Keywords
|
| Clustering, Event detection, Multi-transmission, Reliability |
INTRODUCTION
|
| In a wireless sensor network there will be a large number of sensor nodes, which are densely deployed either inside the phenomenon of interest area or very close to it [1]. The main objective of every wireless sensor networks is to make the destination or sink aware about the occurance of event (which can be a laptop, PC and so on). The main drawbacks of most of the existing methods are that there is no reliable event transmission, no real-time requirement, and the data send to the sink may be large. In this paper, we propose a reliable and congestion aware event detection protocol to send infrequent events in a more reliable manner. |
| Wireless sensor networks is an important emerging technologies for providing observations on the physical world with low cost and high accuracy [2]. The main important applications of wireless sensor network are environment monitoring (fire detection etc), military intrusion detection etc. The heart of WSNs is sensor nodes which is capable for sensing, processing and communication. Depending on their sensing components, sensor nodes can be used to monitor different phenomena like temperature, light and humidity [3]. The motive of processing module of sensor node is to do computations based on the sensed value and also on the received values from neighbour nodes and in communication module the sensor nodes send and receive the information from or to neighbouring nodes and sink [2, 3]. Routing has been carried out in the sensor networks with the intention of conserving energy. The contributions of our RCAETP protocol include: |
| 1) Energy conservation. |
| 2) Congestion aware event transmission. |
| 3) Event decisions are performed in the event area. |
| 4) Data aggregation is performed at the Cluster Heads (CHs). This leads to less energy utilization. |
| 5) A novel multi-transmission scheme is used to ensure the reliable packet transmission. |
| The rest of this paper is organized as follows. Section II presents efficient event detection protocol (EEDP) and our assumptions. Section III briefly reviews related work on event detection and some reliable transmission protocols in a wireless sensor network. Section IV introduces the protocol architecture and its operation. The conclusion of the paper is given in section V. |
PROBLEM STATEMENT
|
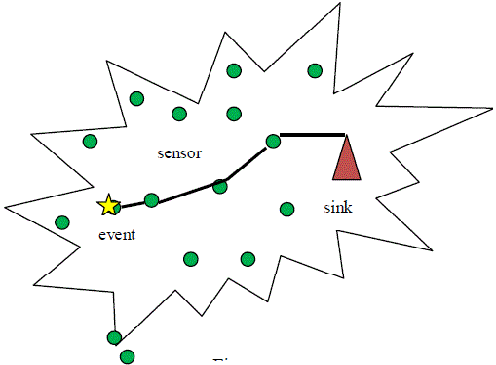
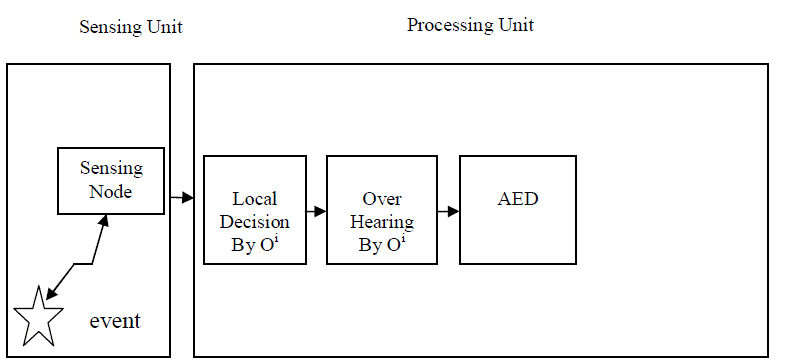
| In an Event Driven Wireless Sensor Network (EDWSN) or WSN the decision about occurance of an event can be made among sensor nodes (node centric) or by the sink (sink centric). For event monitoring in WSN, we have to solve two main problems namely accurate event detection and reliable transmission of packets. In most of the methods the nodes nearer to the event take decisions about an event based on the observed values by them and one of the sensor node called decision-made node will send the event packet or alarm packet to the destination [4] after cooperative decision making as shown in Fig. 1. The main drawback of this approach is that only one node from event region is sending packet to the sink which is not that much of reliable in case of path failure and packet loss. |
RELATED WORKS
|
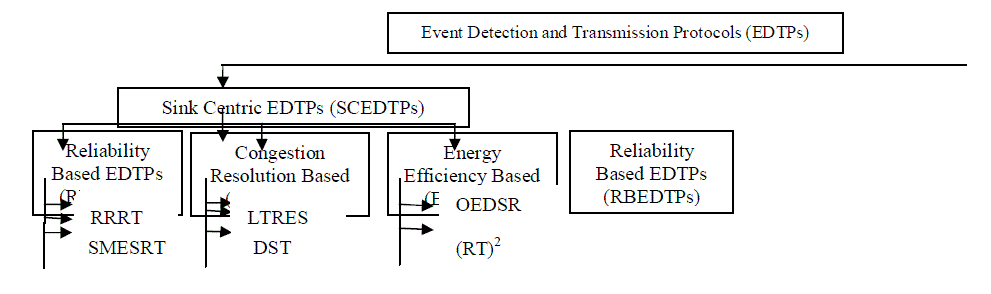
| Several protocols have been proposed in the literature for the event detection and transmission. These protocols can be categorized into: |
| • Sink Centric Event Detection and Transmission Protocols (SCEDTPs) and |
| • Node Centric Event Detection and Transmission Protocols (NCEDTPs) |
| These EDTPs can be further classified as follows [5]: |
Sink Centric EDTPs (SCEDTPs)
|
| The sink centric protocols are classified under the constraints of reliability, congestion control and energy efficiency like 1) RBEDTPs 2) CRBEDTPs and 3) EEBDTPs. |
| 1) RBEDTPs: They perform reliable event detection at the sink based on the number of packets received from the sensor nodes based on different approaches. The protocols coming under this category are: |
