Keywords
|
| AdHoc Network, broadcast storm, MANET, AODV , RREQ |
INTRODUCTION
|
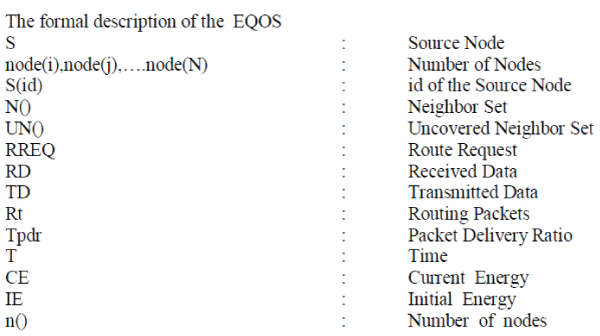
| Mobile Ad Hoc Networks (MANETs) consists of a collection of mobile nodes which are not bounded in any infrastructure. Nodes in MANET can communicate with each other and can move anywhere without restriction. This non-restricted mobility and easy deployment characteristics of MANETs make them very popular and highly suitable for emergencies, natural disaster and military operations. Efficient, dynamic routing is one of the key challenges in mobile ad hoc networks. It consist both mobile and stationary nodes which has low-power, densely distributed, energy constrained stationary sensors, which are able to form MAC level connections and Network level multi-hop routes at runtime . |
| MANETS rely on wireless transmission, a secured way of message transmission is important to protect the privacy of the data. An insecure ad-hoc network at the edge of communication infrastructure may potentially cause the entire network to become vulnerable to security breaches. There is no central administration to take care of detection and prevention of anomalies in Mobile ad hoc networks. Mobile devices identities or their intentions cannot be predetermined or verified. Therefore nodes have to cooperate for the integrity of the operation of the network. However, nodes may refuse to cooperate by not forwarding packets for others for selfish reasons and not want to exhaust their resources. Various other factors make the task of secure communication in ad hoc wireless networks difficult include the mobility of the nodes, a promiscuous mode of operation, limited processing power, and limited availability of resources such as battery power, bandwidth and memory. Therefore nodes have to cooperate for the integrity of the operation of the network. Nodes may refuse to cooperate by not forwarding packets for others for selfish reasons and not want to exhaust their resources. |
RELATED WORK
|
| In [1] authors used the performance analysis of an adaptive probabilistic counter-based scheme (or APCS for short) for broadcasting in mobile ad hoc networks that further mitigate the broadcast storm problem associated with flooding under increased node density and traffic rate. APCS adapts it RAD (random assessment delay) value to network congestion level and uses packet origination rate as an indicator of network congestion by keeping track of the number of packets received per second at each node.Simulation results reveal that this simple adaptation minimizes end-to-end delay and maximizes delivery ratio, and thus achieves superior performance in terms of saved rebroadcast, end-to-end delay and reachability over the other schemes. There are couple of areas worth investigating. One area in which we see the potential for even further improvement is to make the adaptation of the RAD value to other network parameters like number of neighbors, node speed and transmission range. Another area for future work is to explore further the performance of the scheme under combined network conditions (i.e. density, mobility and congestion together) . In [2] authors have demonstrated, through analyses and simulations, how serious broadcast storm problem could be. Several schemes, namely probabilistic, counter-based, distance-based, location-based, and cluster-based schemes, have been proposed to alleviate this problem. Simulation results based on different threshold values are presented to verify and compare the effectiveness of these schemes. The authors in [3] propose a probabilistic broadcasting based on coverage area and neighbor confirmation in mobile ad hoc networks the coverage area of a node to adjust the rebroadcast probability. If a mobile node is located in the area closer to sender, which means it has small additional coverage and rebroadcast from this node can reach less additional nodes, so its rebroadcast probability will be set lower. On the other hand, if a mobile node is located in the area far from sender, which means that the additional coverage from this node is large, its rebroadcast probability will be set higher. The coverage area can be estimated from the distance between sender and receiver and the distance can be estimated by signal strength or global positional system. Our approach combines the advantages of probabilistic and area based approach. Simulation results show that our approach can improve the average performance of broadcasting in various network scenarios. Our approach is simple and can be easily implemented in MANET. [4] Blind flooding is extensively use in ad hoc routing protocols for on-demand route discovery, where a mobile node blindly rebroadcasts received Route Request (RREQ) packets until a route to a particular destination is established. |
