ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
P.G.Mamatha1, T. Ravi Kumar Naidu2, T.V.S. Gowtham Prasad3
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
After a rapid growth of cyber revolution, developing a secret communication is a major task of security that has gained increasing importance. Cryptography and steganography are the best methods for introducing hidden communication. Current technology allows steganography applications to hide any digital file inside of any other digital file. Due to the existence of their redundancies, audio and video files are much suitable for the purpose of hiding. Audio steganography is a challenging subject because human auditory system (HAS) is more sensitive than human visual system (HVS). It requires a text or audio secret message to embed within a carrier audio file. Several basic audio Steganographic methods like LSB method, parity coding etc., are in existence, but the proposed LSB with XORing method gives high security which undergoes cryptographic randomized algorithm too. By performing two level encryption, capacity and robustness will be increased.
KEYWORDS |
| Audio steganography, cryptography, LSB, HAS |
I. INTRODUCTION |
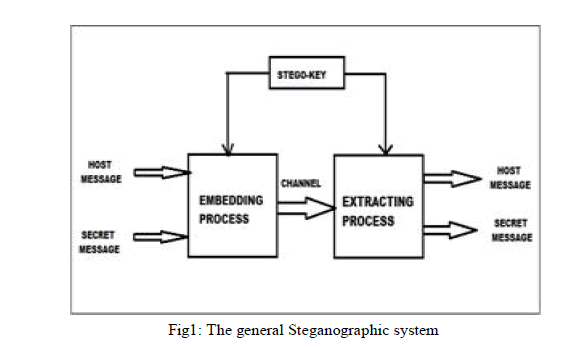
| Steganography is a process of hiding a secret message within a host message and extracting as its destination. Anyone else apart from the sender and intended recipient observing the message will fail to know it contains hidden data. The term hiding refers to the process of making the information secret. With the introduction of digital audio files, this has taken on a whole new meaning to create new methods for performing reversible data hiding as it is often dubbed. This has many possible applications including the copyright watermarking of audio, video and still image data. |
| In digital media, Steganography is mainly oriented around the undetectable transmission of one form of information within another. In this process, first the secret data is encrypted and then hide it in an original data. The stego medium is obtained by the addition of cover medium, secret data and approached algorithm which is nothing but a stego key. The cover medium is the file in which the secret data is hidden. Here, the cover medium is typically an audio file. The stego medium is also the same type of file in the cover medium. In a computer based audio Steganographic system, secret messages are embed in digital signals. In audio Steganography the perception of the Human auditory system (HAS) is used to hide information in the audio because it perceives over a wider power range. Embedding secret messages in digital sound is usually a difficult process than embedding data in other media due to its perception. Here, Steganography is often mixed with cryptography. Unlike steganography, Cryptography changes the representation of the secret message. The main goal of approached method is to combine steganography and cryptography in such a way to make it harder for an intruder to retrieve the plain text of a secret message from a stego object. The general steganography system is shown in Fig.1. |
II. LITERATURE SURVEY |
| Steganography: |