| • ESRT |
| • RRRT |
| • SMESRT |
| ESRT (Event-to-Sink Reliable Transport) Protocol: ESRT performs the reliable event detection at the sink based on reporting frequency f adjustments under four network states such as 1) No Congestion, low reliability (NC, LR)- increase f multiplicatively, 2) No Congestion, High Reliability (NC, HR)- decrease f conservatively, 3) Congestion, High Reliability (C, HR)- decrease f carefully 4) Congestion, Low Reliability (C, LR)- decrease f exponentially and 5) Optimal Operating Region (OOR)- stay [6]. The disadvantages with ESRT are it follows central control method which is not energy efficient and in a sensor field with multiple event occurring at the same time the adjustment of f for all the sensor nodes will not perform better as the events are independent to each other and also the event occurring area may not be same. |
| RRRT (Reliable Robust and Real-Time) Protocol: In RRRT protocol [7], author proposes two concepts such as eventto- action delay bound to meet the application specific deadlines and a combined congestion control mechanism which provide the dual purpose of achieving reliability and conserving energy. |
 |
| In event-to-action delay bound it is based on assumptions such as Observed delay-constrained event reliability (DRo): It is the number of packets received at the sink within a certain delay bound in a decision interval, Desired delayconstrained event reliability (DRd): It is the minimum number of packets required for reliable event detection within a certain delay bound and Delay-constrained reliability indicator (α): i.e.,α= DRo/ DRd. If the observed delay constrained event reliability is higher than the reliability bound i.e., DRo>DRd then the event is reliably detected within a specific delay bound [7]. The drawback with RRRT is congestion detection and control mechanisms lead to extra overhead. |
| SMESRT (Simultaneous Multiple Event-to-Sink Reliable Transport) Protocol: SMESRT [8] is a protocol designed to accomplish simultaneous multiple reliable event detection with a payload control component that serves the dual purpose of less traffic at the sink and conserving energy. With SMESRT the sensor nodes detects the same event sends the event packets to CH at a predefined reporting frequency for that particular period or duration. The CH informs the sink about the network condition. The SMESRT performs the payload control at the CHs. The main drawback with SMESRT is assignment of different reporting frequency leads to extra overhead. |
| 2) CRBEDTPs: Perform event detection and transmission under various congestion or traffic conditions. These protocols include: |
| • CODAR |
| • LTRES |
| • DST |
| CODAR (Congestion and Delay Aware Routing) Protocol: The main objective of CODAR is to improve reliability and the timeliness of the data transmitted by critical nodes through congestion avoidance and mitigation [9]. Each node in event occurring region broadcasts its location and Relative Success Rate (RSR) value using control packets during a fixed interval [9]. The RSR helps to mitigate congestion by choosing lightly congested nodes. Disadvantages of CODAR are not suitable for large number of critical nodes and less energy efficient. |
| LTRES (Loss Tolerant Reliable Event Sensing) Protocol: The LTRES performs the congestion control based on the node-end source rate adaptation mechanism: Node-end Distributed Source Rate Adaptation: The sink calculates the Event-sensing Fidelity level (ESFE) and sends the event sensing reliability measure to the Enodes. Based on this Enodes update their source rate in order to ensure the congestion control [10]. The main disadvantages of LTRES Less energy efficient due to source rate adaptation mechanism. |
