Keywords
|
| Mobile ad hoc networks, neighbor coverage, probabilistic rebroadcast, routing overhead |
INTRODUCTION
|
| Wireless ad-hoc network is a collection of mobile/semi-mobile nodes with no pre-established infrastructure, forming a temporary network. Each of the nodes has a wireless interface and communicates with each other over either radio or infrared. Laptop computers and personal digital assistants that communicate directly with each other are some examples of nodes in an ad-hoc network. Nodes in the ad- hoc network are often mobile, but can also consist of stationary nodes, such as access points to the Internet. Semi mobile nodes can be used to deploy relay points in areas where relay Figure 1.1 show a simple ad-hoc network with three nodes. The outermost nodes are not within transmitter range of each other. However the middle node can be used to forward packets between the outermost nodes. The middle node is acting as a router and the three nodes have formed an ad-hoc network. An ad-hoc network uses no centralized administration. This is to be sure that the Network won't collapse just because one of the mobile nodes moves out of transmitter range of the others. Nodes should be able to enter/leave the network as they wish. Because of the limited transmitter range of the nodes, multiple hops may be needed to reach other nodes. Every node wishing to participate in an ad-hoc network must be willing to forward packets for other nodes. |
 |
| Thus every node acts both as a host and as a router. A node can be viewed as an abstract entity consisting of a router and a set of a listed mobile hosts. It is axed through network recon duration. For instance, if a node leaves the network and causes link breakages, acted nodes can easily request new routes and the problem will be solved. This will slightly increase the delay, but the network will still be operational. |
| Wireless ad-hoc networks take advantage of the nature of the wireless communication medium. In other words, in a wired network the physical cabling is done a priori restricting the connection topology of the nodes. This restriction is not present in the wireless domain and, provided that two nodes are within transmitter range of each other, an instantaneous link between them may form. |
PROBABILISTIC BROADCASTING PROTOCOL WITH COVERAGE AREA AND NEIGHBOR CONFIRMATION
|
| In this section we describe our protocol in detail. Probability based methods use certain predefined rebroadcast probability p (0 ïÿýïÿý p ≤ 1) to decide whether to rebroadcast or not. The biggest problem with these schemes is determining the suitable probability. We propose Probabilistic Broadcasting with Coverage Area and Neighbor Confirmation. |
| A. Shadowing Effect |
| As described in the previous section, the goal of our protocol is to achieve high reachability of broadcasting and reduction of rebroadcast. In a general probabilistic approach, the rebroadcast probabilities of all mobile nodes are fixed as same value. However, the same rebroadcast probabilities can’t reflect the situation of MANETs which topologies are frequently changed. For example, a MANET may be sparse or dense, and relative location of the rebroadcast node is far from or closer to the sender. If these circumstances are not taken into consideration, the rebroadcast probabilities value might be set too small or too large, and after all, the reachability will be poor or many rebroadcast packets will be generated. So, the rebroadcast probabilities need to be adjusted by the circumstances of the node. |
| We allow each node to choose different probability according to its distance from the sender. The distance from a node to the sender can be calculated from the signal strength or GPS (Global Positioning System). In short of our protocol, each node examines how far it is from the sender and determines its retransmission probability. It is better for a node that is farther away from the sender to have high retransmission probability. This means that a node geographically further from the sender may potentially act as a relay node on behalf of a node closer to sender. Note that a node closer to sender might be shadowed from rebroadcast nodes in the extreme case. |
