Keywords
|
| Addressing Protocol, wireless, mobile devices, data transmission. |
INTRODUCTION
|
| Mobile devices such as personal digital assistants (PDAs) and smart phones it can be used to control and monitor machinery in industrial environments. Mobile devices are also used for exchanges of information between workers. Such mobile devices have multiple wireless network interfaces, such as Bluetooth, 3G, and Wi-Fi. Each wireless network interface has fairly different characteristics in terms of its energy consumption, service area, data transfer rate, and other factors. |
| wireless technologies are widely used in various industrial fields with various network interfaces. The network interface that consume more batter energy that can be handled. A wireless network allows for easy connectivity between computers. Files can be shared over the wireless network without the need of saving them to disk or flash drive. Printing tasks can be sent to one printer from different computers through the wireless network, but also other devices set to the wireless network can be shared such as a scanner. Another benefit that wireless networking presents is the way it allows the internet to be used. Multiple computers and devices within a wireless network’s range can use the same ISP for internet use, and can also sign on at the same time from any location in range. Phone calls can be placed on a wireless network using the internet. Voice Over Internet Protocol, abbreviated as VOIP, is the name for phone calls made over the internet. VOIP calls can be cheaper than regular calls, especially beneficial to those who want to make international calls. In General, Collisions on Wireless networks can be a major source of increased latency and packet retransmissions. When collisions occur energy constrained wireless networks, extra latency and retransmissions equate to excess energy consumption. On the mote platform energy is at a premium, therefore collision avoidance can increase the overall lifetime of the network. |
RELATED WORK
|
| the A distributed topology control technique for low interference and energy efficiency in wireless sensor networks technique for energy efficient and low interference topology control in wireless sensor networks was developed in the form of the SBYaoGG algorithm[1]. The limitation is algorithm has the good energy efficiency performance but it has the poor interference performance. In the Integrated Design Framework of Fault-Tolerant Wireless Networked Control Systems for Industrial Automatic Control Applications has A design framework of fault-tolerant wireless networked control systems (NCSs) is developed for industrial automation applications. The main objective is to achieve an integrated parameterization and design of the communication protocols, the control and fault diagnosis algorithms aiming at meeting high real-time requirements in industrial applications. The limitation is the communication speed is low. Recently, wireless technologies have become widely used in various industrial fields, as wireless technologies offer a number of benefits to businesses, including mobility, flexibility, and cost savings because they do not need wired connections [1], [2]. In factories, stationary systems can be connected over a wireless network to mobile subsystems or robots for better connectivity [3].Furthermore, wireless technologies can make it much easier and simpler to gain access to plant machinery for diagnostic or programming purposes [4].Mobile devices such as personal digital assistants (PDAs) and smart- phones can be used to control and monitor machinery [5]. Mobile devices are also used for exchanges of information between workers. Such mobile devices have multiple wireless network interfaces, such as Bluetooth, 3G, and Wi-Fi. Each wireless network interface has fairly different characteristics in terms of its energy consumption, service area, data transfer rate, and other factors [6]–[8]. 3G networks have wider service areas and consume greater receive/transmission energy compare to Wi-Fi net- works [6], [9]–[10]. |