| DST (Delay Sensitive Transport) Protocol: The DST mainly involves two mechanisms 1) Congestion control and detection mechanism. In this for any sensor node whose buffer overflows due to excessive incoming packets is said to be congested and it informs the sink congestion condition by a Congestion Notification (CN) bit the event packet header and, 2) Real-time event transport mechanism: DST performs real-time event detection under event-to-sink delay bound. The main components of event -to-sink delay bound are event transport delay and event processing delay [11]. According to DSRT, for reliable and timely event detection the event-to-sink delay bound should be greater than or equal to the sum of both event transport delay and event processing delay. The disadvantage of DST is the reporting frequency rate adjustment mechanism leads to overhead. |
| 3) EEBDTPs: These protocols perform event detection and transmission with low energy usage. Some protocols coming under this includes: |
| • OEDSR |
| • (RT)2 |
| OEDSR (Optimized Energy-Delay Sub-network Routing) Protocol: The OEDSR, the nodes are either in idle or sleep mode, but once an event is detected, the nodes near the event become active and start forming sub-networks and this formation of inactive network into a sub-network saves energy because only a portion of the network is active in response to an event [12]. |
| (RT)2 (Real-Time and Reliable Transport ) Protocol: The (RT)2protocol uses the new idea of event-to-action delay bound which is the sum of the event transport delay, event processing delay, and action delay [13]. The (RT)2 protocol operation is based on two states namely Start-Up state: In this state the sender transport a probe packet toward the receiver to capture available transmission rates and Steady State: It consists of four sub states namely increase, decrease, hold and probe. During the increase state the sender increases the transmission rate according to the feedback from the sink. In the decrease state the sender reduces its transmission rate according to the feedback coming from the sink. The disadvantage of (RT)2 is the configuration adjustment nature of (RT)2 leads to extra delay. |
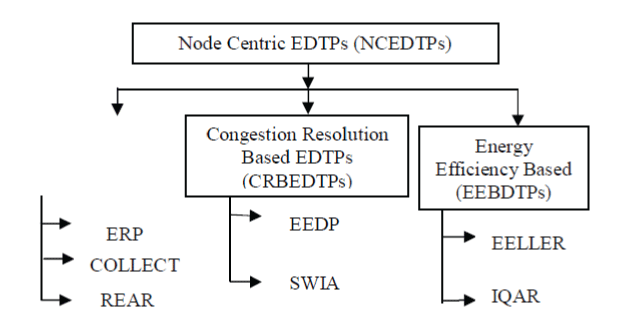
Node Centric EDTPs (NCEDTPs)
|
| With these protocols the sensor nodes makes the final decision from the data received to it and send their result to the sink. NCEDTPs can be classified into 1) RBEDTPs, 2) CRBEDTPs, and 3) EEBEDTPs. |
| • 1) RBEDTPs: The protocols coming under this category are: |
| • ERP |
| • COLLECT |
| • REAR |
| ERP (Event Reliability Protocol): The ERP works based on a mechanism called Region-based selective retransmission mechanism: When the sensor nodes senses the event it will send the detected event to the next hop node and then this next hop node put the event packet in its buffer and the packet at the head of its buffer is transmit to the next hop. When the node hears that the next hop node transmitting the packet it has sent, it is an implicit acknowledgement that the packet is forwarded successfully [14]. And the node then removes the packet from the queue end and the next packet in the queue is processed. The region-based selective retransmission is based on the source ID, source location and event’s time at a source of a particular packet to be retransmitted. By observing the packets in the queue of a particular node the distance between the nodes are calculated and check whether they are in they are in-range of one another. The disadvantage with ERP is less energy efficient. |
| COLLECT (COLLaborative Event deteCtion and Tracking) protocol: The COLLECT consists of three procedures vicinity triangulation, event determination, and border sensor selection. The vicinity triangulation procedure enables the same kind of sensor to construct the respective attribute region, named logical triangle to accurately identify the event region [15]. In event determination procedure a sensor node locally determines the existence of the event according to its sensor data and received messages from the different kinds of sensors within its logical triangles and the border selection procedure aims to select the border sensors to stand for the event boundary [18]. When an ordinary node detects an event it becomes an alert node and send an ATR packet to its neighbours which consists of the ID of the sensor node, its location, the attribute it detected, and the and the timestamp when it detects the event attribute. Based on this information the sensor nodes participate in the vicinity triangulation [5]. The main disadvantage with COLLECT is it cost-effective because of no need of sensor redeployment. |