| The word steganography is a combination of two words which are taken from Greek language: steganos which means covered and graphie which means writing and literally called as covered writing. Thus steganography is said to be a covert communication. In contrast to Cryptography, where the enemy is allowed to detect, intercept and modify messages without being able to violate certain security premises guaranteed by a cryptosystem, the goal of Steganography is to hide messages inside other harmless messages in a way that does not allow any enemy to even detect that there is a presence of second message [1]. Both steganography and cryptography are meant for secret communication but the approach is different. Hiding of secret message using steganography can be done in different forms like text steganography, image steganography, audio steganography and video steganography. Encoding secret messages in audio is the most challenging task while using steganography because human auditory system (HAS) is more perceptive than human visual system (HVS) [5]. Thus audio file is used as a cover file to hide secret data and it is called audio steganography. In Audio steganography, secret message is embedded into digitized audio signal which results into altering the binary sequence of corresponding audio file. There are several methods are available for audio steganography. |
 |
| LSB coding: |
| The LSB modification is one of the simplest audio steganography techniques which is simple to implement and easy to detect but it provides high capacity. In this technique, data is being hidden directly in least significant bits of audio samples in a particular way [6]. There are several methods of data embedding in LSB technique which are Lowest Bit Coding, Sample selection, Bit selection, XORing of LSB's, Variable Low Bit Coding, Average Amplitude Method, Parity Coding etc., |
| Parity coding: |
| Instead of dividing a signal down into individual samples, the parity coding method breaks a signal into isolated regions of samples and encodes each bit from the secret message in a sample region parity bit. If the parity bit of a selected region does not match the secret bit to be encoded, the process flips the lsb of one of the samples in the region. |
| Spread spectrum: |
| It spread out the encoded data across the available frequencies as much as possible. This method spreads the secret message over the audio file’s frequency spectrum, using a code that is not dependable on actual signal. Thus, final signal occupies a band width which is in excess than requirement. |
| Cryptography: |
| Cryptography is also meant for secret communication but unlike steganography it doesn’t conceal the secret data but it scrambles the data. So, cryptography makes the secret data meaningless which is difficult to detect by the third party. Cryptography is also derived from the Greek word ‘cryptos’ which means hidden and ‘graphie’ which means hidden writing and it undergoes the process called encryption. The process of transforming plain text into cipher text is called encryption. Cryptography also provides authentication which is used to verify the identity. Here, the cryptographic process involved is randomized algorithm which consists of parity level and di-bit level. |
| Cryptographic process: |
| Step 1: The encryption of parity checking level starts here. The fundamental aspect of this level is that the key for encryption is stored in the data bits pattern itself and this key varies according to the varying data bits. The encryption is done in bit- by-bit operation. For encrypting data bits having index number (odd) like 1 3 5 7, its corresponding key is data bits having index number (even) 2 4 6 8. The two nibbles are then checked bit-by-bit so that the final result has even parity with data bits 1 3 5 7. This final result is the pseudo-encrypted bit pattern 1` 3` 5` 7` likewise even sequence of bits also encrypted. |
