Keywords
|
| Digital image forgery, Spliced image, Forgery detection, Illuminant Inconsistencies, SVM classifier |
INTRODUCTION
|
| The progression of the digital information age has evolved to replace technologies with state-of-the-art digital counterparts.The change of photography from requiring smelly chemicals and darkroom tricks to manipulate images has given way to the digital era. With the move to the world of Megapixels, a new door opens to the dark-side of image counterfeiting and forgeries. Gone are the days of needing to create “trick shots” with an analog camera or careful chemical preparation in the darkroom. Today, manipulating an image involves simply using tools available in the digital darkroom, such as Adobe Photoshop or Macromedia Fireworks. With these new techniques easily available to the masses via an inexpensive PC, the need exists to verify the authenticity of a digital image because of our increased reliance on digital media. Two examples of the importance of digital image authentication are the one witnessed in the news media we rely on to provide accurate information and second the courtroom where someone’s fate may depend on the authenticity of a digital image as evidence. This explores these issues with emphasis on creating tools to aid in the detection of digital image tampering for spliced images. |
| Image splicing or photomontage is one of the most common image manipulation techniques to create forgery images. Image splicing is a simple process that crops and pastes regions from the same or separate sources. It is a fundamental step used in digital photomontage, which refers to a paste-up produced by sticking together images using digital tools such as Photoshop. Examples of photomontages can be seen in several infamous news reporting cases involving the use of faked images. Searching for technical solutions for image authentication, researchers have recently started development of new techniques. |
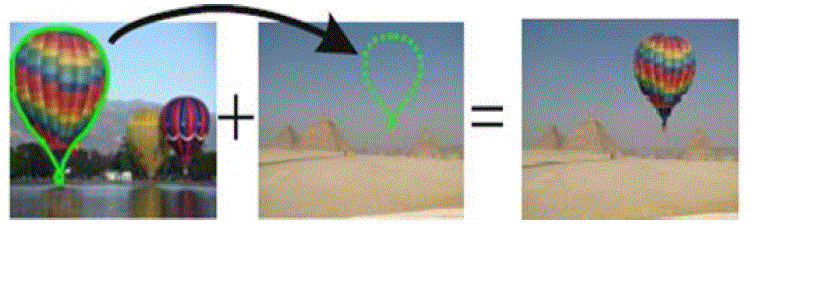
| As shown in Fig. 1, by copying a spliced portion from the source image into a target image, one can create a composite scenery to cheat others. Using image editing softwares, even non-professional users can perform splicing without much difficulty. Although experienced experts can still identify not highly sophisticated forgeries, it is still a challenging issue to tackle this complicated problem by machines in a fully automated way. |
| When assessing the authenticity of an image, forensic investigators use all available sources of tampering evidence. Among other telltale signs, illumination inconsistencies are potentially effective for splicing detection: from the viewpoint of a manipulator, proper adjustment of the illumination conditions is hard to achieve when creating a composite image. When an image is spliced, the statistics of these edges is likely to differ from original images. |
| Exploiting the inconsistencies in illumination of spliced images the tampered image can be detected. When creating a digital composite of, for example, two people standing side-by-side, it is often difficult to match the lighting conditions from the individual photographs. Lighting inconsistencies can therefore be a useful tool for revealing traces of digital tampering. Borrowing and extending tools from the field of computer vision, we describe how the direction of a point light source can be estimated from only a single image. We show the efficacy of this approach in real-world settings. |
RELATED WORK
|
| Johnson and Farid [1] also proposed spliced image detection by exploiting specular highlights in the eyes. In a subsequent extension, Saboia. [2] automatically classified these im-ages by extracting additional features, such as the viewer position. The applicability of both approaches, however, is some-what limited by the fact that people’s eyes must be visible and available in high resolution. |