| REAR (Reliable Energy Aware Routing) Protocol: In [16] it has been proposed that the REAR protocol allows each sensor node to confirm success of data transmission to other sensor nodes by supporting the DATA-ACK oriented packet transmission. The sink node sends the ACK packet to the sensor nodes which indicates the successful receiving of event packets. If the sensor node receives the ACK within the ACK timeout, it transmit new sensing event packet. If ACK does not receives within the desired time it considers it as transmission error and it assumes that the event packet which already has been send is lost. If data transmission to next hope fails the node sends an error message packet to the source node. Then the source node receiving the error message resends it with a second path and thus the reliability of data transmission is guaranteed [16]. The Disadvantage with REAR is the use of queues and estimators leads to extra overhead. |
| 2) CRBEDTPs: The protocols coming under this category are: |
| • EEDP |
| • SWIA |
| EEDP (Efficient Event Detection Protocol): With this protocol the sensor nodes nearer to the event occurring region senses the event and makes their own decision based on Simple Decision Rule (SDR) that is whether the event has happened or not and makes further accurate decision based on Composite Decision Rule (CDR) [4]. The event reliability is achieved by using a method called dynamic multi-copy scheme. EEDP is mainly based on two procedures Primary Detection Procedure (PDP) and Emergency Routing Procedure (ERP). In PDP the accurate event decision is made based on SDR and CDR and in ERP the event packet is forwarded to the sink by using greedy approach and for reliability simple dynamic multi-copy scheme has been used. The disadvantage with EEDP is less reliability due to only one decision node sends the event information to the sink. |
| SWIA (Stop-and Wait-Implicit Acknowledgement) Protocol: The SWIA protocol does not allow the sensor node to send the next packet before it received an ACK packet for the previous packet. The SWIA protocol makes the use of implicit acknowledgement [17]. The iACK mechanism exploits the broadcast nature of wireless sensor network. In iACK mechanism the sensor node after transmitting the packet listens to the channel transmission of packets and thus reduces network traffic. Disadvantage of SWIA is the use of iACK mechanism provides some delay in the network performance [5]. |
| 2) EEBEDTPs: The protocols coming under this category are: |
| • EELLER |
| • IQAR |
| EELLER (Energy Efficient-Low Latency Express Routing) Protocol: During the event detection the detected data is forwarded hop-by-hop through cluster heads. The EELLER uses hierarchical routing to perform energy-efficient routing in an event driven wireless sensor networks. In hierarchical routing procedure the high energy nodes are used to send the information and the low energy nodes is used to sense the event [18]. The EELLER mainly consists of two phases constructing expressways and cluster formation and data communication. During the first phase the first hope and the second hope is selected based on the link factor, where link factor is the ratio of the energy of the node to the distance to the sink. During the second phase of EELLER, it provides a better data transmission after data aggregation and removing redundancy by the cluster heads. Disadvantage of EELLER is less reliability. |
