ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
SUNITA SHARMA1, AMIT CHUGH2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
Cloud computing is envisioned as the next-generation technology. It is an Internet based technology where quality services are provided to users including data and software, on remote servers. Advantages of cloud computing includes creating and storing data at remote servers, hence utilizing the client resource to the minimum level. But this advantage implicitly contains drawback of data security and privacy vulnerabilities. There are a number of algorithms and methodologies available for achieving data security in cloud computing. In this paper we look at the current researches related to data security issues like integrity and confidentiality. In particular, we will discuss how to secure client’s data on remote cloud servers.
Keywords |
| Trusted Storage, confidentiality, integrity, Kerberos services, reliability. |
INTRODUCTION |
| Cloud computing is the use of computing resources (hardware and software) that are delivered as a service over a network (typically the Internet). The name comes from the use of a cloud-shaped symbol as an abstraction for the complex infrastructure it contains in system diagrams [1]. Cloud storage is simply a term that refers to online space that you can use to store your data. As well as keeping a backup of your files on physical storage devices such as: external hard drives, sub flash drives, etc [2]. |
| Example of cloud computing: Amazon Cloud Drive, G Space, Minus, Web e-mail providers like Gmail, Hotmail and Yahoo! Mail store e-mail messages on their own servers, A DriveYouTube,Social networking sites like Face book and MySpaceSites like Flicker and Picasa host millions of digital photograph. As with any storage system, there are certain security properties that are desirable in a cloud storage system: confidentiality, integrity, write- serializability and read freshness. These properties ensure that user’s data is always secure and cannot be modified by unauthorized users and the data is always at the latest versions when being retrieved by the user. [3] Storing important data with cloud storage providers comes with serious security risks. The cloud can leak confidential data, modify the data, or return inconsistent data to different users. This may happen due to bugs, crashes, operator errors, or misconfigurations. Furthermore, malicious security breaches can be much harder to detect or more damaging than accidental ones: external adversaries may penetrate the cloud storage provider, or employees of the service provider may commit an insider attack. [4] These concerns have prevented security conscious enterprises and consumers from using the cloud despite its benefits [5]. |
DISCUSSIONS |
A.Problem statement |
| Security and reliability are main challenges of cloud computing. Clients aren't likely to entrust their data that on cloud will not be accessed by other clients. To achieve security on cloud there are so many techniques and algorithm available. Some of these techniques are: |
| Encryption: technique use complex algorithm to hide the original information with the help of encryption key. |
| Authentication processes, which require creating a user name and password. |
| Authorization practices –firstly list of authorized clients, who can access data stored on cloud system. |
| However, many people worry that data saved on a remote storage system is vulnerable. . Hackers could also attempt to steal the physical machines on which data are stored. A disgruntled employee could alter or destroy data using his or her authenticated user name and password. Cloud storage companies invest a lot of money in security measures in order to limit the possibility of data theft or corruption. |
| We are discussing some techniques that are helping how to get security at administrative level and for different clients by doing survey and reading the different research paper. In this article we look at the Trusted Platform Module (TPM) to get confidentiality and integrity in clouds. Kerberos services to authenticate the users and SLA Proof for retrieving writeserializability, and freshness in clouds. |
A TRUSTED STORAGE SYSTEM FOR THE CLOUD |
