In the last few years communication technology has been improved, which increase the need of secure data communication. For this, many researchers have exerted much of their time and efforts in an attempt to find suitable ways for data hiding. There is a technique used for hiding the important information imperceptibly, which is Steganography. Steganography is the art of hiding information in such a way that prevents the detection of hidden messages. The process of using steganography in conjunction with cryptography, called as Dual Steganography. This paper tries to elucidate the basic concepts of steganography, its various types and techniques, and dual steganography. There is also some of research works done in steganography field in past few years.
Keywords |
| Cryptography, Dual Steganography, Steganalysis, Steganography, LSB technique, DWT technique. |
INTRODUCTION |
| Steganography is a data hiding technique which conceals the existence of data in the medium. It provides secrecy of text
or images to prevent them from attackers. It provides secret communication so that intended hacker or attacker unable to
sense the presence of information. Steganography, derived from Greek, literally means "covered writing" [1]. |
| This paper is organized as follows. Section II discusses the comparison between cryptography and steganography.
Section III discusses the basics of steganography. Section IV discusses the different types of steganography. Section V
briefly discusses the various types of image steganography techniques. Next section VI gives basic idea about
steganalysis. Section VII provides the applications of steganography. Section VIII discusses briefly about dual image
steganography and literature survey of various combinations in section IX. Finally section X gives conclusion. |
COMPARISON OF STEGANOGRAPHY AND CRYPTOGRAPHY |
| Steganography and cryptography are closely related. Cryptography scrambles plain text into cipher text so it can’t be
understood. While Steganography hide the message so there is no knowledge of the existence of the message. The final
result in cryptography is the cipher text, while the final result in steganography is the stego-media [1]. |
| Steganography and cryptography are both ways to protect data from unwanted parties but neither technology alone is
perfect. Once the presence of the hidden information is revealed or even suspected, the purpose of the Steganography is
partly defeated. The strength of Steganography can be amplified by combining it with cryptography [18]. |
STEGANOGRAPHY MODEL |
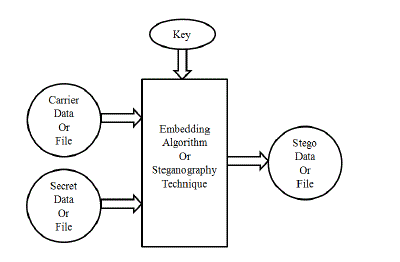
| Generally a steganographic system has a cover file that is used to cover the original message and the steganography
algorithm to carry out the required object as shown in Fig. 1. The result is a file called stego-file which has the message
inside it, hidden. This stego file is then sent to the receiver where the receiver retrieves the message by applying the
de-steganography. The goal of modern steganography is to keep the message undetectable [2]. |
STEGANOGRAPHY TYPES |
| There are five main categories of file formats that can be used for steganography based on these, the types are: |
Text Steganography |
| Hiding information in text is the most important and basic method of steganography. It can be classified in three
categories: format based, random & statistical generation and linguistic method [30]. |
Image Steganography |
| Images are used as the popular cover files for steganography. This technique exploits the weakness of the human visual
system (HVS). HVS can’t detect the variation in luminance of color vectors expressed in terms of 1s and 0s [30, 31]. |
Audio Steganography |
| It takes advantage of the psycho acoustical masking phenomenon of the human auditory system [HAS]. Psycho
acoustical or auditory masking property renders a weak tone imperceptible in the presence of a strong tone in its temporal
or spectral neighbourhood. In audio steganography, secret file is embedded into digitized audio signal which result slight
altering of binary sequence of the cover audio file. |
Video Steganography |
| Video files are generally a collection of image and audio, so most of the presented techniques on images and audio can be
applied to video files too [16]. The advantages of video are the large amount of data that can be hidden inside and
noticeable distortions might go unobserved by humans because of the continuous flow of information. |
Protocol Steganography |
| In this technique, the information is embedded within messages and network control protocols used in network
transmission. A network packet consists of packet headers, user data and packet trailers. So during some of the layers of
the network model, steganography can be used [32]. |
IMAGE STEGANOGRAPHY TECHNIQUES |
| Different types of Image Steganography Techniques are: Spatial domain, Transform domain, Spread spectrum, Masking
& filtering and Distortion Techniques. |
Spatial Domain Technique |
| In this technique, the secret file is embedded directly in the image [16]. Following are some techniques used in spatial
domain [8]: |
LSB Substitution Method |
| The most well known and simplex steganographic technique in the data hiding is least-significant-bits (LSB) substitution.
