Keywords
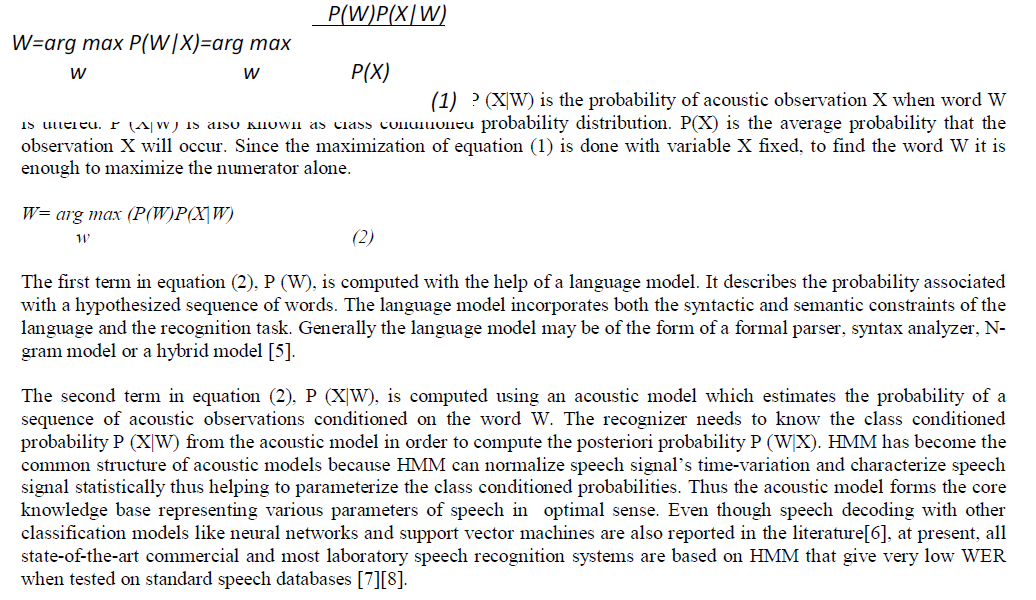
|
| Topology; Routing protocol; Geographic routing; Mobile Ad hoc Network (MANET) |
INTRODUCTION
|
| Mobile Ad Hoc network is a collection of mobile nodes which can communicate with each other forming an infrastructure less network. The communication between various nodes can be achieved using multi hop wireless links, since the base stations are absent. Nodes maintain routing information in the routing table for data forwarding.The mobile nodes can be turned on or off at any time without reporting other nodes as they move randomly. In order to preserve the routing information, the nodes need to track the topological changes that take place in the network. The applications of MANETs are military operations, emergency rescue operations, disaster recovery etc. Several protocols have been developed for MANETs such as (Destination Sequenced Distance Vector) DSDV, (Dynamic Source Routing) DSR, (Ad hoc On Demand Routing) AODV, (Optimized Link State Routing) OLSR, (Greedy Perimeter Stateless Routing) GPSR, (Location Aided Routing) LAR. This paper aims to discover the various energy efficient routing protocols like AODV and DSRfor evaluating energy with respect to network size considering the remaining battery power [1]. It also concentrates on the consumption of mobile node in the network in order toincrease the node life time. |
| The important features of MANET nodes are frequent link breakage and use of constraint resources like bandwidth, computing power, battery lifetime. Communication channel is highly insecure as it is wireless. Overhearing and concealing can be done easily. Routing protocols are highly sophisticated due to non-fixed topology and it is quite challenging to secure such protocols in the presence of hostile nodes. All nodes have similar features and capabilities forming a symmetric environment. The control and management of mobile ad hoc network is shared among the nodes that are involved in participation. |
| The two major routing approaches in MANET are topology based routing and position based routing.Topology-based routing protocols use link information in which the details about the paths is maintained and routes are established based on the link information in the network. Position based routing protocols or geographic routing approaches rely on physical location information of nodes. Thus, it is necessary for nodes to obtain their coordinates either by using a location servicesuch as GPS or other types of positioning services [15]. |
II. LITERATURE SURVEY
|
| Data communication problems in Ad hoc networks includeRouting wheremessage is sent from a source to a destination.Broadcastingwhichfloods a message from a source to all other nodes in the network. Multicastinginwhich message from a source is sent to a set of appropriate destinations. In geocastingamessage is sent from a source to all nodes inside a geographic region, andLocation updatingmaintains accurate information about the location of other nodes [12]. The purpose of each protocol, in an ad-hoc network, is to find effective routes between two communicating nodes [11]. Various categories of protocols are reactive protocol, proactive protocol, flow oriented protocol, hierarchical protocol and hybrid protocol. |
| A. Reactive protocol |
| Reactive protocol also called as on demand routing protocol is based upon query–reply dialog and is used in most cases. Examples for reactive protocols are AODV, DSR, etc. It consumes more time to find routes and network obstruct can cause flooding. |
| 1) Ad-hoc On-Demand Distance Vector Routing |
| AODV is an on demand routing protocol [10] which establishes routes and connection when needed to reduce traffic overhead. AODV is a combination of DSR and DSDV routing protocols. It derives the mechanism of route discovery and route maintenance from DSR protocol, along with the use of sequence number, hop by hop routing, and episodic beacons from DSDV. AODV maintains routing tables on the nodes as an alternative to header in the data packet. The source node initiates route discovery process by sending a route request(RREQ) to the neighbor nodes and an intermediate node sends route reply (RREP) if it knows a recent path than the one known by the sender node to the destination. |
| A destination sequence number indicates the recent path is as follows, a route request by sender node is given a higher sequence number and lower sequence number to node that does not know destination and cannot send RREP. Forward links are setup when these RREP moves back along the path of RREQ. So the routing table entries send the data packet and the route is not included in the packet header. Error message is passed when link fails and repeats the process. |