| The main task of is “A Trusted Storage System “not only storing the data as well as it needs confidential storing also and integrity of the data would be maintained. |
| To achieve confidentiality and integrity of the data, cryptographic techniques can be used to encrypt data. Encrypted file systems (EFS) can be used to encrypt the client’s data within the cloud. An encrypted file system is used to encrypt the user’s data, manage and create keys which are used for data encryption and decryption “[6]. |
| Integrity of the data within the cloud is developed. Five protocols are developed which ensure that the client’s data is stored only on trusted storage servers, replicated only on trusted storage servers, and guarantee that the data owners and other privileged users of that data access the data securely. The system is based on trusted computing platform technology [7]. |
A. Encrypted File Systems |
| EFS (Encrypted File System) meant for encrypting stored files. Encryption procedures are transparent to the user and occurs at the file system level not at the application level. These methods automatically use cryptographic techniques for encryption; hence user saves from cumbersome task of managing keys in encryption. Diagram below depicts the process of encryption using EFS: |
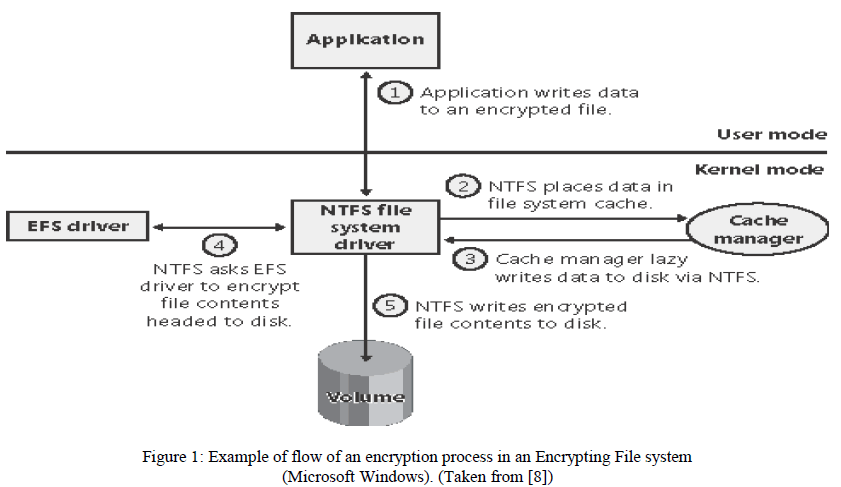 |
| Process explanatory steps are as follows: |
| Data passes from application part to the NTFS file system driver. |
| NTFS passes data to Cache Manager, whose responsibility is to write data to the disk using NTFS. |
| NTFS passes the data to EFS driver for encryption. EFS driver encrypts data and responds to NTFS with data and encryption/decryption keys. |
| NTFS finally writes data and associated keys on the disk. |
| B. Trusted Platform Module |
| What is a TPM? |
| The Trusted Platform Module (TPM) is a computer microchip or a microcontroller which is designed to perform various security-related and cryptographic functions. It can securely store the artifacts used to authenticate the platform of a computer.[9] The artifacts can include encryption keys, certificates, passwords, and integrity metrics of a platform. The TPM can be used in the process of remote attestation of a platform of a machine which will be discussed further later. It is typically installed on the motherboard of a computer. The TPM uses a hardware bus to communicate with the rest of the system. The TPM is a specification or implementation of that specification as a chip. The specification is provided by the Trusted Computing Group [10]. |
C. Architecture of the TPM |
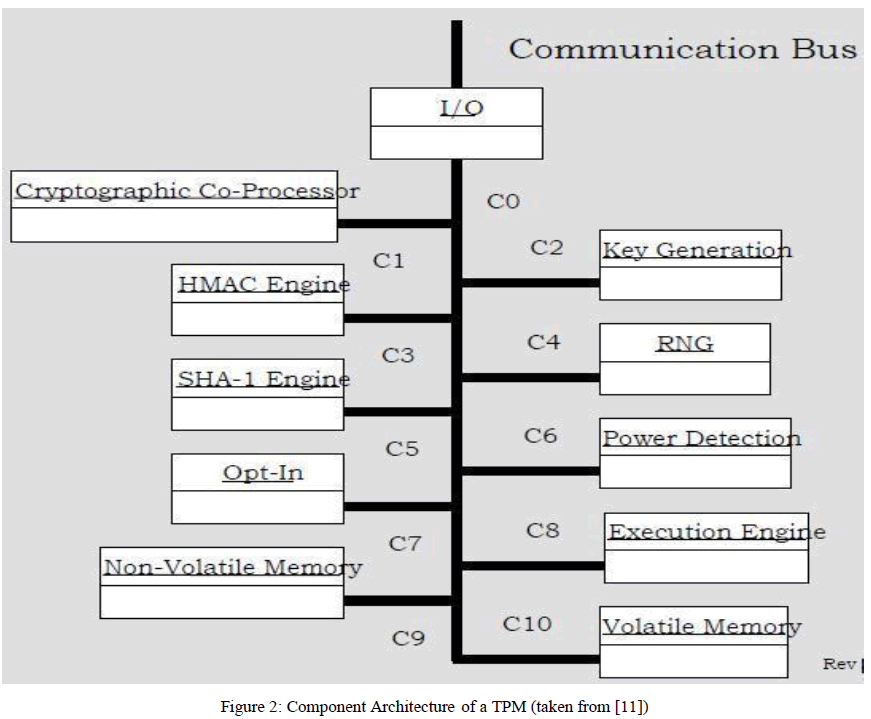 |
| Short description of the different architectural components is as follows: |
| The input and output component is for controlling information flow through communication bus. It does controlling by sending/receiving messages to appropriate components. |
| Cryptographic Co-Processor component performs cryptographic functions like Asymmetric Key Generation (RSA), Asymmetric Encryption/Decryption (RSA), Hashing (SHA-1), and Random Number Generation (RNG), with in TPM. |
| RSA key pairs and symmetric keys are generated by Key Generation Component. |
| HMAC engine solves two main purposes. First purpose is proof of knowledge of user data authentication and second purpose is authentication of request received by TPM. |
| RNG generates random values. These random values acts as nonces for key generation, also plays role in having randomness in signatures. |
| SHA-1 Engine functions during machine boot time, for platform measurement. |
| Power detection component manages the power states in TPM, synchronized with platform power states. |
| Opt-In component functions for following states of TPM : |
| Turn-on and Turn-off, Enable and Disable, Activate and Deactivate |
| Execution Engine responsible for execution the TPM commands received from the I/O component. Non-Volatile Memory component is for storing identity and state of TPM persistently. Entities authorized by TPM owner can also use Non-Volatile Memory for data storing. |
| Result of Trusted Storage system: |
| By using TPM model, security can achieve only for system administrative level. But there is no solution for individual users because cloud is maintained by third party on network. This proposed system gives confidentiality and integrity of the data stored only on trusted storage server. |