| Generally, a Wi-Fi access point can cover a radius of about 100 200 m. 3G consumes about twice as much energy as Wi-Fi to transfer the data [6], [10]. Most current industrial mobile devices are operated by a limited built-in battery. Thus, energy efficiency is a very important issue and an elementary requirement for battery-operated industrial mobile devices [2]. Many studies have been proposed to enhance energy efficiency in a variety of ways. We can improve energy efficiency by leveraging multiple wireless network interfaces. When multiple network interfaces are available in a certain area, we have to use the network interface that is most energy efficient. For example, when 3G and Wi-Fi are both avail- able at the same time in a certain area, the Wi-Fi interface has to be selected in order to reduce energy consumption when the data transfer rate can be ignored. Many studies have been conducted to improve and extend the operating time of mobile devices by leveraging multiple network interfaces [10].To devise efficient wireless network interface management schemes, several factors should be considered, such as the data transfer rate, the signal strength, and the types of available network interfaces. |
PROPOSED ALGORITHM
|
Design Considerations
|
zippy addressing Protocol
|
| 1) Bootstrap the network |
| 2) The first incoming node act as the initial node that can manage the whole network |
| 3) The initial node send the address Request to all other node for managing the IP address |
| 4) The each mobile device has Ip address . |
| 5) The network based the mobile addresses may varied |
| 6) The each node should be self configurable one |
| 7) If any two nodes has same IP addresses means that warning information send by initial node. |
| 8) The mobile can choose the next IP address from the network |
Description:
|
| To proposed the zippy addressing protocol that can be handled the addressing problem in the network dynamically. In each and every node has temporary ip address that based it can be communicated. If the network may varied the temporary address based the node can entered and the address can be verified by network. If the network has same IP address means that address will changed by the network and allow to perform a operation and the transmission delay also detected in the dynamic network and the transmission speed is more to transmit the data. An enhanced handover technique is used to handover the mobile device in one network interface to other. |
Enhanced handover Technique
|
| System Discovery |
| 1) Send the handoff request |
| 2) Check availability of the network |
| 3) Collect the parameter for the corresponding network. Handover Decision Phase |
| 1) Pick the best network |
| 2) Compare with the requirement. Handover Execution phase |
| 1. If the requirement satisfied send the request to the base station. |
| 2. Connection will be established. |
METHODOLOGY
|
| ? Network initialization |
| The initiator can allocate for each node and maintain all addresses and check address allocation occur or not |
| ? Network analyzation |
| They analyze interface of network region and analyze parameters the data transfer energy, interface delay. |
| ? Handoff system discovery |
| In this module check the availability of handoff network and its parameter. |
| ? Decision phase |
| This phase compares the nearby network QOS and the mobile users QOS with this QOS decision maker makes the decision to which network the mobile user has to direct the connection. (Compare the network and its parameters) |
| ? Execution phase |
| This phase is responsible for establishing the connection and release the connections and as well as the invocation of security service. |
SIMULATION RESULTS
|
| To analyse the performance of the proposed system lots of simulation experiments are conducted. The proposed system is implemented in Network Simulator (NS2). In the simulation experiments several parameters are used. They are listed in the below table. |
| To analysis the performance the proposed method several performance metrics are used. They are Probability of Collision and control overhead. |
Probability of Collision
|
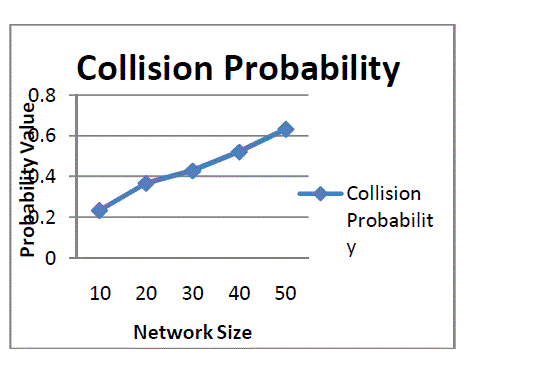
| This project analyze to evaluate the probability that our scheme causes an address collision. A collision occurs when two different joining nodes generate the same address and the same identifier number or if two disjoint partitions own exactly the same filters. In the first case the joining nodes do not notice that their addresses are the same because the message from the other node seems to the first node like a retransmission of its own message. In the second case, the partition merging procedure is not started because the signatures of the Hellos are the same for both the partitions, and, consequently, the network would have a collision for each of its addresses. This is shown in the below table |