| 2) Dynamic Source Routing |
| DSR is a reactive routing protocol designed for use in multi hop wireless Ad hoc networks. A node in the network finds the routes when needed and maintains the routing information in the routing table. In this protocol the mobile nodes need to maintain the route caches. The routes are stored in a route cache to reduce the number of control messages to be sent by updating the new routes. Route Discovery is a mechanism that obtains a route. |
| Route Maintenance is used to detect route if the network topology is altered. Initially when a node wants to communicate with another node, it issues a Route Request (RREQ) to all its neighbor nodes. Each node receiving the RREQ packets retransmits it unless it discovers the target node. The target node replies to the RREQ message with a route reply (RREP) packet. The RREP packet takes the traverse path back to the source node established by the RREQ packet. This route is kept in the source node cache for further communication. If a nodes link is broken the source node is informed by a route error (RERR) packet and is discarded from the route cache. |
| 3) Location Aided Routing Like DSR, LAR is an on-demand source routing protocol similar to DSR. The main difference between LAR and DSR is that LAR sends location information in all packets to (hopefully) decrease the overhead of a future route discovery. In DSR if the neighbors of Source S do not have a route to Destination D then S floods the entire ad hoc network with a route request packet for D[14]. LAR uses location information for mobile nodes by the Global Positioning System (GPS)which knows the location to flood a route request packet for D in a forwarding zone instead of in the entire ad hoc network. |
| B. Proactive protocol |
| In proactive protocol all the nodes maintains the list of information about the next node through routing tables. The entire nodes constantly update their position in order to send the data packet from one node to the other node after mutual agreement. Hence the source node does not need route discovery to find a route to destination. Example for proactive protocol is DSDV. In case of failure it causes slow reaction and needs required amount of data for maintenance. |
| 1) Destination Sequenced Distance Vector |
| Nodes maintain routing table which stores next hop, cost metric towards each destination, and a sequence number that is created by the destination. Each node increments and appends its sequence number when sending its local routing table, routes with greater sequence numbers are preferred. When a node decides that a route is broken, it increments the sequence number of the route. |
| 2) Optimized Link State Routing |
| OLSR is a proactive routing protocol which uses hello and topology control messages to discover and broadcast link state information. Individual nodes use topology information to perform hop destinations. The main uses are energy saving, node interference reduction and network lifetime expansion. The administrator has some control and can change topology by modifying the parameters like state (active or stand by) of thenodes, role of the nodes and transmission power of nodes. |
| C. Flow-Oriented protocol |
| Flow-Oriented protocol finds routes on demand by following present flows. One option is to unicast successively when forwarding data while promoting a new link. Finding new routes without prior knowledge takes a long time and causes traffic to compensate for missing knowledge on routes. |
| D. Hierarchical protocol |
| The routing starts with proactively prospected routes and serves demand for additional routes on reactive flooding. |
| E. Hybrid protocol |
| Hybrid protocol is a combination of proactive and reactive routing and it is based upon distance vector protocol but contain many features and advantage of link state protocol. Hybrid protocol enhances interior gateway routing protocol. In this protocol controlling traffic depends on traffic volume |
| F. Greedy Perimeter Stateless Routing |
| GPSR uses packet destination and position of routers to make packet forwarding. It makes forwarding using routers through immediate neighbors in the network. GPSR is based on greedy and perimeter forwarding where all packet headers include a field indicating whether it uses greedy or perimeter mode. |
| 1) Greedy Forwarding: |
| The greedy choice in selecting next hop of a packet is done if a node knows the radio neighbors position by geographic hops to reach destination. If there is only one route to a destination then the data packet moves temporarily farther in a geometric distance from destination. If there are no closer nodes, it uses Perimeter forwarding |
| 2) Perimeter Forwarding |