| This can potentially lead to high channel contention, causing redundant retransmissions and thus excessive packet collisions in the network. Such a phenomenon induces broadcast storm problem, which has been shown to greatly increase the network communication overhead and end-to-end delay. Authors show that the deleterious impact of such a problem can be reduced if measures are taken during the dissemination of RREQ packets .They propose a generic probabilistic method for route discovery, that is simple to implement and can significantly reduce the overhead associated with the dissemination of RREQs. The analysis reveals that equipping AODV with probabilistic route discovery can result in significant reduction of routing control overhead while achieving good throughput. In [5] authors present RBP, a very simple protocol that bolsters the reliability of broadcasting in such networks. This protocol requires only local information, and resides as a service between the MAC and network layer, taking information from both. RBP improves reliability while balancing energy efficiency. In [6] authors show that in a network with n randomly placed nodes, each node should be connected to _(log n) nearest neighbors. If each node is connected to less than 0.074 log n nearest neighbors then the network is asymptotically disconnected with probability one as n increases, while if each node is connected to more than 5.1774 log n nearest neighbors then the network is asymptotically connected with probability approaching one as n increases. It appears that the critical constant may be close to one, but that remains an open problem. |
| A. Description of the Proposed Algorithm: |
 |
PSEUDO CODE
|
| Step 1 : S-> Computes an initial neighbor set {node(i),node(j),….node(N)} |
| Step 2 : RREQ -> S(id), N(S), Flag. |
| Step 3 : If node(i) receives a new RREQ from S then the node(i) covers that neighbors and also the Source’s neighbors. |
| CN{node(i)}= {node(j),etc} |
| [N(node(i)) INTERSECT N(S)]-{S} |
| Step 4 : It transmits the RREQ to the uncovered neighbors. |
| UN = N(node(i)),N(S) |
| RREQ -> UN |
| Step 5 : To set the Timer |
| If node(i) receives a duplicates RREQ from node(j) before Timer expires Then |
| Discard(RREQ(j)) |
| Step 6 : Tpdr = RD/TD * 100 ; |
| Step 7 : Compute Rebroadcast Delay Ta[node(i)] = T(RD) - T(TD) |
| Step 8: End. |
SIMULATION RESULTS
|
| The simulation is conducted using the Network Simulator NS2. The simulation parameters are tabulated in Table 1 . |
| To implement the proposed mechanism the source code of AODV is enhanced in NS-2 . When a neighbor receives an RREQ packet, it could calculate the rebroadcast delay according to the neighbor list in the RREQ packet and its own neighbor list. The rebroadcast probability would be low when the number of neighbor nodes are high which means host is in dense area The probability would be high when the number of neighbor nodes are low which means host is in sparse area. We are considering the duplicate packet while transferring the RREQ. So we can avoid the overhead in rebroadcasting . |
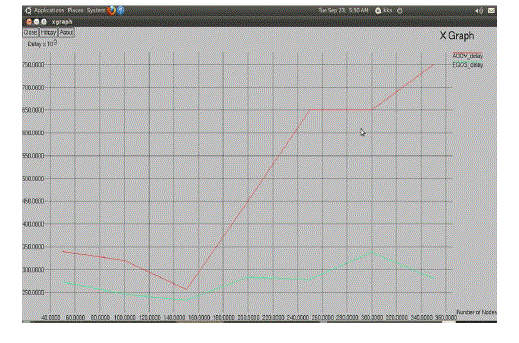
| The simulation is done for the comparison of Delay for AODV and EQOS protocol whose result is shown in Figure 2. |
CONCLUSION AND FUTURE WORK
|
| A EQOS based protocol is a neighbor coverage to reduce the average end-to-end delay in MANETs. This protocol includes additional coverage ratio and connectivity factor. To dynamically calculate the rebroadcast delay, we determine the forwarding order and more effectively exploit the neighbor coverage knowledge. Simulation results show that the proposed protocol generates less rebroadcast traffic than the flooding and some other optimized scheme in literatures. Because of less redundant rebroadcast, the protocol mitigates the network collision and contention decrease the average end-to-end delay. The simulation results also show that protocol has good performance when the network is in high density or the traffic is in heavy load. This protocol can be enhanced so as to increase the Packet delivery ratio and reduce the overhead. |
| |
Tables at a glance
|
 |
| Table 1 |
|
| |
Figures at a glance
|
 |
 |
| Figure 1 |
Figure 2 |
|
| |
References
|
- Anjum Asma and Gihan Nagib,’Energy Efficient Routing Algorithms for Mobile Ad Hoc Networks–A Survey’, International Journal of Emerging Trends & Technology in computer Science, Vol.3, Issue 1, pp. 218-223, 2012.
- Hong-ryeol Gil1, Joon Yoo1 and Jong-won Lee2 ,’An On-demand Energy-efficient Routing Algorithm for Wireless Ad hoc Networks’, Proceedings of the 2nd International Conference on Human. Society and Internet HSI'03, pp. 302-311, 2003.
- S.K. Dhurandher, S. Misra, M.S. Obaidat, V. Basal, P. Singh and V. Punia,’An Energy-Efficient On Demand Routing algorithm for Mobile Ad-Hoc Networks’, 15 th International conference on Electronics, Circuits and Systems, pp. 958-9618, 2008.
- DilipKumar S. M. and Vijaya Kumar B. P. ,’Energy-Aware Multicast Routing in MANETs: A Genetic Algorithm Approach’, International Journal of Computer Science and Information Security (IJCSIS), Vol. 2, 2009.
- AlGabri Malek, Chunlin LI, Z. Yang, Naji Hasan.A.H and X.Zhang ,’ Improved the Energy of Ad hoc On- Demand Distance Vector Routing Protocol’, International Conference on Future Computer Supported Education, Published by Elsevier, IERI, pp. 355-361, 2012.
- D.Shama and A.kush,’GPS Enabled E Energy Efficient Routing for Manet’, International Journal of Computer Networks (IJCN), Vol.3, Issue 3, pp. 159-166, 2011.
- Shilpa jain and Sourabh jain ,’Energy Efficient Maximum Lifetime Ad-Hoc Routing (EEMLAR)’, international Journal of Computer Networks and Wireless Communications, Vol.2, Issue 4, pp. 450-455, 2012.
- Vadivel, R and V. Murali Bhaskaran,’Energy Efficient with Secured Reliable Routing Protocol (EESRRP) for Mobile Ad-Hoc Networks’, Procedia Technology 4,pp. 703- 707, 2012.
|