ISSN ONLINE(2320-9801) PRINT (2320-9798)
ISSN ONLINE(2320-9801) PRINT (2320-9798)
K.Sukanya1 Dr.R.Indra Gandhi2
|
| Related article at Pubmed, Scholar Google |
Visit for more related articles at International Journal of Innovative Research in Computer and Communication Engineering
“AN APPROACH TO UTILIZE MD5 GENERATOR FOR UTILITY OPITIMIZATION”is a web application to automate the process of managing the infrastructure facilities in the Training Hall. The software developed will help in allotment of Systems to the users of the Hall, surrendering of the systems after the usage, monitoring of Hardware devices and Application software installed in the systems. It also aims to register complaints in the system and monitoring of the attending to the complaints by the Hardware Engineer. The System will help to register user details. In case User is a Programmer, the Project details and the Project Head to whom he/she is reporting. The System allows the users to login with their details and can register their system complaints and follow up their complaint till it is attended. Several levels are being designed which consists of modules like user login, system allotment, monitoring of hardware, system software, complaints and attendance is being registered. Final report is being submitted.
Keywords |
|||||||||||||||
| Session, Page Token. Md5 Generator. | |||||||||||||||
INTRODUCTION |
|||||||||||||||
| The objective of Secured Online System for Managing Training Hall Infrastructureis software developing will help in allotment of Systems to the users of the Training Hall, surrendering of the systems after the usage, monitoring of Hardware devices and Application software installed in the systems. | |||||||||||||||
| Session tokens are used for maintaining the user sessions in web applications.A major challenge faced by a web application developer as opposed to any other developer is session management.In non-web client server architecture, once the client connects to the server, the connection is open till explicitly closed. So, the server knows which user and which client it is talking to. Web developers do not have this luxury. Web server treats each request as a new one and serves a response. It has no means of distinguishing between clients leaving it to the developer to maintain different sessions for different users. | |||||||||||||||
PAGE TOKEN |
|||||||||||||||
| Page tokens solve a number of security issues. Since a page token is much short lived, it is now more difficult for attackers to browse a user’s session. The page tokens present in a particular page are valid only till the user clicks one of the links. A soon as the server receives a new request, the old tokens are overwritten with a new set. Variable manipulation attacks can be avoided if page tokens are used. The request for any page needs to be accompanied by a valid page token, the user cannot type the URL for an arbitrary page and view it. | |||||||||||||||
MD5 GENERATOR |
|||||||||||||||
| The MD5 message-digest algorithm is a widely used cryptographic hash functionthat produces a 128-bit (16-byte) hash value. Specified in RFC 1321, MD5 has been utilized in a wide variety of security applications, and is also commonly used to check data integrity. MD5 was designed by Ron Rivest in 1991 to replace an earlier hash function, MD4. An MD5 hash is typically expressed as a hexadecimalnumber, 32 digits long.Fig 3.1 shows how a data is being hashed using md5 generator.File servers often provide a pre-computed MD5 (known as Md5sum) checksum for the files, so that a user can compare the checksum of the downloaded file to it. Most Unix-based operating systems include MD5 sum utilities in their distribution packages; | |||||||||||||||