ENSURING DATA STORAGE SECURITY IN CLOUD COMPUTING WITH EFFECT OF KERBEROS |
| In this technology we ensure cloud storage security with the help of Kerberos authentication service. That is by implementing the Kerberos; security would be achieved for users. We define the Kerberos for create the ticket and granting ticket for each user. So to make the more focus on user we made more secure [12]. |
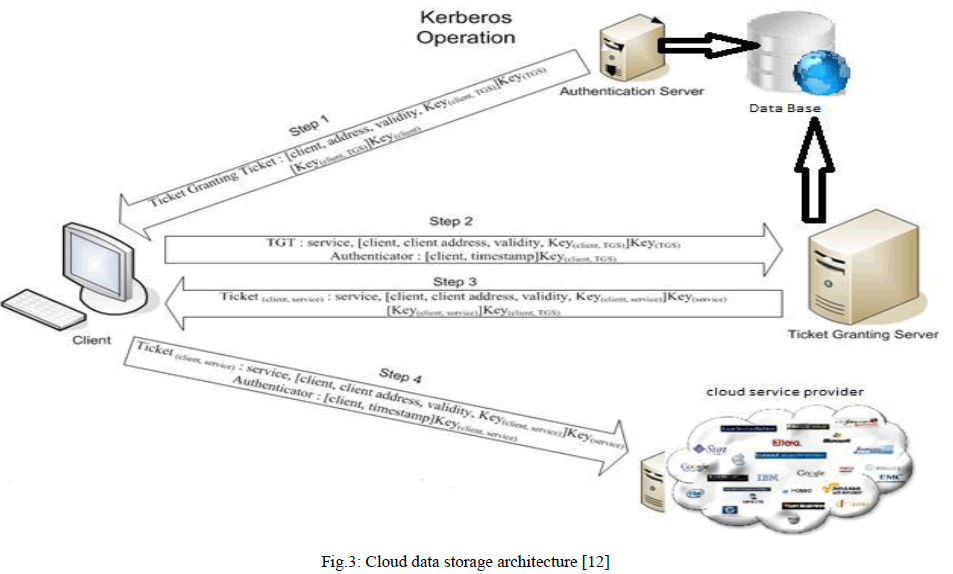
| Kerberos operation |
| Kerberos use strong encryption method and complex ticket granting algorithm [12] so that user can be authenticated on network. It also uses session key which allow encrypted data stream over an IP network for each user. If new user wants to use the cloud then he should make profile on network by providing information then attributes like user ID, hashed password will save in the large Data Base. All user are registered with the Kerberos server have user ID and passwords. Following steps must be taken by each user for using cloud data: |
| Log on to workstation. |
| Send the request for ticket granting ticket to the AS. |
| AS verifies user’s access right in database, create ticket-granting ticket and session key. Results are encrypted using key derived from user password. |
| User will send the request cloud service granting ticket to TGS. |
| TGS will send the Ticket+session key to the user (it execute one per type of service). |
| Workstation sends ticket and authenticator to cloud server provider. |
| Server verifies ticket and authenticator match, then grant access to service. |
| Here assumption is that each user, who connects and utilizes the cloud server, must create the profile and provide some private information for more security of his data at cloud servers. |
| Architecture |
 |
ENABLING SECURITY IN CLOUD STORAGE SLAS WITH CLOUD PROOF |
| I did another survey on cloud storage security based on “Enabling Security in Cloud Storage SLAs with Cloud Proof”. According to this survey it presents a Cloud proof, a secure storage system specifically designed for cloud. In cloud proof customers can not only detect violations of integrity, write-serializability, and freshness, they can also prove the occurrence of these violations to a third party [13] |
System Overview of cloud proof: |
| Cloud Proof has the following four goals. |
| Goal 1: Users should detect the cloud’s violations of integrity, freshness, and write-serializability. Users should provide confidentiality to themselves by encrypting the data they store on the cloud. |
| Goal 2: Users should be able to prove cloud violations whenever they happen. Any proof system has two requirements: (1) the user can convince a third party of any true cloud violation; and (2) the user cannot convince a third party when his accusation of violation is false |
| Goal 3: Cloud Proof should provide read and write access control in a scalable (available) way. Since we are targeting enterprise sizes, there may be hundreds of thousands of users, many groups, and terabytes of data. We want to remove data owners from the data access path as much as possible for performance reasons. Owners should be able to rely (in a verifiable way) on the cloud for key distribution and access control, which is a highly challenging task. |
| Goal 4: Cloud Proof should maintain the performance, scalability, and availability of cloud services despite adding security. The overhead should be acceptable compared to the cloud service without security, and concurrency should be maintained. |
| The system should scale to large amounts of data, many users per group, and many groups, since this is demanded by large enterprise data owners. |
CONCLUSIONS |
| In this discussion we found various solutions to enforce the security for data stored on cloud. In this paper we demonstrate how confidentiality and integrity security can be achieved by using EFS and TPM techniques. Kerberos proofs the authentication of users on network. SLAs with Cloud Proof build confidentiality, integrity, write-serializability and read freshness (denoted by C, I, W, F). Providing privacy to customer and his data on cloud is very complex and cost effective system. |
References |
|