In this, the least significant bits of the pixels are replaced by the message bits. This technique is simple, but causes
noticeable distortion when the number of embedded bits exceeds three for each pixel. |
Optimum Pixel Adjustment Procedure |
| The Optimal Pixel adjustment Procedure (OPAP) reduces the distortion caused by the LSB substitution method by
adjusting pixel value after the hiding of the secret. |
Inverted Pattern Approach |
| This inverted pattern (IP) LSB substitution approach uses the idea of processing secret messages prior to embedding. In
this method each part of secret images is determined to be inverted or not inverted before it is embedded so stego image
has less distortion [26]. |
Pixel Value Differencing |
| Pixel Value Differencing (PVD) is able to provide a high quality stego image in spite of the high capacity of the
concealed information. In this message is embedded within edge area because human perception is less sensitive to subtle
changes in edge areas, it is more sensitive to changes in the smooth areas. |
| Advantages of Spatial Domain Technique [3]: |
| 1. There is less chance for degradation of the original image. |
| 2. Hiding capacity is more i.e. more information can be stored in an image. |
| Disadvantages: |
| 1. Large payload but often offset the statistical properties of the image |
| 2. Not robust against lossy compression and image filters |
| 3. Not robust against rotation, cropping and translation |
| 4. Not robust against noise |
| 5. Many work only on the BMP format |
Transform Domain Technique |
| This is more complex way of hiding information in an image where various algorithms and transformations are used on
the image to hide information in cover image. The process of embedding data in the frequency domain of a signal is much
stronger than embedding principles that operate in the time domain. Today most of the strong steganographic systems
operate in the transform domain [15]. Its types are JPEG Steganography and Discrete Wavelet Transformation (DWT). |
JPEG Steganography: |
| Originally thought was steganography would not be possible to use with JPEG images, as they use lossy compression
which results in parts of the image data being altered. During the DCT transformation, rounding of coefficients are not
noticeable by human eye [16]. This same property is also used to hide messages. The DCT and the quantization phase
form part of the lossy stage and the Huffman encoding used to further compress the data is lossless stage. Steganography
take place between these two stages [27]. By same principles of LSB insertion the message can be embedded into the
LSB of the coefficients before applying the Huffman encoding. So it is extremely difficult to detect, as it is not in the
visual domain [29]. |
Discrete Wavelet Transformation |
| The wavelet transformation describes a multi-resolution decomposition process in terms of expansion of an image onto a
set of wavelet basis function. DWT has its own excellent space frequency localization properly [7]. By applying 2D
DWT on the image, the four subbands are generated which are LL, LH, HL and HH. So by modifying these co-efficient
the stego image is generated [14, 28]. The Haar wavelet is also possible wavelet transform technique [6]. |
| Advantages of Transform Domain Technique: |
| 1. Highly robust, the hidden data cannot be lost with image manipulation |
| 2. Higher imperceptibility |
| Disadvantages: |
| 1. Very complex techniques |
| 2. Too much computations required |
Spread Spectrum Technique |
| In this technique, hidden data is spread throughout the cover image making it harder to detect. Marvel et al, proposed a
system that combines spread spectrum communication, error control coding and image processing to hide information in
images [12]. Here the message is embedded in noise and then combined with the cover image to generate the stego image.
Because of the power of the embedded image is much lower than the power of the cover image, the embedded image is
not perceptible by human eye or computer without access to the original cover image [11]. |
Masking and Filtering Technique |
| These techniques hide information by marking an image, in a way similar to watermarks on actual paper and are
sometimes used as digital watermarks. These techniques embed the information in the more significant areas such that the
hidden message is more integral to the cover image. Masking images entails changing the luminance of the masked area.