| IQAR (Information Quality Aware Routing) Protocol: Unlike other aggregation-based schemes IQAR consider the information content of data during data aggregation and forwarding [19]. The IQAR protocol has been adopted tree based approach and its objective is to detect event in a sensor network. The information quality is concerned with the accuracy of the event information. In this each sensor nodes independently detects and collects data about an event and makes a per-sample binary decision i.e., whether the event has happened or not. If there is an event the result of persample binary decision will be 1 else 0. |
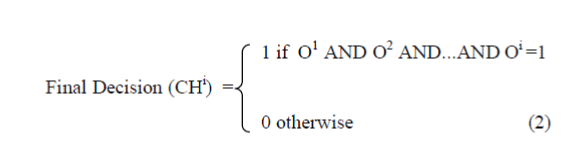 |
| If the final decision in each CHi=1, then we can say that an event has happened and this decision is based on the overhearing of packets from their neighbourhoods. |
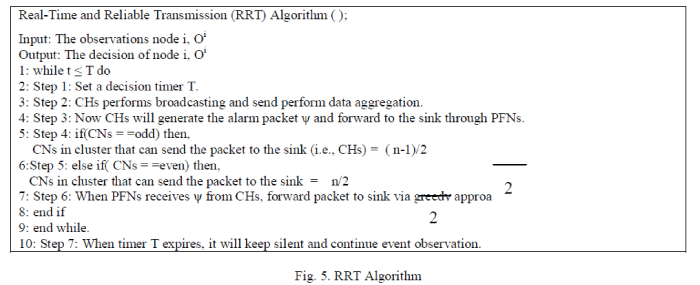
Real-time and Reliable Transmission (RRT)
|
| The RETP performs real-time event detection and transmission by setting a timer for each node. In most of the techniques there is no that much of reliability is achieved because only one node in the event region is sending event packet to the sink else all of the nodes in the event region sending event packet to the sink. In the first case if the packet is lost by a transmission error or link failure it doesn’t reach to the destination. The second case causes to congestion in the network. These all will leads to unnecessary retransmission. In order to improve the event packet reliability it can be possible to send more than one sensor nodes called decision made nodes the event packet to the sink knows as multitransmission. There are two cases: |
| Case 1: If the event region contains odd number of sensor nodes, then the total number of nodes in the cluster group can send event packet are: |
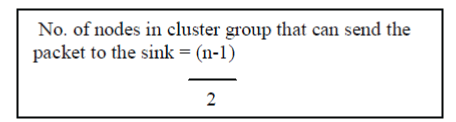 |
| For example if the number of sensor nodes in the event coverage area is 7 then a total of 3 decision made nodes can send the packet to the sink which is more reliable than sending single packet by a single node. |
 |
| Case 2: If the event region contains even number of sensor nodes, then the total number of nodes in the cluster group that can send event packet are: |
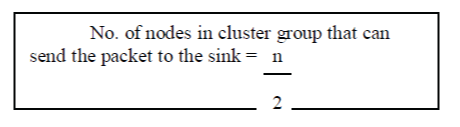 |
| Where n is the total number of sensor nodes in the event region. For example if the number of sensor nodes in the event coverage area is 6 then a total of 3 decision made nodes can send the packet to the sink which is more reliable than sending single packet by a single node (Fig 4). The RRT algorithm is as shown in Fig 5. |
| With these two concepts of Reliable Transmission (RT) at the same time it is possible to send more than one packet from the event region at the same time which will increase the chance to receive the packet to the sink than sending a single packet from the event region. For routing of packets greedy approach has been used. |
| Greedy Approach: In this routing technique each CHs choose the next neighbour node to forward the packet, then that node will chose the next one and so on. The main benefit with this approach is that it reduces the time delay. Where time delay is the time taken between sending and receiving the packet. |
PERFORMANCE EVALUATION
|
Simulation Setup
|
| We have performed simulations using the tool ns-2 to evaluate our proposed ideas. The simulation parameters that we have chosen are summarized in table I. |
| The simulation we have performed focus on a WSN which collects and reports data with low frequency to the sink. The network considered here has a total of 35 nodes with a single sink represented by a maroon colour. If for example 1, 19 and 34 has been formed as one cluster and by using formula (n-1)/2 the node 34 has been chosen as CH randomly and the data aggregation is taking place in CH only. Similarly node 21, 22, 26 and 27 has been detected one event in common and they forms one cluster. In this by using the formula (n)/2 nodes 26 and 27 has been elected as CHs for event packet transmission and the data aggregation is taking place among 26 and 27. |
Simulation Results
|
| Delivery Ratio: The packet delivery ratio is defined as total number of event packet received by sink node to the total number of event packet send by the source nodes or CHs i.e., |