| This method is used in regions where greedy forwarding is not feasible. It forwards the packets by constructing planar graph called Gabriel graph which is constructed using vertices and edges. The graph contains interior and exterior faces. Interior face is boundary close to graph while the Exterior face is boundary outside the graph [4]. |
III.GEOGRAPHIC ROUTING
|
| Geographic routing is based on position of a location where source sends location message to destination rather than address of the network. For the forwarding strategy [5], the geographic routing maintains the position of final destination of packet and the position of a node’s neighbor.The previous can be obtained by querying a location service such as the Grid Location System (GLS) [6] or Quorum [7]. In GLS each node acts location server to track the node locations. It maintains tables which contain node ID and nodes geographic location.In latter, each node exchanges its own location information obtained by using GPS or the localization schemes [8] with its neighboring nodes. Hence every node builds a local map within its locality referred to as the local topology. |
IV. NODE LIFETIME PREDICTION ALGORITHM
|
| Most of the research work is based on node lifetime and history activities to improve the energy level of nodes which involves in routing. Operational lifetime is therefore defined as the time until the network partitioning occurs due to battery outage [9]. |
| A)Active Mode (or Transmit Mode):This is the mode in which transmission and receiving takes place simultaneously using enormous amount of power. |
| B) Doze Mode (or Receive Mode):In this the CPU is capable of processing information and receiving message notifications from other nodes and listening to broadcasts is performed. |
| C) Sleep Mode (or Standby Mode):In this the CPU remains idle without performing any processing, where the remains in inactive state. Initially the energy of nodes is set to any random value. All the modes are set to a specific value. And if the node is within the particular range it is made to participate. |
| Chen [2] have proposed energy-efficient AODV for Low mobility Ad hoc Networks, in which the node energy consumption of the overall network is reduced by dynamically controlling the transmission power by utilizing a novel route cost metric. |
| Wattenhofer [3] have proposed Distributed Topology control for power efficient operation in multi hop wireless Ad Hoc networks can be controlled by varying the transmission power of each node. A distributed algorithm is proposed where each node makes local decisions about its transmission power and these local decisions collectively guarantee global connectivity. |
| If there are two nodes that have the same outstanding energy level, a node that is used in most of the data-forwarding paths consumes energy easily, and thus, it has a shorter lifetime compared to the remaining inactive node. The node lifetime relies on its current residual energy and its past activity solution that does not need to compute the predicted node lifetime from each data packet. An exponential weighted moving average method is used to calculate the energy drain rate evi. |
| Eirepresents the current outstanding energy of the node i, and eviis the rate of energy reduction. Ei is obtained online from a battery management instrument, and evi is the arithmetical value obtained from recent history.Evi nis the estimated energy drain rate in the nth period. The estimated energy drain rate in the nth period, and ev(n−1) is the estimated energy drain rate in the previous (n − 1)th period. αdenotes the coefficient that reveals the relation between evnandev(n−1), and it is a constant value using a range of (0, 1) [13]. Tnis the time in nth second.Ei nTis the energy in nth second at time T. |
| The node lifetime can be obtained at a time t as |
 |
V. CONCLUSION
|
| The challenges and basic concepts behind various routing in MANETs are studied. The AODV protocol is better compared to other protocols since it establishes route only when needed and preserves lifetime of nodes.The applications are expected to expand in the future communication environments. The support for QoS based routing will be an important and desired factor. Several important research issues and open questions need to be addressed to facilitate QoS support in MANETs. Capability estimation, route discovery, route maintenance and possible path selection are studied. A study is also made on how to increase the lifetime of nodes in MANET for better forwarding. |
References
|
- Jaya Jacob and V.Seethalakshmi, “Performance Evaluation of Various Routing Protocols in MANET”, International Journal of EngineeringSciences, Dec. 2011, Vol. 5.