| Johnson and Farid [1] also proposed spliced image detection by exploiting specular highlights in the eyes. In a subsequent extension, Saboia. [2] automatically classified these im-ages by extracting additional features, such as the viewer position. The applicability of both approaches, however, is some-what limited by the fact that people’s eyes must be visible and available in high resolution. |
| Riess and Angelopoulou [3] followed a different approach by using a physics-based color constancy algorithm that operates on partially specular pixels. In this approach, the automatic detection of highly specular regions is avoided. The authors pro-pose to segment the image to estimate the illuminant color locally per segment. Recoloring each image region according to its local illuminant estimate yields a so-called illuminant map . Implausible illuminant color estimates point towards a manipulated region. Unfortunately, the authors do not provide a numerical decision criterion for tampering detection. Thus, an expert is left with the difficult task of visually examining an illuminant map for evidence of tampering. |
| In the field of color constancy, descriptors for the illuminant color have been extensively studied. Most research in color constancy focuses on uniformly illuminated scenes containing a single dominant illuminant. For an overview, see e.g., [4]–[6]. However, in order to use the color of the incident illumination as a sign of image tampering, we require multiple, spatially-bound illuminant estimates. So far, limited research has been done in this direction. The work by Bleier . [7] indicates that many off-the shelf single-illuminant algorithms do not scale well on smaller image regions. Thus, problem-specific illuminant estimators are required. |
| Ebner [8] presented an early approach to multi-illuminant estimation. Assuming smoothly blending illuminants, the author proposes a diffusion process to recover the illumination distribution. Unfortunately, in practice, this approach over smooths the illuminant boundaries. Gijsenij [9] proposed a pixel-wise illuminant estimator. It allows to segment an image into regions illuminated by distinct illuminants. Differently illuminated regions can have crisp transitions, for instance between sunlit and shadow areas. |
A.Collection of trainig samples to form the database
|
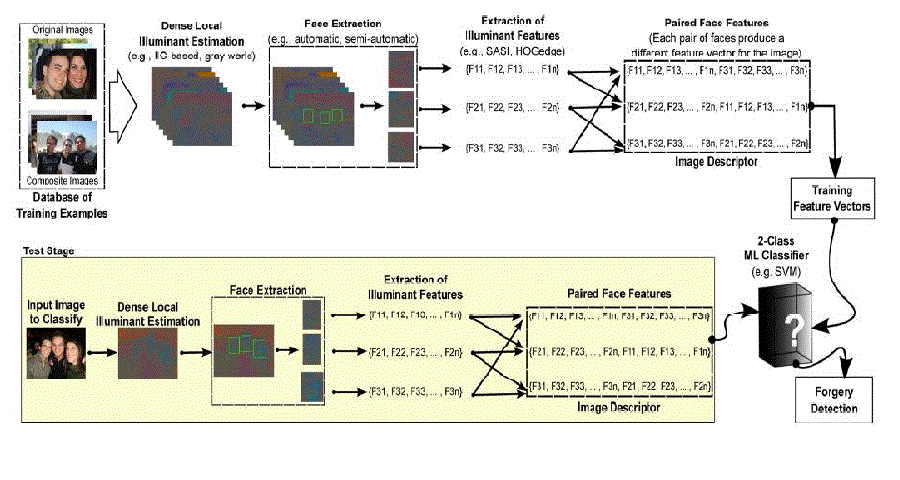
| The first and foremost step in our project is either to collect or create positive and negative samples using image editing softwares . These samples are used for both training phase and testing phase. Positive samples include true images of humans. Negative samples do not contain images with humans or it may contain forgery images . Training process will take about thirty to thirty five days. The data collected from the training process is used to train the SVM classifier which is used during the testing phase. |
B.Illuminant estimation
|
| Second step is to compute a set of localized illuminant color estimates, the input image is segmented into superpixels, i.e., regions of approximately constant chromaticity, using the Gray world algorithm.The input image is segmented into homogeneous regions. Per illuminant estimator, a new image is created where each region is colored with the extracted illuminant color. This resulting intermediate representation is called illuminant map (IM). |
Color constancy
|
| There are different color constancy algorithms. |
| a. Gray World |
| b. White Patch |
| c. Modified White patch |
| d. Progressive |
| e. Single Scale Retinex |
| f. Multi Scale Retinex |
| g. MSR Multi Scale Retinex with Color Restoration |
| h. Automatic Color Equalization |
| Color constancy is the ability to measure colors of objects independent of the color of the light source. |
Gray world Algorithm
|