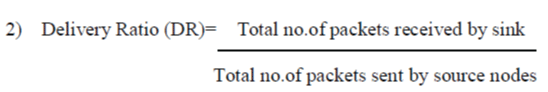 |
| The DR with and without RETP under various channel conditions is as shown in Fig. 6. In order to evaluate the performance under different network condition, the loss rate probability of the channel is varies from 0 to 0.12 with a step of 0.02. By using RRT algorithm event source packets are limited by the RETP protocol. |
| Thus the whole DR is improved than other traditional protocol. The DR usually decreases whenever the loss rate of the channel increases. In our proposed RETP protocol, the RRT algorithm is used to reduced the traffic by limiting the number of packets send to the sink node. And thus can receive the event packets more reliably and also DR is obviously improved and then the latency is reduced correspondingly as fewer packet transmissions and network congestion. |
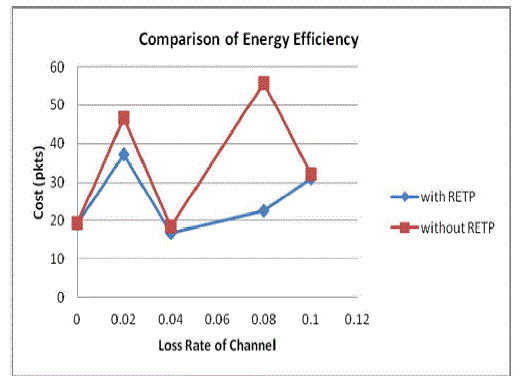
| Energy Efficiency: The RETP protocol has been used clustering concept which helps to increase the energy efficiency of the network. In RETP the data aggregation is taking place only in selected number of nodes. And not all the nodes are participating in the network at the same time, this leads to decrease the excess energy utilization. Fig 7 shows comparison of network energy with and without RETP. |
CONCLUSION
|
| In this paper, we have proposed a reliable event transmission protocol (RETP) in an wireless sensor networks to perform accurate event detection and reliable event packet transmission. The accuracy is achieved by a procedure called accurate event detection (AED) and the real-time and reliable is achieved by a method called Real-time and Reliable Transmission (RRT). The accurate decision is made with the local broadcasting messages and to improve the reliable transmission a multi-transmission scheme has been used. |
| |
Tables at a glance
|
 |
| Table 1 |
|
| |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 5 |
Figure 7 |
|
| |
References
|
- Akyildiz, W.Su, Y. Sankarasubramanian, and E. Cayirci,“A survey on sensor networks”,IEEE Commun. Mag., vol.40, no.8, pp. 102-114, August, 2002.
- Providing Reliable Data Transport for Dynamic Event Sensing in WSN”, Yuyan X, Byrav R and Yong W, IEEE,2008.
- Muhammad AdeelMahmood, WintsonSeah, “Reliability in Wireless Sensor Networks: Survey and Challenges Ahead”, ELSEVIER JOURNEL, February 8, 2012
- Lulu L, Deyun G, Hongke Z, Oliver W.W.Y, “Efficient Event Detection Protocol in Event-Driven WSN,” IEEE Sensor Journal, vol.12, no.6, pp. 2328-2337, June.2012.
- Krishna Priya.K.C and Sebastian Terence, “A survey on event detection and transmission protocol in an event driven WSN”, IJCA, November, 2012.
- O. B. Akan and I. F. Akyildiz, “ESRT: Event-to-sink reliable transport in wireless sensor networks", IEEE/ACM Transactions on Networking, vol. 13, no. 05, pp. 1003-1016, 2005
- Deepali Virmani, Stabirjain, “Reliable Robust and Real-Time Communication Protocol For Data Delivery in Wireless Sensor Networks”, IJITKM , vol.4, pp. 595-601, Dec.2011.
- HafizurRahman, DebajyotiKarmaker, Mohammad Saiedur, Rahman, Nahar Sultana, “SMESRT: A Protocol For Multiple Event-To-Sink Reliability In WSN”, IJET, vol.1, no.1, pp. 9-14, October.2011.
- Mohammad M, IqbalGonda, Jordar K, “CODAR: Congestion and Delay Aware Routing to Detect Time Critical Events in WSNs”, IEEE, 2011.
- Y. Xue, B. Ramamurthy and Y. Wang, “LTRES: A loss-tolerant re-liable event sensing protocol for wireless sensor networks", Computer Communications, vol. 32, no. 15, pp. 1666 -1676, 2009.
- V. C. Gungor and O. B. Akan, “DST: delay sensitive transport in wirelesssensor networks", in Proceedings of the 7th International Symposium on Computer Networks (ISCN), Istanbul, Turkey, pp. 116-122, 16-18 June2006.
- Sibila R, Sarangapani J, Vittal R, “OEDSR: Optimized Energy-Delay Sub-network Routing in WSN”, IEEE, pp. 330-335, 2011.
- Vehbi C.G, Ozgur B.A, Ian F.Akyildiz, “A Real-Time and Reliable Transport (RT)2 Protocol for WSN and Actor Networks”, IEEE/ACM Transactions On Networking, vol.16, no.2, pp. 359-370, April 2008.
|