ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
| Ambarish.A1, Gowthamani.R2 Department of Computer Science, Nehru Institute of Technology, Coimbatore |
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Mobile ad hoc networks (MANET) are infrastructure less one where there is no architecture. There will be security concerns in MANET since it is an open environment. Certificate revocation scheme addresses a lot of security issues in MANETs. It follows a technique of revoking the certificate of the nodes that are considered to be malicious. Once the certificate is revoked, the node is free and canât take part in any of the communications in the network. In order to enhance the security the threshold based mechanisms are used in the cluster to vindicate warned nodes from the legitimate nodes. In this paper we are building on the certificate revocation scheme, to make the cluster secure by choosing the cluster head effectively. The security is being enhanced by the proper selection of cluster head using Fuzzy Relevance Degree. In a given cluster, the cluster head monitor their Cluster Members and watch for the accusations by means of node position or node verification algorithms. The proposed work is focusing on the selection of cluster head using Fuzzy Relevance Degree in a MANET by considering the parameters additional to the normal one. The parameters include the distance, the degree called FRD, the velocity by which the nodes are moving and the distance between them.
Key words |
| Mobile Ad Hoc Network, Certificate Revocation, threshold, Node Verification, Fuzzy Relevance Degree |
I. INTRODUCTION |
| With the advancement of wireless technology, mobile communication becomes popular in recent years. A lot of increasing attention is going on the research of mobile distributed computing. A mobile ad hoc network is a collection of nodes with no infrastructure and these nodes are connected with wireless communication. Also, the topology of the ad hoc network is dynamically changing and the nodes of the ad hoc network are often mobile. The ease of mobility within the network is a major advantage in mobile ad hoc networks. In addition to the mobility, mobile devices cooperate and forward packets for each other to extend the limited wireless transmission range. The development in ad hoc networks helps in the creation of on demand network in areas like disaster relief, war field and in emergency communication areas. |
| A major challenge in the design of mobile ad hoc networks is to protect their vulnerability from security attacks. The certificate revocation scheme plays an important role in ensuring security. There are lots of challenges in ensuring security [1]. Due to the absence of a clear line of defence, a complete security solution for MANETs should integrate both proactive and reactive approaches [2], and encompass all the three components like prevention, detection and reaction. The fundamental vulnerability of MANETs comes from their open peer-peer architecture. The nodes in the MANETs have an additional functionality of forwarding the packets for the other nodes in the network. In wired network there will be dedicated routers to do the packet forwarding. The wireless channel is accessible to both legitimate network users and the malicious attackers. Hence the wireless on demand MANETs are more susceptible to the attacks considering the wired networks |
| Enabling security, conveying real trust, ensuring integrity etc thus becomes an integral part and certificate revocation scheme provides fundamental solutions to all. Tremendous amount of research work are happening in the field of certificate revocation which includes the certificate distribution [3] [4] from a trusted third party. It almost becomes a prerequisite in mobile ad hoc network. This will make sure that every node joining the network has a trusted third party digital signature. The attack detection [5] [6] [7] [8] is another area of concern in wireless medium since any node can freely join the network at a particular instant of time. In my work, we are focusing mainly on the security issue of MANET and how certificate revocation provides it. I go deeper in to the selection of the cluster head using a different method and compares the performance of the technique which I have used with the existing ones. |
| My paper is organized as follows: The next section (Section 2) gives you an idea of the current and existing methods in the assurance of security. Section 3 gives the proposed schema used. Then I conclude the paper in the following section. Last section is fully dedicated to the papers which I have refereed to make do my research work. |
II. RELATED WORKS |