| The Grey-World assumption, which is at the basis of a well-known color constancy method, assumes that the average reflectance of surfaces in the world is achromatic. We propose the Grey-Edge hypothesis, which assumes that the average edge difference in a scene is achromatic. Based on this hypothesis, we derive an algorithm for illuminant color estimation. The method is easily combined together with Grey-World, max-RGB and Shades of Grey into a single framework for color constancy based on low level image features |
Algorithm :
|
| Step 1: Let I be the image of m rows and n columns. Separate R, G, B from an RGB image. |
| Step 2: Convert the 2 dimensional vector to a 1 dimension vector by summing up all the rows and then again sum up the columns for these separate planes. |
| Rmean = sum(sum(I(:,:,1)))/(m*n); eg: Rmean = 143 |
| Gmean = sum(sum(I(:,:,2)))/(m*n); eg: Gmean = 194 |
| Bmean = sum(sum(I(:,:,3)))/(m*n); eg: Bmean = 177 |
| Step 3: Combine all these single values in a vector and find the mean. |
| [Rmean Gmean Bmean] = [143 194 177] |
| Step 4: find the mean of this vector eg: Avg = 171.333 |
| Avg = mean([Rmean Gmean Bmean]); |
| Step 5: Now divide this Avg to Rmean, Gmean, Bmean and store it |
| Kr = Avg/Rmean; |
| Kg = Avg/Gmean; |
| Kb = Avg/Bmean; |
| Step 6: Now Multiply this final stored value with the respective color planes and finally concatenate the color planes and display the output. |
| OUT(:,:,1) = Kr*double(I(:,:,1)); |
| OUT(:,:,2) = Kg*double(I(:,:,2)); |
| OUT(:,:,3) = Kb*double(I(:,:,3)); |
| OUT = uint8(OUT); |
C.Chromatic image conversion
|
| The next step is to convert the the image using YCbCr to obtain the illuminant map.The YCbCr color space is widely used for digital video. In this format, luminance information is stored as a single component (Y), and chrominance information is stored as two color-difference components (Cb and Cr). Cb represents the difference between the blue component and a reference value. Cr represents the difference between the red component and a reference value. (YUV, another color space widely used for digital video, is very similar to YCbCr but not identical.) YCbCr data can be double precision, but the color space is particularly well suited to uint8 data. For uint8 images, the data range for Y is [16, 235], and the range for Cb and Cr is [16, 240]. YCbCr leaves room at the top and bottom of the full uint8 range so that additional (nonimage) information can be included in a video stream. |
 |
D.Face extraction
|
Existing Method
|
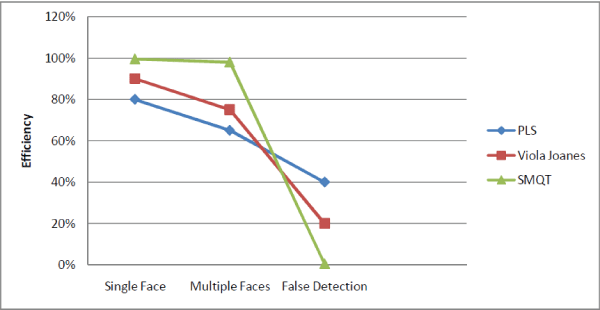
| The algorithm used in the existing is Partial Least Square algorithm(PLS). PLS algorithm results in false detections and at times it fails to detect the faces.So we had to go for semiautomatic face extraction method. This is the only step that may require human interaction in the existing method. An operator sets a bounding box around each face (e.g., by clicking on two corners of the bounding box) in the image that should be investigated. We then crop every bounding box out of each illuminant map, so that only the illuminant estimates of the face regions remain. Implementing the PLS algorithm results at an efficiency rating of only 65%. This is a major disadvantage in this paper. PLS works well only for 2D images and not for 3D images. Failure of PLS is due to the fact that only less number of images can be trained in PLS |
E.Texture description
|
| SASI Algorithm: We use the Statistical Analysis of Structural Information (SASI) to extract texture information from illuminant maps. For our application, the most important advantage of SASI is its capability of capturing small granularities and discontinuities in texture patterns. Distinct illuminant colors interact differently with the underlying surfaces, thus generating distinct illumination “texture”. This can be a very fine texture, whose subtleties are best captured by SASI |
