Keywords
|
| Mobile adhoc network (MANET), Routing protocols |
INTRODUCTION
|
| An ad-hoc network is a wireless network formed by wireless nodes without any help of infrastructure. In such a network, the nodes are mobile and can communicate dynamically in an arbitrary manner. The network is characterized by the absence of central administration devices such as base stations or access points. Furthermore, nodes should be able to enter or to leave the network easily. In these networks, the nodes act as routers. They play an important role in the discovery and maintenance of the routes from the source to the destination or from a node to another one. This is the principal challenge to such a network. If link breakages occur, the network has to stay operational by building new routes. The main technique used is the multi-hopping which increase the overall network capacity and performances. By using multihopping, one node can deliver data on behalf of another one to a determined destination. Thus, the problem of range radio is solved. |
| A Mobile Ad hoc Network (MANET) represents a system of wireless mobile nodes that can self-organize freely and dynamically into arbitrary and temporary network topology. On one hand, they can be quick deployed anywhere at any time as they eliminate the complexity of infrastructure setup. On the other hand, other problems arise, such as route errorsor higher overhead, caused by the mobility of nodes. In order to avoid some designing bugs or problems, it is necessary to analyze the designed protocols formally before protocols are deployed or applied. Considering the particularities of MANET, the secure traits are different from the traditional security such as secrecy and authenticity. Formal analysis methods have used for many years in cryptographic protocols, however, there are no mature theories and methods in MANET. |
RELATED WORKS
|
| Energy is an important resource that needs to be preserved in order to extend the lifetime of the network, on the other hand, the link and path stability among nodes allows the reduction of control overhead and can offer some benefits also in terms of energy saving over ad hoc networks. [11] The conventional on-demand routing protocols use flooding to discover a route. They broadcast a Route REQuest (RREQ) packet to the networks, and the broadcasting induces excessive redundant retransmissions of RREQ packet and causes the broadcast storm problem, which leads to a considerable number of packet collisions, especially in dense networks. Therefore, it is indispensable to optimize this broadcasting mechanism. However, as will be shown in this contribution, the selection of more stable routes under nodes mobility can lead to the selection of shorter routes. This is not always suitable in terms of energy consumption. Some solutions to routing have been presented also for these cases, starting from the basic epidemic routing, where messages are blindly stored and forwarded to all neighboring nodes, generating a flood of messages. Existing routing protocols (AODV, DSR) are must take to a "store and forward" approach, where data is incrementally moved and stored throughout the network in hopes that it will eventually reach its destination. |
| On demand routing protocols for ad hoc networks discover and maintain routes on a reactive, “as-needed” basis. These protocols are attractive for their low routing overheads. We develop a technique to make these protocols energyaware in order to increase the operational lifetime of an ad hoc network. The quality of service support in mobile ad hoc networks depends not only on the available resources in the network but also on the mobility rate of such resources. This is because mobility may result in link failure which in turn may result in a broken path. Furthermore, mobile ad hoc networks potentially have fewer resources than fixed networks. Therefore, more criteria are required in order to capture the quality of the links between nodes. Quality of service routing is a routing mechanism under which paths are generated based on some knowledge of the quality of network, and then selected according to the quality of service requirements of flows. Thus, it is evident that both the aforementioned parameters (i.e., link stability associated with the nodes mobility and energy consumption) should be considered in designing routing protocols, which allow right tradeoff between route stability and minimum energy consumption to be achieved. |