The smaller the luminance change, the lesser chance of detection [16]. This makes it more suitable than LSB with, for
instance, lossy JPEG images [13]. Weiqi Luo [23] proposed a method that finds the edges of cover image and within this
mask area the secret data is embedded. Here the change in edge is less visual compared with change in smooth region. |
| Advantages of Masking and filtering Technique: |
| This method is much more robust than LSB substitution method with respect to compression since the information is
hidden in the visible parts of the image. |
| Disadvantages: |
| Techniques can be applied only to gray scale images and restricted to 24 bits. |
Distortion Technique |
| In this technique, a stego image is created by applying a sequence of modifications to the cover image. This sequence of
modifications is use to match the secret message required to transmit which is encoded at pseudo randomly chosen pixels
[20]. In this cover image is also transmitted so comparing with it, the secret message is extracted. Here the cover image
should never be used more than one time. If an attacker tampers with stego image by cropping, scaling or rotating, the
receiver will easily detect it [21]. |
| Advantages of Distortion Technique: |
| 1. Easy embedding |
| 2. Good imperceptibility |
| Disadvantages: |
| Need for sending the cover image along with stego image |
STEGANALYSIS |
| Steganalysis is the science of detecting hidden information. The objective of steganalysis is to break steganography and
the detection of stego image is the goal of steganalysis. Most of steganalysis algorithms rely on steganographic
algorithms introducing statistical differences between the cover image and stego image. It deals with three important
categories: Visual attacks, Statistical attacks and Structural attacks [30, 31]. |
APPLICATION |
| Few applications of the steganography are [30]: |
| Defense Organizations: Security from enemies |
| Intelligence Agencies: Security of person’s private information |
| Government Agencies: Store critical data like criminal record |
| Smart Identity Cards: Personal information is embedded into photo |
| Medical: Patient’s details are embedded within image |
DUAL STEGANOGRAPHY |
| As we know steganography and cryptography, both are data hiding techniques used for secure communications over
insecure channel. But for obtaining much higher security, the combination of two is used. Inside the steganography
process, cryptography is used, so it’s called as Dual Steganography [25]. |
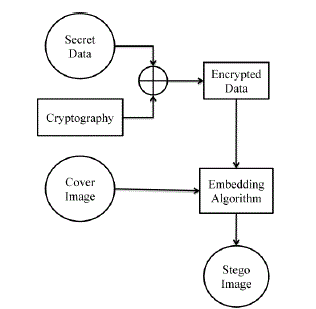
| The basic model of dual steganography is shown Fig 2. Here, the secret data is firstly converted into encrypted form and
then using this encrypted information as secret data, is hidden inside the cover image with the help of embedding
algorithm and finally the stego image is formed which is same as cover image in human perceptible way. The
cryptography algorithms used are RSA (Rivest Shamir Adelman), DES (Data Encryption Standard), AES (Advanced
Encryption Standard), Diffie Hellman or different algorithms can also be created. Sometimes a stego key is also used to
make the communication more secured. This key can directly be given by the sender and used during the embedding
algorithm. The stego key must be known at both transmitter and receiver side. Thus using cryptography along with
steganography, secret information can be easily communicated with high security. This is more secured way of using
steganography [19]. |
| If steganalysis occur during the transmission of stego image generated using dual steganography then even if the hidden
information is detected then it’s in the scrambled form which cannot be understood by the eavesdropper. So by using dual
steganography, highly secured communication can occur. |
LITERATURE SURVEY |
| In this review paper, depending on the combination of steganography and cryptography various papers are referred which
are explained in following parts: |
LSB and Encryption Combination |
| In this, first the secret file is encrypted with cryptography technique then this encrypted data is embedded within cover
image by LSB substitution technique. Some of the related research works are as follows: |
| Shailender Gupta, et al [4] developed a technique for hiding information using LSB steganography and cryptography
where the secret information is encrypted first using RSA or Diffie Hellman algorithm and then the encrypted ASCII
value is converted to binary form. Here even the cover image is converted from pixels to binary form and then the secret
message is embedded in the cover image using LSB technique and the stego image is formed. With the proposed method,
time complexity is increased but high security is achieved at that cost. |
| Md. Rashedul Islam, et al [5] proposed a method that has two parts; one is changing the secret message to cipher text by
AES Cryptography and other is hiding the cipher into image Steganographic technique. But here the LSB substitution is
performed based on the cover image, depending on the darker and lighter area steganography is performed. |
| Mazen Abu Zaher [17] developed a modified LSB method in which text message to be hidden is treated as 8 bit ASCII
codes. Using encryption algorithm these codes are then converted into 5 bit codes and then hidden in cover image using
LSB. As encryption algorithm used, if anyone extract bits from image, he won’t understand until he decrypt it. So with
this technique, more information can be hidden with a level of protection. |
| Mamta Juneja, et al [24] proposed a method that first encrypts the secret data by RSA algorithm. By using this encrypted
data method finds the best match for cover image so that after LSB substitution the generated stego image has fewer
chances of visual attack. So this method has better statistical and visual attack protection. |
| S. M. Masud Karim, et al [25] proposed an efficient LSB based steganographic method that utilizes the secret key to hide
the information into an input pixel of cover image without producing perceptible distortions. Here a bit of hidden
information is placed in either LSB of Green or Blue matrix of a specific pixel which is decided by the secret key. So
anyone cannot exactly make a decision that the bit of hidden information is placed in either LSB of Green or Blue matrix.