| SASI is a generic descriptor that measures the structural properties of textures. It is based on the autocorrelation of horizontal, vertical and diagonal pixel lines over an image at different scales. Instead of computing the autocorrelation for every possible shift, only a small number of shifts is considered. One autocorrelation is computed using a specific fixed orientation, scale, and shift. Computing the mean and standard deviation of all such pixel values yields two feature dimensions. Repeating this computation for varying orientations, scales and shifts yields a 128-dimensional feature vector. As a final step, this vector is normalized by subtracting its mean value, and dividing it by its standard deviation. |
Interpretation of Illuminant Edges: Hogedge Algorithm
|
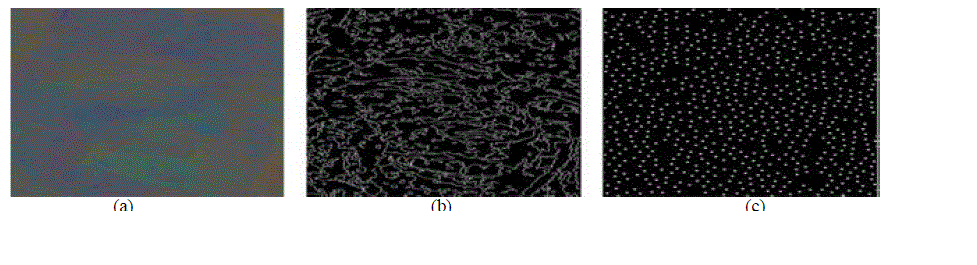
| Differing illuminant estimates in neighboring segments can lead to discontinuities in the illuminant map. Dissimilar illuminant estimates can occur for a number of reasons: changing geometry, changing material, noise, retouching or changes in the incident light. Thus, one can interpret an illuminant estimate as a low-level descriptor of the underlying image statistics.We observed that the edges, e.g., computed by a Canny edge detector, detect in several cases a combination of the segment borders and isophotes (i.e., areas of similar incident light in the image). When an image is spliced, the statistics of these edges is likely to differ from original images. To characterize such edge discontinuities, we propose a new feature descriptor called HOGedge. It is based on the well-known HOGdescriptor |
Procedure
|
| STEP 1: extract edge points using the Canny edge detector |
| STEP 2: yields a large number of spatially close edge points. To reduce the number of points, we filter the Canny output. |
| STEP 3: No. edge points are reduced by selecting bifurication of ridge points |
| STEP 4: We compute Histograms of Oriented Gradients (HOG) to describe the distribution of the selected edge points |
F.Paired face features
|
| Next our goal is to assess whether a pair of faces in an image is consistently illuminated or not. For an image with n faces, we construct joint feature vectors, consisting of (n(n-1))/2 all possible pairs of faces. To compare two faces, we combine the same descriptors for each of the two faces. For instance, we can concatenate the SASI-descriptors that were computed on gray world. The idea is that a feature concatenation from two faces is different when one of the faces is an original and one is spliced. |
G.Classification
|
| We classify the illumination for each pair of faces in an image as either consistent or inconsistent. Assuming all selected faces are illuminated by the same light source, we tag an image as manipulated if one pair is classified as inconsistent. Individual feature vectors, i.e., SASI or HOGedge features on either gray world or IIC-based illuminant maps, are classified using a support vector machine (SVM) classifier with a radial basis function (RBF) kernel. We use a late fusion technique named SVM-Meta Fusion.We classify each combination of illuminant map and feature type independently (i.e., SASI-Gray-World, SASI-IIC, HOGedge-Gray-World and HOGedge-IIC) using a two-class SVM classifier to obtain the distance between the image’s feature vectors and the classifier decision boundary. |
IV.PROPOSED METHOD
|
| Face Extraction plays a very vital role in forgery detection. Unless the face extraction is done flawlessly it is highly impossible to detect the forged or spliced image in the photograph. So further modifications are made in face extraction step in the proposed method. Face Extraction using Successive mean quantization transform (SMQT) along with Sparse network of winnows (SNoW) classifier is employed in the proposed method. |