| Researchers pay a whole lot of attention in ensuring the fundamental security of infrastructure less MANETs. Many approaches took centre stage in enabling trustworthiness in certificate revocation. This section I introduce some of the currently used ones like voting based and non voting based mechanisms. |
| NON VOTING BASED MECHANISM |
| This schema introduces a mechanism where all nodes have to participate in a voting system in order to evict the malicious nodes |
| Several techniques grew hand to hand in the voting based mechanism. URSA [9] proposed by Luo et al. used a voting system to evict nodes. There will be a certificate authority (CA), who issues the valid certificates. The nodes with the valid certificates are considered to be legitimate. The duty of issuing valid certificates to the newly joining nodes, though lies with their neighbors. A major drawback in this technique is that this schema canâÂÂt address false accusations from the neighbor malicious nodes. |
| Arboit et al. [10] in their work put another mechanism allows the nodes in the network to vote together. The basic difference from the Luo et al. is that nodes in network vote with different weights ensuring a larger accuracy. Since every node in network has to participate in eviction of one singe node, the overhead induced is much higher than the other schemas. |
| VOTING BASED MECHANISMS |
| A single neighbor can detect the presence of a malicious node in the non voting based schema which drew forward the certificate revocation mechanisms |
| „Suicide for the common good strategyâ was one of the first methods in these mechanisms which was proposed by Clulow et al. [11] Here the certificates of both the accusing and the accused nodes will be cancelled, thus forcing one to evict forcefully from the network. The major advantage is that the time and overhead will be reduced considerably. This positive though is cancelled out, as this method canâÂÂt able to differentiate falsely accused nodes from the genuine attackers. |
| A cluster based scheme [12] was proposed by Park et al. where a Certificate authority manages control messages. There will be black list and warning list created. The accuser node is put in the warning list and accused node in the black list. The certificate of the malicious attacker node can be revoked by any single neighboring node. It can also deals with the issue of false accusation that enables the falsely accused node to be removed. |
| Wei Liu et al. [13] came forward with the technique of revocation with vindication capability and it maintains a threshold value to vindicate warned nodes as legitimate or not, before recovering them. |
| In a cluster based method, the selection of cluster head (CH)[15][16] is of concern and can act as a major parameter in ensuring security. In the existing method described earlier, a node will proclaim itself as a CH. It propagates CH Hello packet (CHP) to notify neighboring nodes periodically. This selection can become somewhat faulty and in this paper we are using the Fuzzy Relevance Degree to select a CH. |
| CLUSTER BASED MODEL |
| In this section, we introduce the model of cluster based on which my work is to be done. Cluster is largely a collection of nodes that are mobile or stationary. The construction of the cluster should be done in a compatible mode, where the work must be done effectively in both mobile and stationary nodes. I made an assumption that the cluster will contain an optimum number of nodes, say 10 to 100. The main aim is to give the cluster head within a cluster to give all the right to revoke the certificate and thus evict the nodes from the cluster. This scheme maintains two lists, the black list and the warning list. |
| I made the assumption that the nodes that are in the network have received the certificates from a trusted third party even before joining the network. The certificate distribution is not considered. The basic focus is on certificate revocation and the cluster head selection. The nodes can detect their neighbouring attack nodes which are one hop [6] away. |
| CLUSTER- BASIC IDEA |