As a result, the security level of image steganography IS attained. |
DWT and Encryption Combination |
| In this, the secret file is encrypted with any cryptography technique then this encrypted data is embedded within cover
image by DWT technique. Some of the related research works are as follows: |
| Tanmay Bhattacharya, et al [15] proposed a DWT based Dual steganographic technique. Using DWT, a cover image is
decomposed into four sub bands. Two secret images are hidden within HL and HH sub bands respectively by using a
pseudo random sequence and a session key. After embedding the secret data, all four sub bands including two modified
sub bands are combined to produce the stego image using IDWT. By this method large amount of information is
transferred in a more secured way and also have an acceptable level of imperceptibility. |
| Amritha G. [22], et al proposed method steganography is object oriented as it is based on one of the feature of image.
Here the feature used is skin region of image. Instead of using full cover image, embedding data only within the skin
regions provide an excellent secure location for data hiding. Encrypt secret image using RC4 algorithm before embedding
enhances the security level. In this cover image is converted to HSV form to detect the skin color. After that skin segment
is detected and cropped. That region is transformed into DWT form and secret image encrypted with RC4 cryptography
algorithm. This encrypted data embedded within high frequency sub band of cover image and IDWT is performed. At last
by merging this segment stego image is generated. |
| Ketan Shah [33], el at proposed a method which combines the DWT steganography and DES cryptography technique. In
DWT, haar transform is used in two stages and the secret image is encrypted by DES algorithm. This algorithm has 64
bits secret key, 16 rounds of encryption, 64 bits pain text input and 64 bits cipher text output. This output is embedded
into HH sub band. Then IDWT is performed to generate stego image. |
| Archana S. Vaidya [34], el at developed method that uses Blowfish algorithm for encryption. It has scalable secret key
from 32 to 256 bits. It is a block cipher which uses 64 bits message block to encrypt it. Then encrypted data is embedded
within cover image and by IDWT stego image is generated. |
CONCLUSION |
| For the secret communication of internet users, as well as for others, information security has become one of the most
significant problems. Unauthorized access to secret data can have serious repercussions like financial loss etc.
Steganography is one of the solutions whose goal is to hide the existence of communicated message. By using dual
steganography in which steganography and cryptography are woven together, attempts to make steganalysis difficult. In
this paper, the basic concepts of steganography, its methods and highly secured dual steganography methods has been
reviewed. The battle between steganography and steganalysis will continually give rise to new techniques by countering
each other. In near future, the most important use of steganographic techniques will probably lie in the field of digital
watermarking. |
| |
Figures at a glance |
 |
 |
| Figure 1 |
Figure 2 |
|
| |
References |
- Alor-Hernandez, G., Gomez-Berbis, J. M., Jimenez-Domingo, E., RodrÃÆÃÂguez-GonzÃÆález, A., Torres-NiÃÆño, J., âÃâ¬ÃÅAKNOBAS: A Knowledge-based Segmentation Recommender System based on Intelligent Data Mining TechniquesâÃâ¬ÃÂ. Computer Science and Information Systems, Vol. 9, No. 2, 2012, pp: 713-740.