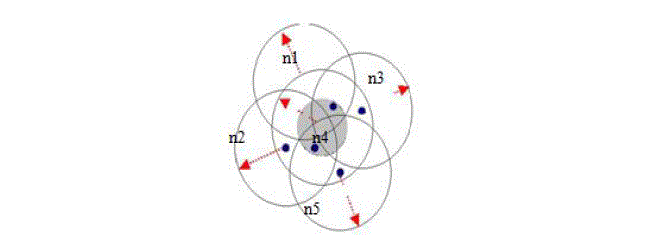
Figure 2 shows the shadowing effect of our approach. |
| In Figure 2, the neighbors (node n1, n2, n3 and n4) that are geographically far away from the sender node (s) will act as relays with high retransmission probability. On the other hand, the neighbors (node n5 and n6) that are geographically close to the sender node (s) will be shadowed from relays with low retransmission probability. This shadowing effect will reduce the number of rebroadcast packets. |
| B. Probabilistic Rebroadcast with Coverage Area |
| Our scheme is based on the shadowing effect. When a node receives a broadcasting packet, it refers to its distance from sender to determine its rebroadcast probability. As explained above, if a node is an outer node, the node assumes that it has larger coverage area, and if a node is inner node, the node assumes that it has smaller coverage area. As the coverage area is proportional to the distances to sender, the rebroadcast probability of a node should be considered according to its coverage area. Our scheme uses its coverage area to determine its rebroadcast probability. It introduce simple equation that defines the relationship between the coverage area and rebroadcast probability to acquire good output. Figure 2 shows how to get the rebroadcast probability that is proportional to the distance. Let R be the communication range of node s, and A be the covering area of node s. A1, A2, and A3 is sub area of A with radii r1, r2, and r3, respectively. When a node receives the broadcast message, its relative distance can be obtained by comparing the signal strength with maximum signal strength or by using GPS. Then the distance to sender can be estimated and the node can determine its coverage ratio μ. It can get the rebroadcast probability (p), a is a sensitivity parameter to control the rebroadcast probability. This approach gives a good approximation in the general distribution of mobile node |
| C . Probabilistic Rebroadcast with Coverage Area and Neighbor Confirmation |
| An important problem is how to minimize the number of rebroadcast packets while retransmission latency and packets reachability are maintained appropriately. Even though a large number of rebroadcasts guarantees high reachability, it causes high network bandwidth wastage and many packets collisions. On the other hand, the small number of rebroadcasts results in low reachability, because it cause rebroadcast chain broken so that some hosts may not receive the broadcast packets. The probabilistic approached presented above may cancel a non-redundant packets retransmission. The distribution of mobile node in MANET, where a) is good distribution and b) is bad distribution. In the case of b), early die-out of rebroadcast may happen. When a non-redundant retransmission is dropped in first few steps, the number of unreachable nodes increases fast hop by hop. |
| To prevent from early die-out of rebroadcast, neighbor confirmation scheme is applied. The neighbor confirmation scheme is to get high reachability to the last nodes by second retransmission of a packet. It is executed by the nodes which do not rebroadcast the packet according to dynamic probability with coverage area. After a given amount of time t, a node checks if all the neighbors have received the broadcast packet. If not, it rebroadcast the packet. Let’s assume that n1 has the probability that doesn’t not rebroadcast the packet. And also assume that n2 is one of the n1’s neighbors, and n2 doesn’t not receive broadcast packet. n1 waits a given amount of time t, and checks if all the neighbors have received the broadcast packet. If n2 didn’t receive the packet, n1 must rebroadcast it. |
PROTOCOL IMPLEMENTATION AND PERFORMANCE EVALUATION
|
| A. Protocol Implementation |