| Broadcasting is an effective mechanism for route discovery, but the routing overhead associated with the broadcasting can be quite large, especially in high dynamic networks [9]. Ni et al. [5] studied the broadcasting protocol analytically and experimentally, and showed that the rebroadcast is very costly and consumes too much network resource. The broadcasting incurs large routing overhead and causes many problems such as redundant retransmissions, contentions, and collisions [5]. Thus, optimizing the broadcasting in route discovery is an effective solution to improve the routing performance. Haas et al. [10] proposed a gossip based approach, where each node forwards a packet with a probability. They showed that gossip-based approach can save up to 35 percent overhead compared to the flooding. However, when the network density is high or the traffic load is heavy, the improvement of the gossip-based approach is limited [9]. Kim et al. [8] proposed a probabilistic broadcasting scheme based on coverage area and neighbor confirmation. This scheme uses the coverage area to set the rebroadcast probability, and uses the neighbor confirmation to guarantee reach ability. Peng and Lu [11] proposed a neighbor knowledge scheme named Scalable Broadcast Algorithm (SBA). This scheme determines the rebroadcast of a packet according to the fact whether this rebroadcast would reach additional nodes. Abdulai et al. [12] proposed a Dynamic Probabilistic Route Discovery (DPR) scheme based on neighbor coverage. In this approach, each node determines the forwarding probability according to the number of its neighbors and the set of neighbors which are covered by the previous broadcast. This scheme only considers the coverage ratio by the previous node, and it does not consider the neighbors receiving the duplicate RREQ packet. Thus, there is a room of further optimization and extension for the DPR protocol. Several robust protocols have been proposed in recent years besides the above optimization issues for broadcasting. Chen et al. [13] proposed an AODV protocol with Directional Forward Routing (AODV-DFR) which takes the directional forwarding used in geographic routing into AODV protocol. While a route breaks, this protocol can automatically find the next-hop node for packet forwarding. Keshavarz-Haddad et al. [11] proposed two deterministic timer-based broadcast schemes: Dynamic Reflector Broadcast (DRB) and Dynamic Connector-Connector Broadcast (DCCB). They pointed out that their schemes can achieve full reach ability over an idealistic lossless MAC layer, and for the situation of node failure and mobility, their schemes are robustness. |
| Stann et al. [13] proposed a Robust Broadcast Propagation (RBP) protocol to provide near-perfect reliability for flooding in wireless networks, and this protocol also has a good efficiency. They presented a new perspective for broadcasting: not to make a single broadcast more efficient but to make a single broadcast more reliable, which means by reducing the frequency of upper layer invoking flooding to improve the overall performance of flooding. In our protocol, we also set a deterministic rebroadcast delay, but the goal is to make the dissemination of neighbor knowledge much quicker. |
PRELIMINARIES
|
A.NODE LIFETIME PREDICTION ALGORITHM
|
| If there are two nodes that have the same residual energy level, an active node that is used in many dataforwarding paths consumes energy more quickly, and thus, it has a shorter lifetime than the remaining inactive node. The node lifetime that is based on its current residual energy and its past activity solution that does not need to calculate the predicted node lifetime from each data packet .An exponentially weighted moving average method to estimate the energy drain rate evi . Ei represents the current residual energy of node i, and evi is the rate of energy depletion. Ei can simply be obtained online from a battery management instrument and evi is the statistical value that is obtained from recent history. The estimated energy drain rate in the nth period, and ev(n−1) i is the estimated energy drain rate in the previous (n − 1)th period. α denotes the coefficient that reflects the relation between evn and evn−1 , and it is a constant value with a range of [0, 1]. |
| We are only concerned with the minimum node lifetime or the connection lifetime in a route from two nodes of a stable connection are within the communication range of each other, the connection lifetime may last longer, and they are not a bottleneck from the route to which they belong.. Easy to measure the distance between nodes Ni and Ni−1 when we use Global-Positioning-System-based location information . Senders transmit packets with the same power level a receiver can measure the received signal power strength when receiving a packet and then calculates the distance by directly applying the radio propagation model. |