- Han, J., Kamber, M., âÃâ¬ÃÅData mining concepts and techniques 2nd edithionâÃâ¬ÃÂ. Morgan Kaufman, 2006, pp: 227-378.
- Agrawal R., Imielinski T. âÃâ¬ÃÅMining associations between sets of items in large databasesâÃâ¬ÃÂ. Proceedings of the ACM SIGMOD International Conference on Management of Data. pp: 207-216.
- Konda, S., âÃâ¬ÃÅWeb Data Mining Based Business Intelligence and Its ApplicationsâÃâ¬ÃÂ. IJCST, Vol. 4, No. 4, 2013, pp: 112-116.
- Aher, B., âÃâ¬ÃÅAssociation Rule Mining in Data MiningâÃâ¬ÃÂ. IJCST, Vol. 4, No. 3, 2013.
- Nagabhushanam, D., Naresh., N., âÃâ¬ÃÅPrediction of Tuberculosis Using Data Mining Techniques on Indian PatientâÃâ¬Ãâ¢s DataâÃâ¬ÃÂ. IJCST, Vol. 4, No. 4, 2013, pp: 262-265.
- Surya, K., Priya, K., âÃâ¬ÃÅExploring Frequent Patterns of Human Interaction Using Tree Based MiningâÃâ¬ÃÂ. IJCST, Vol. 4, No. 4, 2013.
- Rajnikanth, J., âÃâ¬ÃÅDatabase Primitives, Algorithms and Implementation Procedure: A Study on Spatial Data MiningâÃâ¬ÃÂ. IJCST, Vol. 4, No. 2, 2013.
- Quinlan, J. R., âÃâ¬ÃÅC4.5: Program for machine learning. CAâÃâ¬ÃÂ. Morgan Kaufmann, San Francisco, 1992
- Clark, P., Niblitt, T., âÃâ¬ÃÅThe CN2 induction algorithm. Machine LearningâÃâ¬ÃÂ. Vol. 3, No. 4, 1989, pp: 261-283.
- Cohen, W.(1995). âÃâ¬ÃÅFast effective rule inductionâÃâ¬ÃÂ. Proceedings Twelth International Conference on Machine Learning. Pp: 115-123
- Duda, R., Hart, P., âÃâ¬ÃÅPattern classification and scene analysisâÃâ¬ÃÂ. Wiley, New York, 1973
- Ardakani, H. D., Hajizadeh, E., Shahrabi, J., âÃâ¬ÃÅApplication of Data Mining Techniques in stock markets: A surveyâÃâ¬ÃÂ. Journal of Economics and International Finance, Vol. 2, No. 7, 2010, pp: 109-118.
- Lopez, V. F., Moreno, M. N., Polo, M. J., Segrera, S., âÃâ¬ÃÅImproving the Quality of Association Rules by Preprocessing Numerical DataâÃâ¬ÃÂ. II Congreso Espanola Informatics, 2007, pp: 223-230.
- Chung, F. L., Fu, T. C., Ting, J. (2006), âÃâ¬ÃÅMining of Stock Data: Intra-Stock and Inter-Stock Pattern Associative ClassificationâÃâ¬ÃÂ. Proceedings International Conference on Data Mining, pp: 30-36.
- Frank, E., Witten, I. H., (1998). âÃâ¬ÃÅGenerating accurate rule sets without global optimizationâÃâ¬ÃÂ. Proceedings Fifteenth International Conference on Machine Learning, pp: 141-151.
- Ramesh D, Vishnu Vardhan B., âÃâ¬ÃÅData Mining Techniques and Applications to Agricultural Yield DataâÃâ¬ÃÂ, IJARCCE, Vol. 2, Issue 9, September 2013.
- Raorane A.A., Kulkarni R.V, âÃâ¬ÃÅReview- Role of Data Mining in AgricultureâÃâ¬ÃÂ, IJCSIT, Vol. 4, No. 2, pp: 270-272, 2013
- https://www.agmarknet.nic.in/
- https://cacp.dacnet.ni
|