ISSN ONLINE(2278-8875) PRINT (2320-3765)
ISSN ONLINE(2278-8875) PRINT (2320-3765)
Manoj Kumar Nigam1, A. Krishna Nag2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Advanced Research in Electrical, Electronics and Instrumentation Engineering
The evolution of current centralized generation in the form of distributed generation and Smart Grids provides a great opportunity to eradicate several issues associated with energy efficiency, energy security, power quality and the drawback of aging power system infrastructures. In order to meet the rising electrical power demand and increase service quality as well as reduce pollution, the existing power grid infrastructure should be developed into a Smart Grid that has the flexibility to allow interconnection with the distributed generation. However, integrating distributed generation to power systems causes several technical issues, especially system stability. Therefore, to fully address the issue, current existing power systems should be up-graded to Smart Grid. To make the power grid become 'smarter', particularly in terms of stability and flexibility, Flexible AC Transmission System (FACTS) devices, especially Static Synchronous Compensators (STATCOM) are used. This paper discusses the need and impacts of distributed generation in Smart Grid technology, in particular it identifies and determines whether the system remains stable or not after installing distributed generation into Smart Grid systems. Further, an attempt has been made to show that the STATCOM makes the grid become smarter. It is actually a voltagesource converter which can act as either a source or sink of reactive AC power to an electricity network.
Keywords |
| power quality issues, distributed generation, smart grid, FACTS, STATCOM |
INTRODUCTION |
| Currently, the main source of electrical power generation is fossil fuel producing carbon dioxide (CO2) emission and other gases, which leads to global warming. Due to environmental issues in reducing greenhouse gases (GHG), the utilization of renewable energy sources (RES) is now growing rapidly and is being widely accepted as an alternative power supply. |
| An important phenomenon in this regard for further future electric power generation is distributed generation, which is also known as embedded generation, dispersed generation or decentralized generation.Distributed generation in simple term can be defined as a small-scale generation. It is active power generating unit that is connected at distribution level. |
| In order to meet the rising electrical power demand and increasing service quality demands, as well as reduce pollution, the existing infrastructure should be flexible for interconnectivity with distributed generation, such as wind turbines and solar power. However, integrating this concept of distributed generation into Smart Grid systems will increase many complex issues on real time operation, such as on power flow direction, protection, voltage profile, power quality and stability. |
II. IMPACTS OF DISTRIBUTED GENERATION |
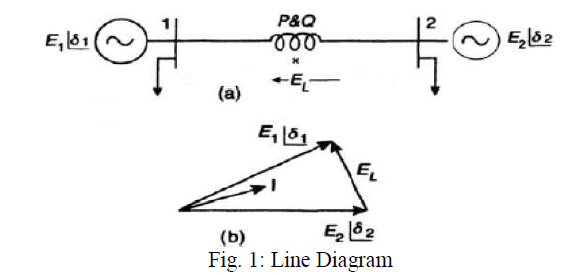
| The following isa simple model of power flow diagram in a transmission system with two power generators with voltages E1 and E2 integrated by a transmission line, which may be interconnecting points or may have load. The transmission line is assumed lossless and represented by the reactance X. The corresponding phasor diagram is also shown below. |
 |
| As per the earlier work carried out on Distributed Generation and Power Quality, Some of the Various Issues involved with distributed generation are as follows: |
| Voltage Regulation, DG Grounding Issue, Harmonic Distortion, Flicker, Islanding, Protection System, False tripping of feeders, Fuse coordination problems, Unwanted tripping of production units, Blinding of protection, Increased or decreased fault levels, Unwanted islanding, Prohibition of automatic reclosingetc.; |
III.EFFICIENT COMMUNICATION |
| In this scheme, each node with message searches for possible path nodes to copy its message. Hence, possible path nodes of a node are considered. Using NSS, each node having message selects its path nodes to provide a sufficient level of end-to-end latency while examining its transmission effort. Here, it derives the CSS measure to permit CRNetworks nodes to decide which licensed channels should be used. The aim of CSS is to maximize spectrum utilization with minimum interference to primary system. Assume that there are M licensed channels with different bandwidth values and ydenotes the bandwidth of channel c. Each CR-Networks node is also assumed to periodically sense a set of M licensed channels. Mi denotes the set including Ids of licensed channels that are periodically sensed by node i. suppose that channel c is periodically sensed by node i in each slot and channel c is idle during the time interval xcalled channel idle duration. Here, it use the product of channel bandwidth yand the channel idle duration x, tc = xy, as a metric to examine the channel idleness. Furthermore, failures in the sensing of primary users are assumed to cause the collisions among the transmissions of primary users and CR-Networks nodes. |