| The above figure shows the collision probability, considering an address range of 256 entries. This project observe that there is a high probability of address collision, but the AREQ collision probability is negligible, even for a number of nodes greater than the number of available addresses, due to the use of the identifiers |
Control Overhead
|
| The main procedures in addressing protocols are network initialization, node joining/leaving, and merging. Usually, these procedures, as well as the ordinary protocol operation, generate control overhead, reducing the available bandwidth. This project estimate the number of control messages sent by all these procedures for ZAP, the partition identifiers, which are numbers shared by the nodes in the same partition to make it possible to distinguish the current partition from the others. Every time a node joins the network or a node observes that it lost a neighbour, the partition identifier of the whole network is changed. This project also based on the knowledge of the Allocated list, which describes the allocated addresses, and the Allocated Pending list, which describes the list of the addresses under evaluation to be allocated to joining nodes. This is shown in the below table |
CONCLUSION AND FUTURE WORK
|
| Thus the proposed zippy addressing protocol that can be handled the addressing problem in the network dynamically. In ZAP, bootstrap the network. The first incoming node act as the initial node that can manage the whole network. The initial node send the address Request to all other node for managing the IP address. If any two nodes has same IP addresses means that warning information send by initial node. The mobile can choose the next IP address from the network. The transmission delay also detected in the dynamic network and the transmission speed is more to transmit the data. An enhanced handover technique is used to handover the mobile device in one network interface to other. In this technique, send the handoff request to one network to other then check availability of the network and collect the parameter for the corresponding network. Pick the best network and then connection will be established. The simulation result shows that the algorithm is feasible and has superior performance. |
| In future the address allocation delay will be reduced by initiator of network. The address allocations delay will occur in any other node can entered in the network then first select the random Ip address and then using ZAP. Finally allocate the Ip addresses. During that time the address allocation delay will occurring. That delay will be reduced by initiator nodes. This is my future enhancements. |
Tables at a glance
|
|
|
Figures at a glance
|
 |
 |
| Figure 2 |
Figure 3 |
|
References
|
- A. Willig, K. Matheus, and A. Wolisz, “Wireless technology in industrial networks,” Proc. IEEE, vol. 93, no. , pp.
- H.Hassan, J. Martinez-Rubio, A. Perles, J. Capella,C.Dominguez, and J. Albaladejo, “Smartphone-based industrial informatics projects andlaboratories,” IEEE Trans. Ind. Informat., vol. 9, no. 1, pp. 557–566,2013.
- J. Ploennigs, V. Vasyutynskyy, and K. Kabitzsch, “Comparative study of energy-efficient sampling approaches for wireless controlnetworks,” IEEE Trans. Ind. Informat., vol. 6, no. 3, pp. 416–424, 2010.
- M. A. Viredaz, L. S. Brakmo, and W. R. Hamburgen, “Energy management on handheld devices,” Queue, 8 vol. 1, no. 7, pp. 44–52,2003.
- N. Balasubramanian, A. Balasubramanian, and A. Venkataramani, “Energy consumption in mobile phones: A measurement study andimplications for network applications,” in Proc. 9th ACM SIGCOMM Conf. Internet Measurement Conf. (IMC), New York, NY, USA, 2009, pp.280–293.
- N. Fourty, T. Val, P. Fraissem, and J.-J.Mercier, “Comparative analysis of new high data rate wireless communication technologiesfromWi-Fi to WiMAX,” in Proc. Joint Int. Conf. Autonomic Autonomous Syst. Int. Conf. Netw. Services (ICAS-ICNS), 2005, pp. 66–71.
- R. Gass and C. Diot, “An experimental performance comparison of 3G andWi-Fi,” in Proc. 11th Int. Conf. Passive ActiveMeas. (PAM),2010, pp. 71–80.
- S. X. Ding, P. Zhang, S. Yin, and E. L. Ding, “An integrated design framework of fault-tolerant wireless wireless networked controlsystems for industrial automatic control applications,” IEEE Trans. Ind. Informat., vol. 9, no.1, pp. 462–471, 2013.
- T.M. Chiwewe and G. P. Hancke, “Adistributed topology control technique for low interference and energy efficiency in wireless sensornetworks,” IEEE Trans. Ind. Informat., vol. 8, no. 1, pp. 11–19, 2012.
- U. Varshney and R. Jain, “Issues in emerging 4G wireless networks,”Computer, vol. 34, no. 6, pp. 94–.96,2008
|