| When greedy routing is used as a packet forwarding scheme, each relaying node dynamically computes the next-hop node for each in-coming packet. Since no state about flow paths is maintained, no node has the knowledge about the entire path. Hence, the issue of consistent forwarding does not exist in this the route request message records all the nodes it traverses. The destination returns a route reply message to the source after it receives the route request message. The route reply message carries the entire source to destination path recorded in the route request message. After learning the path from the route reply message, the source node can send its data packets using source routing and enclose the entire path in the header of each out-going packet. All relaying nodes only forward packets according to the path in these packet, automatically guarantees the consistency of routing. In addition, as long as the greedy-routing based path discovery does not create loops while forwarding the route request messages, loop-freeness is automatically guaranteed by source routing. |
| B. performance evaluation |
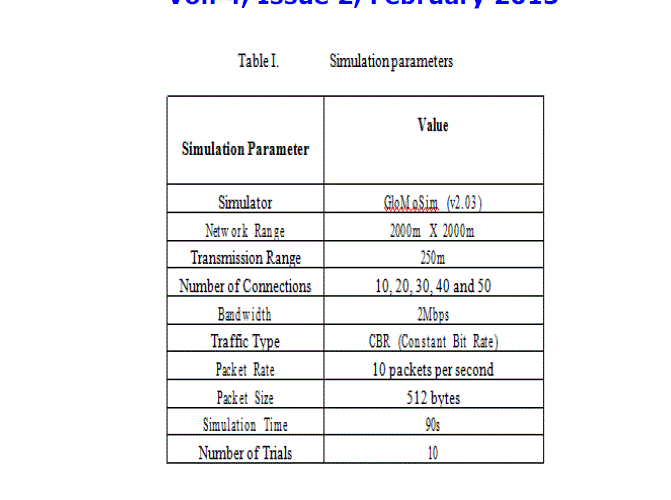
| In this section, we evaluate the performance of our algorithm by comparing with a simple flooding algorithm. We use network simulator Glomosim [13] to evaluate our scheme. All the simulations were performed in a simulation area of 2000m x 2000m, and the number of connections is varied from 10 to 50. Other simulation parameters are shown in Table 1. |
 |
| We used three kinds of measures: rebroadcast number, reachability, and collision, to evaluate the performance of our approach. Rebroadcast number is the number of rebroadcast packets. Reachability is the sum of mobile node that receives the broadcast message directly or indirectly. Collision is the number of collided packet that mobile nodes send. |
RESULTS AND DISCUSSION
|
| A. Packet Delivery Ratio: |
| Many protocols in wireless sensor networks use packet delivery ratio (PDR) as a metric to select the best route, transmission rate or power. PDR is normally estimated either by counting the number of received hello/data messages in a small period of time, i.e., less than 1 second, or by taking the history of PDR into account. The first method is accurate but requires many packets to be sent, which costs too much energy. The second one is energy efficient, but fails to achieve good accuracy. Therefore in this paper we propose a novel estimation method which takes advantage of receiving signal strength. We show our proposed method is much more accurate than the second estimation method, while being simple and energy efficient at the same time. |
| Fig. 4 shows the packet delivery ratio with increasing traffic load. As the traffic load increases, the packet drops of the conventional AODV protocol without any optimization for redundant rebroadcast are more severe. Both the DPR and NCPR protocols increase the packet delivery ratio compared to the conventional AODV protocol, because both of them significantly reduce the number of collisions and then reduce the number of packet drops caused by collisions. On average, the packet delivery ratio is improved by about 11.5 percent in the NCPR protocol when compared with the conventional AODV protocol. And in the same situation, the NCPR protocol improves the packet delivery ratio by about 1.1 percent when compared with the DPR protocol. |
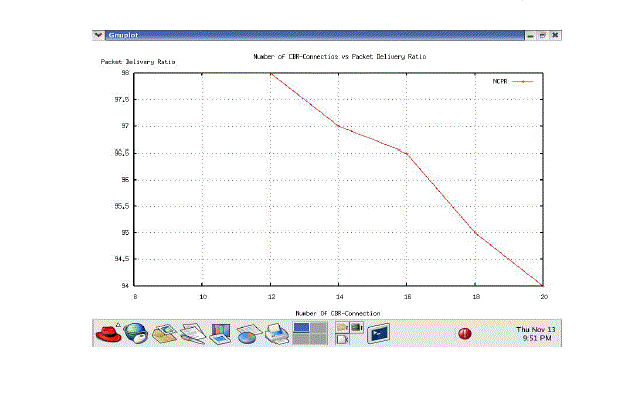
Figure 3. Packet delivery ratio with varied number of CBR connections |
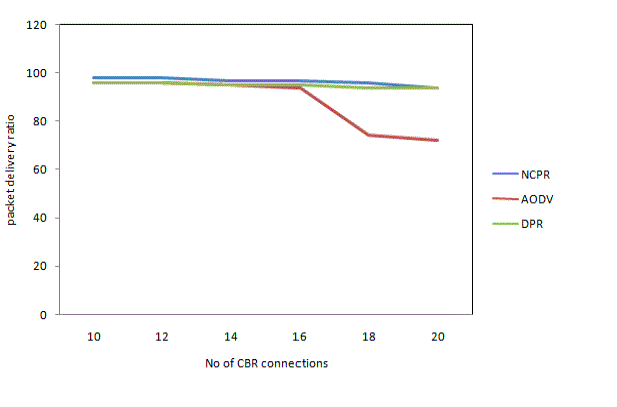
Figure 4. Packet delivery ratio with varied number of CBR connections |
| B. End-to-end delay: |
| End-to-end delay indicates how long it took for a packet to travel from the CBR source to the application layer of the destination. It represents the average data delay an application or a user experiences when transmitting data |
Figure 5. Average end-to-end delay with varied number of CBR connections. |
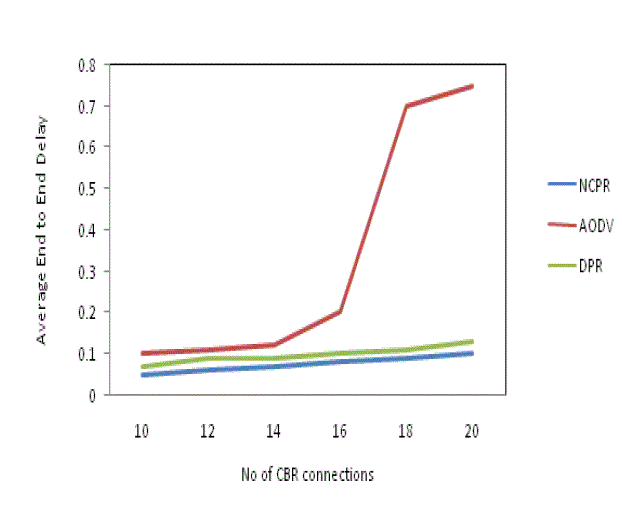
Figure 6. Average end-to-end delay with varied number of CBR connections |