IV.SECURITY |
| Spectrum sensing: Detecting unused spectrum and sharing it, without harmful interference to other users; an important requirement of the cognitive-radio network to sense empty spectrum. Detecting primary users is the most efficient way to detect empty spectrum. Spectrum-sensing techniques may be grouped into three categories: |
| Transmitter detection: Cognitive radios must have the capability to determine if a signal from a primary transmitter is locally present in a certain spectrum. There are several proposed approaches to transmitter detection: |
| 1. Cooperative detection: Refers to spectrum-sensing methods where information from multiple cognitive-radio users is incorporated for primary-user detection. |
| 2. Interference-based detection. |
| Since primary user networks have no requirement to change their infrastructure for spectrum sharing, the task falls to CRs as secondary users to detect the presence of primary users through continuous spectrum sensing. Spectrum sensing by CRs can be conducted either individually or cooperatively. Recently, the efficacy of cooperative spectrum sensing has gained a great deal of attention. There are several advantages offered by cooperative spectrum sensing over the non-cooperative methods. However, due to the randomness of the appearance of PUs, it is extremely difficult to achieve fast and smooth spectrum transition leading to limited interference to PUs and performance degradation of SUs. Locally collected and exchanged spectrum sensing information is used to construct a perceived environment that will impact CR behaviour. This opens opportunities to malicious attackers. In cooperative spectrum sensing a group of secondary users perform spectrum sensing by collaboratively exchanging locally collected information. Malicious secondary users may take advantage of cooperative spectrum sensing and launch attacks by sending false local spectrum sensing results to others, resulting in a wrong spectrum sensing decision. Two known security threats in CRs are Selfish Primary User Emulation (SPUE) and Malicious Primary User Emulation (MPUE) attack. These types of attacks emulate signals with the characteristics of incumbent primary users to fool other secondary users. |
| SPUE: In this attack, an attacker’s objective is to maximize its own spectrum usage. When selfish attackers detect a vacant spectrum band, they prevent other secondary users from competing for that band by transmitting signals that emulate the signal characteristics of primary user signals. This attack is mostly carried out by two selfish secondary users. |
| MPUE: In this attack, the objective is to obstruct the DSA process of SUs- i.e., prevent SUs from detecting and using vacant licensed spectrum bands, causing denial of service. |
| Using the Trust-Worthy algorithm it defines a threshold value to the SUs to overcome the PUE attacks. It enables CRNetworks nodes to efficiently utilize the available spectrum channels. Nodes, which can easily find various licensed channel opportunities without interfering the primary system increases. This reveals that it has a potential to be able to convert the various network conditions into a performance improvement. |
V. RESULT AND DISCUSSION |
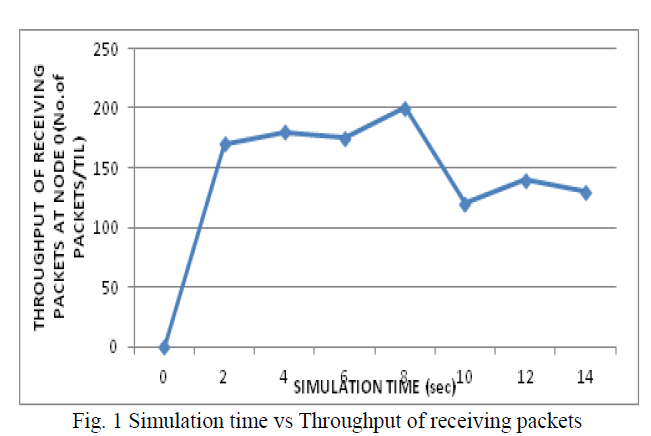 |
| In the fig 1, it shows the graph of time Vs throughput of receiving packet. Throughput is the average rate of successful message delivery over a communication channel. |
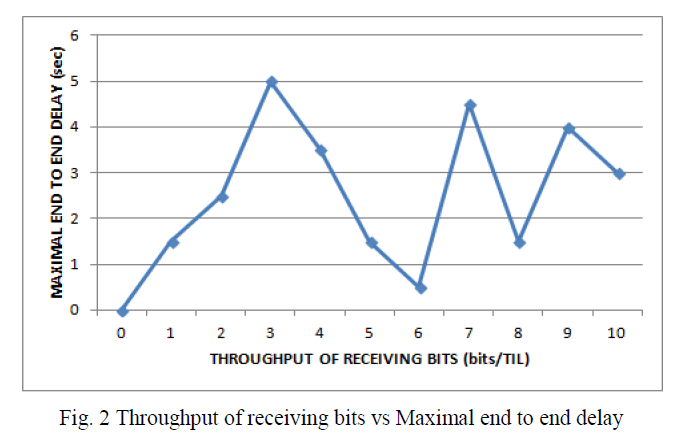 |
| In the fig 2, it shows the graph of throughput of received bits Vs Maximal end to end delay. End to end delay is the time taken by a packet to travel from source to reach destination. |
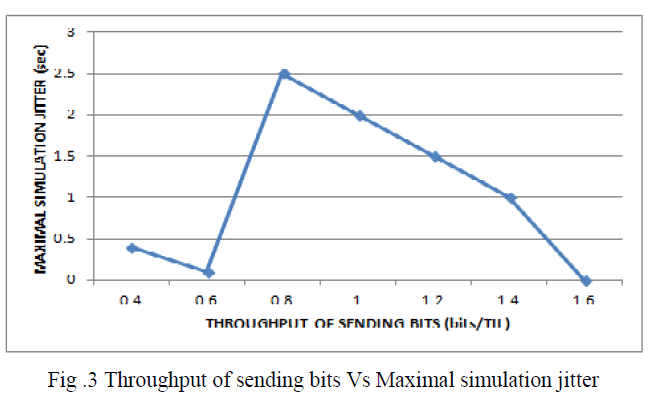 |
| In Fig 3, Throughput of sending bits Vs Maximal simulation jitter. Jitter is the undesired deviation from true periodicity of an assumed periodic signal. Jitter period is the interval between two times of maximum effect (or minimum effect) of a signal characteristic that varies regularly with time. |
VI.CONCLUSION |
| Thus it allows each node with message to decide whether to copy the message to a path node by optimizing its transmission effort in order to provide a sufficient level of message delay. Using a channel selection scheme provides spectrum utilization while it minimizes the interference level to primary system. Using trustworthy algorithm, itimproves the trustworthiness of the Spectrum sensing in CR-Networks. It enables network nodes to adaptively regulate their communication strategies according to dynamically changing network environment. |
References |
|