| If the received signal power strength is lower than a threshold value, we regard this link as an unstable state and then calculate the connection time. Our proposed method requires only two sample packets, and we implement piggyback information on route-request (RREQ) and route-reply (RREP) packets during a route-discovery procedure with no other control message. |
PROPOSED WORK
|
| Routes are pre computed and stored in a table, so that route will be available whenever a packet is available for transmission. The selection and maintenance of a multihop path, however, is a fundamental problem in MANETs. Node mobility, signal interference, and power outages make the network topology frequently change; as a consequence, the links along a path may fail and an alternate path must be found. The last category based on link stability is unique to wireless network. Link stability refers to the ability of a link to survive for certain duration. The higher the link stability, the longer is the link duration. We focus on the stability of a routing path, which is subject to link failures caused by node mobility. The main aim of this work is to propose an optimization routing model within a MANET. The model attempts to minimize simultaneously the energy consumption of the mobile nodes and maximize the link stability of the transmissions, when choosing paths for individual transmissions. |
| We propose a neighbor coverage-based probabilistic rebroadcast (NCPR) protocol. Therefore, 1) in order to effectively exploit the neighbor coverage knowledge, we need a novel rebroadcast delay to determine the rebroadcast order, and then we can obtain a more accurate additional coverage ratio; 2) in order to keep the network connectivity and reduce the redundant retransmissions. |
| The main contributions of NCPR are as follows: |
| 1. We propose a novel scheme to calculate the rebroadcast delay. The rebroadcast delay is to determine the forwarding order. The node which has more common neighbors with the previous node has the lower delay. If this node rebroadcasts a packet, then more common neighbors will know this fact. Therefore, this rebroadcast delay enables the information that the nodes have transmitted the packet spread to more neighbors, which is the key to success for the proposed scheme. |
| 2. We also propose a novel scheme to calculate the rebroadcast probability. The scheme considers the information about the uncovered neighbors (UCN), connectivity metric and local node density to calculate the rebroadcast probability. |
| 3. A routing protocol called Delay Aware and Route Stability Protocol (DARSP) is proposed with addition of NCPR. This routing protocol applies the following three metrics for neighbor coverage selection: 1) the estimated total energy to transmit and process a data packet; 2) the residual energy; 3) the path stability. Route maintenance and route discovery procedures are similar to the DSR protocol, but with the route selection based on the three aforementioned metrics. A delivery probability of each node is used to select link stability path over dynamic route discovery. |
| Delivery probabilities are synthesized locally from context information. We define context as the set of attributes that describe the aspects of the system that can be used to drive the process of message delivery. An example of context information can be the change rate of connectivity, i.e., the number of connections and disconnections that a host experienced over the last T seconds. |
| The process of prediction and evaluation of the context information in DARSP can be summarized as follows: |
| 1. Each host calculates its delivery probabilities for a given set of hosts. |
| 2. This process is based on the calculation of utilities for each attribute describing the context. |
| 3. The calculated delivery probabilities under current status are periodically sent to the route request neighbor as part of the update of routing information. |
| 4. Each host maintains a logical forwarding table of tuples describing the next logical hop and its associated delivery probability for all known destinations. |
| 5. Each host uses local prediction of delivery probabilities between updates of information. |
| 6. Each host selects the best forwarding node among list of neighbor’s on the basis of highest stability value. |
| 7. These steps continue until reach the destination. |
SIMULATION ENVIRONMENT
|