| Fig. 6 measures the average end-to-end delay of CBR packets received at the destinations with increasing traffic load. The end-to-end delay of the conventional AODV protocol significantly increases with the increase of traffic load, which is the same as the MAC collision rate and routing overhead. When the traffic load is heavy, by reducing the redundant rebroadcast, both the DPR and NCPR protocols alleviate the channel congestion and reduce the retransmissions at MAC layer, thus, both of them reduce the end-to-end delay. On average, the end-to-end delay is reduced by about 71.0 percent in the NCPR protocol when compared with the conventional AODV protocol. Under the same network conditions, the delay is reduced by about 28.7 percent when the NCPR protocol is compared with the DPR protocol. |
CONCLUSION
|
| The goal of the system, to design probabilistic rebroadcast protocol based on neighbor Coverage technique to reduce the routing overhead in MANETs. The system provides neighbor coverage knowledge includes additional coverage ratio and connectivity factor. In this system delivers a new scheme to dynamically calculate the rebroadcast delay, which is used to determine the forwarding order and more effectively exploit the neighbor coverage knowledge. Simulation results show that the probabilistic rebroadcast protocol generates less rebroadcast traffic than the flooding. Due to less redundant rebroadcast, the probabilistic rebroadcast protocol mitigates the network collision and contention, such as to increase the packet delivery ratio and decrease the average end-to-end delay. The final result displays the neighbor Coverage Probabilistic Rebroadcast (NCPR) protocol achieves good performance compare to Dynamic Probabilistic Routing (DPR) and Ad hoc On-demand Distance Vector (AODV) routing. |
FUTURE WORK
|
| In Future, the system additionally includes Hybrid Location Forward Routing (HLFR) technique to calculate performance, from the result of Packet Delivery Ratio and End to End Delay measurements is used to find out which one is effective. |
References
|
- S.Y. Ni, Y.C. Tseng, Y.S. Chen, and J.P. Sheu, “The Broadcast Storm Problem in a Mobile Ad Hoc Network,” Proc. ACM/IEEE MobiCom,pp. 151-162, 1999
- W. Peng and X. Lu, “On the Reduction of Broadcast Redundancy in Mobile Ad Hoc Networks,” Proc. ACM MobiHoc, pp. 129-130, 2000.
- B. Williams and T. Camp, “Comparison of Broadcasting Techniques for Mobile Ad Hoc Networks,” Proc. ACM MobiHoc, pp. 194-205, 2002.
- C. Perkins, E. Belding-Royer, and S. Das, Ad Hoc On-Demand Distance Vector (AODV) Routing, IETF RFC 3561, 2003.
- J. Kim, Q. Zhang, and D.P. Agrawal, “Probabilistic Broadcasting Based on Coverage Area and Neighbor Confirmation in Mobile Ad HocNetworks,” Proc. IEEE GlobeCom, 2004.
- J. Chen, Y.Z. Lee, H. Zhou, M. Gerla, and Y. Shu, “Robust Ad Hoc Routing for Lossy Wireless Environment,” Proc. IEEE Conf. MilitaryComm. (MILCOM ’06), pp. 1-7, 2006.
- D. Johnson, Y. Hu, and D. Maltz, The Dynamic Source Routing Protocol for Mobile Ad Hoc Networks (DSR) for IPv4, IETF RFC 4728, vol.15, pp. 153-181, 2007.
- X. Wu, H.R. Sadjadpour, and J.J. Garcia-Luna-Aceves, “Routing Overhead as a Function of Node Mobility: Modeling Framework andImplications on Proactive Routing,” Proc. IEEE Int’l Conf. Mobile Ad Hoc and Sensor Systems (MASS ’07), pp. 1-9, 2007.
- J.D. Abdulai, M. Ould-Khaoua, L.M. Mackenzie, and A. Mo-hammed, “Neighbor Coverage: A Dynamic Probabilistic Route Discovery forMobile Ad Hoc Networks,” Proc. Int’l Symp. Performance Evaluation of Computer and Telecomm. Systems (SPECTS ’08), pp. 165-172, 2008.
- H. AlAamri, M. Abolhasan, and T. Wysocki, “On Optimizing Route Discovery in Absence of Previous Route Information in MANETs,” Proc.IEEE Vehicular Technology Conf. (VTC), pp. 1-5, 2009.
- A. Mohammed, M. Ould-Khaoua, L.M. Mackenzie, C. Perkins, and J.D. Abdulai, “Probabilistic Counter-Based Route Discovery for Mobile AdHoc Networks,” Proc. Int’l Conf. Wireless Comm. and Mobile Computing: Connecting the World Wirelessly (IWCMC ’09), pp. 1335-1339,2009.
- Xin Ming Zhang, Member, IEEE, En Bo Wang, Jing JingXia,and Dan Keun Sung, Senior Member, “A Neighbor Coverage based ProbabilisticRebroadcast for Reducing Routing Overhead in Mobile Ad hoc Networks” IEEE,2013
|