| Step 2: The di-bit level is taking the first and last bits of encrypted bits as reference bits. |
| Step 3: By using reference bits, the remaining bits are indicated as NC (not complement), LSB-C (least significant bitcomplement), MSB-C (most significant bit-complement), FC (full complement). The inverse process is done in decryption process. |
III. PROPOSED METHOD |
| LSB CODING WITH XORING METHOD: |
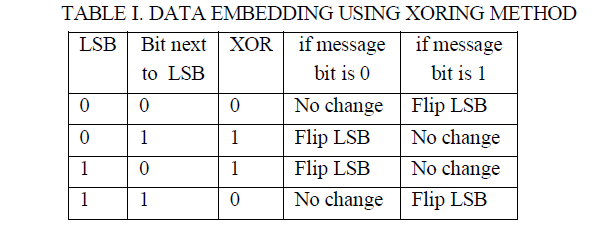
| LSB coding gives high bit rate but it is easy to implement and easy to detect. So instead of using simple LSB method alone, combining it with XORing method increases the level of security. This method performs XOR operation on the LSBs and depending on the result of XOR operation and the message bit to be embeds, the LSB of the sample is modified or remains same [2]. The algorithm for data embedding and data retrieval are explained below and tabular representation of embedding process is given in table I. |
 |
| Steps for data embedding: |
| 1. Read the host audio message and convert it into binary sequence of bits. |
| 2. Read the secret message to be embedded and convert it into binary sequence. Its size must be less than the size of the cover audio. |
| 3. The XORing procedure takes place as follows: |
| • If the message bit to be embedded is 0, then flip the LSB so that the XORing of LSB and next to LSB is 0. |
| • If the message bit to be embedded is 1, then flip the LSB so that the XORing of LSB and next to LSB is 1. |
| 4. Embedding of message bit into the LSB’s of the cover audio is done. |
| 5. The modified cover audio samples are then forms the stego audio signal. |
| Steps for Data Retrieval: |
| 1. Read the Stego audio file. |
| 2. Retrieving of message bit is obtained by XORing the LSB and the bit next to LSB. |
| • If the result of XORing is 0, then the message bit is 0. |
| • If the result of XORing is 1, then the message bit is 1. |
| 3. After retrieval of every such 16 message bits, they are converted to their equivalent decimals. |
| 4. Finally the secret message is reconstructed. |
IV. PERFORMANCE MEASURES |
| Mean square error: |
| It is defined as the square of error between cover audio signal and stego audio signal. The distortion in the audio signal can be measured as follows. |
 |
 |
IV. EXPERIMENTAL RESULTS |
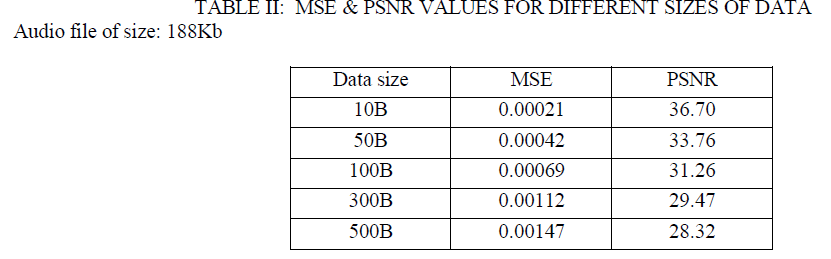
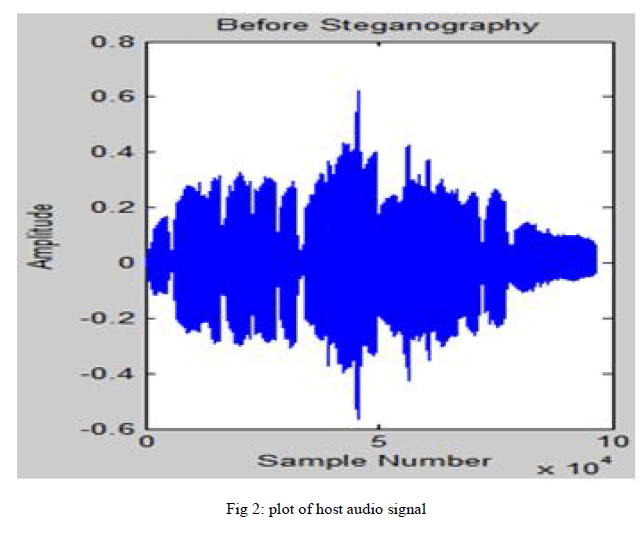
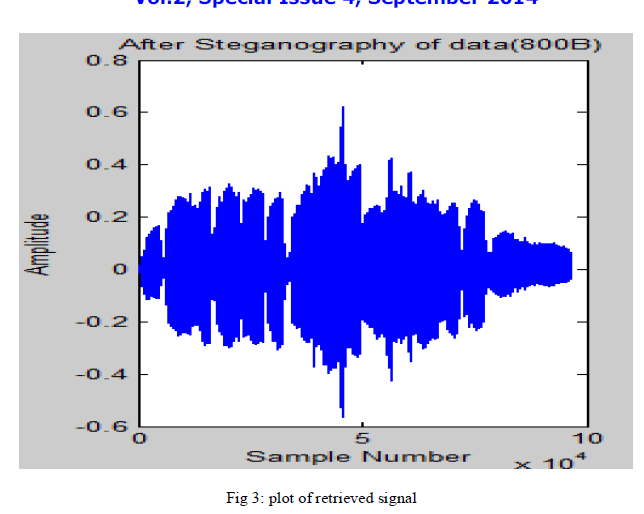
| This paper proposes the LSB coding with XORing method in which the data embedding is done by XORing the LSB’s. Fig.2 shows one of the secret signals used in XORing method. Fig.3 shows the secret signal retrieved at the receiver side. It is obvious from both figures that there is no distraction between the original and retrieved message. Thus, by combining steganography and cryptography gives high security. |
 |
 |
V. CONCLUSIONS |
| Audio steganography is more challenging than image steganography because the HAS has more sensitive than human visual system (HVS). This paper proposes the method of LSB coding along with the cryptographic encryption to hide the data in digital audio files. There is no difference between stego audio signal & the original audio signal i.e. hidden information is recovered without any error. It gives great security and high payload capacity |