Keywords
|
| Wireless sensor network, CTP, FNA-CTP, Data collection |
INTRODUCTION
|
| A Wireless Sensor Network (WSN) is an ad hoc network with a number of sensors deployed across a wide geographical area. Collecting data from the neighboring nodes and forwarding it to the destination node is a most common requirement in sensor networks. CTP is such a routing protocol for transferring data to one or more sensor nodes that achieves agility and efficiency while offering a high reliable data delivery ratio in static sensor networks. Since, wireless sensors are being highly employed in mobile environments such as VANETs, monitoring of large areas and other mobile environments it must provide efficient coverage. |
| There are several other routing protocols for addressing mobility in MANETs providing general communication techniques. The main challenge in mobile sensor networks is that its topology changes over time as the nodes move, thus it requires a highly dynamic and robust methods to ensure packet delivery. It is very essential to have a routing protocol that minimizes energy dissipation in such networks and correctly and reliably transmit the data to the sink node. |
| The Collection Tree Protocol (CTP) is a best effort protocol and is designed for relatively low traffic rates while its performance drops in high traffic rate and is one of the most promising data collection protocol. CTP has shown to be a very efficient routing protocol and has wide applications in static WSN. CTP was selected over other routing protocols in WSN as many applications in WSN involve only data collection rather than peer to peer communication. The intention is to show that CTP would function better than other routing protocols when put in data collection scenarios in mobile sensor networks. |
RELATED WORK
|
| Prior work on CTP mostly focused on evaluating the performance in static sensor networks. Santini et al implemented CTP in Castalia 3.0 WSN simulator which is based on OMNET which offers advanced radio channel model based on empirically measured data and radio model based on real radios for low-power communication range. The underlying MAC module in Castalia is Tunable-MAC which does not support all the features of CTP, so that it has undergone some modifications. The main modifications include changes to the queue length, snooping mechanism, link layer acknowledgements and the backoff timers. The performance of CTP was evaluated through a set of metrices including data delivery ratio, throughput and packet drop. The simulation showed that as the number of nodes increases, the data delivery ratio decreases. This is because of the collisions in the network as the packets travelling in the network increases. There will also be a lack of reliability in the network as the distance between the source and the sink nodes approaches node’s transmission range. This is because of the retransmissions that are needed for successful delivery of a packet. The packets need to be delivered fill up the buffers and new incoming packets were dropped. The control overhead also decreases with the number of nodes sending data at a time increases. This results in congestion, packet drop and lost acknowledgements and affects the performance of CTP. The most important feature of mobile sensor networks are energy consumption and network lifetime. However, CTP focuses only on energy consumption and network lifetime in static scenarios only. |
| In Cluster based routing protocols, the nodes are grouped together and the one with the high residual energy is chosen as the cluster head. Energy distribution will be more efficient in this case. The Cluster based routing protocols includes LEACH, PEGASIS and TEEN protocols. |
| In LEACH (Low Energy Adaptive Clustering Hierarchy), it uses randomization to select the cluster heads balancing the energy dissipation and thus increasing the network lifetime whereas in PEGASIS, each node communicates with only one neighbor at a time and takes turns to communicate with the base station. When all the nodes have communicated with the base station a new round starts. Thus saves power consumption with every round. TEEN protocol is similar to LEACH and it differs in such a way that it defines two thresholds, soft and hard. The advantage of this cluster approach is that they are scalable and managing routes is easier in this case. |