Mathematical Formulation |
|||||||||||||||
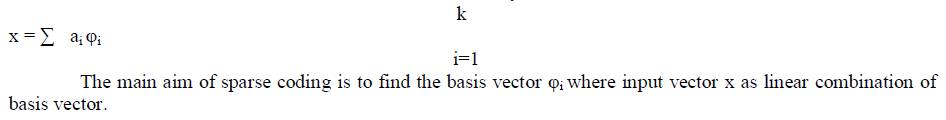 Denote the XOR, AND, OR and NOT operations respectively. Denote the XOR, AND, OR and NOT operations respectively. |
|||||||||||||||
| Fig 3.3 gets input from user and fig 3.4 generates the corresponding output for users input. | |||||||||||||||
4.1 STRUCTURE I: Training Phase |
|||||||||||||||
| The overall plan of the project is to develop an effective application which satisfies the needs of the user who surf the information in the website. | |||||||||||||||
| This will also take into consideration of the various functionalities like allotment, surrender, monitoring of Hardware and system Software, monitoring of complaints. | |||||||||||||||
4.2 STRUCTURE II: Mapping Phase |
|||||||||||||||
Map server for windows: (ms4w) |
|||||||||||||||
| The purpose of this package is to allow all levels of Map Server users to quickly install a working environment for Map server development on windows. | |||||||||||||||
| 1. Organizations who want to distribute preconfigured Map server applications that will run out of the box. | |||||||||||||||
| 2. Developers who want to set up a stable development environment quickly. | |||||||||||||||
| 3. Trainers who need an easily installed configuration that is identical across multiple machines. | |||||||||||||||
| 4. Novices who need help just getting all the various bits and pieces together. | |||||||||||||||
PROCESS |
|||||||||||||||
| Implementation is the most crucial stage in achieving a successful system and giving the user’s confidence that the new system is workable and effective. | |||||||||||||||
| Implementation is the process of converting a new system design into operation. | |||||||||||||||
| The main objective of my project is to develop a web application for NIC.The intension of this application is to provide a flexible, scalable and user-friendly interface for the users. As soon as the user login this application, the system checks for the user id to identify if it’s a block user or a valid user to display the corresponding home page through which the user navigate to various pages to get information or to enter data inform to generate report. | |||||||||||||||
SCREEN SHOTS |
|||||||||||||||
Analysis and Interpretation |
|||||||||||||||
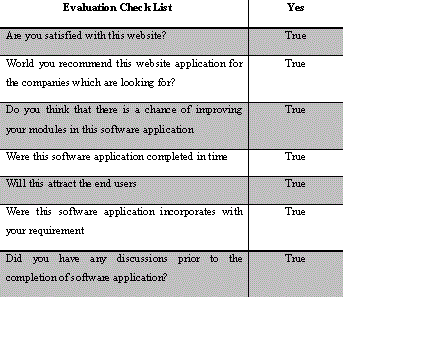
Training Result |
|||||||||||||||
 |
|||||||||||||||
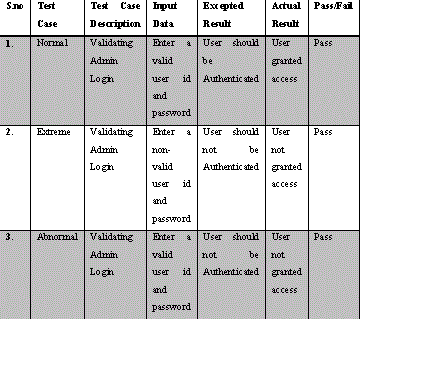
| Testing Result | |||||||||||||||
 |
|||||||||||||||
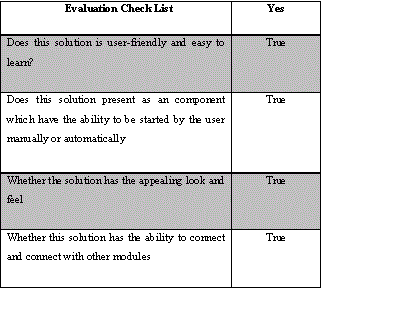
Concluded Result |
|||||||||||||||
 |
|||||||||||||||
CONCLUSION |
|||||||||||||||
| This project incorporates all requirements of a Server. This system has been developed as versatile and uses friendly as possible keeping in mind the features in this technology. This system supports and improves many of the core functionality of the organization. Using such a system helps the organization in minimizing the time and money consumed in fulfilling the day-to-day functionality’s and cutting down the expenses incurred on the same. | |||||||||||||||
Figures at a glance |
|||||||||||||||
|
|||||||||||||||
References |
|||||||||||||||