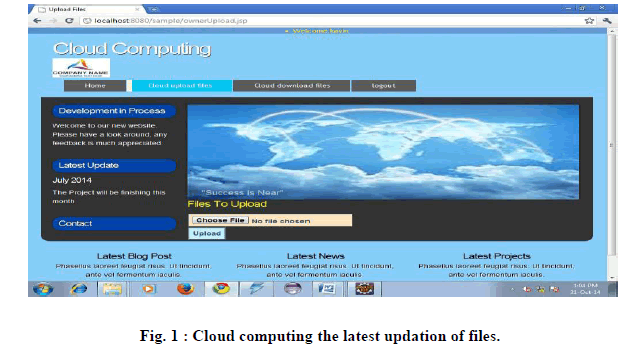
| • After the user selectingan plan, and after the plan is approved by the Admin, the user can start uploading the data files to the Cloud System, the below image represents the upload page where the data can be uploaded by the user. |
 |
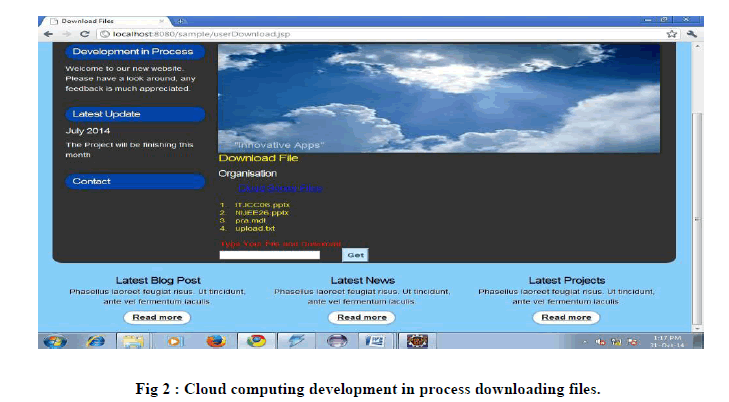
| • After the user's data is uploaded to the Virtual Machine, the allocated memory is where the user's data will be stored according to the user's data storage selection. The user can download the data by merely inserting the file name and receiving the file [35]. |
 |
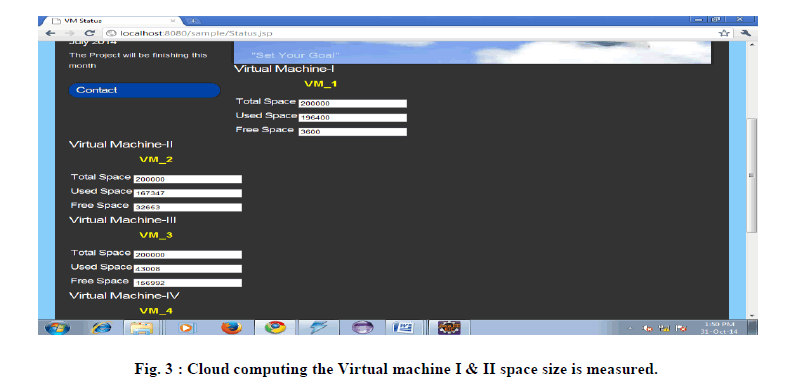
| • The user, after uploading the files to the Virtual Machine, they can download their data, the user can also check their capacity remaining in the Virtual Machine, according to the remaining capacity they can opt for another plan or proceed to upgrade their current plan [30]. |
 |
| • The Admin can get the users storage plan request and then proceed to allocating more memory for the user's profile. Depending on the plan selected by the user, the Admin allocates the specified bytes to the user's profile [39]. |
 |
VII. CONCLUSION & FUTURE ENHANCEMENTS |
| In this paper we considered users satisfaction level as an important factor in profitability for cloud service providers. We tried to investigate influence of two characteristics in user satisfaction level. Since these characteristics, called willingness to pay for service and willingness to pay for certainty, are unknown for service providers, so new methods for estimation of them are provided. Also a new approach presented to reduce impact of SLA violations [40]. So we produce Interactive model, a hint-based VM scheduler that serves as a gateway to IaaS- clouds. Users are conscious of the flow of processes executed in their virtual infrastructures and the position each VM plays. This data is sent to the cloud service, as hints, and helps drive the position of VMs to hosts. Hints are also engaged by the cloud administration to state its own deployment choices. The Interactive model adds consumer and administrative hints to hold peak performance, address performance bottlenecks, and efficiently apply high-level cloud policies such as load balancing and energy savings. An event-based system allows Interactive model to rearrange VMs to adjust to differences in the workloads served. Our advance is associated with the separation of concerns IaaS-clouds introduce as the users remain uninformed of the physical cloud structure and the properties of the VM nodes. Our estimate, using simulated and real private Iaas-cloud environments, shows considerable gains for Interactive model both in terms of performance and power utilization [41] |
| In the future, we plan to: 1) inspect different constraint agreement approaches to address scalability issues present in large systems; 2) offer deployment hints that will effectively handle the deployment of virtual infrastructures in the context of real large cloud installations; 3)We investigate the mentioned advance in a resource distribution situation. The conducted experiments demonstrate that in critical situations, the estimated characteristics can help the service provider to decide about which users should be served and which ones can be discarded. This can raise user satisfaction level as much as possible and leads to more loyalty of users and higher profit for service provider. |
VIII. ACKNOWLEDGEMENT |
| The author would like to thank the Vice Chancellor, Dean-Engineering, Director, Secretary, Correspondent, HOD of Computer Science & Engineering, Dr. K.P. Kaliyamurthie, Bharath University, Chennai for their motivation and constant encouragement. The author would like to specially thank Dr. A. Kumaravel, Dean , School of Computing, for his guidance and for critical review of this manuscript and for his valuable input and fruitful discussions in completing the work and the Faculty Members of Department of Computer Science &Engineering. Also, he takes privilege in extending gratitude to his parents and family members who rendered their support throughout this Research work. |
References |
|