| Successive mean quantization transform is proposed for illumination and Sparse network of winnows is presented to speed up the original classifier. Finally SMQT features and SNoW classifier are combined with the chrom for the frontal face detection. This is very robust to the illumination, pose etc variations and suitable for real-time face detection system. |
| The goal is to detect the presence of faces in an image using color luminance or chrominance based on SMQT features and SNOW classifier algorithm to detect faces uniform and non uniform background color of the scene. This system is developed in such a way that it supports to get a chrom image, from this pixel values it will also be helpful to get face localization and further used for face detection in real-time. It is able to localize an arbitrary number of faces with different sizes in images taken under varying illumination conditions. Thus wrong recognition results, which are a deficiency of many existing systems, can be reduced considerably. |
VI.CONCLUSION
|
| In this work, we presented a new method for detecting forged images of people using the illuminant color. We estimate the illuminant color using a statistical gray edge method and a physics-based method which exploits chromaticity color space. We treat these illuminant maps as texture maps. An efficient face extraction method called Successive mean Quantization Transform algorithm has been proposed which in turn eliminates human interaction. We also extract information on the distribution of edges on these maps. And then combine these complementary cues (texture- and edge-based) using machine learning late fusion. Comparison of results of various face recognition algorithms is presented in this paper for the sake of highlighting the efficiency of the proposed work. |
| From the results produced it is obvious that using the existing face detection algorithm leads to human interaction. The proposed method requires no human interaction and provides a crisp statement on the authenticity of the image. Additionally, it is a significant advancement in the exploitation of illuminant color as a forensic cue. Prior color-based work either assumes complex user interaction or imposes very limiting assumption. |
Figures at a glance
|
 |
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
Figure 5 |
 |
 |
 |
 |
| Figure 6 |
Figure 7 |
Figure 8 |
Figure 9 |
|
| |
References
|
- M. Johnson and H. Farid, “Exposing digital forgeries through specular highlights on the eye,” in Proc. Int. Workshop on Inform. Hiding, 2007,pp311–325
- P. Saboia, T. Carvalho, and A. Rocha, “Eye specular highlights telltales for digital forensics: A machine learning approach,” in Proc. IEEE Int.Conf. Image Processing (ICIP), 2011, pp. 1937–1940
- C. Riess and E. Angelopoulou, “Scene illumination as an indicator of image manipulation,” Inf. Hiding, vol. 6387, pp. 66–80, 2010.
- K. Barnard, V. Cardei, and B. Funt, “A comparison of computational color constancy algorithms–Part I: Methodology and Experiments With
- K. Barnard, L. Martin, A. Coath, and B. Funt, “A comparison of computational color constancy algorithms – Part II: Experiments With ImageData,” IEEE Trans. Image Process., vol. 11, no. 9, pp. 985–996, Sep. 2002
- A. Gijsenij, T. Gevers, and J. van de Weijer, “Computational color con-stancy: Survey and experiments,” IEEE Trans. Image Process., vol. 20,no. 9, pp. 2475–2489, Sep. 2011
- M. Bleier, C. Riess, S. Beigpour, E. Eibenberger, E. Angelopoulou, T. Tröger, and A. Kaup, “Color constancy and non-uniform illumination: Canexisting algorithms work?,” in Proc. IEEE Color and Photometry in Comput. Vision Workshop, 2011, pp. 774–781.
- M. Ebner, “Color constancy using local color shifts,” in Proc. Eur. Conf. Comput. Vision, 2004, pp. 276–287.
- A. Gijsenij, R. Lu, and T. Gevers, “Color constancy for multiple light sources,” IEEE Trans. Image Process., vol. 21, no. 2, pp. 697–707, Feb.
|