| The problem with these routing protocols is that they can be employed only in static scenarios and mobility handling is quiet difficult. Since cluster heads are also moving in mobile scenarios it requires frequent computation. They are also not suited for time critical applications as it takes time to compute these cluster heads. |
| In LEACH- mobile protocol, it uses a two way communication mechanism to become a part of a cluster. The cluster head sends a message to the sensor nodes in its cluster and if it does not hear from a sensor node it is assumed to have moved out and it connects with other clusters. This also has packet losses and energy consumption due to packet overhead. |
| Multihop- LEACH is a routing protocol in which the node with high residual energy is chosen as the cluster head. This selects optimal path and adopts multihop between cluster and the sink. In general, the cluster based routing protocols are not suited for mobile environments since it requires frequent computing. |
PROPOSED SYSTEM
|
| Design: CTP is a collection tree based protocol whose main objective is to provide anycast datagram communication to the root node in the network. There will be a multiple root nodes in the network and the one with minimum cost is chosen as the root node. At start the root node advertises themselves and the source node use these advertisements to form the collection tree. CTP uses routing messages for tree construction and data messages to report data to the sink. CTP uses Expected Transmission Value (ETX) as its routing gradient which indicates the link quality. ETX is nothing but the number of transmissions that a node requires to transmit the data to its neighboring node after receiving the acknowledgement. ETX of a node can be calculated by using the formulae, |
| ETX (node) = ETX (parent) + ETX (link to parent) |
| CTP chooses the route with minimum ETX. ETX of the root node is always zero. The nodes on the tree advertise their ETX values to its neighbors. When the sink node request for information, every node updates its hop count and ETX values and then it transfers the data. The link estimator calculates the link quality by sending the routing beacon packets periodically. The data packets can also be used keep track of link quality changes and therefore it reduces the control packets. The acknowledgement information is given to the forwarding engine by the MAC layer and the forwarding engine removes the data from the cache informing about the acknowledgement to the link estimator. The CTP implementation uses adaptive beaconing mechanism and Trickle algorithm for reducing the control traffic. A topology change in the network results in performance degradation because of the resetting of routing table and long silent intervals. CTP does not respond fast enough to the topology changes and results in packet loss. |
FNA-CTP
|
| The FNA-CTP is adding a few back up static sensor nodes to the mobile nodes to act when the nodes move from the tree. This back up sensor nodes will join the tree as a part of fail over procedure. The fixed nodes are distributed on the basis of the transmission range to cover the entire network. All the mobile sensor nodes will be in the transmission range of at least one of the fixed nodes. Every node will have at least one fixed node entry in its routing table which can be identified by a special flag bit. The procedure is same as that of the CTP except that if the source node does not receive the acknowledgement then it sends the data to the fixed node in its transmission range. The adaptive beaconing mechanism is used here to calculate the link quality except that the beaconing interval is not set to the minimum value. The fixed node may send the received packet to the parent which may be a fixed or mobile node. This is repeated until the packet arrives at the sink node. |
| This method improves the data delivery ratio and throughput. Link quality mechanism of CTP is used for long distance communications. The back-up infrastructure increases the reliability of the network in mobile environments. The tree establishment is same as that of CTP. In FNA-CTP, the fixed nodes send the routing beacons with a special flag bit called fixed bit set. |