| Clustering in MANET can be considered as the virtual partitioning of dynamic nodes in the flat structure or distributed network structure into several clusters. Clusters of the nodes in the flat structure or distributed network structure are made with respect to their nearness to each other. Such nodes are considered neighbors when all neighboring nodes are located within their transmission range and set up a bidirectional link between them. Typical algorithms for clustering in the flat structure or distributed network structure are known as one-hop clustering and multi-hop (d-hop) clustering algorithms. In the one-hop clustering, every member node is at most 1-hop distance away from a central node that is called the cluster head. Thus, all member nodes remain at most two hops distance away from each other within a cluster category. On the contrary, in multi-hop clustering, the management of neighboring nodes to the cluster head is performed by allowing the nodes to be presented at most d-hop distance away from each other to form a cluster. A typical MANET cluster structure consists of flat and hierarchical structures. The basic structure of the cluster is given in the figure 1. This gives an idea of basic cluster structure, where the links in the figure represents the link existing between the nodes. It is a hierarchal one, where gateway that connects the nodes between clusters is represented by shaded rectangular boxes. Within parenthesis the weights of each node is represented. This represented in the figure, provides a complete idea of how the nodes communicate. The gateway represents the channel through which the nodes between the clusters communicate. The cluster head is selected for each of the cluster and the each cluster has only one cluster head. The other nodes in the cluster will represent the cluster members. |
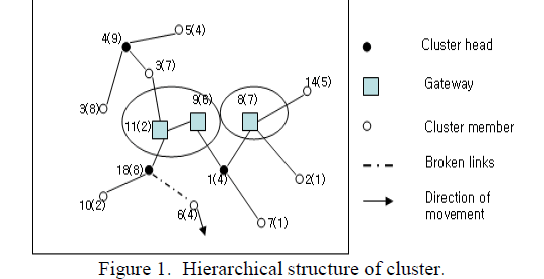 |
| The creation of topology is based on the cluster based [14] architecture. Nodes in the ad hoc network join together and form clusters. Each cluster will have an optimal number of nodes. The nodes in the cluster can find the attackers node which are only one hop away from each node. A cluster head (CH) will be chosen from the nodes in a given cluster and the rest of the nodes can be called as cluster members (CM). The CM must stay within the transmission range of the CH. The nodes must obtain a particular certificate from the Certificate Authority (CA) to join the cluster. |
| In the models existing, the main part in the cluster formation is the cluster head selection. While a node take parts in the network, it is allowed to declare itself as CH with a probability R. The links between the neighbouring nodes are checked efficiently by the usage of neighbour sensing protocols. |
| The periodic broadcast of hello messages are effective protocols used to detect the cluster head in the cluster. These are the one which are used in the existing methods. In this model, if a node proclaims itself as a CH, it propagates a CH Hello Packet (CHP) to notify neighboring nodes periodically. The nodes that are in the range of the CH can accept this packet to participate in this cluster as CM. If the node is deemed to be a CM, it has to wait for the CHP. When the CHP is received it will reply with the CM hello Packet (CMP). |
| The periodic broadcast of hello messages are effective protocols used to detect the cluster head in the cluster. These are the one which are used in the existing methods. In this model, if a node proclaims itself as a CH, it propagates a CH Hello Packet (CHP) to notify neighboring nodes periodically. The nodes that are in the range of the CH can accept this packet to participate in this cluster as CM. If the node is deemed to be a CM, it has to wait for the CHP. When the CHP is received it will reply with the CM hello Packet (CMP). |
| FUZZY RELEVANCE DEGREE |
| Usage of FRD algorithm [17][18] helps maintenance of cluster, most probably a secured cluster, and thus maintaining it in a stable state. The stable cluster in terms of energy allows for the easier access and transfer of packets from one secured cluster to the other thus reducing the transfer rate and reduces the effect of topological changes that are happening. |
| FSV STRUCTURE |
| This FSV (Fuzzy State Viewing) structure is the basis of so called Fuzzy Relevance Algorithm. This is virtually a table like shaped structure given in the Figure 2. This structure consists of five parameters. The importance of FSV comes in the transfer of packets when a node communicates among itself. In other words, when two nodes communicate among each other it will pass an FRD value represented by μ. This μ, ranges from 0 to 1, helps in the avoidance of interference when two nodes exchange the packets. The secured cluster thus formed will have a cluster head selected according to the proposed FRD algorithm. This subsequently results in the selection of Cluster Members. In order to provide the smooth transfer of packets to and from a gateway node is being selected which helps in the broadcasting of packets. |
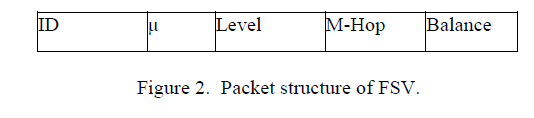 |
| The parameters of the packet are explained as follows: |