| In order to evaluate the performance of the proposed NCPR protocol, we compare it with some otherprotocols using the NS-2 simulator. In this paper, we just study one of the applications: route request in route discovery. In order to compare the routing performance of the proposed NCPR protocol, we choose the Dynamic Probabilistic Route Discovery [12] protocol which is an optimization scheme for reducing the overhead of RREQ packet incurred in route discovery in the recent literature, and the conventional AODV protocol. Simulation parameters are as follows: The Distributed Coordination Function (DCF) of the IEEE 802.11 protocol is used as the MAC layer protocol. The radio channel model follows a Lucent’s WaveLAN with a bit rate of 2 Mbps, and the transmission range is 250 meters. We consider constant bit rate (CBR) data traffic and randomly choose different source-destination connections. Every source sends four CBR packets whose size is 512 bytes per second. The mobility model is based on the random waypoint model in a field of 1;000 m _ 1;000 m. In this mobility model, each node moves to a random selected destination with a random speed from a uniform distribution.After the node reaches its destination, it stops for a pausetime interval and chooses a new destination and speed. In order to reflect the network mobility, we set the max-speed to 5 m/s and set the pause time to 0. The MaxDelay used to determine the rebroadcast delay is set to 0.01 s, which is equal to the upper limit of the random jitter time of sending broadcast packets in the default implementation of AODV in NS-2. Thus, it could not induce extra delay in the route discovery. The simulation time for each simulation scenario is set to 300 seconds. In the results, each data point represents the average of 30 trials of experiments. The confidence level is 95 percent, and the confidence interval is shown as a vertical bar in the figures. The detailed simulation parameters are shown in Table 1. |
| We evaluate the performance of routing protocols using the following performance metrics: |
| MAC collision rate: the average number of packets (including RREQ, route reply (RREP), RERR, and CBR data packets) dropped resulting from the collisions at the MAC layer per second. |
| Normalized routing overhead: the ratio of the total packet size of control packets (include RREQ, RREP, RERR, and Hello) to the total packet size of data packets delivered to the destinations. For the control packets sent over multiple hops, each single hop is counted as one transmission. |
| Packet delivery ratio: the ratio of the number of data packets successfully received by the CBR destinations to the number of data packets generated by the CBR sources. |
| Average end-to-end delay: the average delay of successfully delivered CBR packets from source to destination node. It includes all possible delays from the CBR sources to destinations. |
| The experiments are divided to three parts, and in each part we evaluate the impact of one of the following parameters on the performance of routing protocols: |
| • Number of nodes. |
| • Number of CBR connections. |
| • Random packet loss rate. |
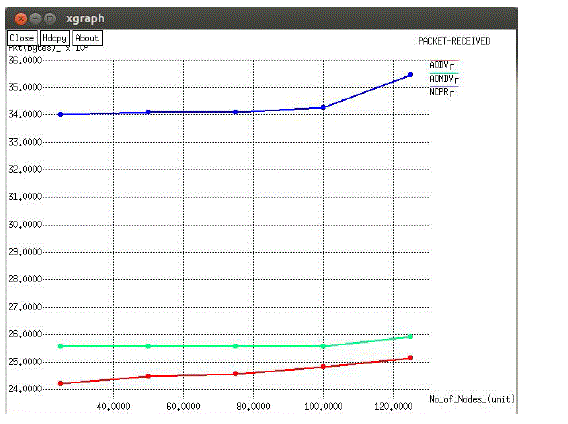
| Figure 1 shows the packet delivery ratio with increasing packet loss rate. NCPR protocols have a higher packet delivery ratio than the conventional AOMDV protocol. On average, the packet. delivery ratio is improved by about 15.5 percent in the NCPR protocol when compared with the conventional AOMDV protocol. |
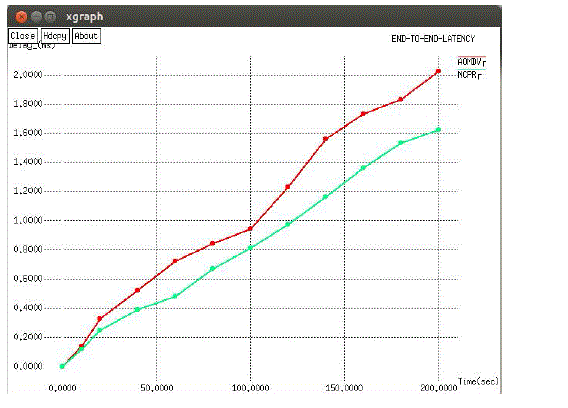
| Figure 2 shows low latency of NCPR compared to the AOMDV. On average, the end-to-end delay is reduced by about 53.9 percent in the NCPR protocol when compared with the conventional AOMDV protocol. This low latency of NCPR will provide good performance. |
| Figure 3 shows the Routing Control Overhead on varying the node mobility. The graph shows that NCPR has Routing Control Overhead less compared to AOMDV even if the Routing Control Overhead increases. |
CONCLUSION
|
| In MANETs, a link is formed by two adjacent mobile nodes, which have limited battery energy and can roam freely, and the link is said to be broken if any of the nodes dies because they run out of energy or they move out of each other’s communication range. The node lifetime and the LLT to predict the route lifetime and have proposed a new algorithm that explores the dynamic nature of mobile nodes, such as the energy drain rate and the relative motion estimation rate of nodes, to evaluate the node lifetime and the LLT. Combining these two metrics by using our proposed route lifetime-prediction algorithm, select the least dynamic route with the longest lifetime for persistent data forwarding. Finally, evaluate the performance of the proposed NCPR protocol based on the DSR. Simulation results show that the NCPR protocol outperforms the DSR protocol implemented with LPR and SSA mechanisms. |
| |
Tables at a glance
|
 |
| Table 1 |
|
| |
Figures at a glance
|
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
|
| |
References
|
- Bettstetter. C, Resta. G and Santi P (2003) “The node distribution of the random waypoint mobility model for wireless ad hoc networks”, IEEE Trans.MobileComput., Vol. 2, No. 3, pp. 257–269.