- R.Wattenhofer, L.Li,P.Bahl,andY.M.Wang,“Distributed topology control for power efficient operation in multi hop wireless ad hoc networks”,INFOCOM 2001, Twentieth Annual Joint Conference of the IEEE Computer and Communications Societies, Proceedings,Volume: 3.
- Chen Jie,ChenJiapin,and Li Zhenbo, “Energy-Efficient AODV for Low Mobility Ad Hoc Networks”, International Conference on WirelessCommunications, Networking and Mobile Computing, WiCom 2007.
- B.Karp and H.T. Kung, “GPSR: Greedy Perimeter Stateless Routing for Wireless Networks,” Proc. ACM MobiCom, pp. 243-254, Aug. 2000.
- Q.Chen, S.S.Kanhere, M. Hassan, and K.C.Lan, “Adaptive Position Update in Geographic Routing”, IEEE International Conference onCommunications (ICC ’06), pp. 4046-4051, June 2006.
- J.Li, J.Jannotti, D.S.J.D. Couto, D.R. Karger and R.Morris, “A Scalable Location Service for Geographic Ad Hoc Routing”, in Proc.ACMMobiCom,pp. 120-130, aug.2000.
- Z.J.Haas and B.Liang, “Ad Hoc Mobility Management with Uniform Quorum Systems”, IEEE/ACM Transactions on Networking, vol. 7, no. 2, pp.228-40, Apr. 1999.
- J.Hightower and G.Borriello, “Location Systems for Ubiquitous Computing”, IEEE Computer, vol. 34, no. 8, August 2001, pp. 57-66.
- Akhilesh.A.Waoo, Dr.P.S.Patheja, Dr. Sanjay Sharma, and TriptiNema, “QoS Routing Algorithm with Sleep Mode in MANETs”, Journal ofComputer Networks, 2013, Vol. 1, No. 1, 10-14.
- C.Perkins, E.Belding- Royer, S.Dasandquet, “Ad Hoc On-Demand Distance Vector (AODV) Routing”, IETF Draft, June 2002.
- V.Kanakaris, D.Ndzi and D.Azzi., “Ad-hoc Networks Energy Consumption: A review of the Ad-Hoc Routing Protocols”, Journal of EngineeringScience and Technology Review 3 (1) (July 2010).
- JieWu and Ivan Stojmenovic, “Ad Hoc Networks”, IEEE computer society, feb 2004.
- Xin Ming Zhang, Feng Fu Zou, En Bo Wang and Dan Keun Sung, “Exploring the Dynamic Nature of Mobile Nodes for Predicting Route Lifetimein Mobile Ad Hoc Networks”, IEEE transactions on vehicular technology, vol. 59, no. 3, march 2010.
- D.Johnson and D.Maltz, “Dynamic source routing in ad hoc wireless networks,” in Mobile Computing, the Kluwer International Series inEngineering and Computer Science Volume 353, pp 153-18, 1996.
- M.Mauve, J.Widmer and H.Hartenstein, “A Survey on Position Based Routing in MobileAd-hoc Networks”, IEEE Network Magazine, 15(6):30–39,November 2001.
|