| ï Identifier (ID): As mentioned above every node that participates in the cluster will have a unique id. This helps in avoidance of interference and will fasten up the cluster head selection process. |
| Fuzzy Relevance Degree (μ): Fuzzy Relevance Degree value, μ is used by the nodes in communication process. This value will be send by the corresponding neighbor nodes when participating in communication. The above μ value is determined by the parameters like mobility, distance and power. On the larger context, we take the value of μ in range of 0 to 1. This will be formed as a set where the FRD value can be selected accordingly. |
| ï Level: The third parameter in the FSV structure is the level. As we arrange the value into sets, this can be further categorized as low level, middle level and high level. Here after itâÂÂs the level parameters in the FSV which acts as the criteria in selecting the cluster head, cluster members and the gateway nodes. |
| M-hop (Multi-hop): Based on the μ value calculated the cluster creation and its management also can be controlled. This is being done by separating the transfer process into multihops ranging from 1-hop to several m-hops. The size of the MANET paves way in selection of multiple hops. |
| Balance: Every node in the secured cluster must be given an equal chance of making into the election of CH. This fair management must help in the proper allocation of the cluster head in a secured cluster. Thus the parameter balance is used for serving the above function. |
| CLUSTER FORMATION |
| Every node in the network must possess an FRD value denoted by μ. This helps in the formation of secured cluster with high reliability and optimum transfer of data packets. Fuzzy Relevance Degree value, μ is used by the nodes in communication process. This value will be send by the corresponding neighbor nodes when participating in communication. The above μ value is determined by the parameters like mobility, distance and power. On the larger context, we take the value of μ in range of 0 to 1. This will be formed as a set where the FRD value can be selected accordingly. |
| Once cluster head is decided each node advocates itself and checks whether clustering is necessary to stabilise or not. This checking with the neighbouring nodes is done by using some criteriaâÂÂs. The energy must be made stable and also nodes within the cluster must possess similar characteristics. We have given two figures, Figure 3 and Figure 4. The unmodified or the structure before the cluster formation is given in the Figure 3. The modified scheme is given in the Figure 4. This adds to the fact that clustering can enhance the security. Node within a cluster having more power and the signal strength, calculated from RS (xi) will be selected as the cluster head Clustering is done basically on the two structures given, that are in C2 and C3, in order to maintain a balance with the cluster structure C1. The other combinations like C1-C2 or C1-C3 will result in possible imbalance in the structure, thus being rejected. |
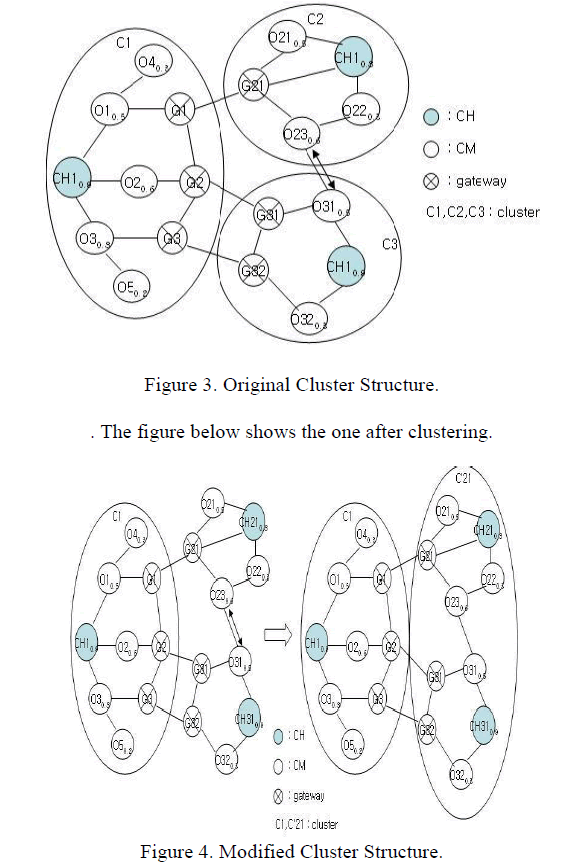 |
| For the formation of cluster given in the Figure 4, we use the FRD value denoted by μ. Adequate value will be selected from the set, which will aid in the balancing of the structure using the balance parameters. It also helps in maintaining a fair allocation as well as controlling the management process. Thus we get a secured cluster that have a high transfer rate in terms of the communication between nodes in the MANET. In the figure two clusters communicate effectively by sending packets to and fro. The gateway node is the one responsible in making the communication possible thus having a stable energy occupied in the cluster structure with security prevailing. |
III. CONCLUSION |
| In this paper, I addressed the basic security of the MANET and how the consideration of Cluster Head impacts the creation of a secured cluster. The existing models emphasis the selection of the cluster head based on the neighbour sensing protocol, just by proclaiming the hello packets. But I considered FRD method in CH selection including various parameters like battery power, life time, the velocity of nodes, the distance between them and also the FRD value. The revocation scheme is basically build up on the existing work of certificate revocation, considering how to revoke the certificates effectively by addressing the problem of false accusation. The efficient selection of cluster head and the revocation process help in the creation of a secure cluster and improve the performance of the network. The usage of network simulator will help in the detection of the enhancement. The overall through put will be increased by the usage and hence be far more efficient. |
References |
|