| The nodes receiving these broadcast messages will create an entry in the routing table with its ETX value. |
| Route discovery, forwarding and reacting to failure methods are different from CTP. Route discovery happens after the link estimator table determines its routing table entries. The data is forwarded to the next hop with minimum ETX. If the fixed node has the minimum ETX then the data is forwarded to it otherwise it is forwarded to the mobile node with minimum ETX. Only two attempts are made. If both the attempts fail, the FNA-CTP chooses the fixed node as its next hop. No adaptive beaconing mechanism is employed here to react to failures. But it is used to react to lost links. The data delivery ratio is thus increased by having more fixed nodes. Some of the packets were dropped because the buffer is filled up and when the mobile node is too far. This can be avoided by using fixed nodes with a higher transmission range. |
| Security: Public key encryption is used here. A public key is given to all the nodes in the network and a private key will be available to the communicating nodes. To communicate with the sink, source node fetches the public key of the sink and encrypts it using the public key and an encryption algorithm. The sink node, on receiving decrypts the data using its private key. If there is any intruder, then an IDS (Intrusion Detection System) is used to inform all the nodes in the network. This provides a secured data delivery. |
Simulation and Results
|
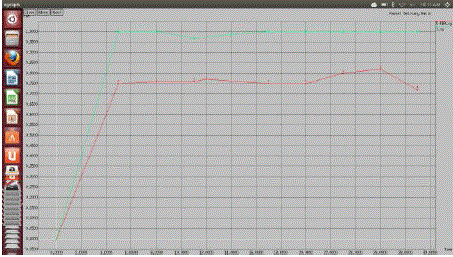
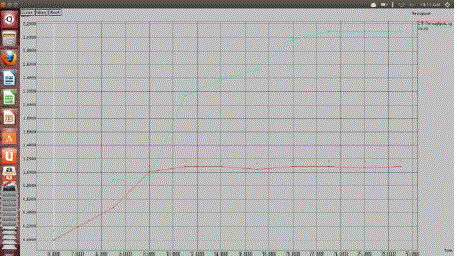
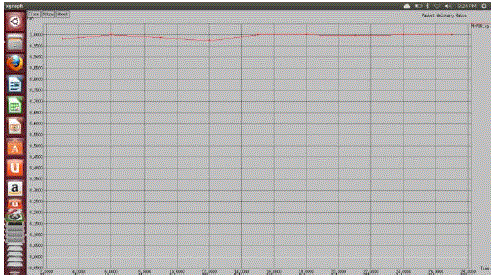
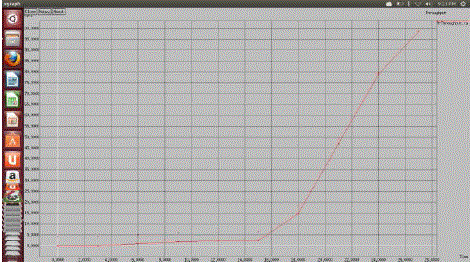
| The simulation results show that data delivery ratio of FNA-CTP increases when compared with CTP. The packet drop is also decreased when more number of fixed nodes is used. |
CONCLUSION AND FUTURE SCOPE
|
| In this work, fixed nodes acts as a back upwhen the mobile nodes are not able to deliver the packets to the nodes which are destined. This results in improved data delivery ratio and throughput. By using the IDS features secured data delivery is also guaranteed in the mobile networks. This is also suitable for VANETs where the speed of the vehicles vary. |
Figures at a glance
|
 |
 |
 |
 |
| Figure 1 |
Figure 2 |
Figure 3 |
Figure 4 |
|
| |
References
|
- Steere DC, Baptista A, McNamee D, Pu C, Walpole J,(2002) Research challenges in environmentalobservation and forecasting systems, 292-299.
- Akyildiz IF, Su W, Sankarasubramaniam Y, CayirciE(2002). A survey on sensor networks,Communications magazine, IEEE. 40 102-114.
- Colesanti U, Santini S (2010), A performance evaluation of the collection tree protocol based on itsimplementation for the castalia wireless sensor networks simulator, ETH.
- Ding Y, Xiao L.(2012) SADV: Static-node-assisted adaptive data dissemination in vehicular networks,Vehicular Technology, IEEE Transactions on. 59 2445-2455.
- RR Selmic, J Kanno, J Buchart, N Richardson(2007). Quadratic Optimal Control of Wireless SensorNetwork Deployment, Proc. Cyberspace Research Workshop, Shreveport, Louisiana .
- De Couto DS, Aguayo D, Bicket J, Morris R(2005). A high-throughput path metric for multi-hop wirelessrouting, Wireless Networks.11 419 434.
- Sharma D,Liscano R, Shah Heydari S, (2011) Collector Tree Protocol (CTP) performance in mobile Wireless Sensor Networks, 001548-001552.
- Chen X, Yu P,(2010) Research on hierarchical mobile wireless sensor network architecture with mobile sensor nodes, 7 2863-2867.
- Lotf J, HosseinzadehM,Alguliev RM,(2010) Hierarchical routing in wireless sensor networks: a survey, 3 V3-650-V3-654.
- Biradar RV, Sawant D, Mudholkar D, Patil D.(2011) Multi-Hop Routing In Self-Organizing WirelessSensor Networks, IJCSI International Journal ofComputer Science. 8 154-164.
- Santhosh Kumar G, Vinu Paul, and Poulose Jacob K.(2008)"Mobility metric based leach-mobileprotocol." in 16th International Conference on Advanced Computing and Communications, pp. 248-253.IEEE, 2008.
- Levis PA, Patel N, Culler D, ShenkerS(2003), Trickle: A self-regulating algorithm for code propagationand maintenance in wireless sensor networks,Computer Science, University of California 2003.
|