- Dube. R, Rais. C.D, Wang. K.Y and Tipathi S.K (1997) “Signal stability based adaptive routing (SSA) for ad hoc mobile networks”, IEEE Pers.Commun., Vol. 4, No. 1, pp. 36–45.
- Gerharz. M, de Waal. C, Frank. M and Martini P (2002), “Link stability in mobile wireless ad hoc networks”, in Proc. 27th Annu.IEEE Conf. Local Comput. Net. pp. 30–42.
- Le Boudec. J Y and Vojnovic M (2005) “Perfect simulation and stationary of a class of mobility models”, in Proc. IEEE INFOCOM, pp. 2743–2754.
- Maleki. M, Dantu. K and Pedram. M (2003) “Lifetime prediction routing in mobile ad hoc networks” ,in Proc. IEEE WCNC, pp. 1185–1190.
- Marbukh.V and Subbarao.M (2000) “Framework for maximum survivability routing for a MANET”, in Proc. MILCOM, pp. 282–286.
- Misra.A and Banerjee. S (2002), “MRPC: Maximizing network lifetime for reliable routing in wireless environments”, in Proc. IEEE WCNC, pp. 800–806.
- Qin. L and Kunz.T (2002) “Pro-active route maintenance in DSR”, ACM SIGMOBILE Mobile Comput.Commun. Rev., Vol. 6, No. 3, pp. 79–89.
- Samar.P and Wicker.S.B (2004) “On the behavior of communication links of a node in a multi-hop mobile environment”, in Proc. Int. Symp.Mobile Ad Hoc Netw.Comput, pp. 145–156.
- Sarkar.T.K, Ji. Z, Kim. K, Medouri. A, and Salazar Palma. M, (2003) “A survey of various propagation models for mobile communication”, IEEE Antennas Propag. Mag., Vol. 45, No. 3, pp. 51–82.
- Xin MingZhang, En Bo Wang, Jing Jing Xia, Dan Keun Sung (2013) “A Neighbor Coverage-Based Probabilistic Rebroadcast for Reducing Routing Overhead in Mobile Ad Hoc Networks” IEEE transactions on Mobile Computing, Vol. 12,.
- J.D. Abdulai, M. Ould-Khaoua, L.M. Mackenzie, and A. Mohammed,(2008) “Neighbour Coverage: A Dynamic Probabilistic Route Discovery for Mobile Ad Hoc Networks,” Proc. Int’l Symp. Performance Evaluation of Computer and Telecomm. Systems (SPECTS’08), pp. 165-172..
- J. Chen, Y.Z. Lee, H. Zhou, M. Gerla, and Y.Shu, (2006) “Robust Ad Hoc Routing for Lossy Wireless Environment,” Proc. IEEE Conf. Military Comm. (MILCOM ’06), pp. 1-7,.
|